- Short Summary: The Cyber Army of Russia Reborn (CARR) is a prominent hacktivist group known for its disruptive cyberattacks on critical infrastructure and financial systems, primarily targeting entities opposing Russian interests. Their operations include large-scale DDoS attacks and manipulation of Industrial Control Systems (ICS), reflecting a blend of technical and psychological warfare strategies aligned with Russian geopolitical goals.
- Key Points:
- The Cyber Army of Russia Reborn is involved in significant cyberattacks against countries opposing Russian interests.
- They utilize Distributed Denial of Service (DDoS) attacks to disrupt critical services.
- The group has links to the notorious Sandworm unit within Russia’s GRU military intelligence.
- CARR has targeted critical infrastructure in the U.S. and Europe, including water utilities and energy sectors.
- They employ psychological warfare alongside technical disruptions, using platforms like Telegram for coordination and propaganda.
- Recent attacks have included sophisticated operations against Industrial Control Systems (ICS).
- The group is part of a larger coalition of pro-Russian hacker groups, including the High Society alliance.
- U.S. sanctions have been placed on key members of CARR for their cyber activities.
- MITRE ATT&CK TTPs – created by AI
- Information Gathering from Social Media – T1593.001
- Collecting information about targets through social media platforms.
- System Network Connections Discovery – T1049
- Identifying active network connections on a system.
- System Network Connections Discovery – T1016
- Gathering information about network connections to identify potential targets.
- Application Layer Protocol – T1071
- Using application layer protocols for command and control communications.
- Network Denial of Service – T1498
- Executing denial of service attacks to disrupt network availability.
- Endpoint Denial of Service – T1499
- Targeting endpoints to render them unusable through denial of service.
- Manipulation of Industrial Control Systems – T0831
- Interfering with ICS to disrupt essential services.
- Data Manipulation – T1565
- Altering data within systems to achieve malicious objectives.
- Boot or Logon Autostart Execution – T1547
- Establishing persistence through autostart mechanisms.
- Information Gathering from Social Media – T1593.001
In Russian Народная CyberАрмияa (People’s CyberArmy) is a prominent hacktivist group involved in disruptive attacks on critical infrastructure and financial systems, demonstrating significant DDoS capabilities and strategic motivations. However, is the group a hacktivist movement or a Russian state-sponsored threat actor, we shall see.

Threat actor card for Cyber Army of Russia
Who is People’s Cyber Army of Russia
The People’s Cyber Army of Russia or Cyber Army of Russia Reborn is a player in Russia’s hacktivist landscape, conducting cyber threat activities against many countries. This group has been implicated in several significant cyberattacks, including many attacks on Ukraine’s critical infrastructure. Their operations are characterized by the use of Distributed Denial of Service (DDoS) attacks, among other tactics, to disrupt and damage their targets.
However, the Cyber Army of Russia reportedly has its roots in the broader landscape of Russian cyber warfare. This includes activities such as denial of service attacks, dissemination of disinformation, and disruptive activities.

Cyber Army of Russia Reborn’s logo on Telegram
It’s not that surprising, not directly related to the Cyber Army of Russia but Russian cyber actors are frequently reported to be attacking the foreign countries. Early notable operations include the large-scale cyberattacks on Estonia in 2007 and during Russia’s conflict with Georgia in 2008. The GRU, Russia’s military intelligence agency, has been a significant player in these operations, known for its aggressive and high-risk approach.
In this context, it is even claimed that hacktivist groups are involved in Russia’s cyber warfare strategy. For further information check out our blog post about hacktivism.

Roots of Cyber Army of Russia
As reported by Mandiant in April, the origins of the Cyber Army of Russia could be traced back to Sandworm, a notorious cyber unit within Russia’s GRU military intelligence agency. For over a decade, Sandworm has been the Kremlin’s most aggressive cyber warfare force, responsible for some of the most devastating cyberattacks in history. Notable operations include triggering blackouts across Ukraine and unleashing the NotPetya malware, which caused widespread damage globally.

