“Scammers Paradise” —Exploring Telegram’s Dark Markets, Breeding Ground for Modern Phishing Operations
By Oleg Zaytsev, Nati Tal (Guardio Labs)
Over the last few years, the phishing ecosystem has been “democratized. “ There was a time when kits, infrastructure, and know-how, were available only on invite-only forums in the Dark web, hidden behind Tor Onion networks. Today, they are readily and publicly available on Telegram — accessible via a simple search.
This messaging app has transformed into a bustling hub where seasoned cybercriminals and newcomers alike exchange illicit tools and insights creating a dark and well-oiled supply chain of tools and victims’ data. Free samples, tutorials, kits, even hackers-for-hire — everything needed to construct a complete end-to-end malicious campaign.
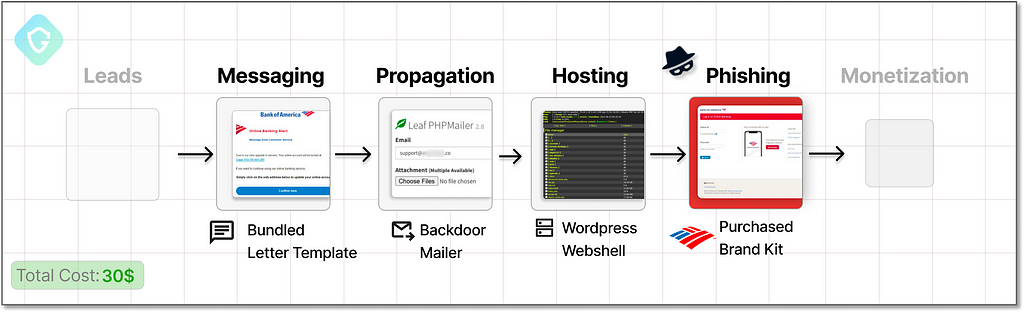
In this write-up, we will put our Black Hat on, and delve into an exploration of this not-so-hidden underworld. Step by step, we will reconstruct a malicious campaign and show how, for as little as 230$, a successful mass attack can be mounted from scratch. We will dissect the inner workings of the ecosystem and attack chain to learn how we can fight back.
WARNING: This article discusses publicly available methods for malicious activities, but it is in no way meant to be a tutorial or encouragement to engage in such acts. We aim to increase awareness about these activities and offer insights on combating them.

Telegram. Telegram Phishing Markets Everywhere
It’s startling how easily one can stumble upon these digital marketplaces on Telegram. Public channels, groups, and bots bustling with thousands of participants, where messages cascade continuously showcasing various products and services, tips and tricks, and knowledge you once had to dig deep into the dark web even to get close to.
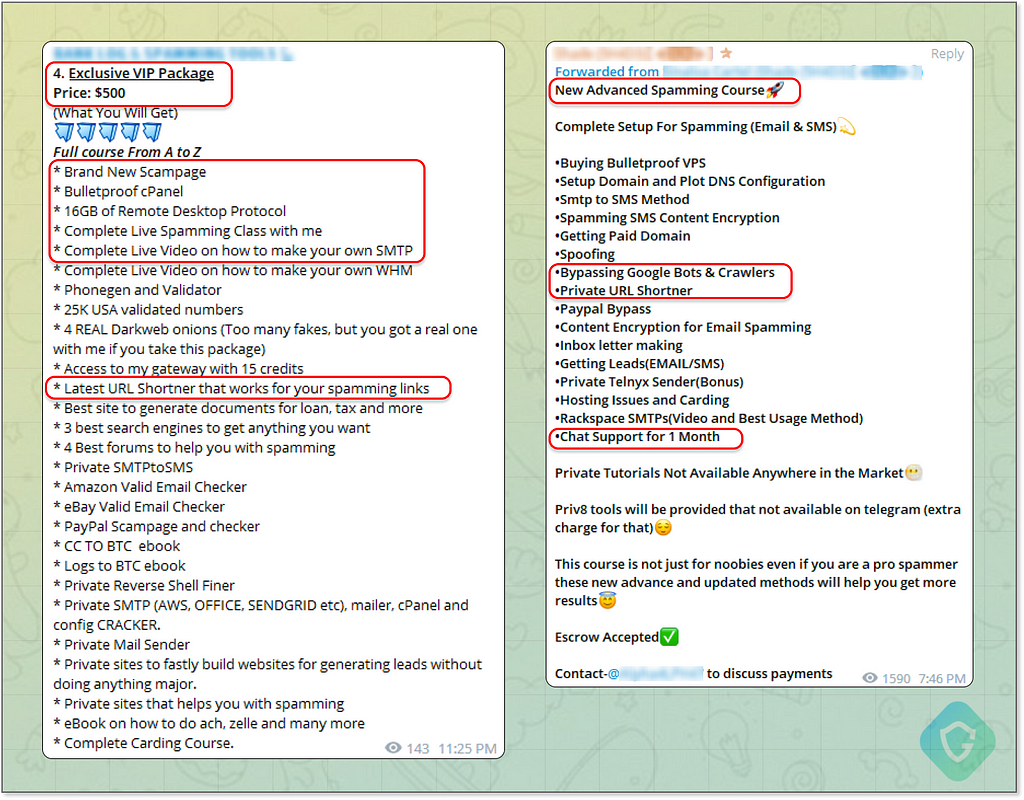
Our latest writeups on “MrTonyScam”, a phishing campaign targeting millions of Facebook business accounts, introduced us to one of many examples of Telegram’s malicious use. This campaign utilized Telegram channels to offer hijacked social accounts of victims targeted by phishing and malware. On sale are credentials and session cookies — many of them fresh out of the oven, hacked and stolen just hours or even minutes ago, and already available for sale.
And so, if Telegram is so easily and freely used to monetize on stolen accounts and identities, it’s a no-brainer that it is also used to create those malicious activities in the first place.
Let’s Put On The Black Hat
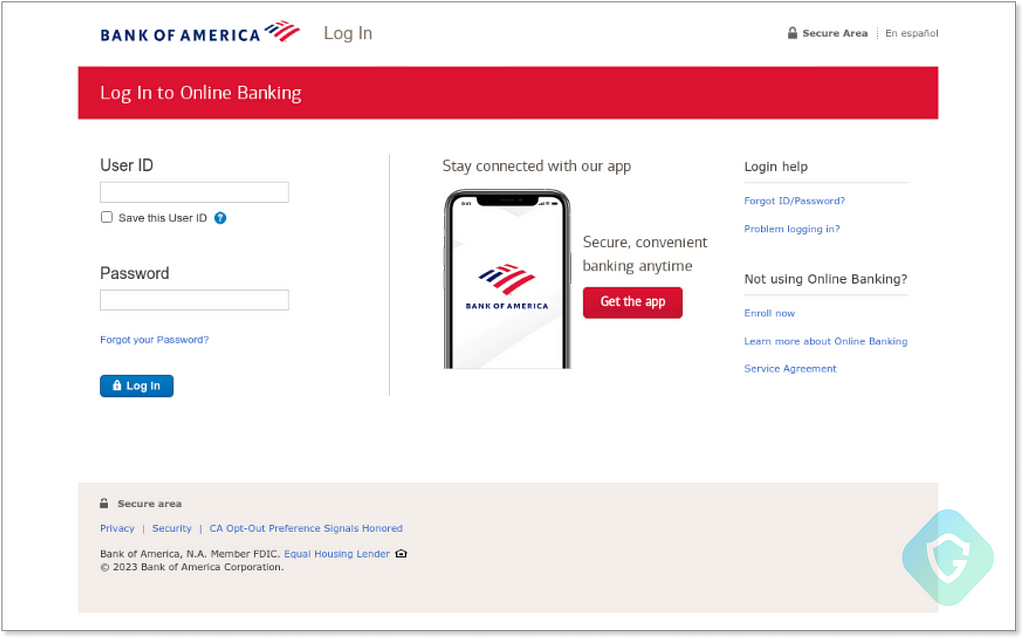
