On February 21st, 2024, Cofense Intelligence identified an advanced phishing campaign that targeted the Oil and Gas sector to deliver Rhadamanthys Stealer, an advanced information stealer offered as Malware-as-a-Service (MaaS). The campaign incorporates several complex tactics, techniques, and procedures (TTPs) along with a unique vehicle incident lure that spoofs the Federal Bureau of Transportation. This campaign follows close behind several updates to the Rhadamanthys MaaS on the market place, and law enforcement’s takedown of the LockBit Ransomware group, one of the most notorious Ransomware-as-a-Service on the market. Due to the uniqueness of the campaign and success rate at which emails were reaching targets, a Cofense Intelligence Flash Alert New MaaS InfoStealer Malware Campaign Targeting Oil & Gas Sector was published along with an Active Threat Report.
Key Points
- The phishing emails use a unique vehicle incident lure and, in later stages of the infection chain, spoof the Federal Bureau of Transportation in a PDF that mentions a significant fine for the incident.
- TTPs in this campaign follow suit with those known to assist in bypassing secure email gateways (SEGs) and other layers of security infrastructure that are in place to quarantine malicious emails.
- Overall, the goal of the campaign is to infect users with Rhadamanthys Stealer, an advanced MaaS that is uncommon in the phishing threat landscape.
- Based on a report by Cyberint, Rhadamanthys Stealer received major updates (update 5.0) earlier this year that has led to improved stealing capabilities and evasion tactics.
- This campaign appeared within days of the law enforcement takedown of the LockBit ransomware group. While this could be a coincidence, there were reports of Rhadamanthys Stealer used in the delivery of LockBit ransomware in 2023.
Phishing Campaign Targeting Oil & Gas Sector
As of this report, the targets for this campaign have primarily been in the Oil and Gas sector. It is not clear as to why this specific sector is, but the campaign in its current form could be relevant in most sectors if threat actors decided to change targets. While the campaign was actively sending emails, it was successfully reaching targets at an alarming rate. This is attributed to a combination of commonly used TTPs known to disrupt analysis. By joining multiple TTPs, like trusted domains, multiple redirects, and clickable images, threat actors can increase the chances that their emails will bypass the current email security standards and reach targets. Figure 1 shows the infection chain for this campaign from the threat actor to the final Rhadamanthys Stealer executable.

Figure 1: Infection chain of the phishing campaign.
The campaign starts with threat actors crafting a unique subject and body for each email with the overall theme being the recipient’s vehicle being involved in an incident. The first malicious indicator is a link embedded in the email that abuses an open redirect, a vulnerability on a website that allows threat actors to leverage a specific path on a legitimate domain to redirect victims to a malicious location. Open redirects in this campaign are primarily hosted on legitimate Google domains, specifically Google Maps and Google Images. The embedded link redirects to a URL shortener, a URL generated to reduce the size of a URL but also assists in hiding the URL. The URL shortener acts as an additional layer of evasiveness in this campaign, because threat actors typically associate more redirects in the infection chain to have a better chance of SEGs not recognizing the malicious intent of the email, which does seem to be the case.
After the redirection, victims are taken to a clickable PDF file hosted on docptypefinder[.]info, a domain registered on the same day that this campaign was first seen. The PDF, shown in Figure 4 later in the report, is a clickable image that spoofed the Federal Bureau of Transportation and mentions a possible fine of $30,000 for the incident. Clicking on the image downloads or prompts for the download of a ZIP Archive file. This file contains an executable that, when ran, unpacks and initiates Rhadamanthys Stealer. The malware immediately starts a connection with a command and control (C2) location that collects any stolen credentials, cryptocurrency wallets, or other sensitive information.
Vehicle Incident and Urgency Lures
As peculiar as it might seem to use vehicle incidents as a phishing lure, the threat actor(s) here put immense effort to ensure that their emails along with the infection chain target recipient’s emotions. Each email body and subject are both different than the next, but they can be summarized by notifying an employee of a car incident through an employer notification, possible legal actions, or even a notice of contacting law enforcement. Figure 2 below, is an example of one of the phishing emails seen in this campaign. While the subject and body will differ from the other emails, the overall theme still stands, in this case a notification by an employer that the employee had a car accident.
