By Securonix Threat Research: D. Iuzvyk, T. Peck, O. Kolesnikov
tldr: In this article, we take a deeper dive into a prevalent “DLL sideloading” attack technique we’ve been observing in real-world attacks, including many of those we discovered, to understand its variations, how it works, and how we can detect it.

DLL sideloading: an overview
In Windows operating systems, Dynamic Link Library (DLL) files are simple binary files which contain common code which can be used by other applications simultaneously. DLL sideloading is a known technique often leveraged by threat actors which exploits the way Windows applications load DLLs. This technique falls under the DLL hijacking category, which consists of several methods that attackers can use to abuse these library files.
DLL Search order hijacking (T1574.001) is one of the most common methods of DLL sideloading that occurs when an attacker places a malicious DLL with the same name as a legitimate DLL in a location that is searched before arriving at the legitimate DLL’s path. When the application runs, it subsequently loads the attacker’s DLL in place of the legitimate one, executing the malicious code.
For example, Windows contains many DLL files in C:WindowsSystem32 which are used by many Windows and third party applications. If a third party application is vulnerable to DLL sideloading, an attacker could create their own malicious DLL named after the same in System32, and place it next to the vulnerable application’s executable. When the application is executed, rather than loading the DLL file in System32, the dropped malicious DLL (with the same name but in the executable’s folder) is executed first rather than the legitimate DLL.
This technique takes advantage of the way in which libraries (DLL) are loaded from executables (EXE). By default, inside the executable, if no path is specified for the DLL, the application will first load the target DLL in its own local directory. Occasionally, programmers will specify just the name of the library versus its entire path. For example, specifying simply “dwmapi.dll” versus “C:WindowsSystem32dwmapi.dll” creates a DLL sideloading search order hijacking vulnerability. Attackers can exploit this behavior by mimicking the names of legitimate DLLs expected by genuine applications by dropping a malicious DLL named the same as one found in a legitimate directory, so the malicious DLL is loaded first.
Since these applications are often signed and trusted, the malicious activity initiated by the sideloaded DLL can bypass security software that relies on signature-based detection mechanisms. This evasion tactic is particularly effective because it exploits the trust relationship between the software and its environment, making detection challenging without detailed endpoint telemetry.
The use of DLL sideloading in modern attack chains illustrates its effectiveness in evading detection and maintaining persistence. Practical examples in cybersecurity incidents reveal how sophisticated threat actors, including state-sponsored groups and cybercriminal syndicates, have adopted DLL sideloading to deploy various types of malware including information stealers, backdoors and even ransomware.
DLL sideloading: practical examples
To highlight the prevalence of this technique, let’s walk through a few practical examples of real-world use cases where DLL files were used in sideloading attacks.
Example1: SEO#LURKER
You don’t have to look far to find modern malware attack chains or campaigns leveraging this technique. The Securonix Threat Research team has recently published several campaigns including SEO#LURKER which used several DLL sideloading techniques.
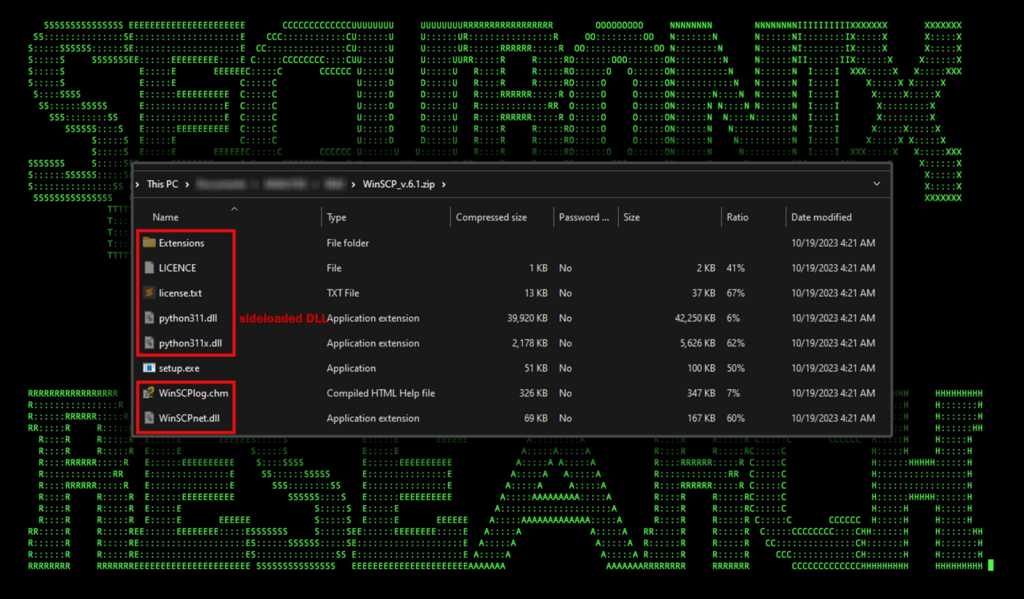
Figure 1: SEO#LURKER DLL sideload using Python Windows binaries
If you recall from the SEO#LURKER campaign, the attackers renamed the legitimate pythonw.exe to setup.exe and executed it. The legitimate (and digitally signed) process, sideloaded the malicious python311.dll file contained inside the same directory.
