Short Summary
The Unit 42 Managed Threat Hunting team has identified a variant of WikiLoader, known as WailingCrab, which is being delivered through SEO poisoning and spoofing of GlobalProtect VPN software. This article discusses the evasion techniques employed by WikiLoader, the specific tradecraft observed, and the implications for threat hunting and detection.
Key Points
- WikiLoader Variant: Identified as WailingCrab, delivered via SEO poisoning.
- Delivery Method: Spoofing GlobalProtect VPN software through cloned websites.
- Historical Activity: Active since late 2022, initially delivered via phishing.
- Target Sectors: Primarily affects U.S. higher education and transportation sectors.
- Evasion Techniques: Includes anti-analysis checks, typosquatting, and using legitimate sites for command and control (C2).
- Indicators of Compromise: Provided URLs and SHA-256 hashes for detection.
- Detection Mechanisms: Multiple XQL queries for Cortex XDR shared for threat hunting.
MITRE ATT&CK TTPs – created by AI
- Initial Access (T1071.001): Application Layer Protocol
- Using MQTT for C2 communications.
- Execution (T1203): Exploitation for Client Execution
- Malicious payload executed upon downloading spoofed GlobalProtect installer.
- Persistence (T1547.001): Startup Items
- Creating scheduled tasks for persistence.
- Defense Evasion (T1562): Impair Defenses
- Using legitimate software renamed to evade detection.
- Employing fake error messages to mislead users.
- Command and Control (T1071): Application Layer Protocol
- Using MQTT brokers for C2 communications.
- Credential Access (T1555): Credentials from Password Stores
- Potentially accessing credentials through injected code.
Executive Summary
The Unit 42 Managed Threat Hunting team (MTH) identified a variant of WikiLoader loader for rent (aka WailingCrab) being delivered via SEO poisoning and spoofing our GlobalProtect VPN software. Analysis conducted by the Advanced WildFire reverse engineering team has uncovered the latest evasion techniques for WikiLoader, providing new insights into its evolution.
We provide multiple XQL queries for Cortex XDR to hunt for this WikiLoader campaign. We also provide hashes that identify samples found in the wild as well as command and control (C2) URLs extracted from the original sample that spoofed GlobalProtect.
Palo Alto Networks customers are better protected from the threats discussed in this article through detection mechanisms available from the following products:
Overview of Tradecraft Used by WikiLoader in Campaigns Spoofing GlobalProtect
WikiLoader is a multistage malware loader that adversaries developed with consideration toward evasion. Our industry partners have documented this threat well. As such, we’ll focus on the specific tradecraft we observed related to campaigns spoofing GlobalProtect, anti-analysis techniques employed by the loader and resources for threat hunters.
Proofpoint has reported WikiLoader has been active since at least late 2022. They also noted that phishing was initially the primary means of delivery. Its operators used compromised WordPress sites and public MQ Telemetry Transport (MQTT) brokers for C2.
We have not observed the follow-on payloads from complete WikiLoader infections. However, Proofpoint reported attackers used the threat to deliver banking Trojans such as Danabot and Ursnif/Gozi to organizations based in Italy.
In June 2024, we observed a WikiLoader campaign leveraging GlobalProtect themed SEO poisoning, rather than using previously documented phishing tactics. SEO poisoning is the process of getting an attacker-controlled site on the front page of search engine results for a legitimate product through purchasing advertisements or improving page rank.
Attackers commonly use SEO poisoning as an initial access vector to trick people into visiting a page that spoofs the legitimate search result to deliver malware rather than the searched-for product. This campaign’s delivery infrastructure leveraged cloned websites relabeled as GlobalProtect along with cloud-based Git repositories.
Unit 42 primarily observed WikiLoader affecting the U.S. higher education and transportation sectors. However, the use of SEO poisoning for delivery almost certainly broadens the scope of possible victims as compared to phishing.
WikiLoader is a loader for rent, which is suspected to be leveraged by at least two initial access brokers (IABs). Attribution for this specific campaign requires further research. However, we do make the following observations.
- Campaigns leveraging WikiLoader and spoofing GlobalProtect have shown reasonable regard for evasion
- The threat operators show an awareness of simple techniques that, when executed well, make machine and signature-based detection of such threats difficult
Such OPSEC considerations include:
- Using the MQTT internet of things (IoT) event queue protocol for C2
- Typosquatting and spoofing download pages modified to deliver WikiLoader throughout the life of a campaign
- Using legitimate sites running vulnerable, third-party WordPress plugins as C2 infrastructure
- Using cloud-hosted Git solutions to host malicious content
- Using legitimate, signed binaries for sideloading WikiLoader
- Using common file names associated with security tooling, where allowlistings in security products would reduce detection and response efficacy
- Embedding payloads in seemingly benign file names and types
- Hiding attributes for all files except the file that receives user interaction
- Encrypting shellcode that is stored in separate binaries from the WikiLoader executables
- Decrypting keys for shellcode that operators stored in the C2 servers
- Performing multiple anti-analysis checks
- Displaying fake error messages on execution
Figure 1 provides a summary of the infection chain.
