Summary: This content discusses the evolving tactics of phishing attacks, particularly focusing on how threat actors exploit URL rewriting features of email security services to bypass protections. It highlights the alarming trend of attackers manipulating these security measures to deliver malicious links disguised as legitimate URLs.
Threat Actor: Phishing Attackers | phishing attackers
Victim: Organizations Worldwide | organizations worldwide
Key Point :
- Attackers are increasingly using URL rewriting to disguise phishing links, taking advantage of the trust users place in known security brands.
- Recent phishing campaigns have exploited URL protection services from various email security vendors, leading to widespread attacks across multiple organizations.
- Perception Point’s Dynamic URL Analysis offers a proactive approach to detect and neutralize threats before they reach users, outperforming traditional URL rewriting methods.
Threat actors who specialize in phishing are always seeking the most effective methods to deliver their malicious links via email messages. In recent years, we’ve witnessed the rise of new tactics such as QR code phishing (a.k.a. “quishing”) and two-step delivery methods that disguise malicious links behind legitimate services like Canva or Office Forms. These techniques aim to evade both legacy and AI-powered email security solutions. However, since mid-June 2024, a highly alarming trend has emerged – attackers are now turning email security against itself, exploiting URL rewriting features designed to prevent phishing threats. It’s a poetic quid pro quo, but not the kind defenders would necessarily appreciate.
To understand how attackers are increasingly abusing these features, let’s first break down what “URL rewriting” actually is.
What is URL Rewriting?
Different email security vendors may call it by various names (URL protection, click-time-protection, etc.) but URL rewriting serves a singular goal: protecting users from malicious links embedded in emails. The process at its core is quite similar between vendors and involves replacing original URLs with modified links that direct the recipient first to the vendor’s servers. There, the links are scanned for threats when clicked – if deemed safe, the recipient can access it and is redirected to the web content, if not it will get blocked.
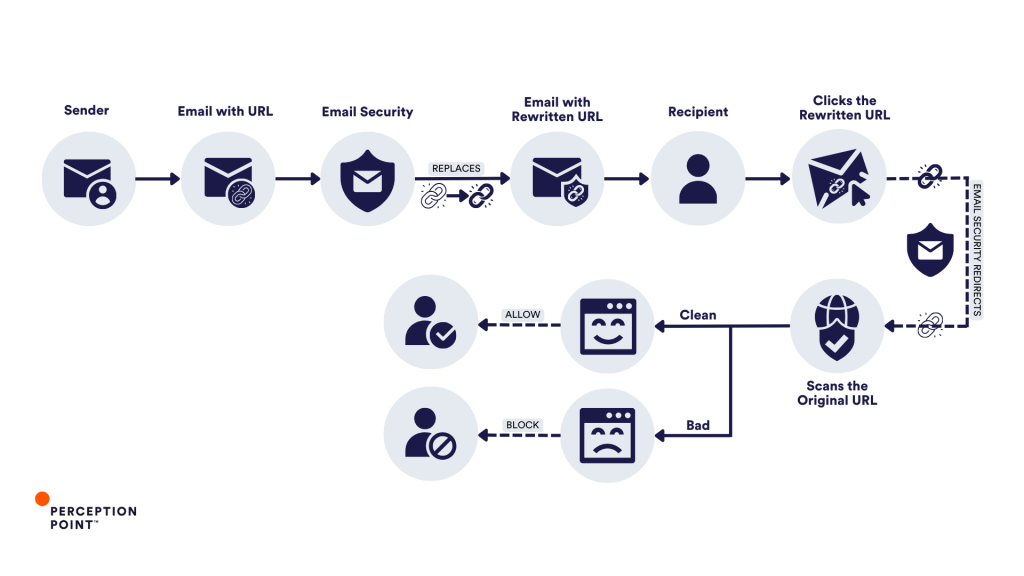
There are two main paradigms for URL Rewriting:
- Legacy security solutions rely on rules and signatures that are based on previously identified threats. These solutions rewrite URLs so that they can assess the link later, leveraging updated threat intelligence and their broad visibility to email traffic. This approach allows them to block a site if new information becomes available – often, unfortunately, after an initial victim has already been hit and reported back to them (“patient zero”).
- The newer approach to URL rewriting is a bit more proactive. It scans links at the time of the click, using technologies like computer vision and machine learning algorithms. Unlike legacy systems, these solutions don’t just rely on known malicious attacks or threat intelligence databases but also evaluate the URL’s behavior in real-time.
Sometimes, organizations use a combination of the two.