Dark Web Profile: Sandworm APT
The Cyber Army of Russia Reborn has distinguished itself with a series of brazen cyberattacks targeting critical infrastructure in the United States and Europe. Unlike its predecessor, which often prepared for attacks in secret or indirectly impacted victims, the Cyber Army of Russia Reborn has openly targeted water utilities and hydroelectric facilities. Their attacks have involved the manipulation of human-machine interfaces, and software that controls physical equipment, leading to attempts to sabotage essential services.
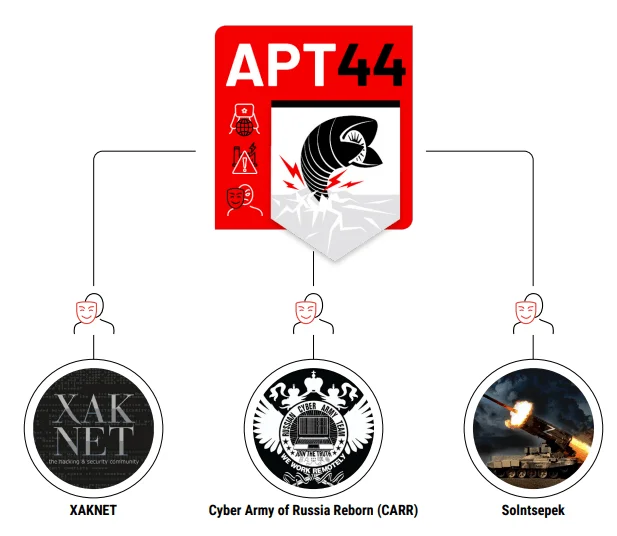
Hacktivist Telegram personas associated with Sandworm/APT44 (Mandiant)
Mandiant has reported that the Cyber Army of Russia Reborn may have been created or supported by Sandworm, noting instances where data stolen by Sandworm was later leaked by this new group. However, it remains unclear whether the Cyber Army of Russia Reborn is simply another cover for Sandworm’s activities or a distinct group that has branched out with its own operations.
Thus, the rise of the Cyber Army of Russia Reborn signals an evolution in Russia’s cyber warfare strategy, and that’s not it, the hacktivist threat landscape grows ever larger, and not only the Russian groups are involved.
High Society and Holy League
The “High Society” hacker alliance has emerged as a vast coalition within the cybercriminal world, bringing together several well-known pro-Russian hacker groups, including the Cyber Army of Russia, UserSec, and NoName. This alliance has gained attention due to its coordinated cyberattacks, particularly against Western targets, reflecting a shared motivation rooted in political and ideological goals aligned with Russian interests.
The Cyber Army of Russia’s involvement in this alliance highlights its role in orchestrating and executing large-scale cyberattacks, often with the intent to disrupt or retaliate against entities perceived as antagonistic to Russian policies. The High Society collective has been expanding its reach, recently claiming responsibility for attacks on Italian companies, showcasing their growing capabilities and collaborative efforts.
This hacker coalition’s activities underline the increasing trend of politically motivated cyberattacks, where hacking is used as a tool to further nationalistic or ideological agendas. The collective’s operations are marked by their focus on targets that align with their pro-Russian stance, often leveraging tactics such as DDoS attacks and data breaches to achieve their objectives.
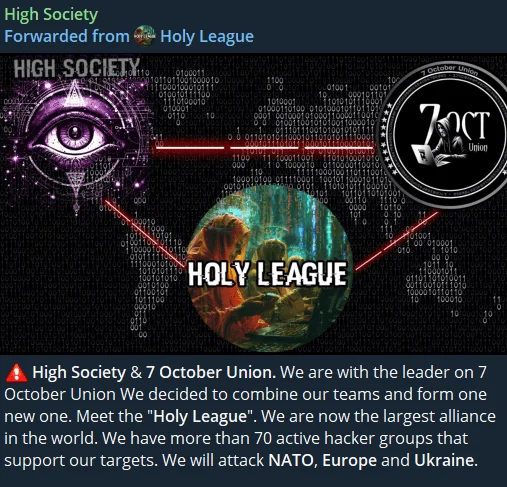
Holy League announcement in High Society’s Telegram channel
The Holy League is a broader coalition within the pro-Russian cyber landscape that encompasses various hacker groups, including the High Society alliance. Unlike the more focused High Society, which consists of groups like the Cyber Army of Russia, UserSec, and NoName, the Holy League brings together a wider array of hacktivist collectives with only one cause, common enemies. Therefore, even if their attacks are somewhat limited to more basic tactics like defacement attacks and DDoS, a large collective’s focused attack could cause significant damage.
As proof of their actions and the damage they may cause, the group’s members were sanctioned last month. The US Treasury Department announced sanctions on two members of the Russian hacktivist group Cyber Army of Russia Reborn (CARR) for cyberattacks on US critical infrastructure. Yuliya Pankratova, the group’s leader, and Denis Degtyarenko, a key hacker, were named.
How and Whom They Attack?
The Cyber Army of Russia Reborn (CARR) has emerged as a significant threat in the realm of hacktivism, particularly focusing on entities that oppose Russian interests, including those associated with NATO and countries that support Ukraine. Their attacks are multifaceted, often combining technical disruption with psychological and informational warfare. CARR employs large-scale Distributed Denial of Service (DDoS) attacks, using botnets to overwhelm the networks of their targets, rendering them inaccessible. These attacks are designed to cripple the digital infrastructure of their enemies, causing disruption in critical services.
Recent DDoS attacks against Ukraine due to Kursk offensive