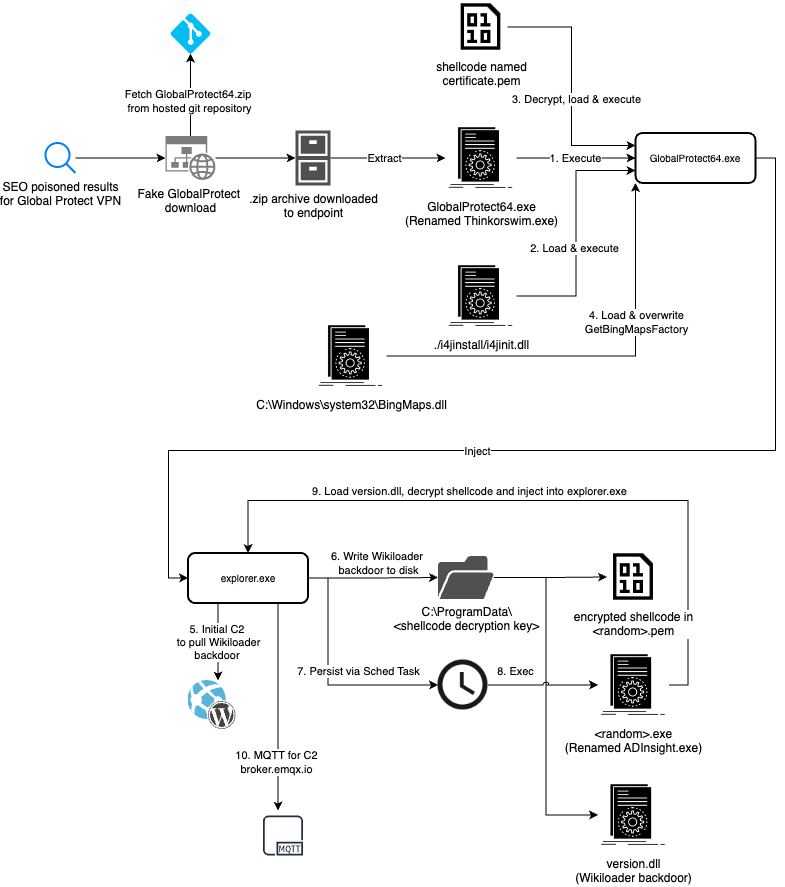
Delivery and Execution
The following section details the execution of WikiLoader as delivered through GlobalProtect-based SEO poisoning.
The advertisements we observed linked to multiple fake sites serving spoofed GlobalProtect installers. Figure 2 shows a malicious advertisement that attackers used to lure victims to a spoofed GlobalProtect download page.
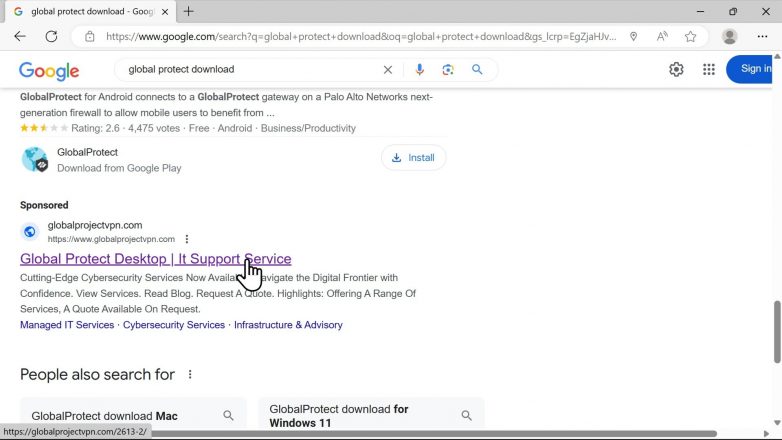
The first site is a clone of a legitimate business that fetches the malicious payload upon download shown in Figure 3. Bitbucket took the site offline when we notified them of it.
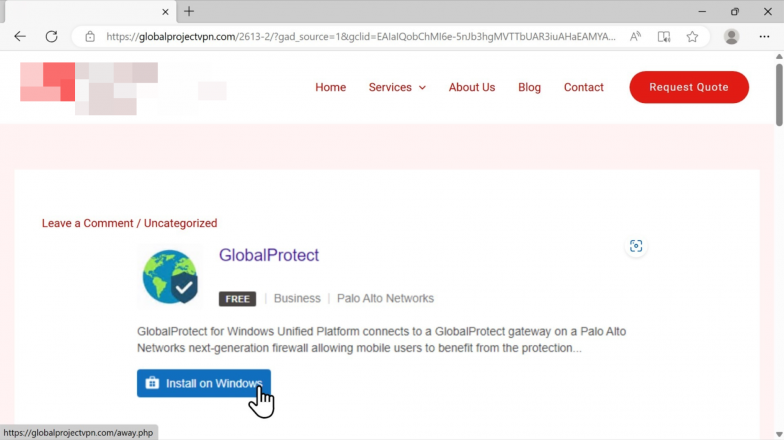
The second site shown in Figure 4 is a site that spoofs the GlobalProtect client download page.

