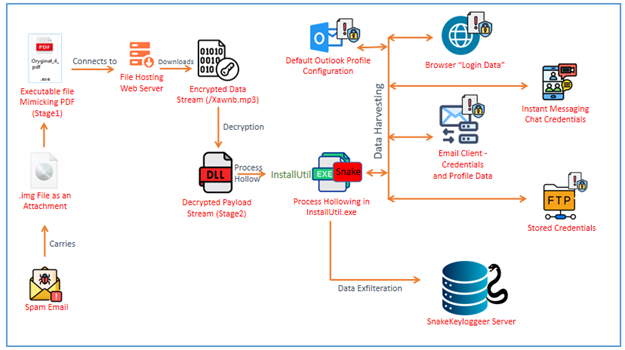
The SnakeKeylogger campaign illustrates a sophisticated credential-stealing threat targeting both individuals and businesses. Utilizing multi-stage infection techniques, it cleverly evades detection while harvesting sensitive data from various platforms. Attackers employ malicious spam emails containing disguised executable files to initiate the infection. Affected: Individuals, Businesses, Email Clients, Web Browsers, FTP Clients.
Keypoints :
- SnakeKeylogger is an advanced info-stealer malware recognized for its stealthy infection process.
- Utilizes malicious spam emails with .img attachments to deliver the payload.
- The initial executable file masquerades as a PDF to entice users to open it.
- Employs techniques like downloading and decrypting payloads to avoid detection.
- Infects systems by injecting malicious code into legitimate processes.
- Targets numerous web browsers and email clients to extract saved credentials.
- Accesses sensitive data including Outlook profiles and stored FTP details.
- Malware is distributed through an Apache server for increased operational efficiency.
MITRE Techniques :
- Initial Access (TA0001) – T1566.001: Spearphishing Attachment via malicious spam emails containing infected .img files.
- Execution (TA0002) – T1204.002: Malicious File Execution through the disguised executable.
- Defense Evasion (TA0005) – T1140: Deobfuscate/Decode Files or Information to stealthily execute payloads.
- Defense Evasion (TA0005) – T1027: Obfuscated Files or Information to hinder detection.
- Defense Evasion (TA0005) – T1218.004: System Binary Proxy Execution using InstallUtil for process injection.
- Credential Access (TA0006) – T1555: Credentials from Password Stores, targeting browsers and email clients.
- Discovery (TA0007) – T1083: File and Directory Discovery to access stored passwords and data.
- Collection (TA0009) – T1114.002: Email Collection via Client Application, specifically targeting Outlook profiles.
- Command and Control (TA0011) – T1071.001: Application Layer Protocol for data exfiltration using web protocols.
Indicator of Compromise :
- [File Hash] 851A5FFAC3EE2DA08557108239F90FABFD7634082A916C3BD8C94C8493FC83E29AD19A4E2D41E214D7BF04F74151DDBD07B21AAE60698970EBDC2E854B3ACFED
- [URL] hxxp://103.72.56.30/PHANTOM/
Full Story: https://www.seqrite.com/blog/snakekeylogger-a-multistage-info-stealer-malware-campaign/