For instance, a company might employ a Secure Email Gateway (SEG) like Proofpoint or Microsoft Defender’s native “Safe Links” feature while also using an ICES (Integrated Cloud Email Security) solution for extra protection. In such cases, the ICES solution might embed its rewritten link within the first layer’s rewritten link, let’s call it a “double rewrite.” However, this complexity doesn’t always result in “double protection”.
Much like you do right now reading this blog, attackers too have studied the inner workings of URL rewriting, and now, they exploit it. This has led to an increase in phishing attacks where the very tools designed to protect users against phishing are being used against them.
Lemons to Cyber Lemonade: the URL Rewriting Abuse
Over the past 3 months, Perception Point security researchers have observed a dramatic surge in phishing attacks exploiting the URL protection services of trusted, legitimate email security vendors – SEG and ICES alike. Such well-crafted campaigns have already targeted hundreds of organizations worldwide, potentially impacting many more.
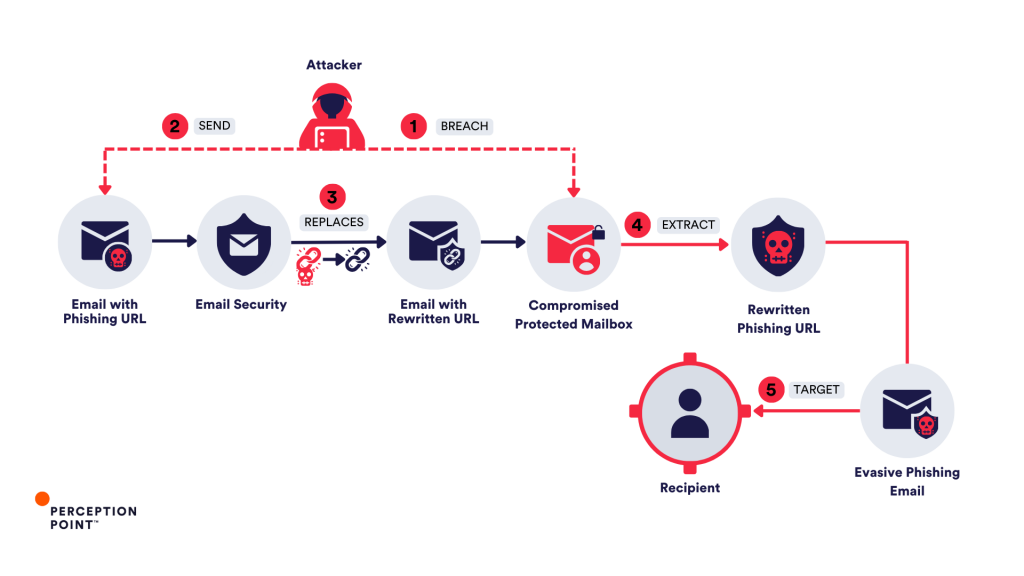
To abuse URL rewriting, attackers typically have 2 theoretical options. The less likely possibility requires gaining access to internal encryption systems of an email security vendor to rewrite phishing URLs directly. However, the more probable tactic is for attackers to first compromise legitimate email accounts protected by a URL rewriting feature and then to send an email to themselves containing their “clean-later-to-be-phishing” URL. Once the email passes through the URL protection service, the link is replaced, and includes the email security vendor’s name and domain, giving it an extra layer of legitimacy. Some email security services, in an effort to save on resources, often whitelist their own dedicated rewriting domains (e.g. protect/defend*name of vendor*.com), which plays directly into the attackers’ hands when they target users protected by specific vendors they abused.
This “branded” rewritten URL is later weaponized. After it has been “whitelisted” by the security service, the attackers can modify the destination of the URL to redirect users to a phishing site. This technique allows the malicious link to bypass further security checks, as many services rely on the initial scan and do not rescan known URLs. As an alternative course of action, attackers often employ advanced evasion techniques such as CAPTCHA evasion or geo-fencing to circumvent even a thorough analysis by the email security vendor.
This manipulation of URL rewriting is particularly dangerous because it takes advantage of the trust that users place in known security brands, making even highly aware employees more likely to click on the seemingly safe link. The threat actors exploit the gap between the time a URL is rewritten and when it is weaponized, bypassing most traditional security tools.
URL Rewriting Attacks Caught by Perception Point
As phishing evolves, attackers are increasingly leveraging creative ways to manipulate URL rewriting services to their advantage. Below are several examples of how Perception Point’s Advanced Email Security detection capabilities intercepted these sophisticated attacks, showcasing the critical role of in-line Dynamic URL Analysis:
Example 1: Double Rewrite Attack – Proofpoint and INKY
In one of the recent URL rewriting attacks intercepted by Perception Point, a sophisticated phishing involved the use of a “double rewrite,” where two email security vendors, Proofpoint and INKY, were exploited.
