Summary: G DATA security researchers have uncovered a sophisticated malware infection chain targeting First Ukrainian International Bank, centering on the enhanced SmokeLoader and its intermediary, Emmenhtal Loader. The attack utilizes social engineering, living off the land binaries, and advanced evasion techniques to deploy multiple malware stages stealthily without detection. This analysis highlights the persistent evolution of malware tactics, including the use of archive-based evasion and fileless execution methods.
Affected: First Ukrainian International Bank (pumb[.]ua)
Keypoints :
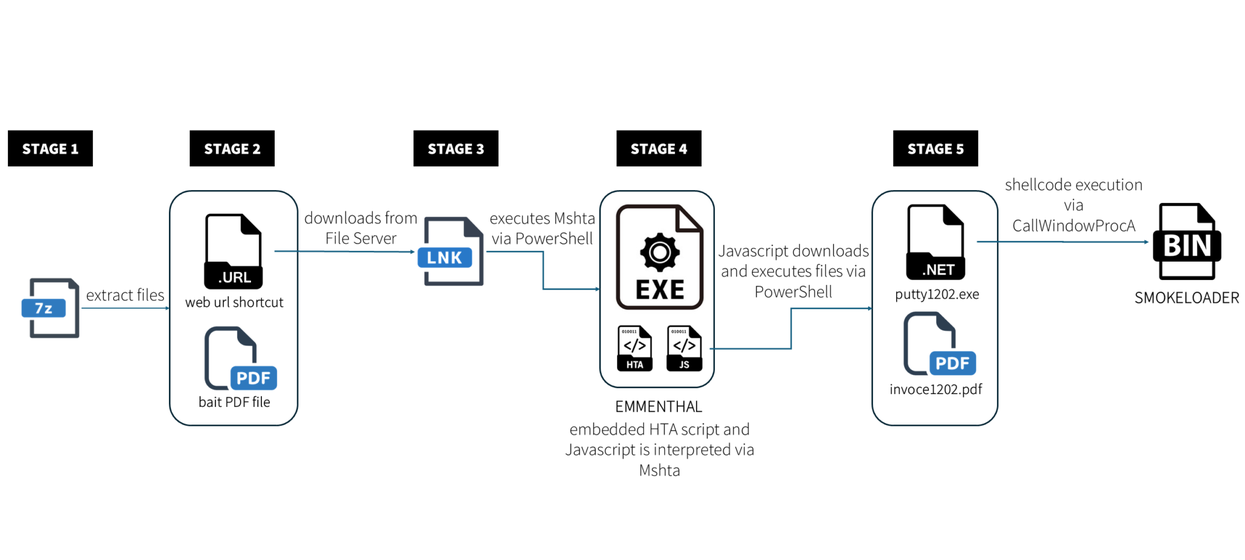
- The campaign begins with a phishing email featuring an attachment that appears to be a payment instruction.
- The attacker uses archive-based evasion techniques, a modified DCCW.exe, and PowerShell to maintain stealth and execute malicious payloads.
- SmokeLoader is deployed as the final stage, known for its capabilities in delivering secondary payloads and stealing credentials, showcasing a shift towards more sophisticated malware tools.
Source: https://securityonline.info/smokeloader-malware-deployed-in-stealthy-campaign-targeting-major-banks/