Short Summary
The Summer Intelligence Insights report by Securonix Threat Labs highlights significant cyber threats identified over the last three months, including phishing campaigns, cyber-espionage efforts, and ransomware attacks. The report emphasizes the importance of monitoring tactics, techniques, and procedures (TTPs) used by threat actors, along with recommendations for protective measures to mitigate risks.
Key Points
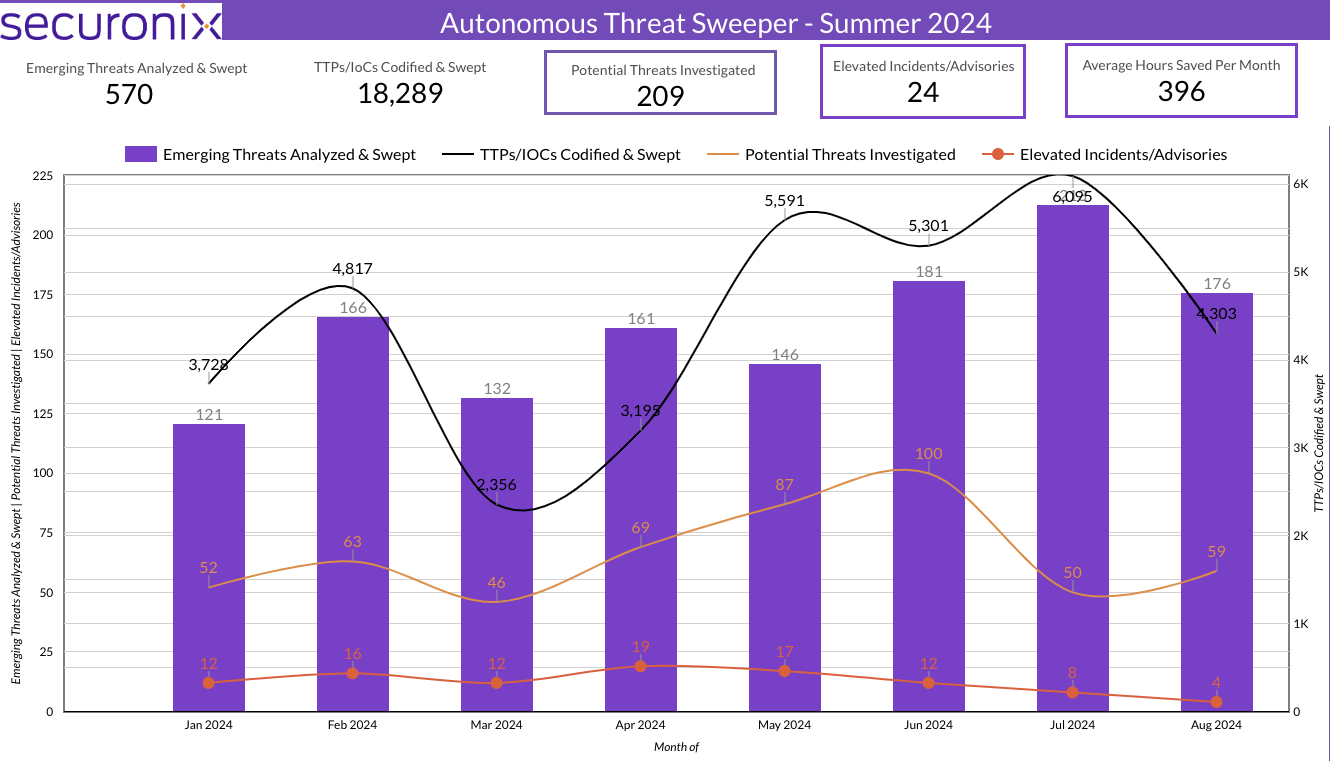
- Securonix identified 18,289 TTPs and IoCs, 570 emerging threats, and investigated 209 potential threats.
- PHANTOM#SPIKE phishing campaign targets individuals in Pakistan using military-themed tactics.