The entire campaign was designed around malvertising and luring the victim to install malicious software masquerading as WinSCP. The clever attack chain sideloaded the malicious DLL file as well as downloaded and executed the legitimate WinSCP installer.
Example 2: PlugX malware
In a recent report published by SophosLabs, threat actors were observed using PlugX malware to infect systems all over the world. PlugX is a USB worm which functions as a RAT. Its primary method of code execution relies on users running an executable which sideloads a malicious DLL.
The legitimate application “AvastSvc.exe” is susceptible to DLL sideloading “wsc.dll” which normally exists in the AVAST software install directory.
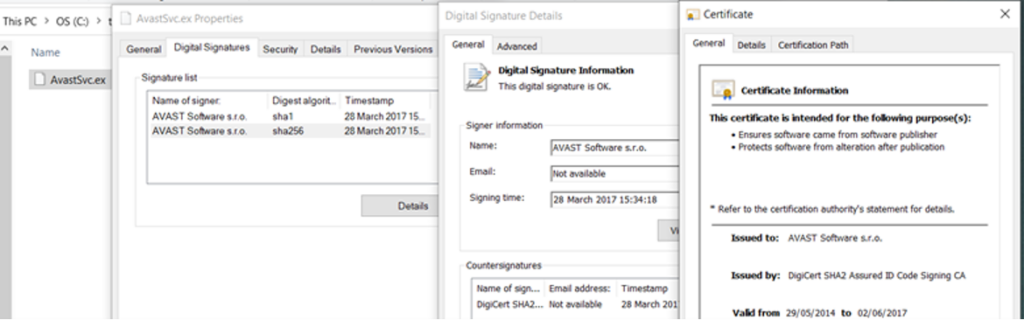
Figure 2: AvastSvc.exe file properties (image credit: Sophos, Ltd. [news.sophos.com])
Once the process is executed, the malicious DLL file is loaded into memory and executed which kicks off further stages of the PlugX attack chain.
Example 3: DarkGate malware
TrendMicro recently published research highlighting DLL sideloading as a primary method of malware delivery for the DarkGate malware. The threat actors exploited CVE-2024-21412 by using phishing campaigns distributing PDFs with links to compromised sites.
These sites hosted fake Microsoft software installers (.MSI) masquerading as legitimate applications but contained a sideloaded DLL to decrypt and deploy the main DarkGate malware payload.