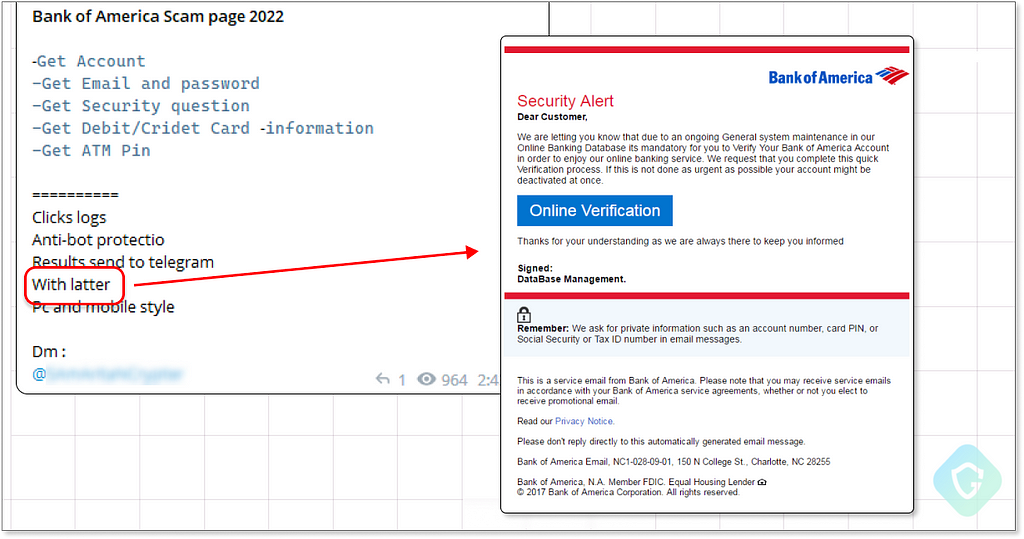
To aid in understanding how mind-blowing and dangerous those freely offered services and solutions in Telegram are, let’s put on the black hat for a short while to craft a phishing campaign — from A to Z . Take for example this “Bank Of America” scampage (phishing page) that has been widely circulating in US network traffic lately:
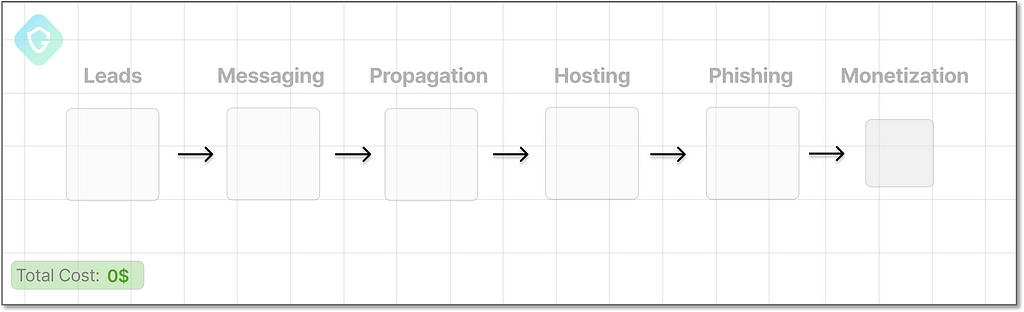
If we were to re-create this scheme, we would need several building blocks:
- The phishing web page (“scam page”) as shown above
- Hosting solution to serve this scampage
- Email sending system
- A well-designed email message (Letter) to lure victims to the scampage
- Lists of valid and relevant email addresses to target (Leads)
- A means to monetize on our stolen credentials collected
We are about to construct the whole chain, from readily available building blocks on Telegram — some offered at very low prices, and some even for free!
So, we go undercover and start from scratch, filling in the missing pieces one by one:
First Thing First — The “scampage”
And so we go hunting, abusing the name and reputation of a banking corporation with 90+ billion dollar annual revenue. We start with the scampage, the focal point of our campaign, designed purely to deceive and collect bank account details from our victims by pretending to be the real bank login page.
To develop this page, we can try to simply copy the original login page’s HTML and manipulate it a bit. Yet, attempting to do so proved to be too complex for editing and most likely to be quickly blocked by standard security measures.
However, this isn’t a major hurdle, as the “market” offers a vast array of phishing pages for virtually any brand you can think of — from banks and social media platforms to cryptocurrency services and even pizza places.
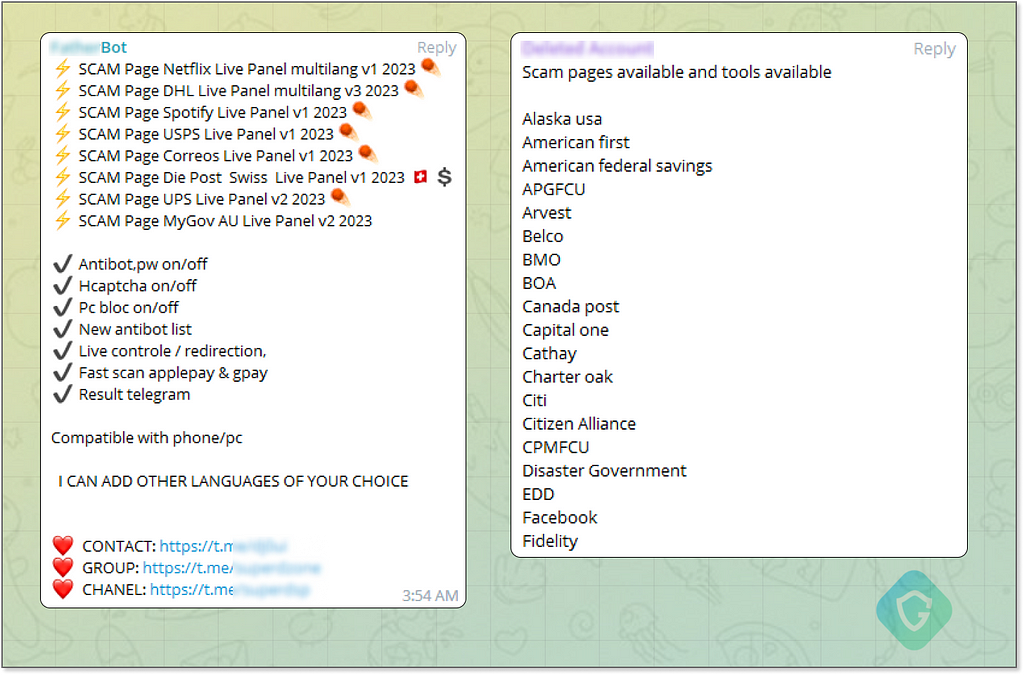
These pages are equipped with sophisticated anti-detection and code obfuscating techniques, anti-bot, anti-scanner technologies, and optional “send-to-telegram” capabilities — another Telegram abuse to collect back the stolen data anonymously.
Some of the more sophisticated scampages are bundled with features like 2FA/OTP bypass, incorporating an active proxy that connects to the actual service (such as a bank). This setup enables victims to unknowingly log into a fake interface and even enter their 2FA codes. Meanwhile, their credentials are automatically relayed to the real service through proxy automation. As a result, while the victim is logged out, the attacker gains access to the account.
