This article discusses the rise of macOS-targeting malware, particularly from North Korean APT groups, focusing on two notable malware samples: RustDoor and Koi Stealer. RustDoor disguises itself as a legitimate software update, while Koi Stealer, which is previously undocumented, primarily aims to steal sensitive data, including cryptocurrency wallet information. The campaign highlights the risks from state-sponsored cybercrime, especially in the tech industry. Affected: macOS, cryptocurrency sector, software development industry
Keypoints :
- Increasing prevalence of macOS malware related to cybercrime.
- North Korean APT groups heavily involved in targeting software developers in the cryptocurrency sector.
- RustDoor is a Rust-based malware that masquerades as a legitimate update.
- Koi Stealer is an undocumented variant that aims to collect sensitive data.
- Attackers employ social engineering tactics to spread malware.
- Detectable patterns of behavior such as executing multiple malware variants and utilizing reverse shells.
- An assessment indicates that these attacks are likely state-sponsored.
- Palo Alto Networks offers protection against these particular malware threats.
MITRE Techniques :
- T1071 – Application Layer Protocol: The malware uses HTTP/S for command and control communication.
- Tactic: Credential Access, Techniques: T1537 – Default Credentials: The Koi Stealer attempts to steal credentials from local storage.
- T1566 – Phishing: The campaign utilizes social engineering by posing as recruiters to distribute malware.
- T1041 – Exfiltration Over Command and Control Channel: Data is exfiltrated to C2 servers using established connections.
- T1560 – Archive Collected Data: The Koi Stealer gathers various file types related to sensitive information before exfiltration.
Indicator of Compromise :
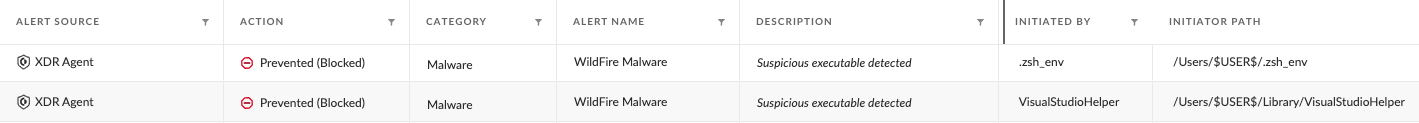
- [File] .zsh_env
- [Hash] MD5: a900ec81363358ef26bcdf7827f6091af44c3f1001bc8f52b766c9569b56faa5
- [Domain] apple-ads-metric[.]com
- [IP Address] 31.41.244[.]92
- [Hash] SHA256: c42b103b42d7e9817f93cb66716b7bf2e4fe73a405e0fbbae0806ce8b248a304
Full Story: https://unit42.paloaltonetworks.com/macos-malware-targets-crypto-sector/