- Cyber-espionage efforts by UTA0137 targeting Indian government entities with DISGOMOJI malware.
- UNC5537 exploits customer credentials in Snowflake data breaches, highlighting the need for improved credential security.
- CrowdStrike faced a significant outage due to a flawed update, leading to phishing scams and malware distribution.
- New threat actors like CRYSTALRAY and TAG-100 are conducting large-scale cyber-spying campaigns.
- Iranian threat actors have increased ransomware and espionage activities, particularly targeting sensitive sectors.
- Citrine Sleet, linked to North Korea, is exploiting a zero-day vulnerability in Chromium browsers.
MITRE ATT&CK TTPs – created by AI
- Monitor for suspicious PowerShell and command line activity – TTP: T1059.001
- Monitor for execution of Zenity Utility for Social Engineering – TTP: T1203
- Monitor for GravityRAT Infection on Windows – TTP: T1071.001
- Monitor for suspicious login attempts via GravityAdmin – TTP: T1078
- Monitor for failed login activity – TTP: T1075
- Monitor for password spraying – TTP: T1110
- Monitor for DLL sideloading and DLL search order hijacking – TTP: T1073
- Monitor for unusual email patterns – TTP: T1204
- Monitor for credential dumping tools – TTP: T1003
- Monitor for indicators of kernel tampering – TTP: T1066
Authors: Dheeraj Kumar, and Sina Chehreghani
The Summer Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in last 3 months. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
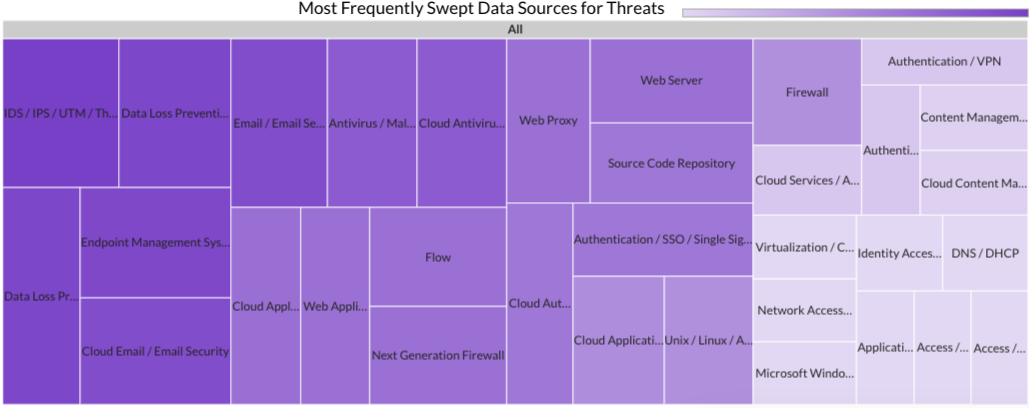
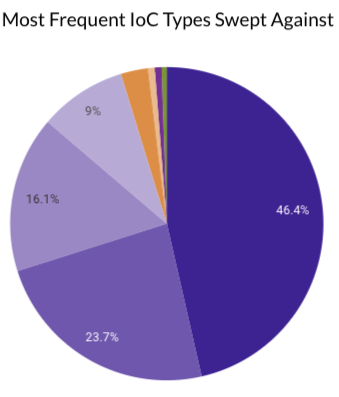
During Summer 2024, Securonix Autonomous Threat Sweeper identified and analyzed 18,289 TTPs and IoCs, 570 emerging threats, investigated 209 potential threats, and elevated 24 threat incidents. The top data sources swept against include Cloud Application Audit, Cloud Content Management, Cloud Antivirus/Malware/EDR, Data Loss Prevention, and Email/Email Security.
PHANTOM#SPIKE attack campaign
(Originally published in Summer 2024)
The Securonix Threat Research team has discovered a new phishing campaign targeting individuals in Pakistan. This campaign uses a custom backdoor called PHANTOM#SPIKE. Military-themed phishing tactics have been used by the perpetrators behind this operation who are leveraging documents linked to the International Military-Technical Forum Army 2024, a genuine event organized by the Russian Ministry of Defense that will take place in Moscow in mid-August 2024.