Upon download, Cortex XDR shows the following information associated with Chrome where the sample is enriched with Mark of the Web (MotW) data as shown in Figure 5. MotW is a security feature in Windows that adds metadata to files downloaded from the internet to indicate a potentially unsafe source. Analysts can use this information to assist in understanding the source of a file, and where someone may have been browsing before downloading the file.
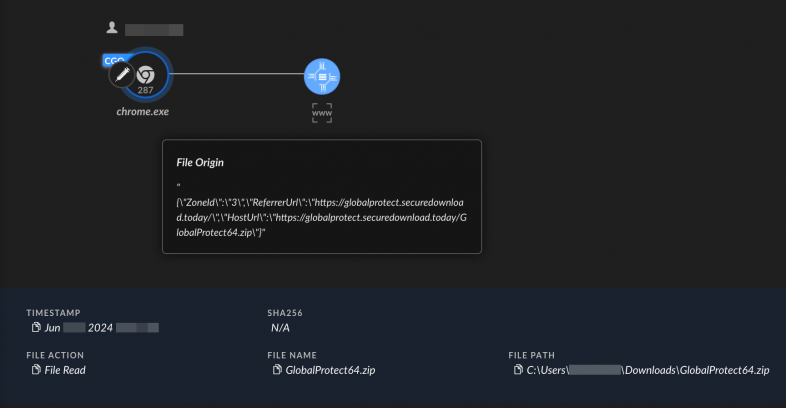
Figure 6 shows how the sample appears to the victim. The sample only shows a single file in the folder.
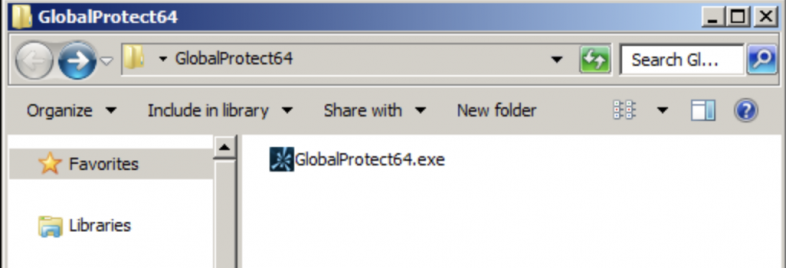
Figure 7 shows that when viewing all the hidden files and folders, there are more than 400 files.
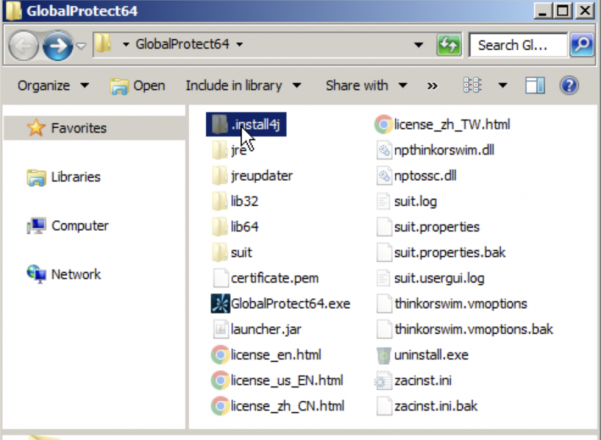
Figure 8 shows what we see when viewing all files in the archive and checking the signer. GlobalProtect64.exe is a renamed copy of a legitimate share trading application that attackers used to sideload the first WikiLoader component.
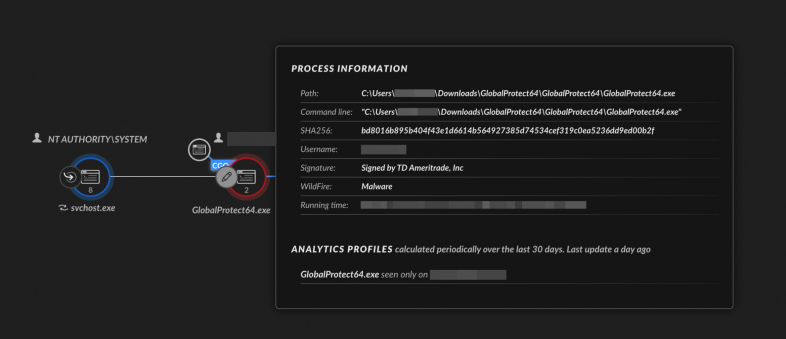
Figure 9 shows that upon execution of GlobalProtect64.exe, the threat loads the first WikiLoader component i4jinst.dll, located inside the directory .install4j.
