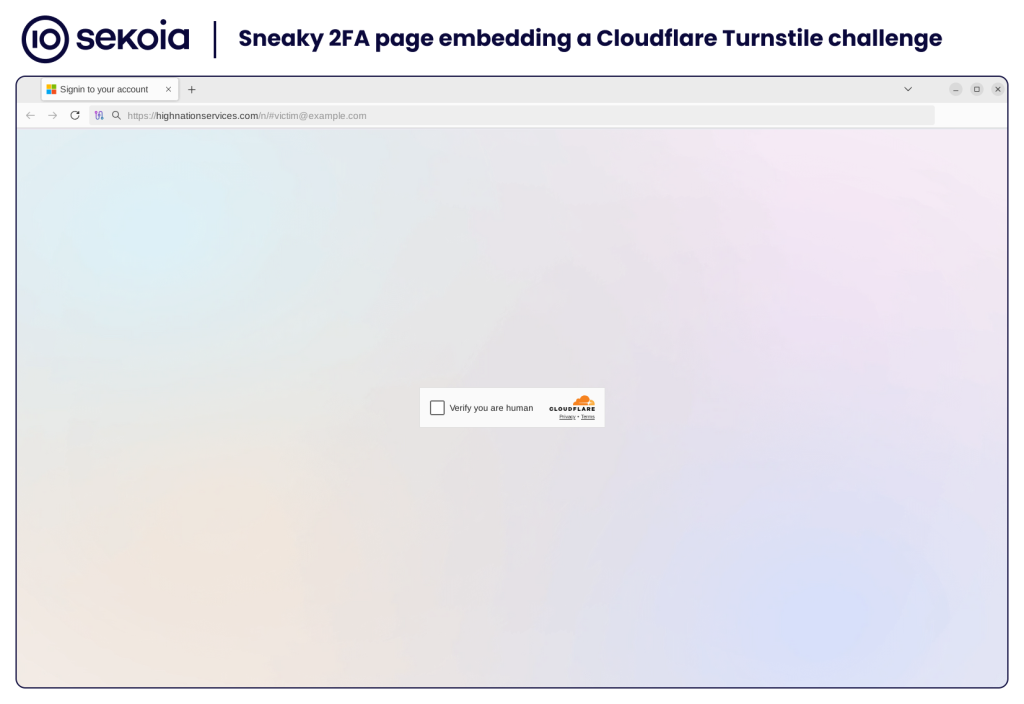
In December 2024, a new Adversary-in-the-Middle (AiTM) phishing kit known as Sneaky 2FA was identified, targeting Microsoft 365 accounts. This phishing kit, sold as Phishing-as-a-Service (PhaaS) by the cybercrime service “Sneaky Log”, utilizes sophisticated techniques including autograb functionality and anti-bot measures. The analysis reveals its operational methods, including the use of Telegram for distribution and support. Affected: Microsoft 365
Keypoints :
- Identification of Sneaky 2FA phishing kit in December 2024.
- Targeting Microsoft 365 accounts through sophisticated phishing techniques.
- Sold as Phishing-as-a-Service (PhaaS) by the cybercrime service “Sneaky Log”.
- Phishing pages utilize autograb functionality to prefill email addresses.
- Phishing URLs are generated with complex alphanumeric patterns.
- Cloudflare Turnstile and anti-debugging techniques are employed to evade detection.
- Phishing kit operations are managed through Telegram bots.
- Detection opportunities identified based on User-Agent anomalies.
- Phishing kit includes source code from W3LL Panel OV6.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Uses Microsoft API for authentication.
- T1071.002 – Application Layer Protocol: Communicates with the phishing server for credential harvesting.
- T1070.001 – Indicator Removal on Host: Utilizes obfuscation techniques to hide malicious content.
- T1070.004 – Indicator Removal on Host: Employs anti-debugging techniques to prevent analysis.
- T1071 – Application Layer Protocol: Uses Telegram for command and control communications.
Indicator of Compromise :
- [domain] sneakylog[.]store
- [ip address] 185.125.100[.]81
- [domain] highnationservices[.]com
- [domain] mysilverfox[.]com
- [domain] kagumigroup[.]id
- Check the article for all found IoCs.
Full Research: https://blog.sekoia.io/sneaky-2fa-exposing-a-new-aitm-phishing-as-a-service/
Views: 0