The threat actors employed ZIP files containing password-protected payload packages which they used to gain remote access to target devices through to avoid detection. The key feature of this campaign is its simplicity and use of straightforward payloads.
The victims receive emails with ZIP archives claiming to contain meeting minutes from the forum. Once opened, the archive has a harmless Microsoft Compiled HTML Help (CHM) file inside it. When an individual opens this file and clicks on any part of it, a hidden executable known as “RuntimeIndexer.exe” is silently initiated in the background.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this malicious campaign.
- Be Cautious with Downloads: Never download a file or attachment from untrusted sources like email, social media, and messaging applications. Malware is often distributed via ZIP files.
- Check File Extensions: Make sure you crosscheck the extension of any file you want to open with its expected type. To facilitate this process switch on file extensions visibility in your operating system’s settings or right-click on a file and click Properties.
- Watch Important Folders: Frequently inspect directories that are vulnerable to malware attacks, such as C:ProgramData and %APPDATA%. This is particularly important on script-based activities indicating a security risk.
- Utilize Strong Endpoint Logging: Put in place adequate endpoint logging tools that provide extensive data at the process level. Sysmon tool and enhanced PowerShell logging are extremely useful when it comes to identifying suspicious activities especially those utilizing encrypted channels such as SSL/TLS (port 443).
- Keep Updated And Be Adaptive: Learn about new evolving threats like PHANTOM#SPIKE campaign which uses encryption for evasion purposes. Adapt your security defenses as well as monitoring strategies to be able to counter sophisticated cyber threats.
- 13 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the PHANTOM#SPIKE include but are not limited to the following:
- Monitor suspicious PowerShell and command line activity.
Tags: Malware: PHANTOM#SPIKE | Target: individuals (Comman People) | Target Country: Pakistan | Attack Type: Phishing
Attacks on the Indian Government
(Originally published in Summer 2024)
Researchers at Volexity have discovered a cyber-espionage effort carried out by a possible threat actor based in Pakistan, which Volexity is presently monitoring under the alias UTA0137. Volexity lists the malware employed in these latest attacks as DISGOMOJI, which is built for Linux systems and written in Golang. Volexity is confident that UTA0137 has espionage-related goals and a mandate to target government entities in India.
Also, researchers from Cisco Talos have revealed Operation Celestial Force, a new malware operation that has been active since at least 2018. It is still in use today, using a Windows-based malware loader known as HeavyLift in addition to the Android-based malware GravityRAT. A stand-alone program they are referring to as GravityAdmin is responsible for managing all GravityRAT and HeavyLift infections. It performs malicious operations on a compromised device. Analysis of the panel binaries reveals that they are intended to administer and execute numerous campaigns at the same time, each with its own admin panel and codename.
Threat Labs summary
Securonix Threat Labs recommends caution against these attacks and deploying the following protective measures against increased threats:
- Monitor for detecting Execution of Zenity Utility for Social Engineering
- Monitor for detecting Downloads from Suspicious Domains”
- Monitor for detecting GravityRAT Infection on Windows and HeavyLift Loader Activity on Windows
- Monitor for detecting Suspicious Login Attempts via GravityAdmin
- 316 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the DISGOMOJI malware include but are not limited to the following:
- Monitor for detection Execution of Zenity Utility for Social Engineering.
- Monitor for detecting Downloads from Suspicious Domains.
TTPs related to the Operation Celestial Force include but are not limited to the following:
- Monitor for detecting GravityRAT Infection on Windows and HeavyLift Loader Activity on Windows.
- Monitor for detecting Suspicious Login Attempts via GravityAdmin.