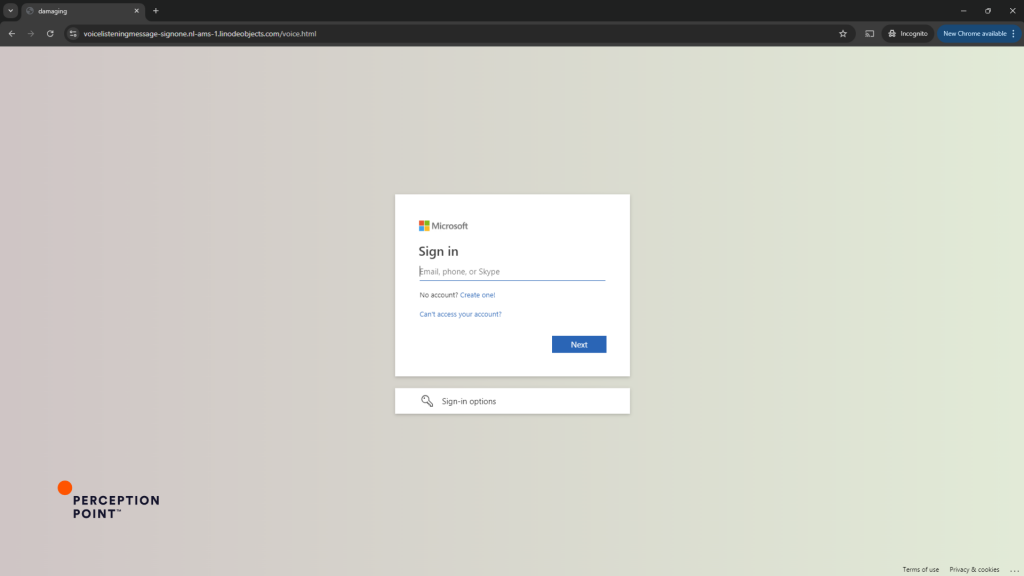
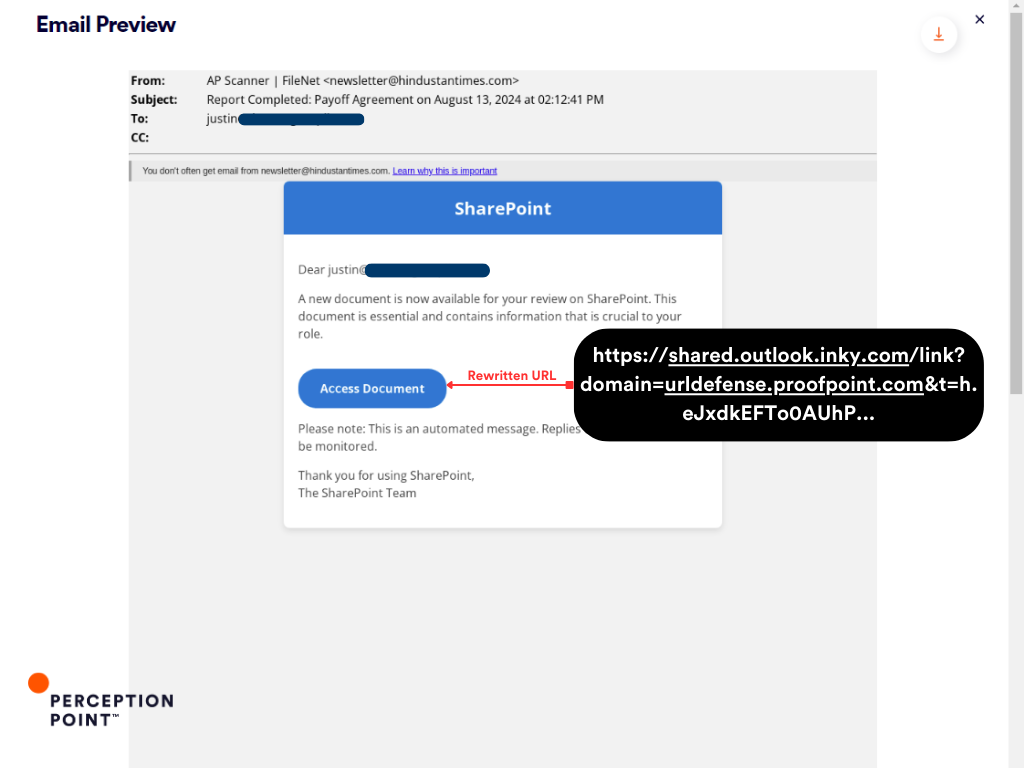
Email: The attacker sent an email message containing a rewritten phishing link disguised as a legitimate SharePoint document notification.