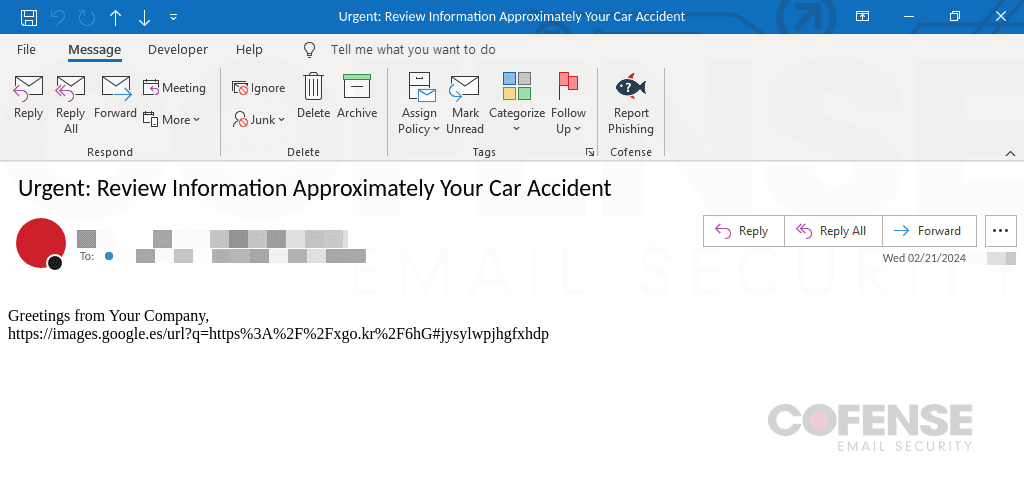
Figure 2: Vehicle incident-themed phishing email delivering Rhadamanthys Stealer.
Due to the volume of emails and the seemingly randomness of each email, Figure 3 was created to give an idea of all the keywords used throughout the entire campaign. Following in line with the campaign, popular words like incident, accident, vehicle, automobile, car, carriage, and other key words are distinctly seen in the word cloud. However, in addition to those, there are several filler words to spark recipient’s emotions like urgent, immediate, required, notification, concerning, and important. The risk level of a phishing threat greatly increases when the threat actors merge TTPs known to aid in bypassing security with well-crafted and socially engineered lures like this one.
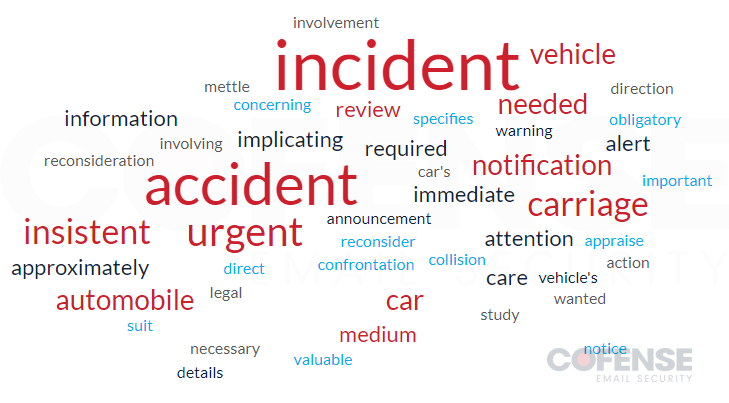
Figure 3: Word cloud of keywords used in email subjects.
Table 1 below is just a sample of how diverse each email subject is. The subjects all follow the same theme but appear to be randomly generated. The common theme consists of emotional filler words like urgent or attention needed, and then a message referencing the accident. Due to the volume of the campaign and uniqueness of each email, it is possible that threat actors incorporated AI or ChatGPT to assist in the different phrases.
Table 1: Different subjects used in the campaign.
| Phishing Email Subjects |
|---|
| Urgent: Review Information Approximately Your Car Accident |
| Attention Needed: Your Vehicle’s Collision |
| Incident Implicating Your Car: Insistent Care Required |
| Notification: Incident Involving Your Vehicle |
| Your Automobile Incident: Urgent Legal action Needed |
In addition to a relatively believable phishing lure, the abuse of an open redirect does add a false sense of legitimacy to the campaign. As seen in Figure 2, the embedded link in the email is hosted on Google Images, which, when considering the theme of the campaign, can make sense to a victim. Especially when you compare it to that of a phishing URL hosted on a random compromised domain.