Tags: Threat actor: the alias UTA0137 | Goal: Espionage-related goals and a mandate to target government entities in India
Snowflake Breach
(Originally published in Summer 2024)
Snowflake has observed and examined a hike in cyber threat activity against some of its customer accounts. They believe that there is an ongoing industry-wide, identity-based attack to obtain customer data. Based on research, these types of attacks are performed using their customers’ user credentials which were exposed through unrelated cyber threat activity. Snowflake believes this activity does not result from any vulnerability, misconfiguration, or malicious actions within the product.
To Back up Snowflakes claim that a string of customer data breaches was down to customer security failures rather than what it said was a limited incident at Snowflake itself, they brought in two of the most well-known incident response companies globally: Mandiant and CrowdStrike.
In 10th June 2024, Mandiant issued a report about a threat campaign that targeted Snowflake customer database instances with the aim of stealing data and asking for money. Snowflake is a multi-cloud data warehousing platform that is used to save and process huge amounts of structured and unstructured information. This cluster of activity is tracked by Mandiant as UNC5537, which they believe is a financially motivated actor who has stolen many records from the environments of Snowflake customers. Using stolen customer credentials, UNC5537 systematically compromises Snowflake customer instances, advertising victim data on cybercrime forums for sale, and attempting to extort multiple victims.
Threat Labs summary
This campaign’s broad impact is the result of an expanding infostealer market and missed chances to enhance credential security:
- UNC5537 probably accessed many different channels of infostealer logs that enabled it to aggregate credentials for Snowflake victim instances. The underground economy on infostealers is also very strong, with huge lists of stolen credentials being available both within and outside the dark web.
- Many of these affected customer instances had no multi-factor authentication implemented on them, and in some cases, their passwords hadn’t been changed as far back as four years. Network allow-lists are also not employed to restrict access to trusted locations.
- 363 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Snowflake Breach include but are not limited to the following:
- Monitor for Snowflake account for Detecting suspicious failed login attempts.
Tags: Threat Actor: UNC5537 | Targeting: Customer Data
CrowdStrike Outage
(Originally published in Summer 2024)
On July 19, 2024, a flawed update to the CrowdStrike Falcon sensor caused many Windows computers worldwide to experience the Blue Screen of Death (BSOD), leading to widespread system crashes. This disruption affected various sectors, including businesses, airports, train stations, banks, broadcasters, and healthcare providers. Although a fix has been released.
CrowdStrike Intelligence has observed several malicious activities taking advantage of this issue:
- Phishing Emails: Fraudsters are sending emails pretending to be CrowdStrike support, trying to trick customers.
- Fake Phone Calls: Impersonators are calling people, pretending to be CrowdStrike staff.
- Bogus Research Claims: Scammers are posing as independent researchers, claiming to link the update issue to a cyberattack and offering false advice on how to fix it.
- Fake Recovery Scripts: Some are selling scripts that falsely promise to fix the update problem.
- Deceptive Domains: New fake websites have been set up to look like they offer genuine fixes but are actually designed to deceive users and spread malware.
One instance of this offensive activity is HijackLoader that was distributed via phishing emails pretending to be a necessary “hotfix” and targeted LATAM countries. This loader was designed to install Remcos, a remote access Trojan (RAT) which allows the attacker full control over victims’ systems.
On July 23rd, 2024, another malicious ZIP file called CrowdStrike Falcon.zip was identified by CrowdStrike Intelligence. This archive contained Connecio – an information stealing python-based program. The file appeared soon after the initial content update issue with the purpose of being taken for a real Falcon update.
While Securonix operations remained unaffected, we had provided the relevant information to help understand and mitigate these attacks’ impact. The report by the Securonix Threat Research Team reveals various attack vectors and malware involved in the latest CrowdStrike incident.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this malicious campaign.
- Do not provide any personal or organizational information in online platforms that offer “free claim reviews” or similar services, these might be frauds targeted at acquiring your details.
- Ensure the legitimacy of any service or response to an incident before engaging with it.
- Only follow CrowdStrike’s official support channels and their instructions.
- To scan and block malicious files or websites, keep your antivirus and Anti-malware software up to date. Learn about current threats and proper security practices for protecting systems.