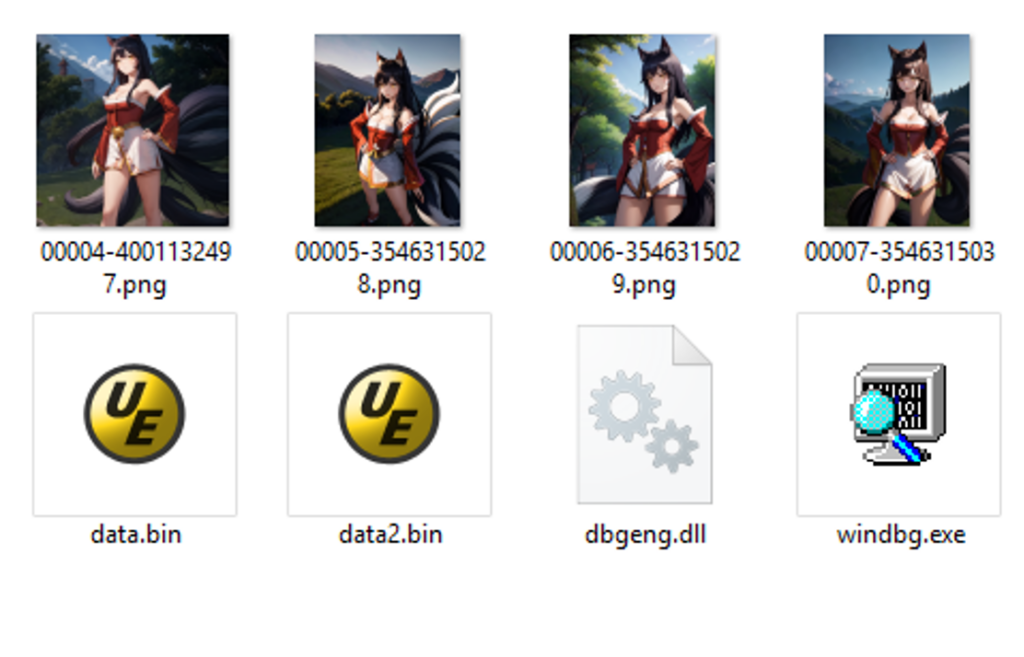
Figure 3: DarkGate DLL sideloading of dbgeng.dll (image credit: Splunk [splunk.com])
Researchers at Splunk also identified DarkGate using DLL sideloading techniques, this time using the legitimate “Wndbg.exe” process to sideload and execute the malicious code in “dbgeng.dll”, which similar to TrendMicro’s analysis, is used to decode the contents of a .bin file to run the newly generated payload.
The list continues…
Finally, here are some other quick examples of DLL sideloading being used in the wild. On top of these there are many more examples, more of which are being discovered every day.
Stately Taurus campaign:
DLL used: 1. KeyScramblerIE.dll, 2. EACore.dll
Target application: 1. Talking_Points_for_China.exe ,2. EACoreServer.exe
Chinese threat actors used a double malicious DLL sideloading campaign which featured two digitally signed binaries to load malicious code from DLLs.
Qakbot malware:
DLL used: WindowsCodecs.dll
Target application: calc.exe
This technique allowed the malware to inject the final Qakbot payload into the explorer.exe process
Farseer malware:
DLL used: sys.dll
Target application: Bscmake.exe
Farseer was observed executing through a VBS script which in turn executes bscmake.exe, while using custom encryption for its configuration data.
Dragon Breath campaign:
DLL Used: UNITYPLAYER.dll
Target Application: XLGames.exe (renamed to XLGameUpdate.exe)
The sideloading process involved replacing UNITYPLAYER.dll with a malicious variant to decrypt and execute the payload.
NetWire and Remcos:
DLL Used: libcrypto-1_1.dll
Target Application: openvpn-gui.exe
The campaign delivered RATs by sideloading the malicious DLL to the OpenVPN client.
REvil ransomware:
DLL used: mpsvc.dll
Target application: MsMpEng.exe (Windows Defender)
In a supply chain attack, REvil used this sideloading technique to gain initial access through compromised software, which provided the ability to load the malicious DLL.
Mustang Panda loading PlugX:
DLL used: hex.dll
Target application: update.exe (part of Adobe Reader)
This cyber-espionage group targeted various organizations with a revised version of the PlugX malware, all of which used DLL sideloading techniques.
QuasarRAT campaign
DLL used: MsCtfMonitor.dll
Target application: ctfmon.exe (renamed to eBill-997358806.exe)
This campaign featured a dual DLL sideloading attack chain by initially using ctfmon.exe to load a malicious DLL, which then releases both a legitimate calc.exe file and another malicious DLL
Given the popularity of DLL sideloading with malware and threat actors today, the Hijack Libs open project seeks to categorize the binary files and corresponding DLL files which have been used in the past. Today, there are over 388 currently listed with new entries being added regularly.
Practical example: TCPView
In this example, we’ll use an currently undocumented DLL sideload which leverages DLL search order hijacking (MITRE: ) to trick the legitimate Sysinternals tool TCPView to sideload dwmapi.dll. Typically, dwmapi.dll resides in C:WindowsSystem32. However, if we build our own malicious dwmapi.dll file and modify the import functions so that the TCPView application doesn’t experience errors upon execution, we should be able to get the TCPView application to load and execute the malicious payload.
