Summary: A new threat named “Rilide” has emerged as a malicious browser extension that steals sensitive user information, primarily targeting Chromium-based browsers. Disguised as legitimate extensions like Google Drive, Rilide employs deceptive tactics including phishing campaigns and PowerShell loaders to install itself and capture data such as passwords and cryptocurrency credentials. Researchers have documented various methods used for its distribution and the complex processes involved in its installation and data exfiltration.
Affected: Users of Chromium-based browsers (Google Chrome, Microsoft Edge, etc.)
Keypoints :
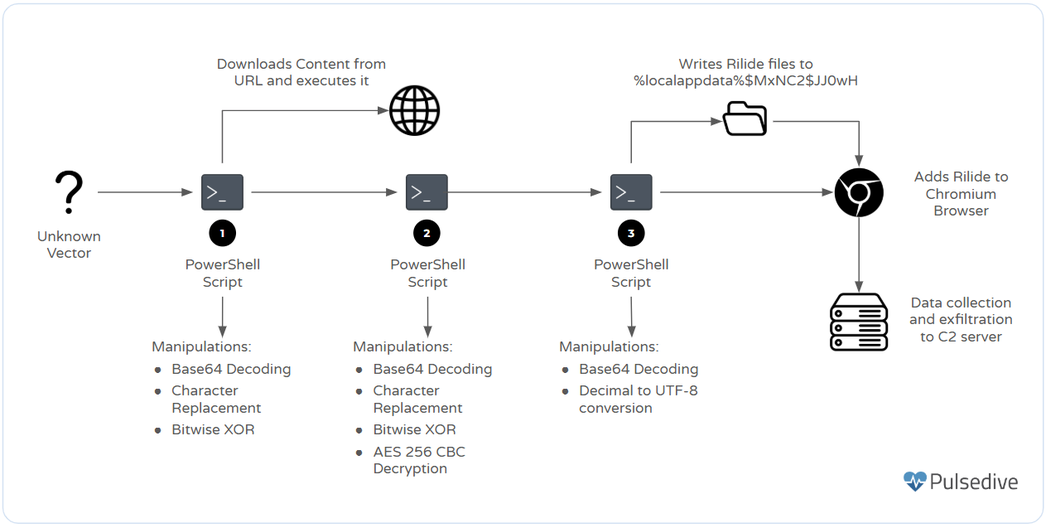
- Rilide operates through phishing sites and malicious advertisements, often using well-known extensions as a facade.
- Multiple delivery campaigns have been identified, including PowerPoint lures and Twitter-based redirection to phishing sites.
- The extension has the capability to access system information, collect clipboard data, and even take screenshots, posing a significant risk to user privacy.
- The PowerShell scripts involved in its installation employ complex obfuscation techniques and manipulate encoded data for execution.
- Rilide communicates with a command and control server to exfiltrate retrieved data, indicating ongoing data theft operations.
Source: https://securityonline.info/rilide-the-browser-extension-stealing-your-crypto/