- Educate employees how to identify scams and phishing attempts.
- 273 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the exploitation of crowdStrike updates include but are not limited to the following:
- Monitor for ZIP archive named “crowdstrike-hotfix.zip”.
- Boot the Windows system into safe mode or the Windows Recovery Environment (winRE) and open the File Manager and navigate to C:WindowsSystem32driversCrowdStrike. Look for and delete any files that match the pattern C-00000291*.sys.
- Monitor for a shortcut file with the initial payload named “y_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.lnk”, and the target location of the shortcut file pointed to a malicious macro code document named “New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.docm”.
- Monitor for a shortcut file named “Steps to recover from CrowdStrike Blue Screen.lnk”, and the target location of the shortcut file points to a document named “Steps to recover from CrowdStrike Blue Screen.docx”.
- Monitor for a filename “payload2.txt”.
- Monitor for filename “CSfooter.png” and “update1.pdf”.
- Monitor for filename “CrowdStrike Falcon.zip”.
- Monitor for filename “CrowdStrike Falcon.exe”.
Tags: Affected Product: CrowdStrike Falcon sensor, Microsoft Windows | Affect Region: Global Attack Type: Phishing
New threat actor’s activities
(Originally published in Summer 2024)
The Sysdig Threat Research Team has detected significant improvements in the operations of the SSH-Snake threat actor, now referred to as CRYSTALRAY. Their activities have increased substantially with over 1500 victims reported. This hacking group uses various open-source security tools to enable it to scan vulnerabilities in infrastructure, deploy backdoors, and ensure that compromised environments are always accessible.
Another one, a newly discovered threat actor known as TAG-100, was found to be using open-source tools in what is believed to be a global cyber-spying campaign on a large scale. The targets for this campaign are both government and private sector organizations located in different parts of the globe such as Africa, Asia, Europe, and America. It is worth noting that at least ten countries have been affected by this campaign with two un-named intergovernmental organizations based in the Asia Pacific being involved.
Lastly, a new APT group, Actor240524, emerged with an advanced adversary toolkit for evading detection and maintaining persistence. In early July 2024, this group launched a spear-phishing attack targeting ambassadors from Azerbaijan and Israel. The attackers stole important information from the victims using a malicious Word document written in Azerbaijani and masquerading as official documents.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these APT groups.
- Network Monitoring: Establish solid network monitoring to notice abnormal scanning and lateral movement.
- Patch Management: Regularly update and patch systems to fix vulnerabilities identified by tools like nuclei.
- SSH Key Management: Use strong SSH key management practices and conduct regular audits of SSH access.
- Cryptominer Detection: Install endpoint protection solutions that are capable of detecting and blocking cryptomining activities.
- 62 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the APT group Actor240524 include but are not limited to the following:
- Monitor for unusual email patterns, such as emails with unexpected attachments or links, especially if they come from unrecognized or suspicious sources.
- Monitor for a Word document with the filename “iden.doc”
- Monitor for abnormal macro activity in documents, such as unusual VBA scripts or macro execution.
- Monitor for unusual macro execution patterns or any macros that attempt to modify system files or execute unauthorized programs.
- Monitor for suspicious file modifications or creation in directories commonly used by malware. Look for executables being saved in non-standard locations (e.g., C:UsersPublicDocuments).
- Monitor for the file named “MicrosoftWordUpdater.log” (referred to as ABCloader).
- Monitor for file name “synchronize.dll” ABCloader subsequently loads this file (referred to as ABCsync).