Rewrites: The URL within this email was initially rewritten by Proofpoint’s security system (urldefense.proofpoint.com), the same email underwent a second rewriting process by INKY, embedding its own URL protection link (shared.outlook.inky.com) within the first rewrite.
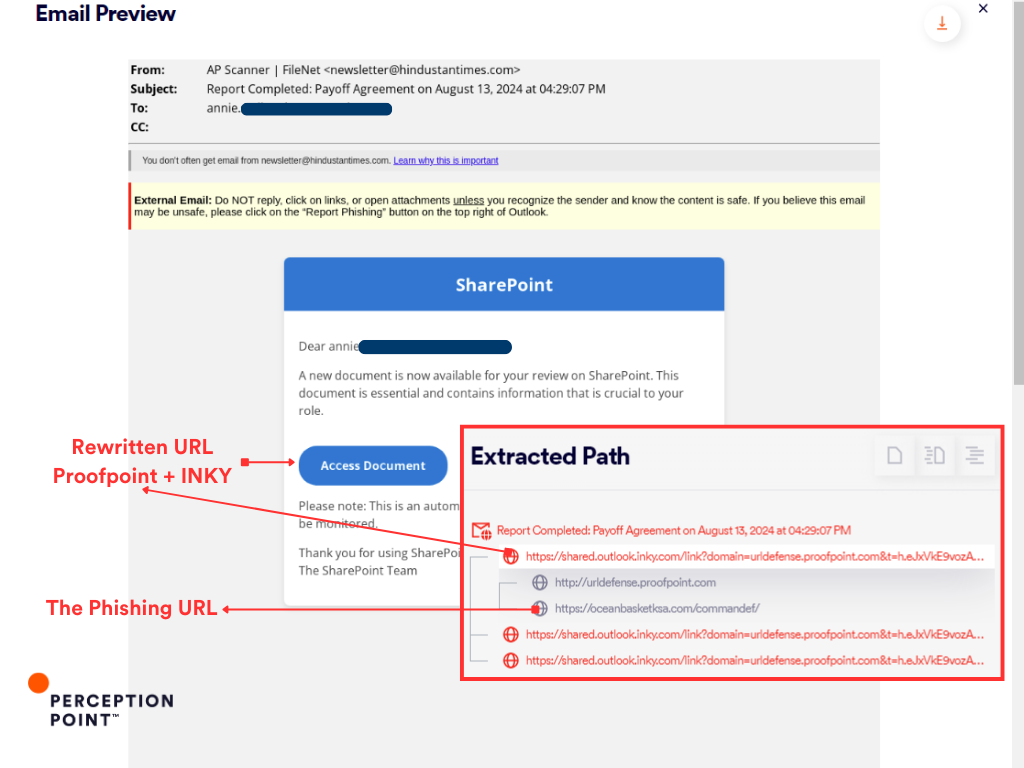
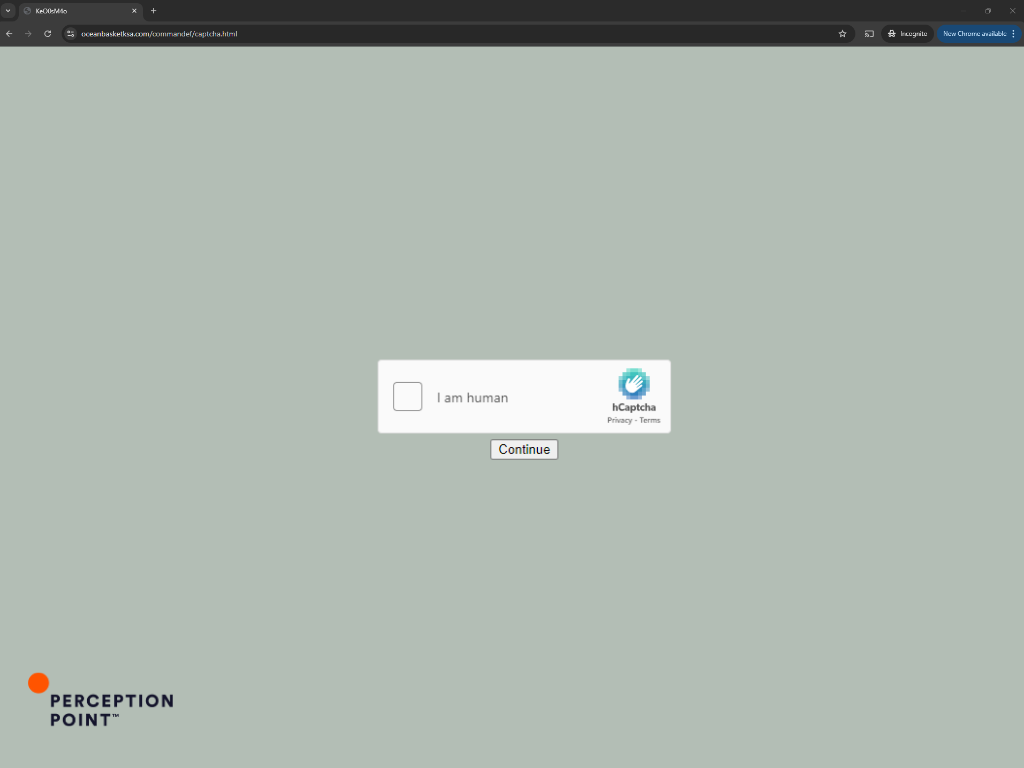
CAPTCHA Bypass: If the target clicked the link, they would have been directed to a custom made CAPTCHA challenge page (as shown in the screenshots). This step is added to evade detection of the automated analysis/threat intel checks by the vendors.