The prices vary:
$10+ for basic pages
$100 — $800+ for pages with advanced 2FA bypass and real-time account hijacking automation
In some cases, you can quickly customize your scampage with any feature and advanced capabilities using a dedicated Telegram-Bot:
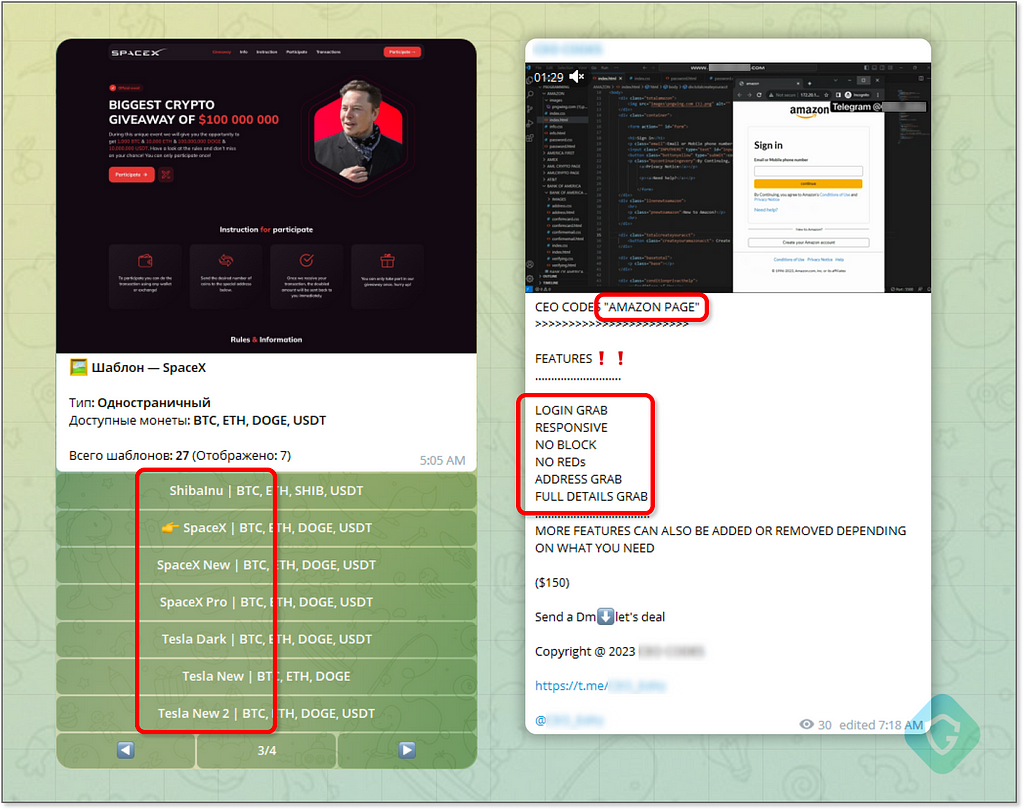
The above crypto-giveaway Elon Musk-themed scampage generator is exactly the one we’ve seen bombarded on YouTube live feeds from hijacked channels in the past year (See StreamJacking analysis).
Spot on! After some browsing on the markets we quickly found a relevant scampage for our scheme:
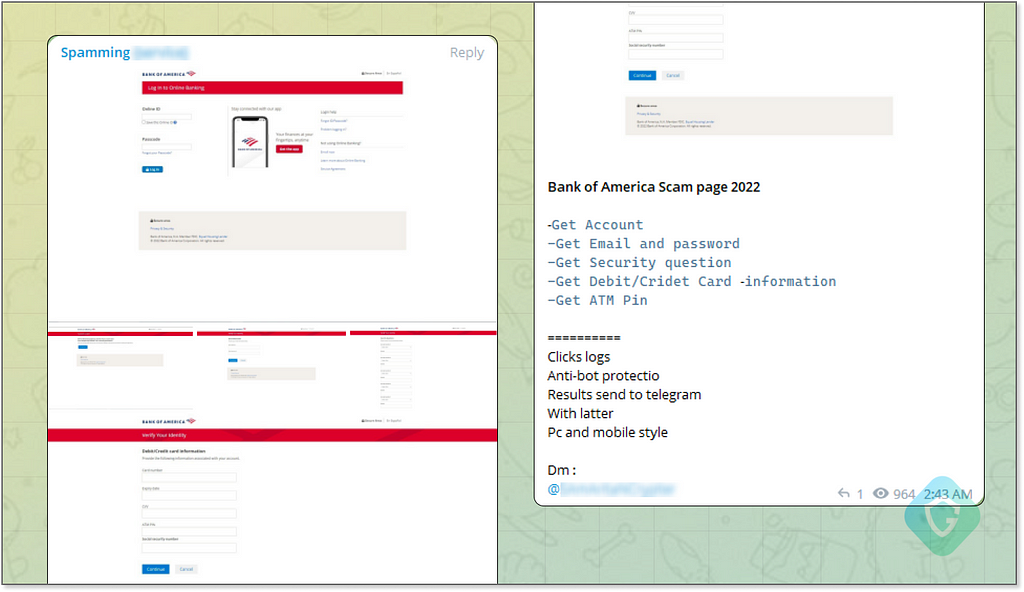
After contacting the seller, we were able to negotiate the price down to $30 and get a copy of the scampage with everything needed to get started.
With this, we mark the completion of the first step 
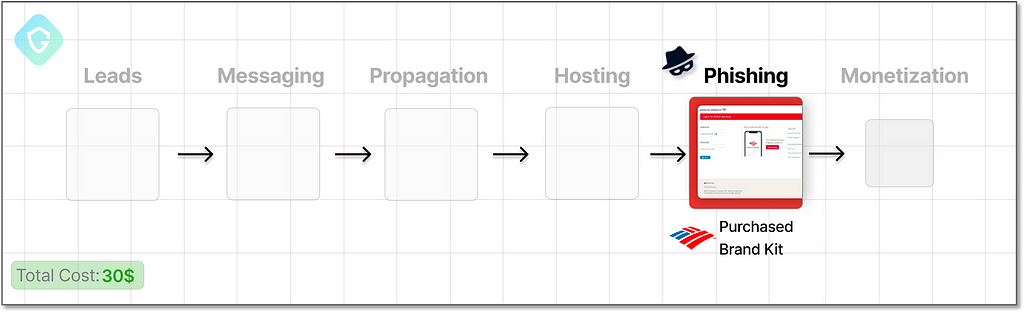
Hosting And Domains
To offer that scampage to potential victims, we need it to be hosted somewhere. Hosting on popular/legit hosting providers will probably lead to being reported and blocked, as those providers mostly have an effective report center. Thus, we shall dwell in the world of alternative hosting:
Bulletproof Hosting — The concept of offshore hosting providers that do not interrupt or monitor their users is well-known among scammers. In most cases, scammers will buy and resell a hosting solution that already has a proven track record of hosting malicious content without interruption.
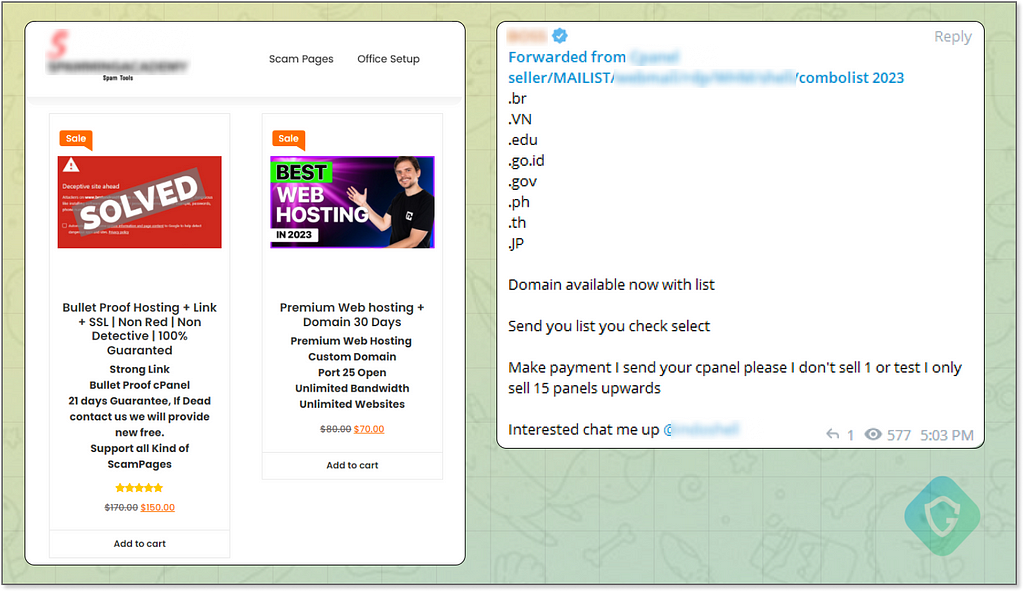
We find endless options of “cPanel”s for rent or purchase.