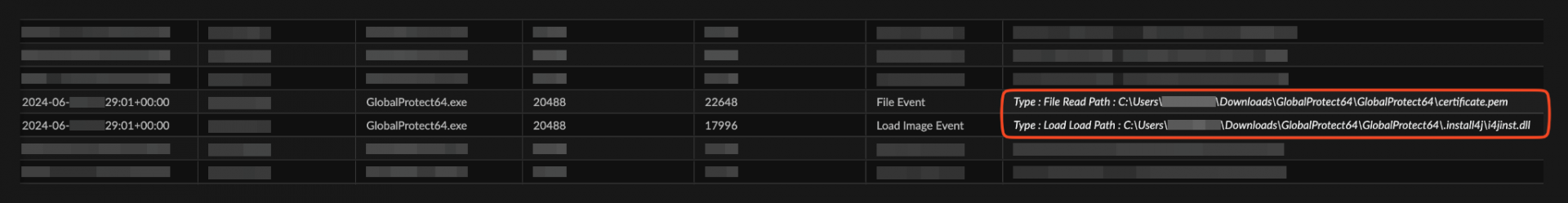
The i4jinst.dll Load Image event causes the malicious module to be loaded into the binary spoofing GlobalProtect64.exe. Once loaded, i4jinst.dll reads the first stage encrypted shellcode from certificate.pem. It then decrypts the shellcode and injects it into explorer.exe.
This includes the following discrete actions:
- The decrypted certificate.pem contains the first stage shellcode that is executed
- The shellcode loads C:WindowsSystem32BingMaps.dll
- The function GetBingMapsFactory is then overwritten with another shellcode decrypted from certificate.pem
- The overwritten shellcode then carries out thread injection into the explorer.exe process
At this point in the infection chain, Cortex’s shellcode prevention raised alerts as shown in Figure 10.
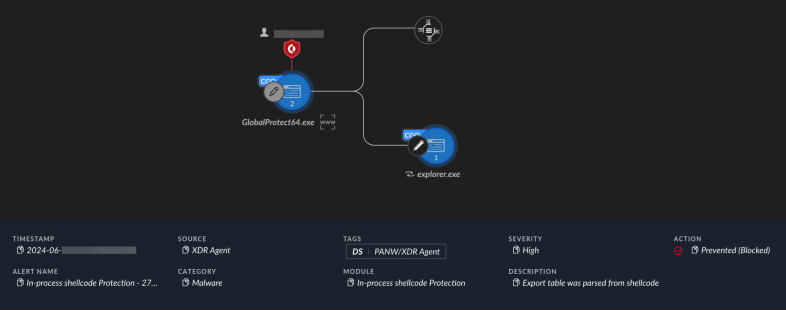
If unprevented, the injected code in explorer.exe will contact a compromised site running WordPress CMS as a C2 server for the WikiLoader backdoor. It will then establish persistence and communicate with MQTT brokers for tasking.
The injected code will load license_us_EN.html. In the GlobalProtect spoofing campaign, license_us_EN.html is a renamed copy of the AdInsight.exe Microsoft Sysinternals binary. License_us_EN.html will side load the WikiLoader backdoor downloaded from the C2 server.
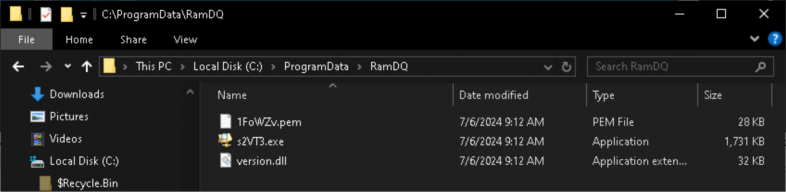
Upon establishing persistence, AdInsight.exe (renamed to license_us_EN.html) will be renamed again to a random filename. This file will be written into a randomly named folder in ProgramData along with a randomly named file with the extension .pem and the WikiLoader backdoor as a .dll. This process is shown in Figure 11.
In testing environments where shellcode protection was disabled, Cortex XDR still generated an analytic behavioral indicator of compromise (BIOC) detection for the unusual creation of a scheduled task created by explorer.exe following the shellcode injection.
In summary, the infection chain is as follows:
- Malicious behaviors begin when the victim launches GlobalProtect64.exe and this file then loads i4jinst.dll (located inside .install4j)
- Once loaded, i4jinst.dll will read and decrypt the contents of the file certificate.pem
- The decrypted certificate.pem contains the first stage shellcode that the threat executes
- The shellcode loads C:WindowsSystem32BingMaps.dll
- The function GetBingMapsFactory is then overwritten with another shellcode decrypted from certificate.pem
- The overwritten shellcode then carries out thread injection into the explorer.exe process
- The injected code in the explorer.exe process will contact the C2 server for the WikiLoader backdoor
- If persisting, the threat will write license_us_EN.html and another file with extension .pem to a randomly named folder in ProgramData along with the WikiLoader backdoor as a .dll
- The threat will establish persistence via a scheduled task to execute the renamed license_us_EN.html
- The injected code will read and execute a hidden PE file from license_us_EN.html
- License_us_EN.html will side load the WikiLoader backdoor downloaded from the C2 server
- The backdoor will decrypt the shellcode encrypted in the randomly named file with extension .pem. The decryption key is the name of the folder where the backdoor is located.