First, let’s identify the target import functions. For this we can use the dumpbin.exe application which is packaged with Visual studio. Using the /exports flag, and then specifying our victim DLL, we can discover all ordinals, and function names associated with dwmapi.dll
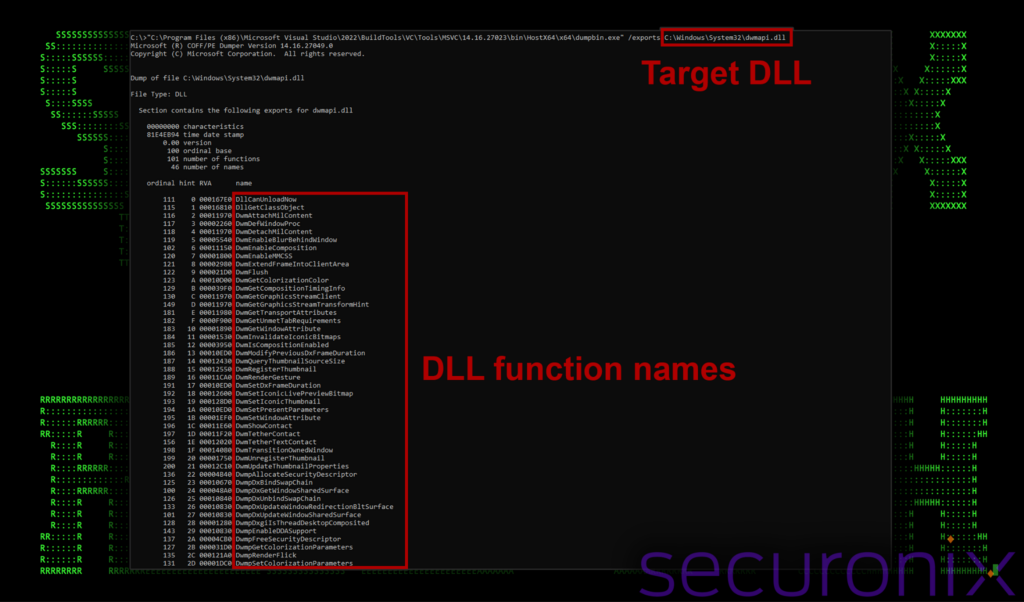
Figure 4: Using dumpbin.exe to analyze DLL import functions
This is critical data as if we used any hastily generated DLL, say from Meterpreter and renamed it to dwmapi.dll, it would likely crash the TCPView application as the application would fail to retrieve code from the DLL. This is because the expected import functions would not exist in our malicious sample.
To overcome this we can build our own malicious DLL using one of many samples that exist online. The CSharp code used to build the DLL contains “stubs” or pointers which we can specify inside the CSharp application to have it accept all of the DLL functions we enumerated from the legitimate dwmapi.dll file. The newly created stubs (or import functions) each call the same LoadLibraryEx function to load the DLL into the TCPView executable’s memory at runtime.
The code injected into memory is shellcode generated by Sliver. If all goes well, we should get our Sliver implant to execute in memory after the TCPView executable loads our malicious version of dwmapi.dll.
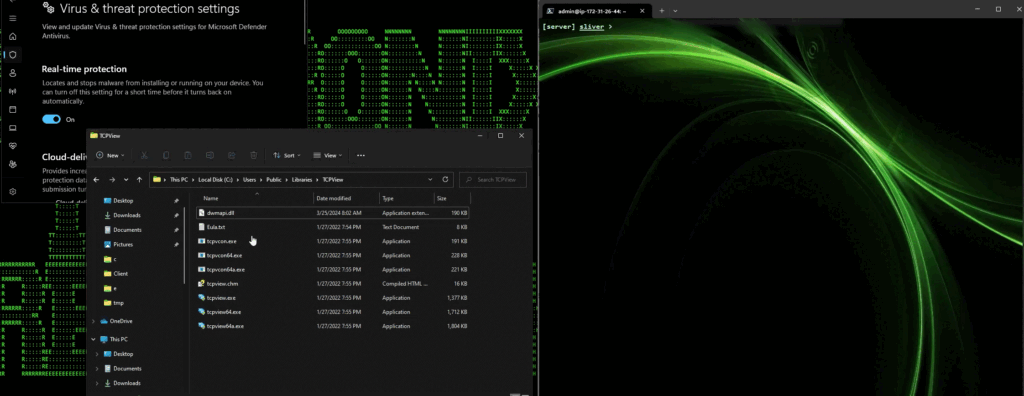
Figure 5: Sideloading dwmapi.dll from tcpview64.exe
As you can see in the figure above, our Sliver session on the left received a session from our custom-built dwmapi.dll. The DLL was successfully loaded and its code was executed through tcpview64.exe. Not only that, but this was also on a fully patched Windows 11 installation with Windows Defender enabled and running in the background.
