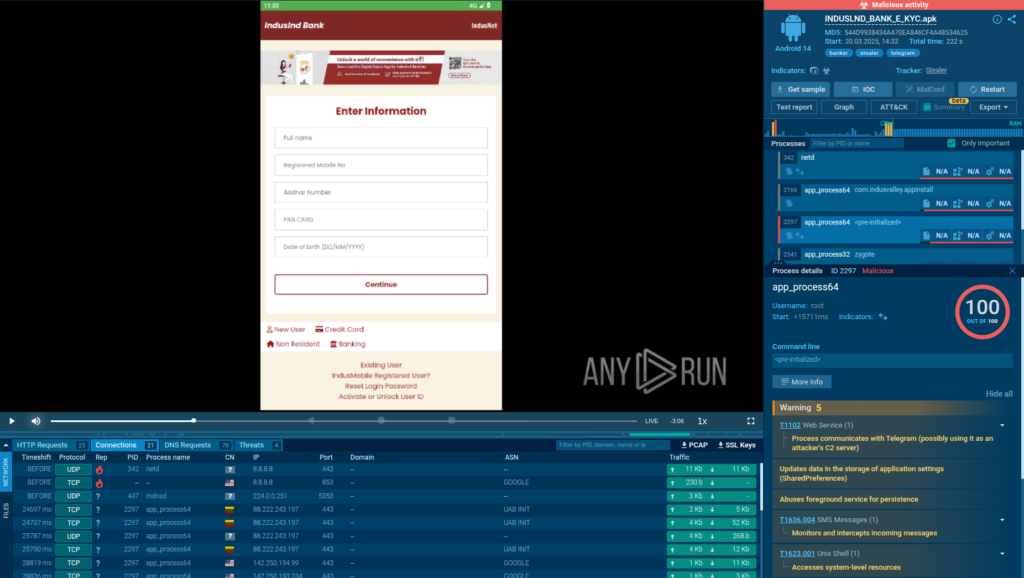
The report discusses Salvador Stealer, a new Android malware posing as a banking application to steal sensitive user data, such as banking credentials and personal information. The malware employs phishing techniques and has multiple methods for exfiltrating data, including SMS interception and real-time communication with a Command and Control (C2) server via Telegram. The exposed infrastructure offers insight into the threat actor potentially being based in India. Affected: Android users, Financial institutions
Keypoints :
- Salvador Stealer is an Android malware masquerading as a banking application.
- It employs a dropper APK to install and initiate the actual banking credential stealer payload.
- Users are tricked into providing sensitive data through an embedded phishing website.
- Data is exfiltrated in real-time to both a phishing server and a Telegram C2 server.
- The malware captures incoming SMS to facilitate OTP theft, bypassing two-factor authentication.
- Debugging and analysis were conducted using the ANY.RUN Android sandbox.
- Persistence mechanisms ensure the malware restarts after termination and survives device reboots.
- Phishing infrastructure includes accessible admin panels hinting at a potential geographic location of the attacker.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: The malware uses Telegram Bot API to exfiltrate stolen data.
- T1070.001 – Indicator Removal on Host: The malware hides its activities and utilizes persistence methods.
- T1133 – External Remote Services: The malware connects to a C2 server via Telegram.
- T1056.001 – Input Capture: Phishing credentials from the user via a fake banking interface.
- T1203 – Exploitation for Client Execution: The installation of the banking app involves the dropper APK exploiting user permissions.
Indicator of Compromise :
- [URL] hxxps://t15.muletipushpa.cloud/page/start.php
- [URL] hxxps://t15.muletipushpa.cloud/admin/login.php
- [Telegram Bot URL] hxxs://api.telegram.org/bot7931012454:AAGdsBp3w5fSE9PxdrwNUopr3SU86mFQieE
- [SHA256] 21504D3F2F3C8D8D231575CA25B4E7E0871AD36CA6BBB825BF7F12BFC3B00F5A
- [Phone Number] +916306285085
Full Story: https://any.run/cybersecurity-blog/cybersecurity-blog/salvador-stealer-malware-analysis/