We have added additional protections to Cortex, and we share a collection of hunting rules written in XQL at the end of this post.
Highlighting WikiLoader Anti-Analysis and Defense Evasion
The following are some unique tricks that this sample of WikiLoader used.
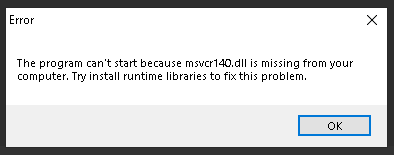
Fake Error Message
As the spoofed GlobalProtect installer is not an actual installer, the authors of WikiLoader needed another trick to fool victims. The threat shows a fake error message when it completes infection of the victim machine. This prevents the victim from wondering why GlobalProtect is not installed.
Figure 12 shows the fake error message generated by the sample.
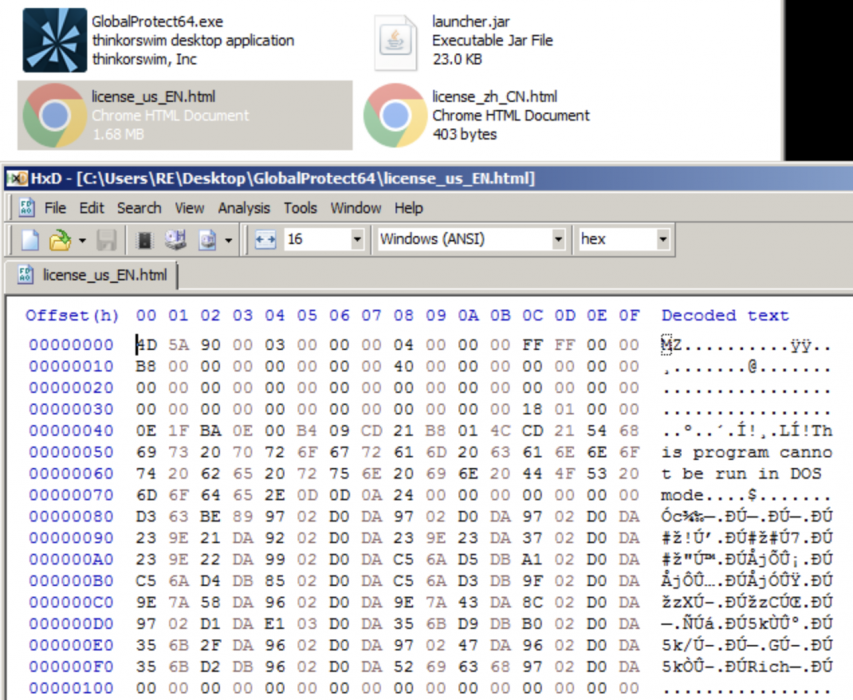
Renamed Legitimate Software Used for Side-Loading Backdoor
Attackers renamed the Microsoft Sysinternals tool ADInsight.exe to license_us_EN.html, and hid it inside the spoofed GlobalProtect installer. ADInsight.exe is used to side load the WikiLoader backdoor. Figure 13 shows the contents of license_us_EN.html.
Checks for Analysis Environments
The sample checks the running processes in the victim machine against a list of hashes of software commonly used by malware analysts. As most malware analysts would be using a virtualized environment to analyze malware samples, the WikiLoader sample will terminate if it finds processes related to virtual machine software.
To hide the list of processes that WikiLoader is looking for, the malware uses a 32-bit hashing routine similar to those used by Emotet back in 2021. Figure 14 shows the hashing routine used by this WikiLoader sample.