Tags: APT Group: CRYSTALRAY, SSH-Snake, TAG-100, Actor240524 | Target Sector: Government and private sector organizations | Target Location: Africa, Asia, Europe, America, Azerbaijan, and Israel
SLOW#TEMPEST campaign
(Originally published in Summer 2024)
The Securonix Threat Research team has identified a covert cyber campaign, codenamed SLOW#TEMPEST, targeting Chinese-speaking users with Cobalt Strike payloads delivered through phishing emails. This campaign, which remains unattributed to any known threat actor, begins with malicious ZIP files containing a disguised Windows shortcut file named “违规远程控制软件人员名单.docx.lnk” (translated as “List of people who violated the remote control software regulations”). Upon unpacking the ZIP archive, the infection chain is triggered, deploying a post-exploitation toolkit on the compromised systems. The attackers were able to move laterally, establish persistence, and remain undetected within the systems for over two weeks. Given the use of language related to remote control software regulations, the campaign likely targets Chinese business or government sectors that enforce such regulations.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this malicious campaign.
- Avoid Downloading Suspicious Files: Refrain from downloading files or attachments from unknown or unsolicited sources. This includes commonly used file types such as ZIP, RAR, ISO, and PDF files. Be particularly cautious with ZIP files, as they may be password-protected and used to deliver malicious payloads.
- Secure Common Malware Staging Areas: Regularly monitor and secure directories frequently used by attackers to stage malware, including:
- `C:ProgramData`
- `C:WindowsTemp`
- `%APPDATA%`
- Script-Related Activity: Pay close attention to script-related activities in world-writable directories, as these are commonly exploited by threat actors to execute malicious scripts.
- Enhanced Logging and Monitoring: During the SLOW#TEMPEST campaign, the attackers used different ports for encrypted communications. In the light of all this, maximum endpoint logging including, but not limited to, processes logging using Sysmon and PowerShell has to be performed in order to increase the detection potential.
- 21 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the SLOW#TEMPEST campaign include but are not limited to the following:
- Monitor for unusual or unexpected email attachments, particularly ZIP files.
- Monitor for unusual DLLs in directories where they are not typically found.
- Monitor for unexpected changes in user privileges or group memberships, especially for administrative or privileged accounts.
- Monitor for unusual RDP connections or failed login attempts on RDP.
- Monitor for the use of stolen credentials or hash-based authentication attempts.
- Monitor for credential dumping tools or suspicious access to LSASS memory.
- Monitor for access to or extraction of credentials from browsers or other password stores.
- Monitor for commands or tools that query system information or run system enumeration commands.
- Monitor for changes or queries related to permission groups or user roles.
- Monitor network traffic for unusual or encrypted data exfiltration patterns.
Tags: Campaign: SLOW#TEMPEST | Target System: Windows | Payload: Cobalt Strike
Iranian Threat Actor Activity
(Originally published in Summer 2024)
Iranian cyber actors have ramped up their operations significantly in 2024, using a variety of tactics to target U.S. and international organizations across multiple sectors. One group backed by the Iranian government, known in the private sector as Pioneer Kitten and Lemon Sandstorm among others, has been running ransomware campaigns in partnership with known affiliates like NoEscape and BlackCat. They’ve been hitting critical systems in education, healthcare, and defense, not just deploying ransomware but also stealing data. These actors are making money off stolen credentials while simultaneously conducting state-sponsored espionage, with a particular focus on sensitive industries in the Middle East.
At the same time, another Iranian group dubbed “Peach Sandstorm” has been busy gathering intelligence, especially in defense, satellite communications, and the oil and gas sector. They’re using sophisticated methods like password spraying and social engineering, even leveraging LinkedIn to gather intel and break into sensitive networks. Their latest piece of malware, called Tickler, shows just how advanced they’ve become – it allows them to maintain a foothold and control compromised systems for extended periods. Peach Sandstorm has also started using compromised Azure infrastructure as a command-and-control hub, which shows how their attack techniques are evolving.
On top of all this, Iran’s counterintelligence operations have been expanding. The Islamic Revolutionary Guard Corps (IRGC) is running campaigns to collect information on dissidents and anyone they think might be working with foreign intelligence agencies. They’ve set up fake recruitment websites to trick targets into handing over personal details, which could later be used for surveillance or even persecution.