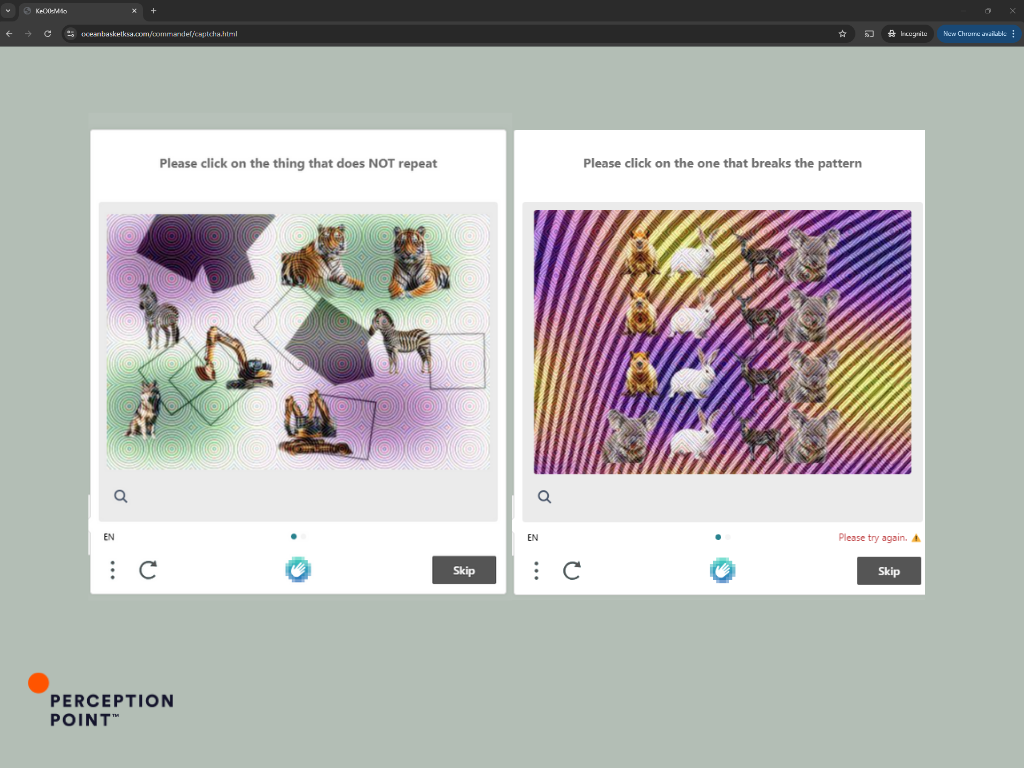
Final Redirect: After solving the CAPTCHA, the user is redirected to a phishing site mimicking a Microsoft 365 login page (shown in the fourth screenshot), where their credentials could be stolen.
Example 2: Exploiting Rewritten URLs Across Multiple Targets – Proofpoint and INKY
In this sophisticated phishing attempt, the attacker used a strategy that involved compromising an organization protected by INKY and Proofpoint URL rewriting service. The attacker generated a rewritten URL using the compromised account and then repurposed this link to target multiple other organizations.
Email: Similar to the first example – a SharePoint notification.