Once interacting with the embedded link and the multiple redirects, victims are met with the PDF in Figure 4. The image can be extremely convincing given the added distress of a victim thinking their vehicle might be involved in an accident.
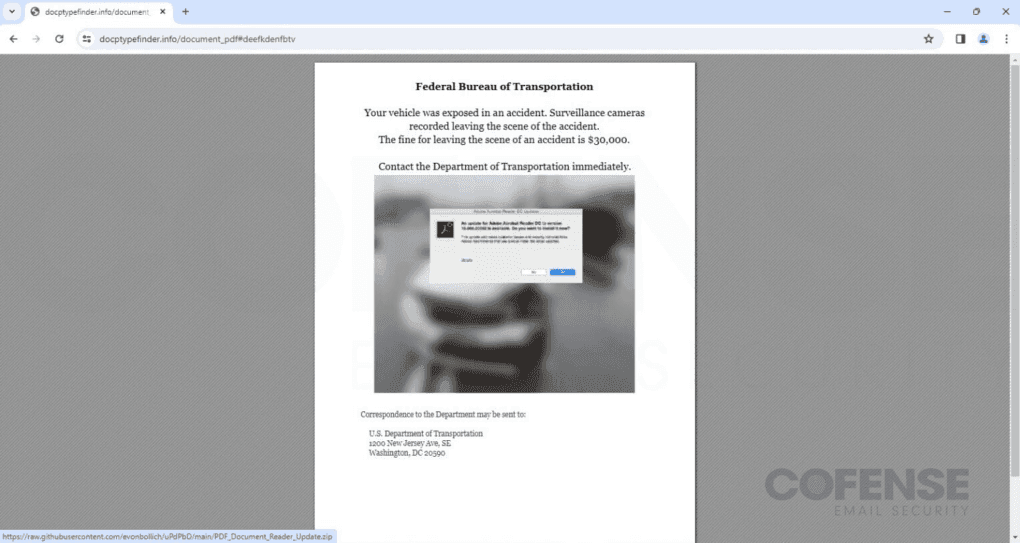
Figure 4: PDF hosted on registered domain docptypefinder[.]info spoofing the Federal Bureau of Transportation.
Rhadamanthys Stealer: Malware-as-a-Service
The uniqueness of this campaign, including the sophisticated social engineering tactics and evasive TTPs are used with the overall goal to infect targets with Rhadamanthys Stealer. This is an uncommon but advanced information stealer malware that is offered as a MaaS for anyone, with access, to purchase via a subscription. The malware is written in the C++ programming language and contains several unique features that make it an ideal choice for threat actors seeking to steal credentials, sensitive information, and cryptocurrency. For credentials, this malware primarily targets those that are stored in various applications and browsers. Once the malware is successfully infected on a machine it will connect to a C2, typically a URL with a unique URL path, in this case the URL ended with [.]gir3n.
MaaS Updates – Likely Reason Behind the Campaign
Rhadamanthys Stealer is a rare sight compared to the more common information stealers seen in the phishing threat landscape. The sudden appearance of such an unusual malware family raises questions as to why the threat actor(s) chose this specific malware, especially given the steep price tags seen in Figure 5. A report released by Cyberint on January 22nd of this year mentions that Rhadamanthys Stealer received several major updates. These updates included additional plugins, stealing capabilities, and evasive tactics for the malware. This is a probable reason for the campaign given that it appeared within such a short timeframe after the updates were released.

Figure 5: Rhadamanthys Stealer logo and pricing.
LockBit Ransomware Takedown
The Rhadamanthys Stealer campaign appeared within days of law enforcement’s takedown of LockBit ransomware group, one of the most active Ransomware-as-a-Service (RaaS). Due to LockBit being offered as a service, the takedown affects more than just the creators. Threat actors seeking to employ the service into their campaigns are also impacted. Considering how similar a RaaS and a MaaS can be, it is not surprising to see a new campaign emerge that incorporated the use of a similar subscription-based service. In addition to that, this is not the first time Rhadamanthys Stealer and LockBit have crossed paths, a report by Threadreader mentions Rhadamanthys Stealer being utilized to deliver a leaked variant of the LockBit ransomware. Showing both the advanced capabilities by Rhadamanthys with the devastating costs that ransomware can bring.