“cPanel” is a popular platform for site management — all you need is access to this control panel, from which you can host and control your scampage immediately. Combos of bulletproof hosting solutions including domain names are constantly sold and re-sold on the market:
Web shells — Web shells are a means of gaining unauthorized access to reputable websites and their connected services. The age and SEO (Search Engine Optimization) ranking of a domain is crucial in avoiding detection. For more effective phishing campaigns, attackers look to host their scam pages on reputable domains. They achieve this by compromising those reputable legitimate sites and inserting a backdoor script, giving them control over the website’s hosting and file storage, often without the site owner’s knowledge:
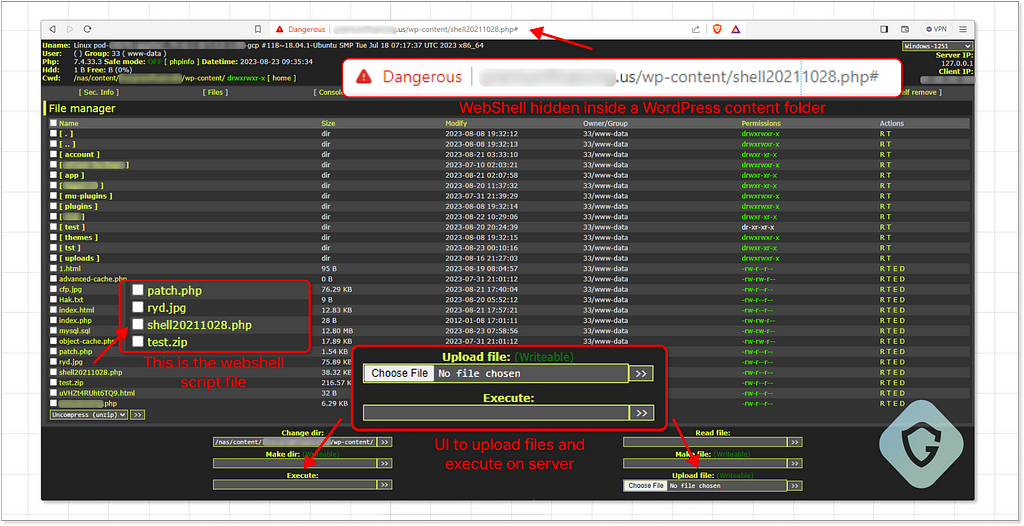
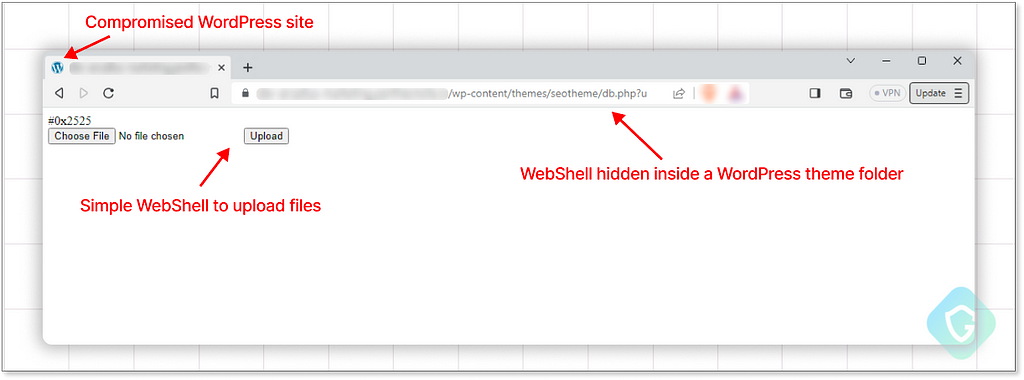
These scripts enable attackers to upload malicious files and scampages to the compromised server. Web shells are commonly found on compromised WordPress sites, getting there by exploiting known vulnerabilities. Hackers may use those web shells for hosting their scam operations while also selling this unauthorized access to others on the market. There, you can also find scanning tools that detect if sites are vulnerable to web shell installation so we can host on a target of our choosing if the “off the shelf” site inventory is not to our liking.
Offline / File Attachments – As an alternative for hosting a scampage online, we can also use offline standalone Scampages and distribute those as an email attachment. These scampages function similarly to a basic phishing website, only that the entire scripting and resources like images and style are embedded as part of the file. These are of course also available for sale, including all the latest detection mitigation techniques like scrambled code, dynamic page generation, and text encoding shenanigans.
As “newbie blackhat hacker wannabes”, we opted to start with something simple. We chose to use a free web shell sample of a randomly compromised WordPress website found in one of the groups. To maintain persistence, we replaced the current web shell with our own password-protected PHP file. It was striking to see how effortlessly and without cost we could proceed with our scheme. We went live with the scampage almost instantly, utilizing a reputable domain.
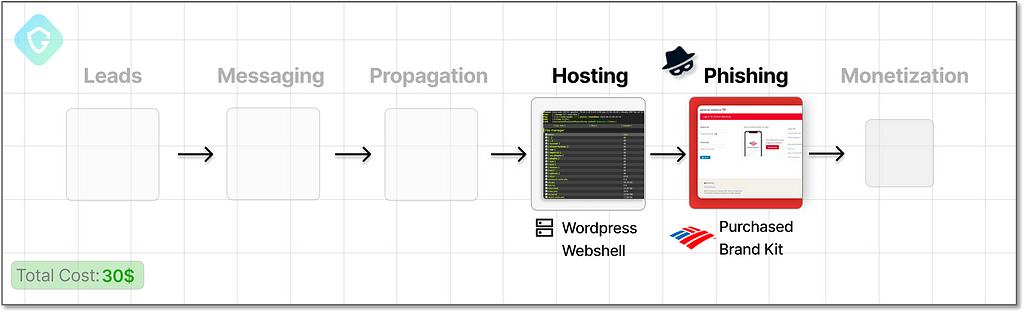
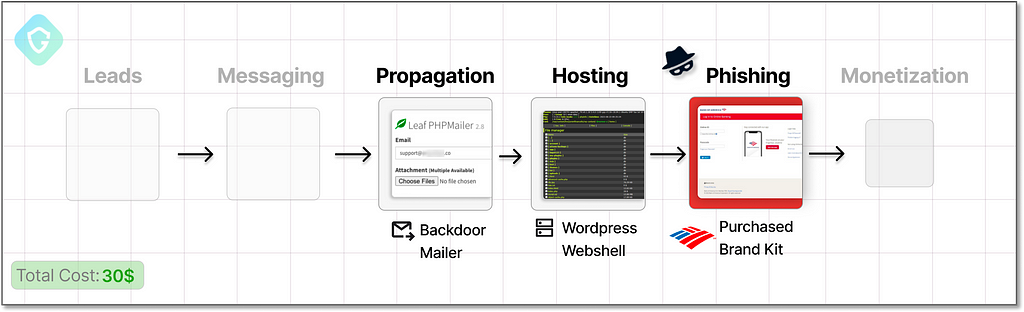
Propagation — Sending 100K+ Phishing Emails
Distributing our freshly crafted scampage link effectively is about targeting the right audience and in masses. An email can be a powerful tool for reaching a broad demographic and telling the right “story”. However, there are significant limitations and challenges. For instance, personal Gmail accounts have a cap of around 500 on the number of emails they can send per day, and emails from new accounts often end up in spam folders, diminishing the impact of the campaign.
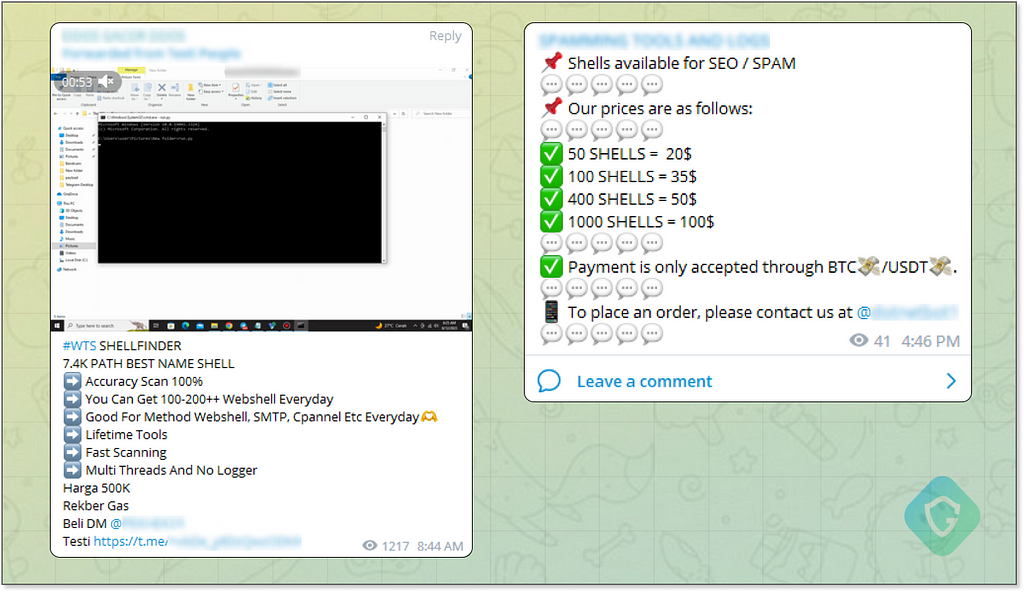
Despite these challenges, the Telegram market offers an array of tools and methods to overcome these hurdles.