By the time we took this screenshot, the original URL was already reported to be phishing and got blocked as we can see on INKY Link Protection page:
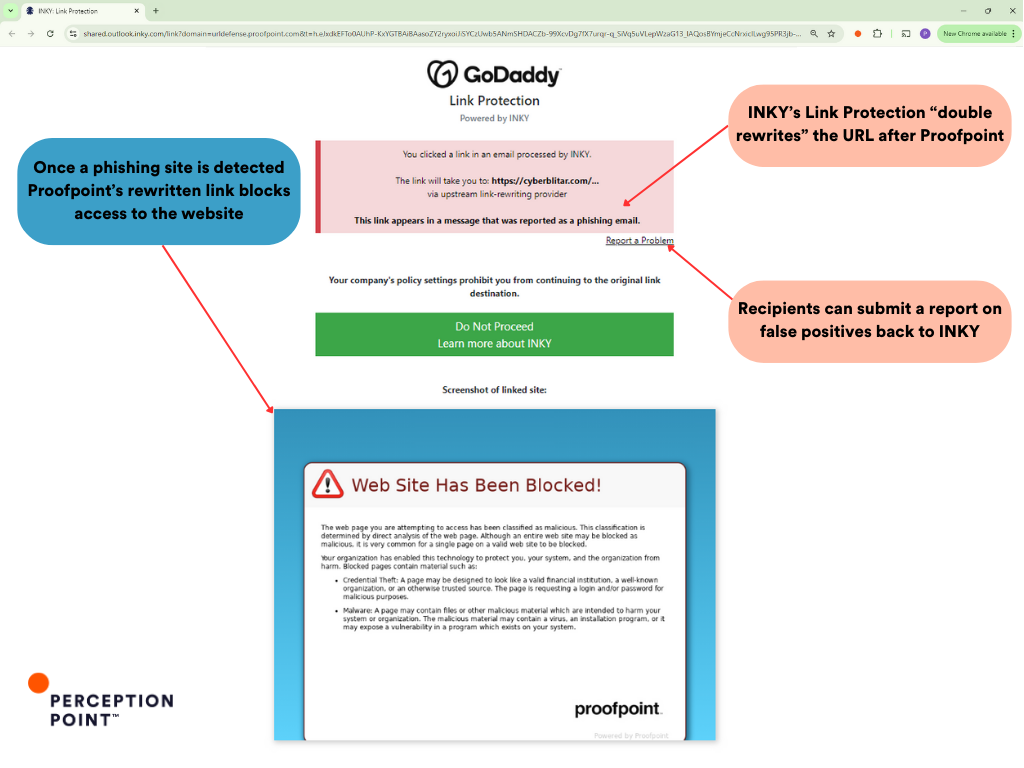
Now if we click the “Report a Problem” button we can sneak a peek into the Modus Operandi of the threat actors. The attackers initially targeted a protected user they have compromised prior, generating a rewritten URL through Proofpoint and INKY’s services. However, instead of only using this link within the compromised organization, the attacker exploited it to target users across various other organizations.
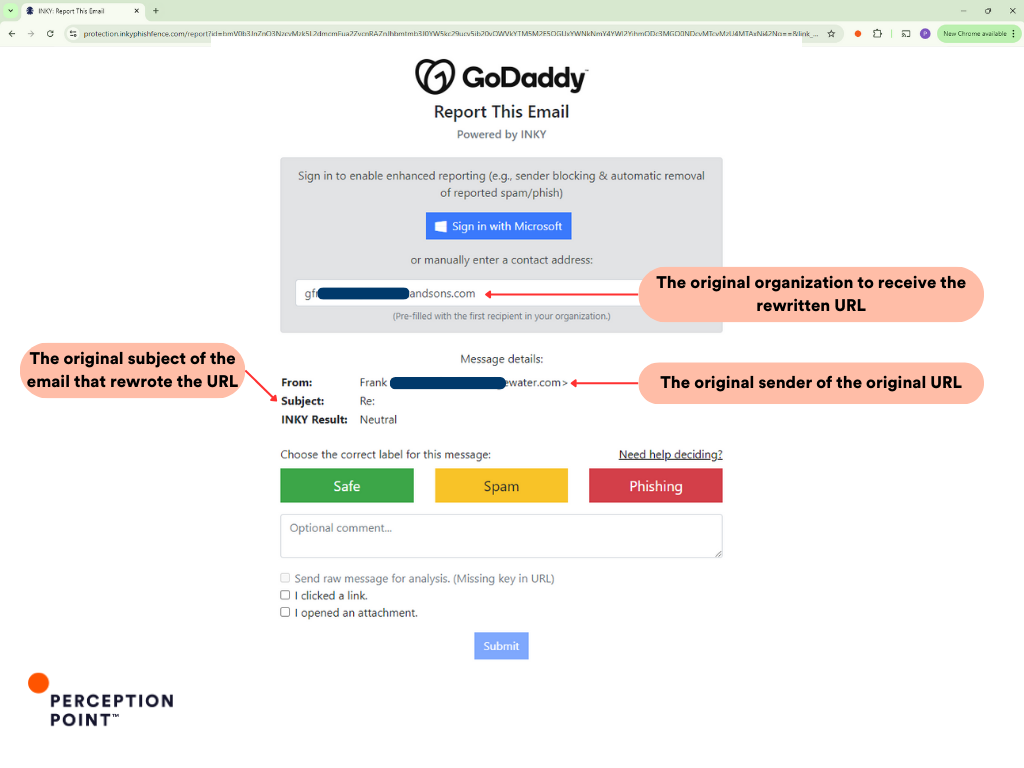
The screenshots reveal that the original recipient of the rewritten URL (the compromised organization) is different from the subsequent targets which Perception Point is protecting. This indicates that the attackers not only exploited the rewritten URL but also utilized it in a broader attack campaign against multiple organizations, leveraging the trust placed in INKY and Proofpoint’s brand and rewriting services.