Threat Labs summary
By combining ransomware attacks, espionage, and counterintelligence operations, Iranian cyber actors are seriously upping their game in cyber warfare. This multi-pronged approach poses a complex threat to both government and private organizations around the world. Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this malicious campaign.
- Implement Robust Password Policies: Enforce strong, unique passwords and multi-factor authentication across all systems. This helps defend against password spraying attacks frequently used by Iranian actors, particularly against cloud services.
- Monitor LinkedIn Activity: Watch for suspicious LinkedIn profile creation and connection requests, especially those targeting employees in sensitive positions. Iranian actors, like “Peach Sandstorm,” often use LinkedIn for intelligence gathering and social engineering.
- Secure Azure Infrastructure: Regularly audit Azure resources for unexpected changes or creations. Iranian threat actors have been observed leveraging compromised Azure infrastructure for command-and-control operations.
- Enhance Data Exfiltration Detection: Implement robust data loss prevention (DLP) measures, focusing on sensitive industries often targeted by Iranian actors, such as defense, satellite communications, and oil and gas. Monitor for unusual data access patterns or large data transfers, especially to unfamiliar IP addresses.
- Ransomware and Data Theft Prevention: Deploy file integrity monitoring and behavior-based detection systems to identify potential ransomware activity. Iranian actors often combine ransomware deployment with data theft operations.
- Secure Common Malware Staging Areas: Regularly monitor and restrict access to directories frequently used by attackers, including:
- %TEMP%
- %APPDATA%
- C:ProgramData
- Enhanced Logging for Custom Malware: Implement comprehensive logging, including process creation and network connections, to detect custom malware like “Tickler”. Pay special attention to unexpected outbound connections and unusual process behavior.
- Counterintelligence Awareness: Educate employees about fake recruitment websites used by Iranian actors for information gathering. Implement web filtering to block access to known malicious sites and monitor for unusual submissions of personal information.
- 65 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to Iranian threat actor activity include but are not limited to the following:
- Monitor for failed logon activity, including failed attempts to sign-in from multiple sources that originate from a single ISP
- Monitor for password spraying
- Monitor for unfamiliar sign-in properties
- Monitor for DLL sideloading and DLL search order hijacking
- Monitor for a typical travel and impossible travel activity
- Monitor for suspicious administrative activities
- Monitor for activity from a Tor IP address or anonymous proxy
Tags: APT Group: Peach Sandstorm, Lemon Sandstorm, Pioneer Kitten
Citrine Sleet exploiting Chromium zero-day
(Originally published in Summer 2024)
Microsoft Security identified a threat actor dubbed Citrine Sleet, linked to North Korea and abusing CVE-2024-7971, a zero-day vulnerability in the Chromium browser, on August 19, 2024. This actor has been exploiting a zero-day vulnerability in Chromium-based browsers, which include Google Chrome and Microsoft Edge. The vulnerability allows attackers to execute malicious code on a victim’s machine. Also, it has affected the V8 JavaScript and WebAssembly engines and enabled remote code execution (RCE).
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this malicious campaign.
- Apply Security Updates: Make sure your systems are up to date with the most recent patches, especially for vulnerabilities such as CVE-2024-7971, CVE-2024-38106, and CVE-2024-38193.
- Block Exploit Chains: Make sure that components of the exploit chain, such as CVE-2024-38106, are addressed to prevent the whole attack chain from executing.
- Strengthen defenses against zero-day exploits: Keep systems up to date so that vulnerabilities can be addressed before they are exploited in zero-day attacks.
- Use Advanced Security Systems: Deploy systems that can detect and prevent kernel tampering and malware, such as FudModule.
- 2 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Citrine Sleet group include but are not limited to the following:
- Monitor for indicators of kernel tampering and DKOM techniques.
- Monitor for unexpected activity in the cryptocurrency asset management sector.
Tags: Target Sector: Cryptocurrency, Financial institutions, Gaming Companies | Malware Involved: AppleJeus trojan, FudModule rootkit, Kaolin RAT | Threat Actor: Citrine Sleet
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh
Source: Original Post
Views: 2