The Monthly Intelligence Insights report from Securonix Threat Labs analyzes significant cybersecurity threats from February 2025, including sophisticated campaigns such as DEEP#DRIVE by Kimsuky and various ransomware activities. Key findings include the emergence of new threat actors and tactics targeting critical sectors through phishing and exploiting vulnerabilities. Affected: South Korean businesses, government organizations, cryptocurrency users, healthcare, financial services, critical infrastructure, manufacturing, education, and more.
Keypoints :
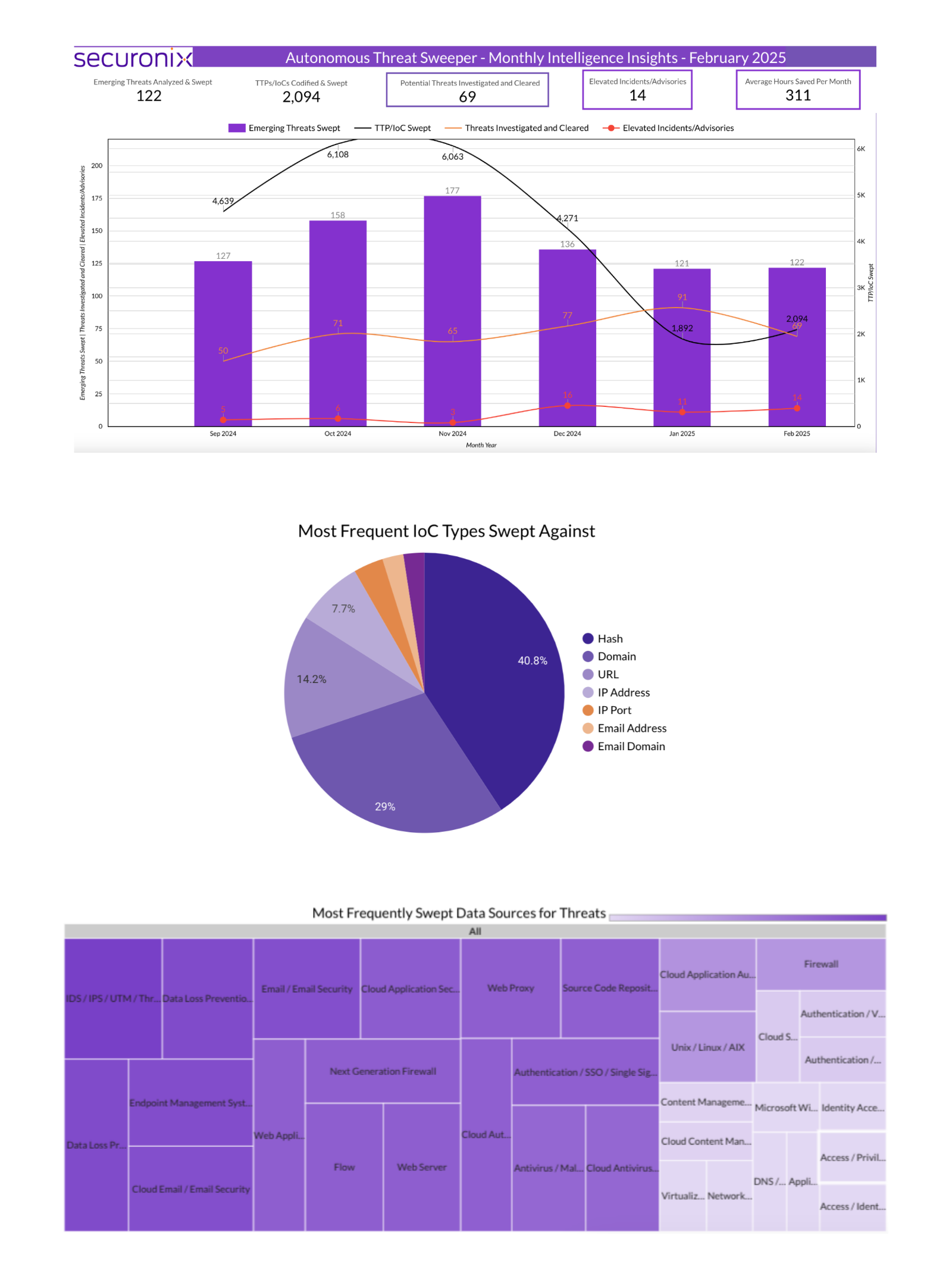
- Securonix identified 2,094 TTPs and IoCs, including 122 emerging threats.
- DEEP#DRIVE campaign targets South Korea, employing sophisticated phishing techniques.
- Kimsuky group uses PowerShell scripts and Dropbox for payload delivery and data exfiltration.
- New threat actors TA2726 and TA2727 linked to macOS malware distribution.
- Cyber campaigns REF7707 and BadPilot focus on government entities and critical infrastructure.
- Winnti group exploits SQL injection vulnerabilities targeting Japanese industries.
- Ransomware threats from Ghost (Cring), LockBit, and Abyss Locker have escalated.
MITRE Techniques :
- Technique T1193 (Spear Phishing): Kimsuky uses LNK files disguised as legitimate documents for malware delivery.
- Technique T1059 (PowerShell): PowerShell scripts employed for execution of additional malware and payload delivery.
- Technique T1071 (Application Layer Protocol): Dropbox used for data exfiltration and command-and-control operations.
- Technique T1060 (Registry Run Keys / Startup Folder): Scheduled tasks created to maintain persistence in infected systems.
- Technique T1070 (Indicator Removal on Host): Attacks erase traces of the incident by cleaning up logs and tampering with recovery options.
- Technique T1213 (Data from Information Repositories): Utilizes Dropbox to gather sensitive information and credentials.
- Technique T1203 (Exploitation for Client Execution): Exploiting vulnerabilities in applications like Atlassian Confluence to deploy ransomware.
Indicator of Compromise :
- [File Name] 종신안내장V02_곽성환D.pdf.pdf
- [File Name] SoftwareDistribution.txt (Unknown script executed)
- [File Name] FontDrvHost.exe (Downloaded by the attacker)
- [Hash] 1234abcd… (Example hash for demonstration)
- [IP Address] 192.168.1.1 (Example IP for demonstration)
Full Story: https://www.securonix.com/blog/securonix-threat-labs-monthly-intelligence-insights-february-2025/