Detecting DLL sideloading
Next let’s review some of the gathered logs after tcpview64.exe sideloaded dwmapi.dll. Probably the easiest method for catching any form of DLL sideloading is using a log source which is designed to monitor DLL loading such as EDR logs or Sysmon EVID 7 (image loaded).
Detecting DLL sideloading requires monitoring for unusual or unexpected behavior related to DLL loading processes, especially when contrasting normal system behavior to something out of the ordinary. While Sysmon Event ID 7 is indeed one of the most valuable sources for detecting DLL sideloading by tracking the loading of DLLs into processes, there are several other log sources and events that can complement this detection:
Sysmon Event ID 1 or Windows Security Event ID 4688 – Useful for understanding the context around process launches, which can be critical in identifying suspicious behavior that might precede or accompany DLL sideloading, for example, unusual parent/child relationships. In the case of this example, tcpview64.exe spawning cmd.exe.
Antivirus and endpoint detection and response (EDR) logs – Enterprise antivirus and EDR solutions often include heuristic and behavior-based detection mechanisms that can identify patterns of activity commonly associated with DLL sideloading, even if specific event IDs aren’t triggered. Data from these sources can be quite robust and include fantastic telemetry for analyzing unusual patterns surrounding process-library interactions.
Windows application logs – Since DLL sideloading relies on the misuse of an application’s main intent, it’s possible that spikes in application errors may occur. Additionally, some applications that log their own interactions with DLLs can provide additional context or confirmation of DLL sideloading.
Since we know that dwmapi.dll is supposed to reside in C:WindowsSystem32, we can put together a small policy which triggers when the DLL is loaded from anything but its typical directory:
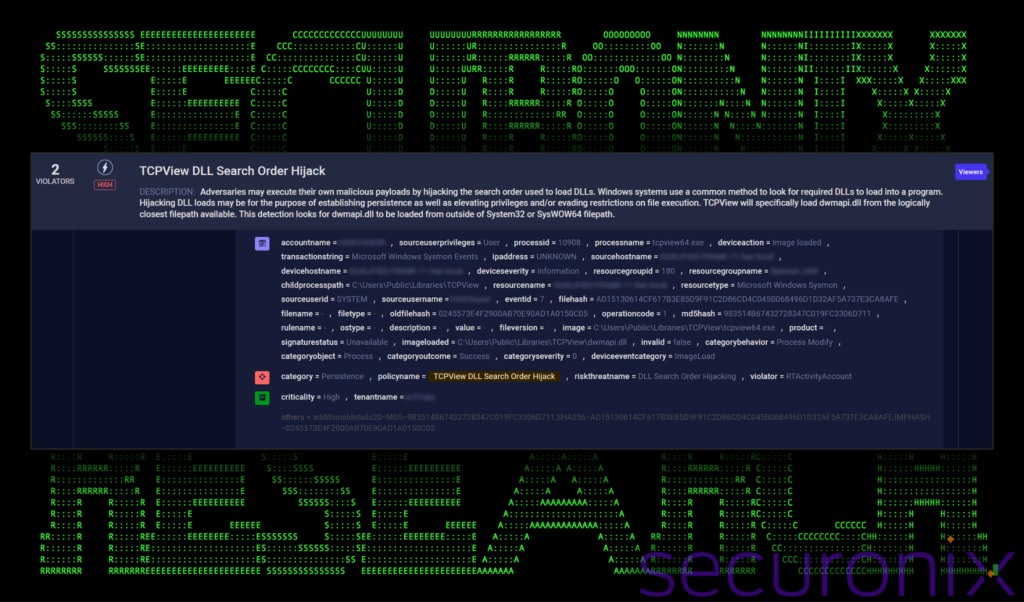
Figure 6: Detecting DLL sideloading in Securonix
The figure above was taken from the video demonstration (figure 5) and highlights an example policy violation in Securonix where dwmapi.dll was loaded by an application from outside its normal directory. In this case, it was loaded from the C:UsersPublic directory, which is a typical staging directory for malware.
