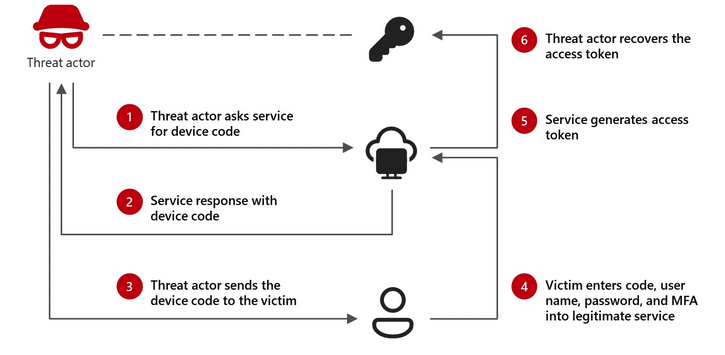
Summary: A Russia-linked threat actor, tracked as Storm-2372, is executing a widespread device code phishing campaign targeting various sectors including government and private organizations globally. Using authentication codes to bypass conventional security measures, the actor has successfully compromised numerous accounts while maintaining persistence through stolen tokens. The threat actor has also adopted sophisticated tactics involving social engineering to lure victims into providing access credentials.
Affected: Government, IT, defense, telecoms, health, education, energy sectors, and NGOs
Keypoints :
- Storm-2372 targets organizations in Africa, Europe, the Middle East, and North America since at least August 2024.
- Phishing emails often include fake Microsoft Teams invitations to trick victims into submitting device codes.
- The actor utilizes Microsoft Graph to search victims’ emails for sensitive information and may leverage regionally appropriate proxies.
- Recent shifts in tactics include using Microsoft Authentication Broker’s client ID for enhanced access capabilities.
- Similar techniques are reported to be used by other Russia-linked actors such as CozyLarch, UTA0304, and UTA0307.
Source: https://www.securityweek.com/russian-state-hackers-target-organizations-with-device-code-phishing/