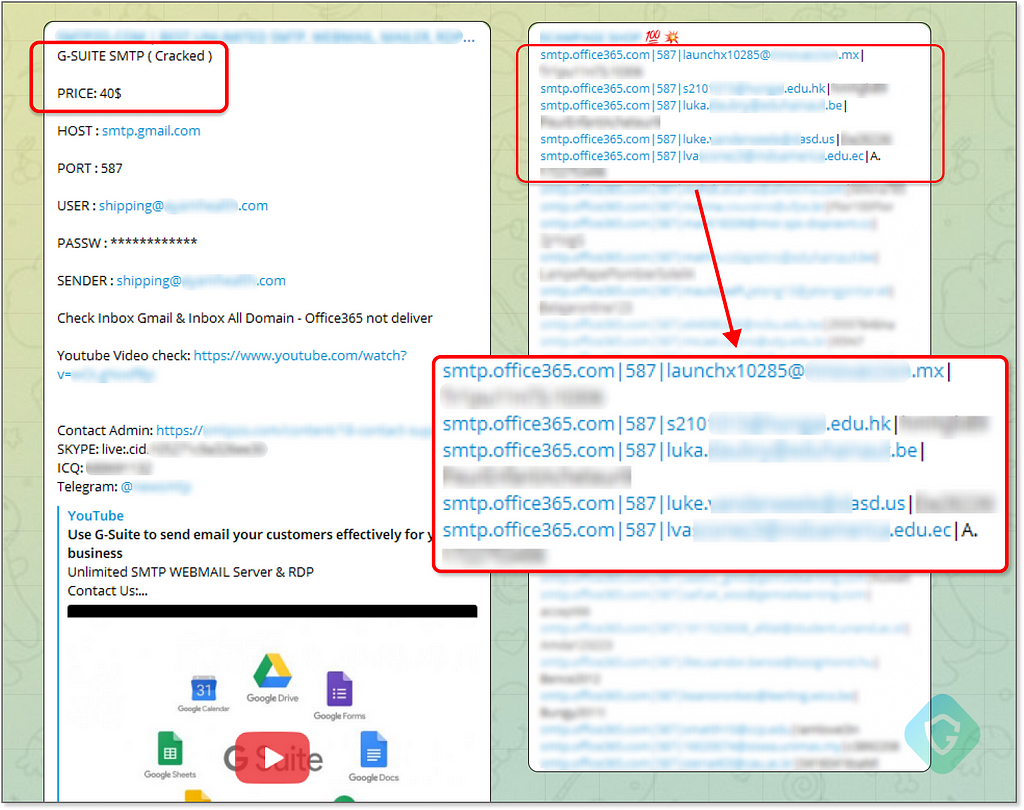
Hacked SMTP Credentials — Using someone else’s SMTP server credentials is an effective way to obtain a higher sending quota and leverage a reputable source. These credentials, which are often hacked, leaked, or acquired through brute force, are available for purchase. This approach, however, carries significant risks. The credentials are generally good for one-time use, as they tend to get blocked quickly once abuse is discovered. It’s a gamble — as the sellers often warn — “high risk, high reward”.
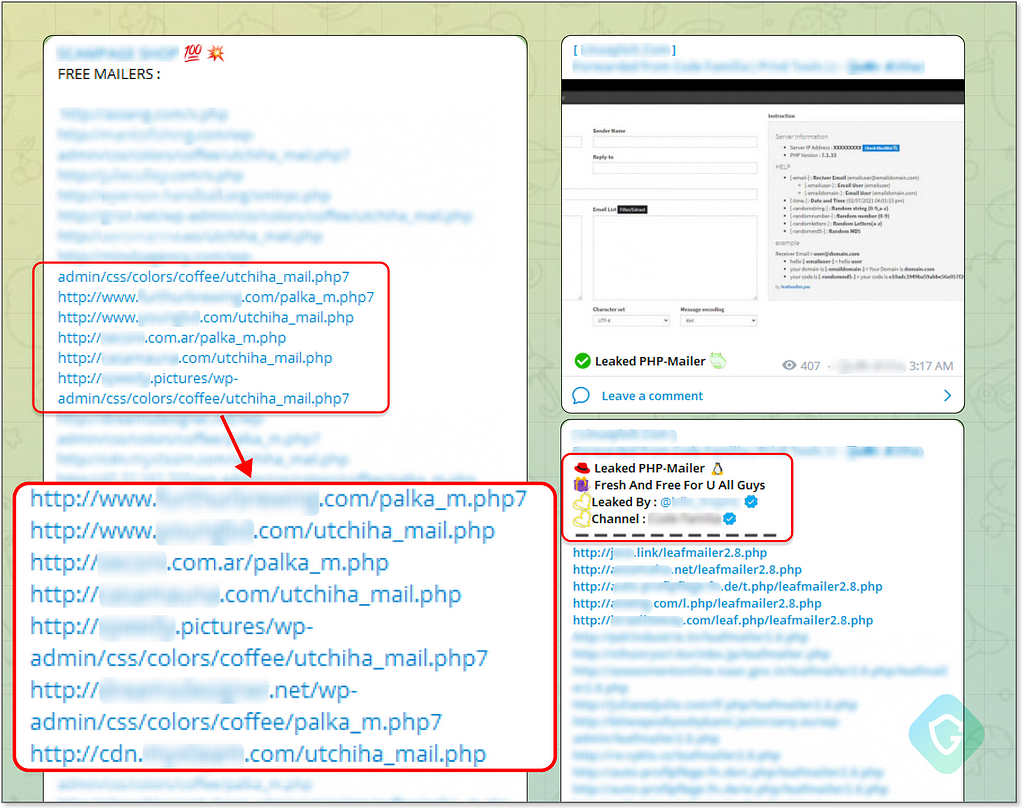
Backdoor Mailers — Similar to a web shell upload interface we saw earlier, this script is injected into compromised websites and gives you a user-friendly interface, referred to as “Mailer” in the Telegram lingo.
As this Mailer is hosted on compromised websites, it enables us to craft emails using a legitimate domain of the exploited website. For example, if a backdoor mailer is installed on a site like www.youritsolutions.it/hacked_mail_interface.php, it enables sending convincing, reputable tech scam emails from an address such as support@youritsolutions.it. These emails are more likely to bypass spam filters and reach their targets, seeming credible due to their origin.
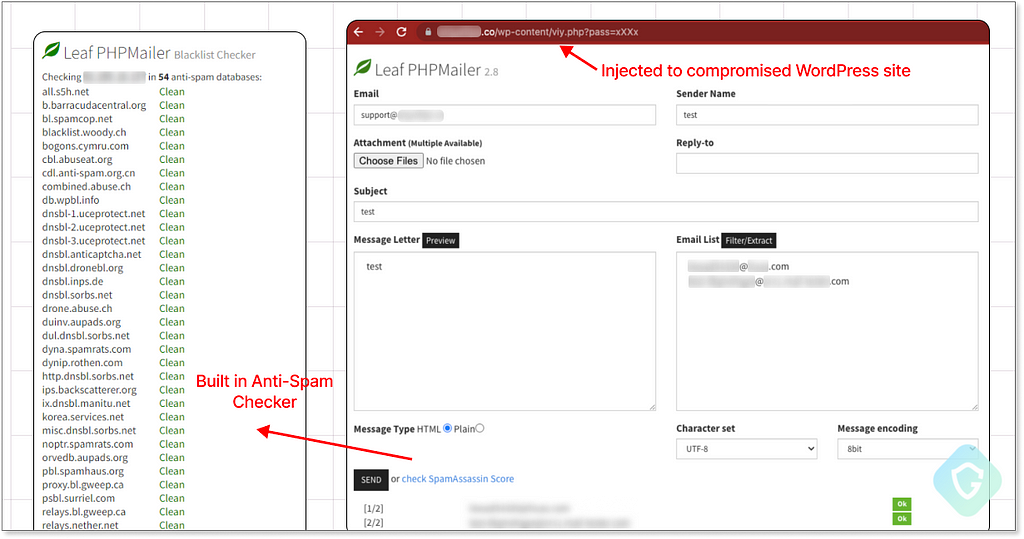
Probably the most common mailer is the “Leaf PHPMailer”, based on an open-source PHP library. It’s a user-friendly interface that even includes a built-in DNS spam check feature for the hosted compromised domain. This function is critical for assessing the mailer’s effectiveness and determining whether it has already been flagged as a spamming source.