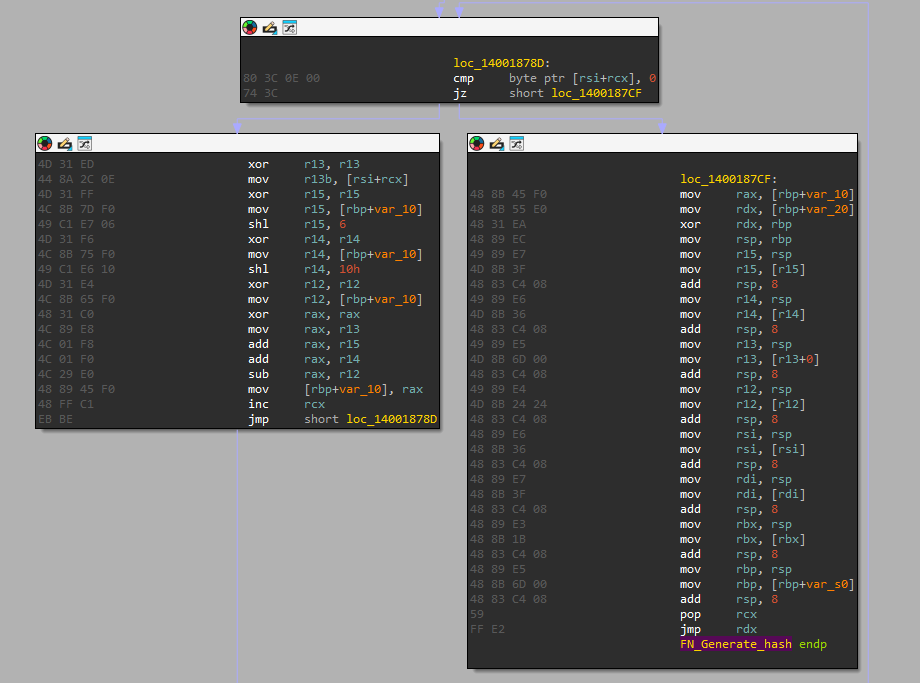
Folder Name as Decryption Key for the Backdoor
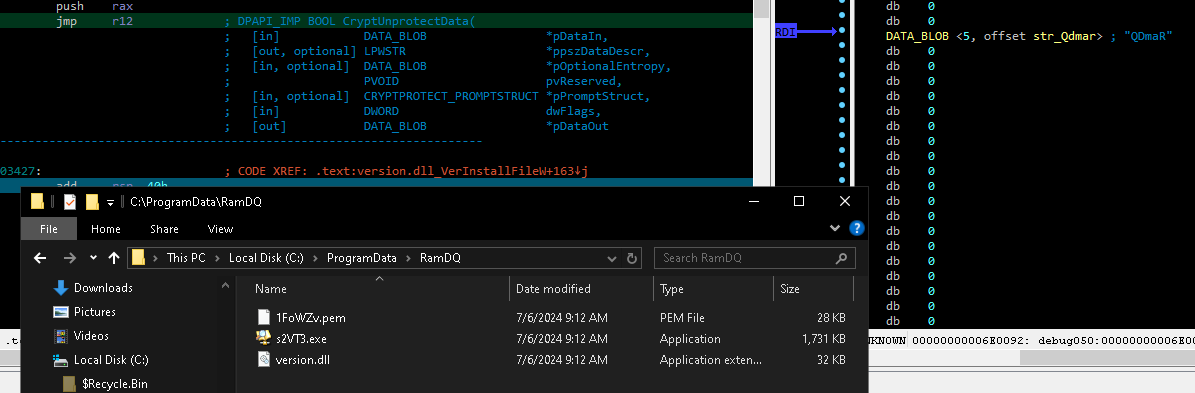
The backdoor is encrypted using the CryptUnprotectData API. This sample of WikiLoader used the folder name (RamDQ) as the decryption key for its backdoor.
Figure 15 shows the folder named RamDQ, which contained the encrypted backdoor 1FoWZv.pem and the executables (s2VT3.exe and version.dll) required to decrypt and execute the backdoor.
Conclusion
Financially motivated threat actors will continue to use WikiLoader as a loader for rent in a variety of campaigns where they require a robust, stealthy Windows loader that pays reasonable attention to OPSEC.
What remains to be seen is why threat actors have shifted from phishing to SEO poisoning to deliver WikiLoader. One hypothesis is that another initial access broker (IAB) has begun to work with WikiLoader to operationalize its delivery through SEO poisoning in recent months. Alternatively, groups that are publicly tracked using WikiLoader could have shifted to SEO poisoning from phishing after an improvement in endpoint security controls or industry reporting disrupted their operations.
While SEO poisoning is not a new technique, it continues to be an effective way to deliver a loader to an endpoint. Spoofing trusted security software is likely to assist in bypassing endpoint controls at organizations that rely on filename based allow listing.
The combination of spoofed, compromised and legitimate infrastructure leveraged by WikiLoader campaigns reinforces the malware authors attention to building an operationally secure and robust loader, with multiple C2 configurations. The authors suspect that we will likely see continued WikiLoader use throughout 2024 and beyond.
Regardless of the anti-analysis and EDR evasion techniques employed by WikiLoader, the procedures employed can be identified using many common endpoint threat hunting methods. We share a selection of four queries in our appendix that organizations can use to hunt for WikiLoader with high fidelity in endpoint data. The queries can be expanded in scope with minimal changes from XQL users to cast a wider net, or narrow in on threats that may be more applicable to an organization’s environment.
