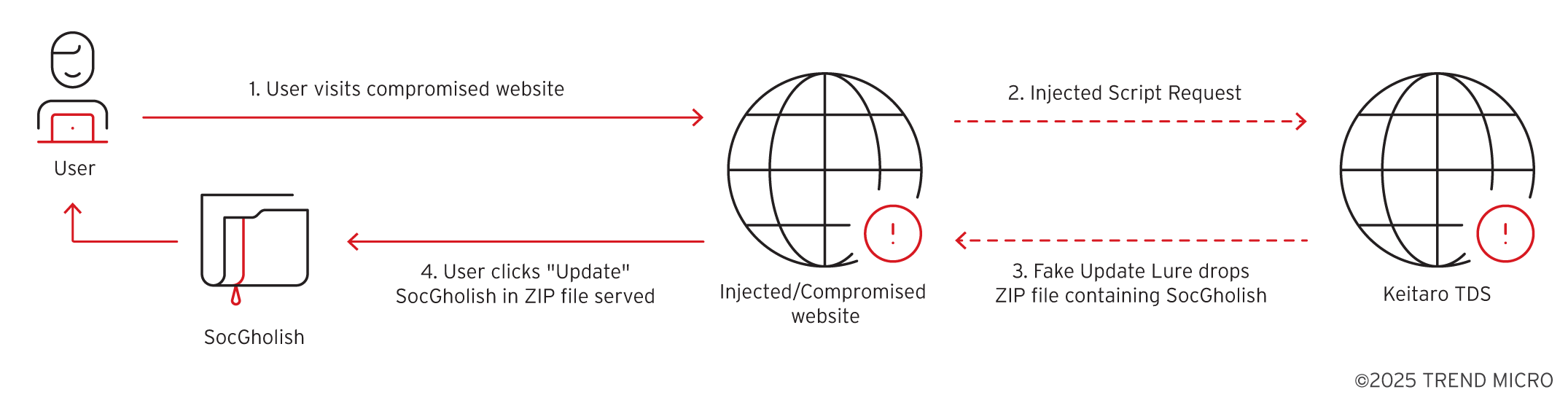
Trend Research’s analysis of SocGholish’s MaaS framework highlights its critical role in delivering RansomHub ransomware via compromised websites. Utilizing highly obfuscated JavaScript loaders, SocGholish evades detection and successfully executes malicious tasks. Notably, the framework propels initial access for ransomware attacks, mainly affecting government entities in the United States. Key tactics include website compromises, rogue TDS collaboration, and data exfiltration.
Affected: United States, Government organizations, Banking sector, Consulting industry
Affected: United States, Government organizations, Banking sector, Consulting industry
Keypoints :
- SocGholish’s MaaS framework aids in deploying RansomHub ransomware.
- It operates through highly obfuscated JavaScript loaders to avoid detection.
- The primary method of propagation is via compromised legitimate websites.
- Users are misled into downloading a malicious ZIP file through fake browser update notifications.
- Key sectors affected include government, banking, and consulting industries, primarily in the US.
- Collaboration with rogue Keitaro TDS instances is integral to SocGholish’s operation.
- The loader allows persistent access and exfiltration of sensitive data.
- Security measures include hardening endpoints and enhancing detection capabilities.
- Trend Research has been tracking SocGholish since 2018.
MITRE Techniques :
- T1608.004 – Drive-By Target: Compromised websites are injected with malicious code, hijacking user traffic to redirect users to fake updates.
- T1204.002 – Malicious File: Execution of the malicious JavaScript file relies on user interaction.
- T1059.007 – Command and Scripting Interpreter: JavaScript: The loader uses JavaScript to carry out malicious activities.
- T1059.001 – Command and Scripting Interpreter: PowerShell: PowerShell commands are executed for reconnaissance and backdoor deployment.
- T1059.006 – Command and Scripting Interpreter: Python: A Python backdoor is deployed to facilitate external connections.
- T1027.013 – Obfuscated Files or Information: Heavy code obfuscation complicates detection.
- T1070.004 – Indicator Removal on Host: File Deletion: The loader contains functions to remove evidence of its operation.
- T1006 – Direct Volume Access: Certutil.exe is used to access sensitive data stored by the SAM.
- T1041 – Exfiltration Over C2 Channel: Stolen data is exfiltrated to the command and control server.
Indicator of Compromise :
- [Domain] blackshelter[.]org
- [Domain] rednosehorse[.]com
- [Domain] newgoodfoodmarket[.]com