CARR’s targets include government agencies, financial institutions, media outlets, and critical infrastructure in Europe and the United States. Notably, in late 2023, the group expanded its operations to include more sophisticated attacks on Industrial Control Systems (ICS). These attacks have targeted sectors like water supply, energy, and wastewater management. For example, they claimed responsibility for the overflow of water storage tanks in Abernathy and Muleshoe, Texas, showcasing their ability to manipulate human-machine interfaces remotely.
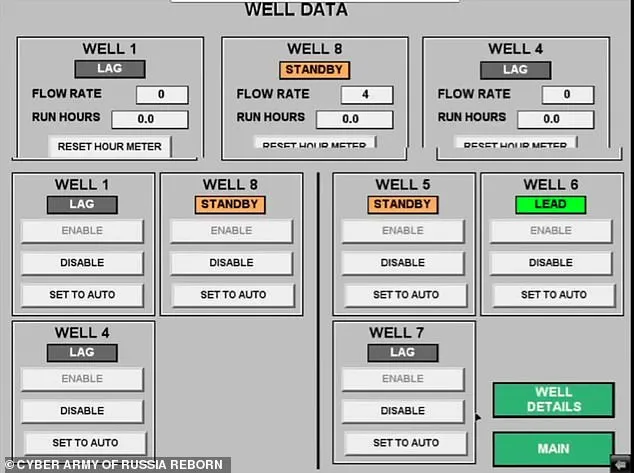
Alleged screenshots of hijacked ICS
The group is organized, utilizing platforms like Telegram to coordinate attacks, disseminate propaganda, and recruit supporters. Their Telegram channel serves as a hub for organizing DDoS attacks, sharing techniques, and amplifying their messages. Through these platforms, they engage in disinformation campaigns, spreading narratives that align with Russian state objectives, particularly concerning the ongoing conflict in Ukraine.
Thus, if we acknowledge the allegations about the hacktivism of Russian actors, CARR’s attacks are not just limited to technical disruptions; they are part of a broader strategy of hybrid warfare, combining cyberattacks with information operations to achieve strategic goals. By targeting critical infrastructure, government agencies, and key industries, they aim to sow chaos, disrupt operations, and undermine public confidence in the affected nations.
In summary, Cyber Army of Russia Reborn is a highly adaptive and dangerous hacktivist group, capable of both technical and psychological warfare, with a clear agenda aligned with Russian geopolitical interests. Their use of DDoS attacks, combined with more advanced ICS manipulation, makes them a significant threat to global cybersecurity.
Conclusion
Cyber Army of Russia Reborn (CARR) represents a significant and multifaceted threat in the realm of hacktivism. This group targets entities that oppose Russian interests, including those linked to NATO and countries supporting Ukraine. Their operations extend beyond mere Distributed Denial of Service (DDoS) attacks; they integrate technical disruption with psychological and informational warfare.
CARR employs large-scale DDoS attacks using botnets to overwhelm and incapacitate their targets’ networks, causing substantial disruptions in critical services. Their recent activities have expanded to more sophisticated attacks, including manipulations of Industrial Control Systems (ICS) affecting water supply, energy, and wastewater management. Notably, they have been linked to incidents such as the overflow of water storage tanks in Abernathy and Muleshoe, Texas, demonstrating their capability to remotely interfere with human-machine interfaces.
The group’s organization is evident through their use of platforms like Telegram for coordinating attacks, spreading propaganda, and recruiting supporters. Their Telegram channel is instrumental in organizing DDoS operations, sharing attack techniques, and promoting disinformation campaigns aligned with Russian state objectives.
Given CARR’s advanced and varied attack strategies, including both technical and psychological components, it is crucial for organizations in NATO member states and those supporting Ukraine to enhance their defenses. Key sectors like government, financial institutions, media, and critical infrastructure must prioritize robust DDoS protection and ICS security measures to safeguard against these threats.
Additional precautionary measures include:
- Restricting the number of connections per IP address.
- Setting limits on connections per second or lowering thresholds.
- Controlling the number of downloads from a single IP address.
- Blocking requests with non-standard User-Agent headers indicative of automated tools.
- Implementing CAPTCHA systems on public forms without authentication.
- Monitoring and detecting heavy request patterns to databases.
What are the MITRE ATT&CK TTPs of CARR?
| Tactics | Technique | Technique ID |
| Reconnaissance | Information Gathering from Social Media | T1593.001 |
| Discovery | System Network Connections Discovery | T1049 |
| Discovery | System Network Connections Discovery | T1016 |
| Command and Control | Application Layer Protocol | T1071 |
| Impact | Network Denial of Service | T1498 |
| Impact | Endpoint Denial of Service | T1499 |
| Impact | Manipulation of Industrial Control Systems | T0831 |
| Impact | Data Manipulation | T1565 |
| Persistence | Boot or Logon Autostart Execution | T1547 |

Source: Original Post
Views: 1

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português