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
XQL Hunting Queries
Explorer.exe communicating with MQTT brokers
1 2 3 4 5 6 7 8 9 10 11 | // Description: Communication to known MQTT broker services from explorer.exe. Observed samples have communicated with MQTT brokers over over plaintext or encrypted TCP ports, not using websockets. Typically these are TCP 1883,8883,8884 config case_sensitive = false | dataset=xdr_data | filter event_type = ENUM.STORY | filter dst_action_external_hostname in (“broker.emqx.io”,“broker-cn.emqx.io”,“mqtt.eclipseprojects.io”,“test.mosquitto.org”,“broker.hivemq.com”,“*mqtt.one”,“*iotbind.com”) and actor_process_image_name = “explorer.exe” and action_remote_port not in (53,80,443) | fields _time, agent_hostname, agent_ip_addresses, actor_effective_username, actor_process_image_name, actor_process_image_path, dst_action_external_hostname, action_remote_port, action_remote_ip |
Common DLL sideload targets (step 8 in infection chain)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | // Description: Processes that have have written 2 PEs, one must be a .exe, and the // other a .dll with a name commonly abused for search order hijacking. config case_sensitive = false | dataset = xdr_data // Get DLL and Exe writes excluding users and program files directories. | filter event_type = ENUM.FILE and event_sub_type in (ENUM.FILE_WRITE, ENUM.FILE_CREATE_NEW) and action_file_extension IN (“dll”,“exe”) and action_file_path !~= “C:(?:Users|ProgramsFiles(s(x86))?).*” // Collate the file writes by the actor (writing) process | comp count_distinct(action_file_path) as cnt_pe_written, count_distinct(action_file_extension) as cnt_pe_extensions, count_distinct(action_file_signature_status) as cnt_pe_sig_status, values(action_file_path) as pe_written, values(action_file_signature_status) as action_file_signature_status, values(action_file_signature_vendor) as action_file_signature_vendor, values(action_file_signature_product) as action_file_signature_product, values(actor_effective_username) as username, values(action_file_sha256) as action_file_sha256, values(_time) as time, values(actor_process_command_line) as command_line, values(action_file_name) as pe_written_name, values(agent_hostname) as agent_hostname by actor_process_instance_id // Filter out those that have only written 1 Exe and 1 DLL, with a DLL using a known abused name | filter cnt_pe_written=2 and cnt_pe_extensions=2 and pe_written_name ~= “^(?:vcruntime140|vcruntime|oci|version|msfte|secur32|nw|rw32core|iphlpapi|wininet).dll” | filter pe_written_name not in (“*cortex-xdr-payload*”,“*xdrhealth.exe*”,“*winpty-agent.exe*”) |
Processes executing as GlobalProtect without a parsed Palo Alto Networks certificate.
1 2 3 4 5 6 7 8 9 10 11 | // Description: A signed process starts with GlobalProtect or PanGP in the image name, but is not signed by a known Palo Alto Networks certificate. config case_sensitive = false | dataset=xdr_data | filter event_type IN (ENUM.PROCESS) and event_sub_type = ENUM.PROCESS_START | filter (action_process_image_name contains “GlobalProtect” or action_process_image_name contains “PanGP”) and action_process_signature_vendor not in (“Palo Alto Networks”,“Palo Alto Networks (Netherlands) B.V.”,“Developer ID Application: Palo Alto Networks (PXPZ95SK77)”,“Palo Alto Networks, Inc”) and action_process_signature_status=ENUM.SIGNED | fields _time, agent_hostname, actor_effective_username, action_process_image_path , action_process_image_command_line , action_process_image_sha256, action_process_signature_status, action_process_signature_vendor, action_process_signature_product, action_process_image_sha256, actor_process_image_path , os_actor_process_command_line, causality_actor_process_command_line |
Review ZIP files with GlobalProtect naming that have Mark of the Web applied for suspicious download sources
1 2 3 4 5 6 7 8 9 10 11 | // Description: Delivery via .zip files is common, display those that were downloaded with Mark of the Web data. config case_sensitive = false | dataset=xdr_data | filter event_type=ENUM.FILE and event_sub_type IN (ENUM.FILE_OPEN, ENUM.FILE_CREATE_NEW) | filter action_file_extension=“zip” and action_file_path ~= “Downloads|Appdata” and action_file_name contains “GlobalProtect” and not action_file_name contains “GlobalProtectLogs” | fields _time, event_sub_type, agent_hostname, actor_effective_username, action_file_name, action_file_path, action_file_web_mark, action_file_sha256 , actor_process_image_name, actor_process_image_sha256 |
Indicators of Compromise
These indicators were active throughout June 2024.
Delivery URLs
- URL: hxxps://globalprotect[.]securedownload[.]today/GlobalProtect64.zip
Description: URL serving archive impersonating GlobalProtect.