This example underscores how attackers can manipulate security measures to extend their reach, turning a single point of compromise into a widespread phishing campaign.
Example 3: Exploiting Mimecast’s URL Rewriting
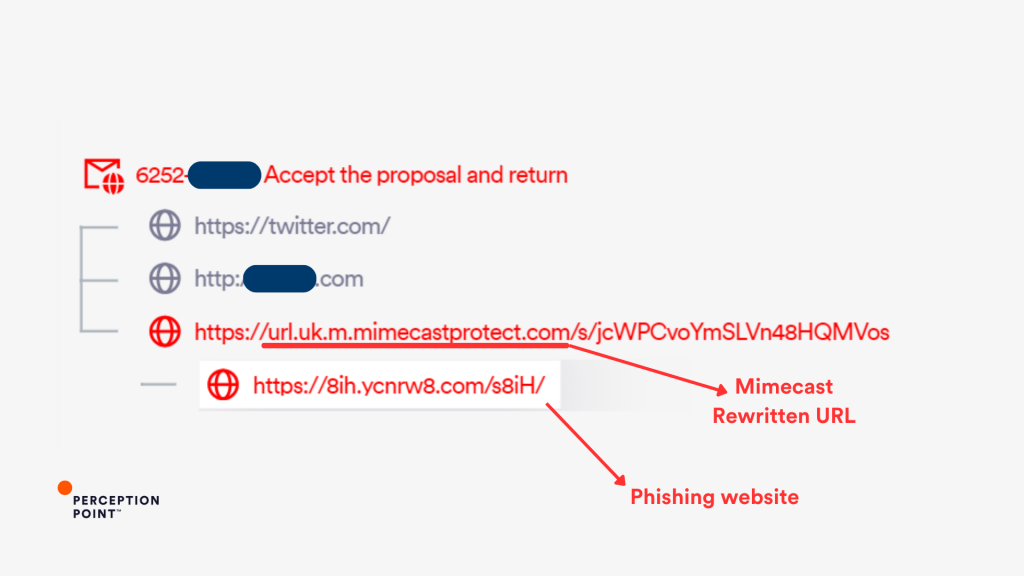
In this instance, Perception Point prevented a phishing attack that likely leveraged Mimecast’s URL rewriting service to disguise a malicious link. The phishing link was rewritten by Mimecast’s URL Protection service, giving it the appearance of a safe URL (mimecastprotect.com). However, the final destination was a phishing site (ycnrw8.com) designed to steal credentials.
Example 4: IRS Phishing Attack via Sophos URL Rewriting
In this potential phishing incident, Perception Point detected an attack where Sophos’s URL rewriting service was used to disguise a malicious link.
Email: The phishing email was crafted to appear as an urgent verification request from a legitimate organization (ID.me + IRS). The URL in the email was rewritten by Sophos, adding a layer of legitimacy.