Wrapping up…
DLL sideloading is probably one of the most tried and true tactics that threat actors are using to bypass detections and execute malware, especially since it has a solid track record of bypassing EDR detections. While it’s been in their toolkits over over 15 years, there is no sign of slowing down and it’s important for organizations to take advantage of detection opportunities which can lend a hand in detecting these types of attack chains.
Relevant provisional Securonix detections
- EDR-ALL-226-RU
- EDR-ALL-924-RU
- EDR-ALL-958-RU
- EDR-ALL-1027-RU
- EDR-ALL-1143-RU
- EDR-ALL-1262-RU
- EDR-ALL-1271-RU
Relevant threat hunting query to detect potential DLL sideloading
index = activity AND rg_functionality = "Endpoint Management Systems" AND baseeventid = "7" AND filename IN (aclui.dll, activeds.dll, adsldpc.dll, aepic.dll, amsi.dll, apphelp.dll, applicationframe.dll, appvpolicy.dll, appxalluserstore.dll, appxdeploymentclient.dll, archiveint.dll, atl.dll, audioses.dll, auditpolcore.dll, authfwcfg.dll, authz.dll, avrt.dll, batmeter.dll, bcd.dll, bcp47langs.dll, bcp47mrm.dll, bcrypt.dll, bderepair.dll, bootmenuux.dll, bootux.dll, cabinet.dll, cabview.dll, certcli.dll, certenroll.dll, cldapi.dll, clipc.dll, clusapi.dll, cmpbk32.dll, cmutil.dll, coloradapterclient.dll, colorui.dll, comdlg32.dll, configmanager2.dll, connect.dll, coredplus.dll, coremessaging.dll, coreuicomponents.dll, credui.dll, cryptbase.dll, cryptdll.dll, cryptsp.dll, cryptui.dll, cryptxml.dll, cscapi.dll, cscobj.dll, cscui.dll, d2d1.dll, d3d10.dll, d3d10_1.dll, d3d10_1core.dll, d3d10core.dll, d3d10warp.dll, d3d11.dll, d3d12.dll, d3d9.dll, d3dcompiler_47.dll, dataexchange.dll, davclnt.dll, dbgcore.dll, dbghelp.dll, dcntel.dll, dcomp.dll, defragproxy.dll, desktopshellext.dll, deviceassociation.dll, devicecredential.dll, devicepairing.dll, devobj.dll, devrtl.dll, dhcpcmonitor.dll, dhcpcsvc.dll, dhcpcsvc6.dll, directmanipulation.dll, dismapi.dll, dismcore.dll, dmcfgutils.dll, dmcmnutils.dll, dmcommandlineutils.dll, dmenrollengine.dll, dmenterprisediagnostics.dll, dmiso8601utils.dll, dmoleaututils.dll, dmprocessxmlfiltered.dll, dmpushproxy.dll, dmxmlhelputils.dll, dnsapi.dll, dot3api.dll, dot3cfg.dll, dpx.dll, drprov.dll, drvstore.dll, dsclient.dll, dsparse.dll, dsprop.dll, dsreg.dll, dsrole.dll, dui70.dll, duser.dll, dusmapi.dll, dwmapi.dll, dwmcore.dll, dwrite.dll, dxcore.dll, dxgi.dll, dxva2.dll, dynamoapi.dll, eappcfg.dll, eappprxy.dll, edgeiso.dll, edputil.dll, efsadu.dll, efsutil.dll, esent.dll, execmodelproxy.dll, explorerframe.dll, fastprox.dll, faultrep.dll, fddevquery.dll, feclient.dll, fhcfg.dll, fhsvcctl.dll, firewallapi.dll, flightsettings.dll, fltlib.dll, framedynos.dll, fveapi.dll, fveskybackup.dll, fvewiz.dll, fwbase.dll, fwcfg.dll, fwpolicyiomgr.dll, fwpuclnt.dll, fxsapi.dll, fxsst.dll, fxstiff.dll, getuname.dll, gpapi.dll, hha.dll, hid.dll, hnetmon.dll, httpapi.dll, icmp.dll, idstore.dll, ieadvpack.dll, iedkcs32.dll, iertutil.dll, ifmon.dll, ifsutil.dll, inproclogger