Summary: In May 2024, Kaspersky Labs revealed a targeted malware campaign named SambaSpy, specifically aimed at Italian-speaking users. This sophisticated Remote Access Trojan (RAT) utilized a unique approach to ensure that only users with Italian language settings were infected, showcasing a high level of customization and precision in its execution.
Threat Actor: Unknown | unknown
Victim: Italian users | Italian users
Key Point :
- The SambaSpy malware was delivered through phishing emails disguised as legitimate communications from an Italian real estate company.
- Infection was contingent upon the victim’s system language being set to Italian, demonstrating a highly targeted approach.
- SambaSpy offers extensive control over infected devices, including file management, keystroke logging, and remote desktop capabilities.
- Despite its focus on Italy, traces of Brazilian Portuguese in the malware suggest potential broader targeting ambitions by the attackers.
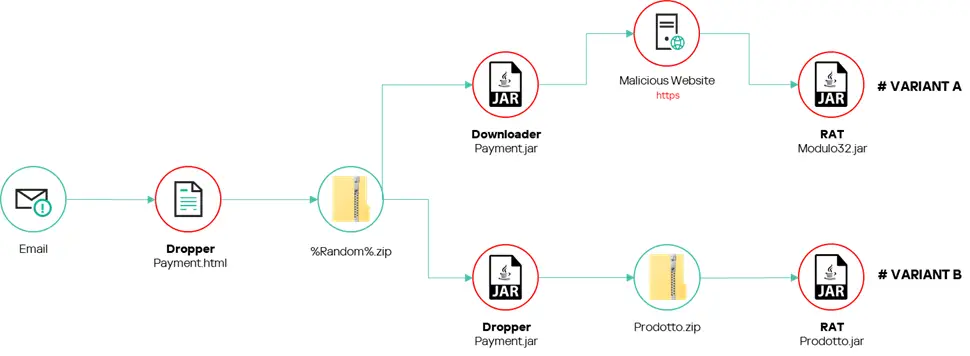
In May 2024, Kaspersky Labs uncovered a sophisticated malware campaign exclusively targeting users in Italy. Unusual for cybercriminal activities, this campaign focused solely on Italian victims, deploying a new Remote Access Trojan (RAT) dubbed SambaSpy. What makes this campaign stand out is the precision with which the attackers ensured their malware only infected Italian-speaking users, as detailed in Kaspersky’s latest report.
While many malware campaigns target broad geographic regions, this campaign was specifically designed to infect only Italian users. At multiple stages in the infection chain, checks were implemented to verify the system language was set to Italian. If the target didn’t meet these criteria, the malware would simply halt its execution, demonstrating a high degree of customization.
SambaSpy was delivered through a malicious email appearing to come from a legitimate Italian real estate company, written in perfect Italian. The emails typically contained a link to view an invoice, redirecting users to a legitimate document-sharing platform used by Italian businesses. However, beneath this legitimate-looking façade, the attackers embedded a malicious link leading to a JAR file, the first stage of the SambaSpy infection.
Once installed, SambaSpy grants attackers nearly full control over the infected device. Written in Java and obfuscated using the Zelix KlassMaster protector, SambaSpy is equipped with a wide array of features that allow it to:
- Manage files and processes
- Upload and download files
- Control the webcam
- Log keystrokes and clipboard activity
- Take screenshots
- Steal credentials from popular browsers like Chrome, Edge, and Brave
- Execute remote desktop operations
- Start a remote shell
The malware’s capabilities extend to loading additional plugins at runtime, further expanding its range of attacks depending on the victim’s environment.
Kaspersky identified two infection chains in this campaign, both starting with an email. In the more elaborate case, the victim would receive an email from a German address but written in Italian, urging them to view an invoice. After clicking the link, the victim would be redirected to a legitimate Italian cloud invoicing service—FattureInCloud—to display an actual invoice. However, behind the scenes, victims matching the Italian-language check would be redirected to a malicious OneDrive link, leading to the SambaSpy dropper.
Interestingly, if a victim’s system didn’t match specific criteria—such as running Edge, Chrome, or Firefox with the language set to Italian—they would be left on a legitimate website, avoiding infection. This level of precision in targeting highlights the expertise of the attackers.
Despite the campaign’s exclusive focus on Italian victims, Kaspersky found traces pointing to Brazil. Brazilian Portuguese language artifacts, such as code comments and error messages, were found within the malware and malicious domains. The campaign’s infrastructure also contained links to other regions, including Spain and Brazil, suggesting the attackers could have broader ambitions beyond Italy.
Related Posts:
Source: https://securityonline.info/sambaspy-rat-targets-italian-users-in-a-unique-malware-campaign