Mass Mailer Services — Using a legitimate account from a well-known mass mailing service like SendGrid or Amazon SES can be a more reliable method than relying on hacked credentials or backdoor mailers. These platforms are already used for marketing and other large-scale email purposes.
As a scammerhacker, Directly signing up for these services can be complex due to rigorous customer verification processes, including credit card validation and other authorization steps. That’s why scammers often purchase accounts from Telegram sellers:
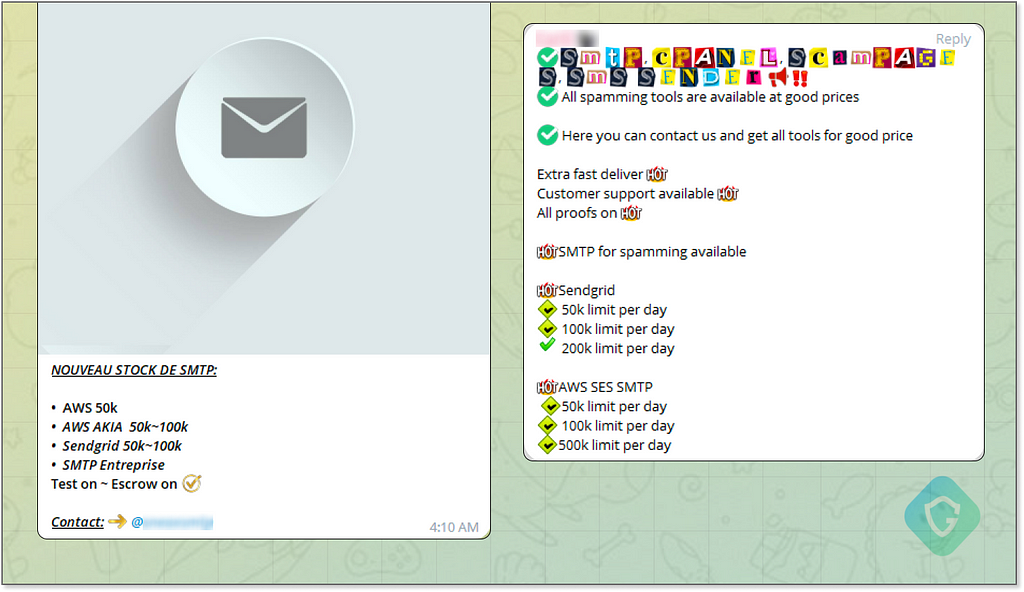
These sellers sometimes “warm up” the accounts by sending legitimate emails for a while, boosting the account’s reputation. Each SMTP account from these services has a daily sending limit, which can range anywhere from 20,000 to 500,000(!) emails. The price of these accounts typically varies according to their email-sending limit.
Indeed, the methods mentioned earlier can be expensive, especially for those just starting in this field. That’s where the PHP mailer method comes into play, offering a range of free samples. With some experimentation, we managed to find fresh samples that hadn’t been used before, were not blacklisted by any DNS provider, and were fully functional. However, their effective lifespan is short, so it’s crucial to act quickly and utilize the full quota — which is around 25,000 emails per sample. That’s a substantial number for a free option.
Messaging — The Initial Hook
With 3–4 functioning mailers at our disposal, we can dispatch nearly 100,000 emails.
Now the missing part is: what should these emails say? What will ensure that they bypass spam filters, entice clicks, and ultimately lead to the submission of bank credentials?
In today’s landscape, we could leverage tools like ChatGPT to compose professional-looking messages. However, crafting an email that convincingly mimics legitimate bank communication requires more than just persuasive text. The styling and branding are vital: HTML, images, CSS, and ensuring compatibility across devices. The goal is to make the message appear as authentic as possible, indistinguishable from genuine bank correspondence. This is what scammers often refer to as “Letters” — expertly designed, branded templates that are virtually indistinguishable from the real thing.
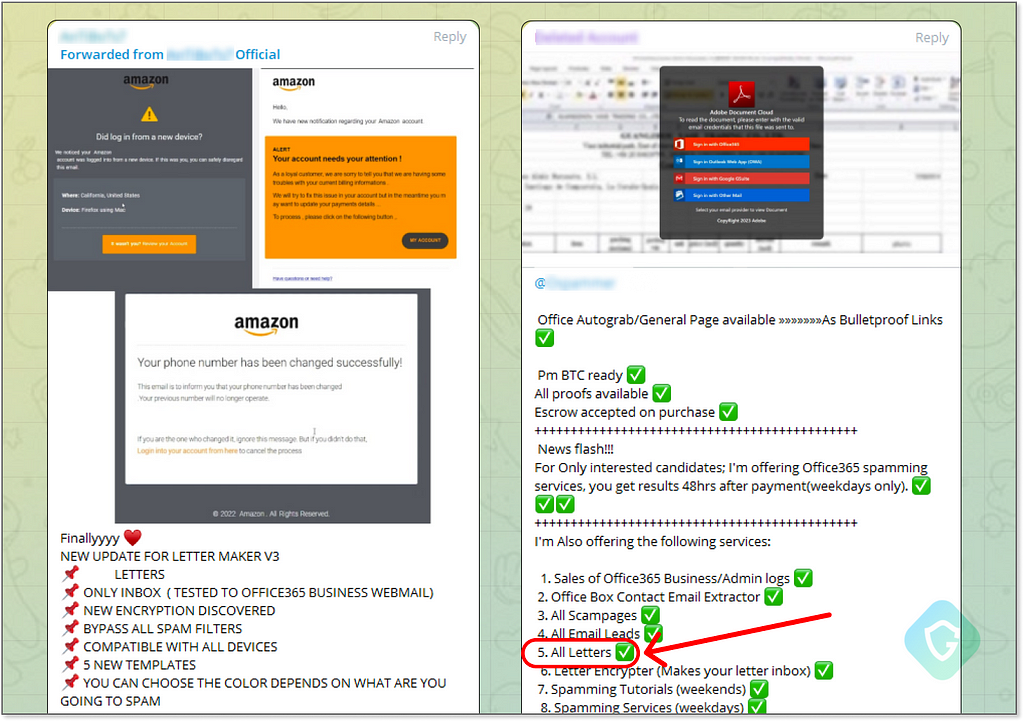
These “Letters” also incorporate techniques to evade spam detection, such as randomizing content between messages, inserting invisible characters, and using images instead of scannable text. Many also include embedded analytics tools to track if the email has been read and to pinpoint the location of the recipient. This allows for a more strategic management of the “marketing” campaign.
Fortunately, our purchased scampage of Bank of America already came bundled with a “Letter“:
To ensure its success, as it was probably used in the past already, one can edit it a bit, change the text, and reformat it to make it unique. And so, we are ready with everything needed to send those emails. Well, almost…
Leads — Exploiting Stolen Contact Data
With our setup ready, time is of the essence to dispatch those emails before the fragile mailers are detected and blocked. We just need to know whom we are going to send them to. It’s time to acquire a substantial list of relevant and active email addresses — ideally, at least 100,000.
These lists, known as “leads” in scammer lingo, are a bulk of contact information of potential targets. They typically include email addresses and phone numbers, and sometimes they’re enriched with additional personal information like names, physical addresses, and other data that might have been leaked or stolen. These leads can be incredibly specific, tailored for any region, niche, demographic, specific company customers, and more.
“Your Personal Details Have Been Leaked!”
Does this alarming message sound familiar? This is precisely what happens to your details after they are leaked. Your private details become ‘leads’ — that hackers exploit for further malicious activities!
Every piece of personal information adds to the effectiveness and credibility of these attacks. This underscores the importance of having a comprehensive understanding of one’s leaked data. At Guardio, we address this through our “Leaks” feature, which involves deep scanning of the dark web for any bit of personal information compromised and promptly informing our users, ensuring real-time awareness and protection.