.dll, iphlpapi.dll, iri.dll, iscsidsc.dll, iscsium.dll, isv.exe_rsaenh.dll, iumbase.dll, iumsdk.dll, iviewers.dll, joinutil.dll, kdstub.dll, ksuser.dll, ktmw32.dll, licensemanagerapi.dll, licensingdiagspp.dll, linkinfo.dll, loadperf.dll, lockhostingframework.dll, logoncli.dll, logoncontroller.dll, lpksetupproxyserv.dll, lrwizdll.dll, magnification.dll, maintenanceui.dll, mapistub.dll, mbaexmlparser.dll, mdmdiagnostics.dll, mfc42u.dll, mfcore.dll, mfplat.dll, mi.dll, midimap.dll, mintdh.dll, miutils.dll, mlang.dll, mmdevapi.dll, mobilenetworking.dll, mpclient.dll, mpr.dll, mprapi.dll, mpsvc.dll, mrmcorer.dll, msacm32.dll, mscms.dll, mscoree.dll, msctf.dll, msctfmonitor.dll, msdrm.dll, msdtctm.dll, msftedit.dll, msi.dll, msiso.dll, mstracer.dll, msutb.dll, msvcp110_win.dll, mswb7.dll, mswsock.dll, msxml3.dll, mtxclu.dll, napinsp.dll, ncrypt.dll, ndfapi.dll, netapi32.dll, netid.dll, netiohlp.dll, netjoin.dll, netplwiz.dll, netprofm.dll, netprovfw.dll, netsetupapi.dll, netshell.dll, nettrace.dll, netutils.dll, networkexplorer.dll, newdev.dll, ninput.dll, nlaapi.dll, nlansp_c.dll, npmproxy.dll, nshhttp.dll, nshipsec.dll, nshwfp.dll, ntdsapi.dll, ntlanman.dll, ntlmshared.dll, ntmarta.dll, ntshrui.dll, oci.dll, oleacc.dll, omadmapi.dll, onex.dll, opcservices.dll, osbaseln.dll, osksupport.dll, osuninst.dll, outllib.dll, p2p.dll, p2pnetsh.dll, p9np.dll, pcaui.dll, pdh.dll, peerdistsh.dll, pkeyhelper.dll, pla.dll, playsndsrv.dll, pnrpnsp.dll, policymanager.dll, polstore.dll, powrprof.dll, printui.dll, prntvpt.dll, profapi.dll, propsys.dll, proximitycommon.dll, proximityservicepal.dll, prvdmofcomp.dll, puiapi.dll, radcui.dll, rasapi32.dll, rasdlg.dll, rasgcw.dll, rasman.dll, rasmontr.dll, reagent.dll, regapi.dll, reseteng.dll, resetengine.dll, resutils.dll, rmclient.dll, rpcnsh.dll, rsaenh.dll, rtutils.dll, rtworkq.dll, samcli.dll, samlib.dll, sapi_onecore.dll, sas.dll, scansetting.dll, scecli.dll, schedcli.dll, secur32.dll, security.dll, shell32.dll, slc.dll, snmpapi.dll, spectrumsyncclient.dll, spp.dll, sppc.dll, sppcext.dll, srclient.dll, srcore.dll, srmtrace.dll, srpapi.dll, srvcli.dll, ssp.exe_rsaenh.dll, ssp_isv.exe_rsaenh.dll, sspicli.dll, ssshim.dll, staterepository.core.dll, structuredquery.dll, sxshared.dll, systemsettingsthresholdadminflowui.dll, tapi32.dll, tbs.dll, tdh.dll, timesync.dll, tpmcoreprovisioning.dll, tquery.dll, tsworkspace.dll, ttdrecord.dll, twext.dll, twinapi.dll, twinui.appcore.dll, uianimation.dll, uiautomationcore.dll, uireng.dll, uiribbon.dll, umpdc.dll, unattend.dll, updatepolicy.dll, upshared.dll, urlmon.dll, userenv.dll, utildll.dll, uxinit.dll, uxtheme.dll, vaultcli.dll, vdsutil.dll, version.dll, virtdisk.dll, vssapi.dll, vsstrace.dll, wbemprox.dll, wbemsvc.dll, wcmapi.dll, wcnnetsh.dll, wdi.dll, wdscore.dll, webservices.dll, wecapi.dll, wer.dll, wevtapi.dll, whhelper.dll, wimgapi.dll, winbio.dll, winbrand.dll, windows.storage.dll, windows.storage.search.dll, windows.ui.immersive.dll, windowscodecs.dll, windowscodecsext.dll, windowsperformancerecordercontrol.dll, windowsudk.shellcommon.dll, winhttp.dll, wininet.dll, winipsec.dll, winmde.dll, winmm.dll, winnsi.dll, winrnr.dll, winscard.dll, winsqlite3.dll, winsta.dll, winsync.dll, wkscli.dll, wlanapi.dll, wlancfg.dll, wlbsctrl.dll, wldp.dll, wlidprov.dll, wmiclnt.dll, wmidcom.dll, wmiutils.dll, wmpdui.dll, wmsgapi.dll, wofutil.dll, wpdshext.dll, wscapi.dll, wshbth.dll, wshelper.dll, wsmsvc.dll, wtsapi32.dll, wwancfg.dll, wwapi.dll, xmllite.dll, xolehlp.dll, xpsservices.dll, xwizards.dll, xwtpw32.dll) AND (resourcecustomfield5 NOT CONTAINS "windowssystem32" OR resourcecustomfield5 NOT CONTAINS "windowssyswow64")
References
- THREAT ANALYSIS REPORT: DLL Side-Loading Widely (Ab)Used
https://www.cybereason.com/blog/threat-analysis-report-dll-side-loading-widely-abused - New SEO#LURKER Attack Campaign: Threat Actors Use SEO Poisoning and Fake Google Ads to Lure Victims Into Installing Malware
https://www.securonix.com/blog/seolurker-attack-campaign-uses-seo-poisoning-fake-google-ads-to-install-malware/ - Hijack Libs: wsc.dll
https://hijacklibs.net/entries/3rd_party/avast/wsc.html - A border-hopping PlugX USB worm takes its act on the road
https://news.sophos.com/en-us/2023/03/09/border-hopping-plugx-usb-worm/ - CVE-2024-21412: DarkGate Operators Exploit Microsoft Windows SmartScreen Bypass in Zero-Day Campaign
https://www.trendmicro.com/en_us/research/24/c/cve-2024-21412–darkgate-operators-exploit-microsoft-windows-sma.html - Enter The Gates: An Analysis of the DarkGate AutoIt Loader
https://www.splunk.com/en_us/blog/security/enter-the-gates-an-analysis-of-the-darkgate-autoit-loader.html - New Qakbot Malware Strain Replaces Windows Calculator DLL to Infected PCs
https://www.bitdefender.com/blog/hotforsecurity/new-qakbot-malware-strain-replaces-windows-calculator-dll-to-infected-pcs/ - Farseer: Previously Unknown Malware Family bolsters the Chinese armory
https://unit42.paloaltonetworks.com/farseer-previously-unknown-malware-family-bolsters-the-chinese-armoury/ - A doubled “Dragon Breath” adds new air to DLL sideloading attacks
https://news.sophos.com/en-us/2023/05/03/doubled-dll-sideloading-dragon-breath/ - THREAT ANALYSIS REPORT: DLL Side-Loading Widely (Ab)Used
https://www.cybereason.com/blog/threat-analysis-report-dll-side-loading-widely-abused - THREAT ANALYSIS REPORT: DLL Side-Loading Widely (Ab)Usedhttps://www.cybereason.com/blog/threat-analysis-report-dll-side-loading-widely-abused
- Double Trouble: QuasarRAT’s Dual DLL Sideloading in Focus
https://www.uptycs.com/blog/quasar-rat - Evading EDR by DLL Sideloading in C#
https://globetech.biz/index.php/2023/05/19/evading-edr-by-dll-sideloading-in-csharp/ - Improving Your Blue Team’s Ability To Detect Threats With Enhanced Siem Telemetry
https://www.securonix.com/blog/improving-blue-team-threat-detection-with-enhanced-siem-telemetry/ - ASEAN Entities in the Spotlight: Chinese APT Group Targeting https://unit42.paloaltonetworks.com/chinese-apts-target-asean-entities/
Source: Original Post