- URL: hxxps://globalprojectvpn[.]com
Description: Fake GlobalProtect site that delivers fake GlobalProtect64.zip
- URL: hxxps://globalprojectvpn[.]com
Description: Fake GlobalProtect site that pulled from a Bitbucket project to deliver fake GlobalProtect64.zip
- URL: hxxps://bitbucket[.]org/bitprotect/globalproject/src/main/
Description: Bitbucket project that hosted fake GlobalProtect64.zip
WikiLoader C2 URLs
- hxxps://carniceriamartinezadria.com/wp-content/themes/twentytwentyfour/rleoec.php?id=1
- hxxps://jlholgado.com/wp-content/themes/twentytwentyfour/zca2ck.php?id=1
- hxxps://elpgtextil.com/wp-content/themes/twentytwentyfour/44snwx.php?id=1
- hxxps://arbeitsschutz-mmk.de/plugins/search/contacts/chrndi.php?id=1
- hxxps://www.estudioemm.com/wp-content/themes/twentytwelve/d4kih3.php?id=1
Description: C2 providing the decryption key to the payload of the WikiLoader sample
SHA-256 hashes for WikiLoader shellcode loader DLLs
- d4eb9a4ee389f03c402e553724015af8d5b85835828bd66b1b45131b6837802f
- 534c989d110ece8c429d2ded913933b961710726d8655b858474bc31dfed25c3
- a001642046a6e99ab2b412d96020a243a221e3819eaac94ab3251fad7d20614b
- c6c250e1cd6d5477b46871ffe17deac248d723ad45687fc54ae4fc5e3f45d91c
- f1a49cea454bac3e78ac765b247b65d00c896d84de2028892b00d4310453c665
- 2ab449666cf006125075e3ded8053cdfd318e4772d4145f0fa861f1d42cb2b08
- 1d6f76acecff63fb373b5774a3cb34b87266a4a4bbb8e3a0757d107187d280ee
- b412b2c190b8406392406d9a8e3abce91c9014950bcf835eb7d9b50d0f128cb0
- 66735d0178badf035be0e142f4fb8e23d860bfc9bbdc3e12ad1f2764de91ee9b
- edec55f87e535f869119db44e4e7302081f53dbf33a27aaf905430cedc5a78b9
- 148b29123bb0c28614858460d7a10707469fecebd6a9ff1da98a0c76a89a9819
- 0de42118dd0cd861bea13de097457ccb407aae901b14e0bec59b0abe660cdf1f
- 5576ab87eb11ca4d2944bc1c2c6a8c349e18c7ded583c1ba9bd99eff9d8ac4d7
- 551da6814a01a280afe90aa6bb238f499d98ad496c0d8472a1705540a6f422da
- 4f573ab13882efa234a79483d305b3001cb09c0a166ff94c925844b860162415
- 4f2079cd2e228a2777df45ae00714c8679531fd8ad82a66b5c1b10e800771f18
- 2add886330db1480da7314ee38428ca79af04f8c461c3bbbd68e202bb5f4c415
- 76d1a876c90ec16f44685f795e64ab84bd2d3f5a91db659c9879b3461ee104f9
- 6aa4a830aa8d89b629fe87d3d3e986042215b5bcd670417933fca854b6dd58d9
- 1c1d739f0282bfd9367e29ca81c61ed4a731e5150a836d0371e5e9d0121c9dfd
- 69a94bbed366bfd917dfd8fb6e5fd7ba52e2dbf338edd0c259654981060943c8
- 9a48f32e00877a4335206c7da45a94ca8bd46648d3a0bc88e0789dabf8139024
- c3280452e7c96253b215342f2fac14634591adf68f88bcf7dc920d5f28022cd6
- 0c44a46f1c8e46fe6b6f83ec249c95301aca1bc4765cee7bdadd021bbfd2ff66
- 2b8b3f5b692f716116a1468b8d7b273baf7a6cef0726e831cd307d2f2c7452ec
- e07787caf52dd3e7dd0da600dbd1d909f3799dcebcdc60d101baf3ea17ef1e32
- 50810e4696dd075ca23349e3e1c3a87fc7b46ab89f4b1eb093a5cfb74f84cc51
- 912cc2a3592b3b7835205d275cbf92bb66effc99cbd5cc338a223888de1b0d35
- f04715827e5453b33ba6fae8475b8c45150b27cc1361441648c46d13025283d2
- e693652763141522621f9fcd80efb30cefa363f8bd9bdc65e5ffbf9fb8d76d3b
- 8d5e185d53e81e90646d684dff7cb399973e3cde6d833e6f7431074f4362139a
- ec59616b1c80951d6597d4f25a9c031be0391151dc1073a5bece466473f0bdfe
- e7e674218a7d93595e33a092f4f519a65499651a398ca350f5a50e135e64fa41
- 78f6f94aaa72e41d64e4dc309a3553399db2b4cd0edae5653ca4b6e7839e1215
- abce298ebb4ac7bc1a5167179875afc88e7e99475bf681953e8b964237b7d7ed
- 82ec4e1a6ddf6eeb4030d6dd698f4576d0445d4d5722d5c60b0cc74ac501bb85
- 0d495a94e29faa4dfded29253322be1b2c534a56c078bea1ad8f1dc1fd23b742
SHA-256 hashes for WikiLoader backdoor
- 4044a0d7a0ed7f66efc2bd13616ec63a5722fc7a73a28fe3bda513f60ef24dd9
- c9eaaa6aee55704ce651c8b4cde7949cfa9711e05a136fa15f234d1bb2ea994c
Additional Resources
Source: Original Post