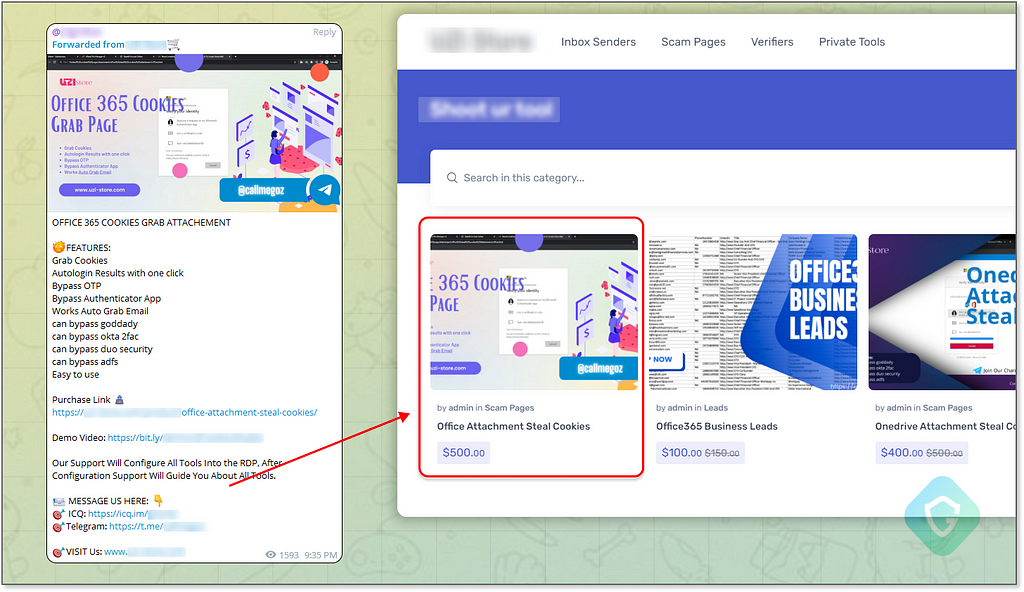
Some sellers even specialize in providing leads for individuals who are likely to be more vulnerable or lucrative targets for scams — such as those with higher incomes, homeowners, business owners, the elderly, and other demographics deemed more susceptible to fraud. These targeted leads increase the chances of a successful scam.
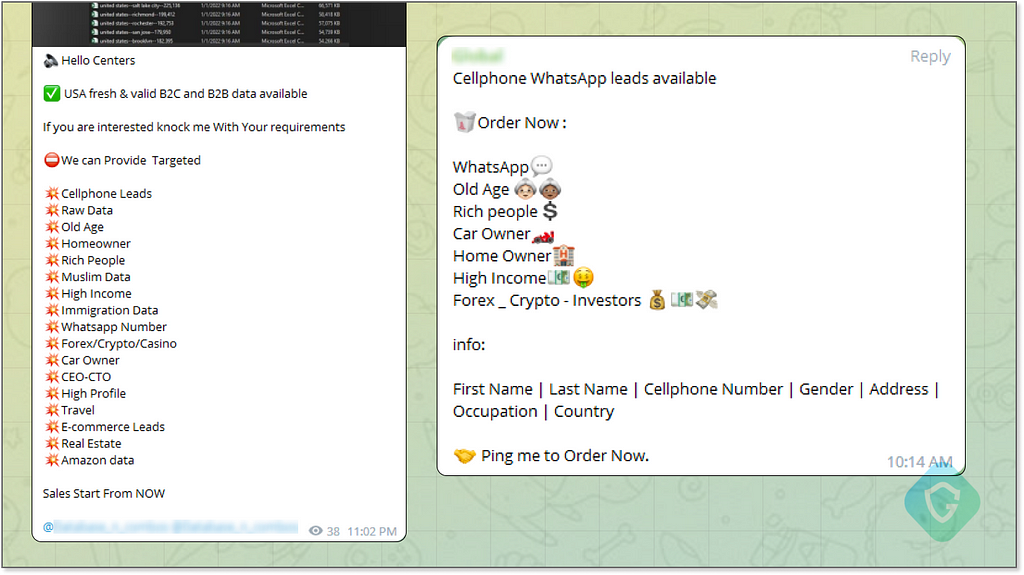
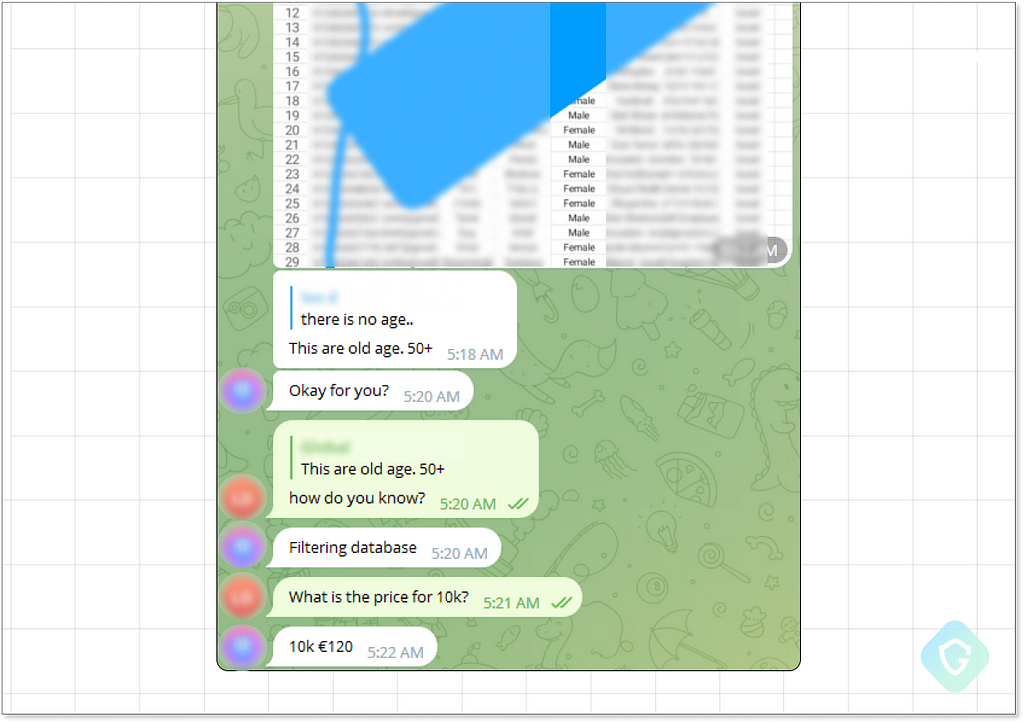
The origins of these lead lists can vary significantly among sellers. Some acquire them by sifting through data leaks from major companies, which occasionally are available for free. For instance, a data breach at a bank can easily yield a list of its account holders. The more detailed the information in the data leak, the easier it is to compile a comprehensive and precise list.
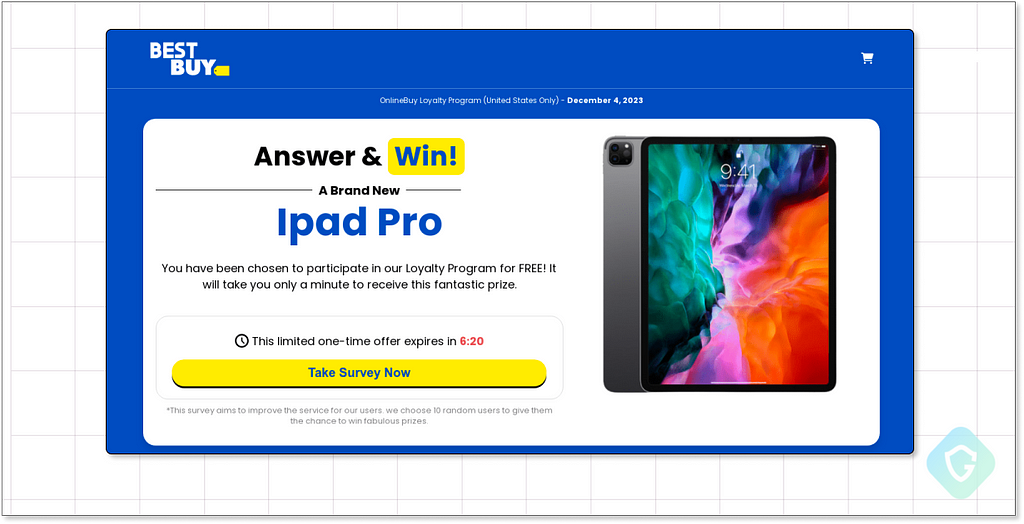
Other sellers, particularly those offering more high-end services, gather their lists through survey scams. These are deceptive websites that lure users with the promise of rewards for answering questions, only to harvest and sell their private data.