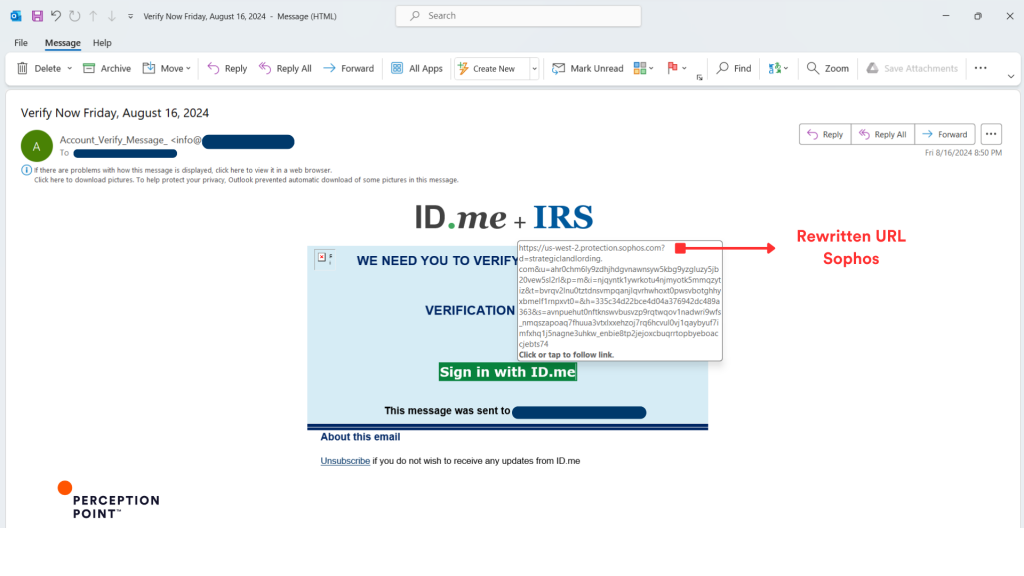
The attacker leveraged the rewritten URL provided by Sophos (protection.sophos.com) to mask the actual phishing destination. The URL appeared safe due to the Sophos domain, making it difficult for the recipient to recognize the threat.
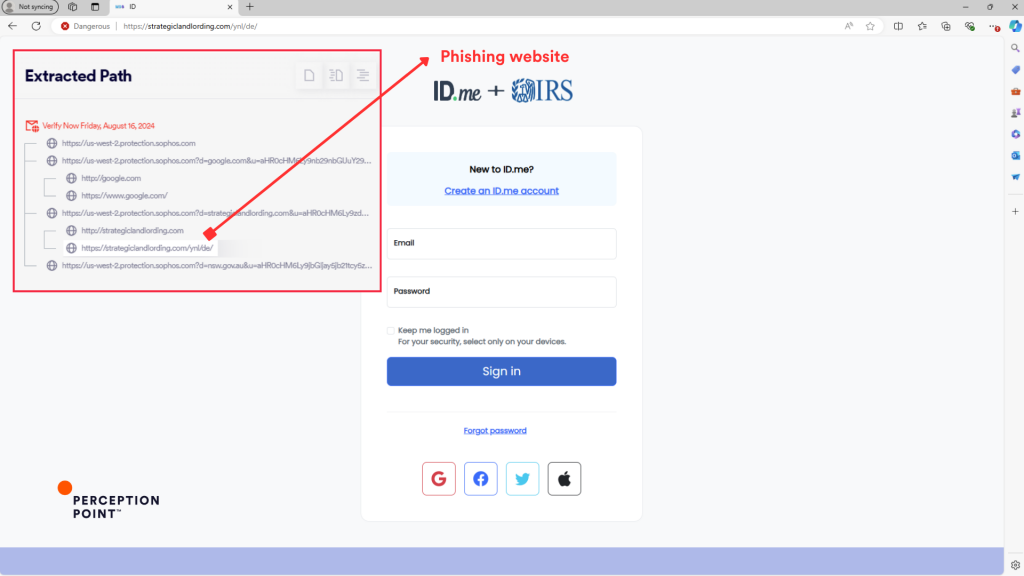
Phishing Site: Upon clicking the rewritten link, the targets are redirected to a phishing website (strategiclandlording.com), designed to harvest personal information under the guise of a legitimate service.
Dynamic URL Analysis: Perception Point’s Answer to URL Rewriting Abuse
Perception Point’s unique Dynamic URL Analysis offers superior protection compared to traditional URL rewriting by actively browsing to new or unknown URLs and analyzing their behavior before the email is even delivered. Unlike URL rewriting, Perception Point leverages in-line computer vision, Large Language Models, and proprietary anti-evasion engines to emulate user behavior and uncover the true payload by following email links to their final destination.
This preventative approach ensures higher detection accuracy and neutralizes even the most evasive and well-masked threats before they reach their target inbox.
- Proactive Detection: By scanning and evaluating URLs in real-time, Perception Point prevents attacks from even entering the inbox, protecting against threats that exploit the gaps left by URL rewriting.
- Advanced Anti-Evasion: Advanced Email Security is equipped to undo evasion tactics, such as CAPTCHA and geo-fencing, ensuring that even the most cleverly disguised threats are detected and blocked.
- Post-Delivery and Meta Analysis: Perception Point’s unique XDR-like infrastructure leverages big data to autonomously rescan and reassess links after delivery, updating verdicts and catching threats that evolve post-delivery.
- Advanced Browser Security: Perception Point’s Advanced Browser Security extension scans URLs upon click from the target’s point of view, ensuring that any malicious activity is detected in real-time.
Source: https://perception-point.io/blog/rewriting-hysteria-rising-abuse-of-url-rewriting-in-phishing