Ever seen one of these? You didn’t really win an iPad — you just gave away your info to scammers for their next targeted campaign.
For the final piece of our phishing scheme, securing a precise and relevant leads list is critical. Following some negotiation, we acquired a list of 100,000 Bank of America customers. This list is particularly valuable due to its relevance and targeting, hence it comes at a significant cost. We spend an additional $200, bringing our total expenditure to $230. Now, we are just a click away from launching our campaign!
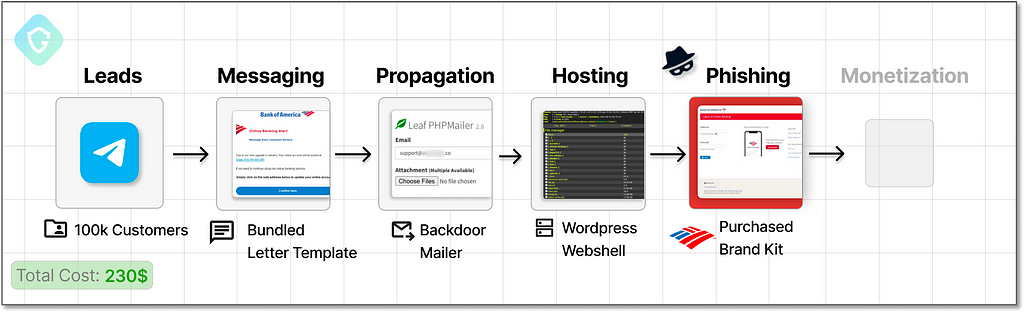
Time to Monetize — Exploit Or Sell To Bigger Fish!!
“Congratulations”! Our (definitely not real) first phishing campaign is up and running!

Our efforts soon start to bear fruit. Victims fall for the trap, clicking on the link and some even proceed to log into the fraudulent bank site — our scampage. Once they do this, their bank accounts become compromised.
The balance in these accounts varies; some hold minimal funds, while others have substantial balances. Extracting cash from these accounts is a whole different level of criminality, and significantly more complex. This is where the scammer’s supply chain comes into play.
As smaller-scale scammers, who only need a computer, some free time, and an internet connection to execute their schemes and gather a multitude of stolen credentials, are effectively fueling the supply chain for the bigger players. These more sophisticated and organized criminal groups purchase these credentials (a.k.a “Logs” in underworld lingo) to further their illicit operations.
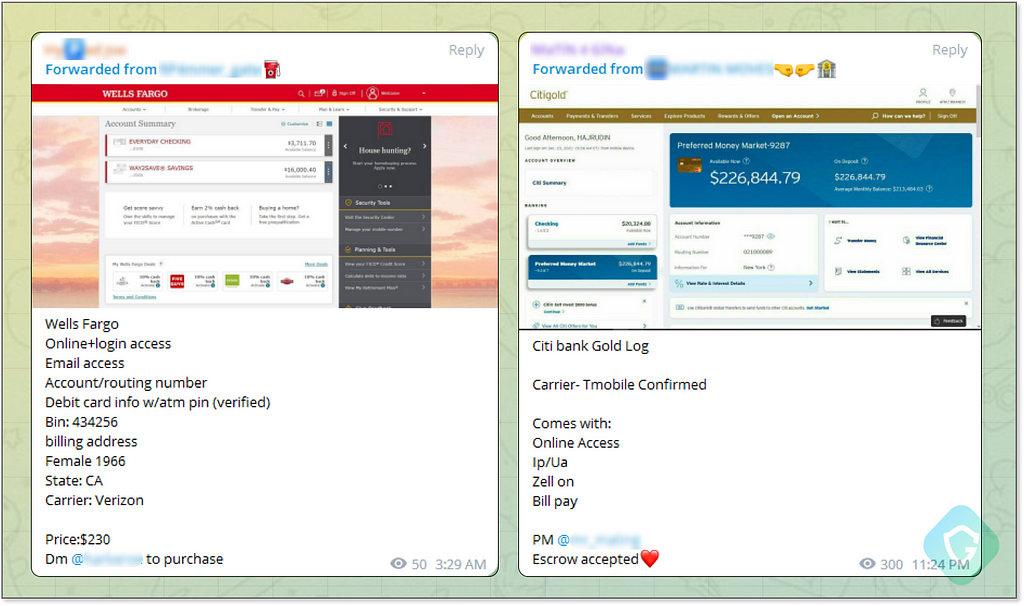
Social media account credentials are sold for as little as a dollar, while banking accounts and credit cards could be sold for hundreds of dollars — depending on their validity and funds.
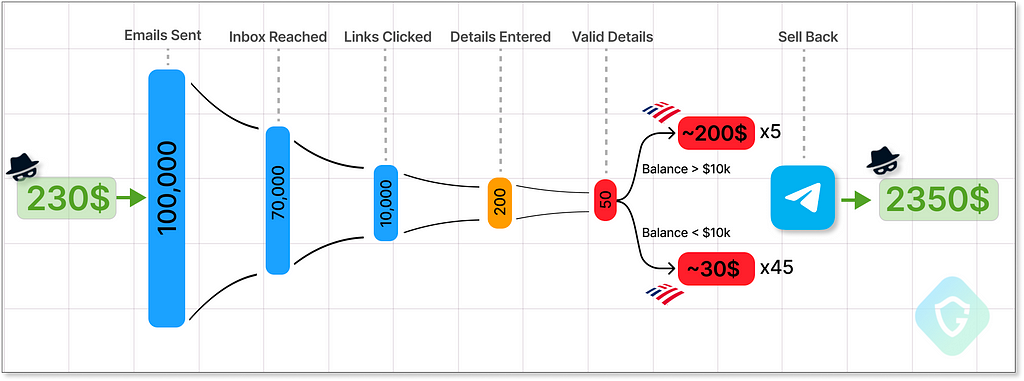
Simulating Revenues of our Illicit Operation
Now, let’s play the numbers game and assume the worst-case financial scenario to illustrate the minimal financial gain these types of scam activities might yield.
After sending 100k emails to relevant BOA customers, let’s say we get only 50 valid bank account details. These accounts can now be exploited or sold up the supply chain to other criminal entities or scammers.
Let’s say five of those have a decent 10k+ USD balance we can sell at around 200$ each, and the rest for around 30$. Assuming the following funnel we can make a 10x return on our investment. Not bad!
Summing Up Our Dark Markets Shopping Spree
These markets have transformed significantly from the hidden, invite-only forums of the DarkNet. Now, they are public channels on mainstream platforms, teeming with thousands of users and daily activity. Sellers build reputations and offer “free samples,” “customer support,” “trial versions,” and even “money-back guarantees” — terms previously associated with legitimate businesses, signifying the emergence of a real industry with substantial financial stakes.
Unfortunately, with just a small investment, anyone can start a significant phishing operation, regardless of prior knowledge or connections in the criminal underworld. Those campaigns even leverage advanced detection and MFA mitigations that easily circumvent protections we blindly rely on.
While we’ve covered a range of services, this is merely scratching the surface. There’s a plethora of other operations like SMS, carding, money laundering, advertising services, unethical SEO solutions, and much more.
A Broader Implication on Web Security
Note how tools for phishing campaigns are often sourced through compromising legitimate websites, services, and accounts. A prime example is vulnerabilities in WordPress sites belonging to organizations, small businesses, or educational institutions, not adequately protected against known security threats.
This situation highlights a dual responsibility for site owners. They must safeguard not only their business interests but also protect against their platforms being used by scammers for hosting phishing operations, sending deceptive emails, and conducting other illicit activities, all unbeknownst to them.
At Guardio, our Labs research team is deeply embedded in monitoring the underground cyber world, keeping a watchful eye on emerging threats. Our mission is dual-purpose: firstly, to increase awareness about these malicious activities and secondly, to enforce the Guardio protection suite and the rest of the cyber security ecosystem with strong strategies and techniques to counter them effectively.
Source: Original Post
Views: 4