The LAC Cyber Emergency Response Team confirmed a new attack campaign named “RevivalStone,” launched by the China-based “Winnti Group” in March 2024. This campaign targeted Japanese companies in the manufacturing, materials, and energy sectors, utilizing a new version of “Winnti malware.” The report elaborates on the campaign’s overall scope, the updated functionalities of the Winnti malware, and introduces detection and mitigation strategies against similar attacks. Affected: Japan’s manufacturing and energy sectors
Keypoints :
- RevivalStone campaign confirmed by LAC Cyber Emergency Response Team in March 2024.
- Targeted Japanese firms in manufacturing, materials, and energy sectors.
- New functionalities of Winnti malware unveiled during the campaign.
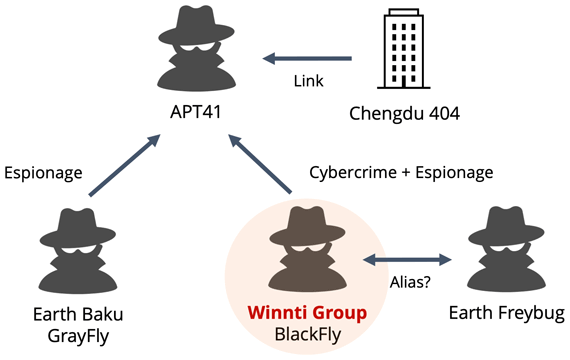
- Winnti Group has changed targets over time, now focusing on intellectual property.
- Use of SQL injection to install web shells on vulnerable web servers as an entry point.
- Winnti malware has evolved, with a new version reported as v5.0.
- Multiple web shells used, including China chopper and Behinder.
- Winnti malware utilizes complex obfuscation and encryption techniques.
- Detection and mitigation strategies against similar future attacks were discussed.
MITRE Techniques :
- T1190 – Exploit Public-Facing Application: SQL injection vulnerabilities exploited.
- T1053.005 – Scheduled Task/Job: Utilized for executing malware via scheduled tasks.
- T1059.003 – Command and scripting interpreter: Executed scripts and commands via batch files.
- T1505.003 – Server Software Component: Deployment of WebShells for persistence.
- T1574.001 – Hijack Execution Flow: DLL hijacking used for executing Winnti malware.
- T1547.006 – Boot or Logon Autostart Execution: Winnti Rootkit deployed during startup.
- T1078.002 – Valid Accounts: Compromised shared accounts for lateral movement.
- T1014 – Rootkit: Utilized Winnti Rootkit to conceal communications and actions.
- T1036.005 – Masquerading: Renamed WinRAR to rundll.exe for disguise.
Indicator of Compromise :
- [Hash] e1e0b887b68307ed192d393e886d8b982e4a2fd232ee13c2f20cd05f91358596 (SHA-256)
- [Hash] c649e75483dd0883de2fef001a44263a272c6b49a8d1c9ea7c00c044495200ad (SHA-256)
- [Hash] 169d35bdb36c2bfcb3bbf64392de1b05d56553172a13cae43a43acbe2aa18587 (SHA-256)
- [Hash] b9d4ec771a79f53a330b29ed17f719dac81a4bfe11caf0eac0efacd19d14d090 (SHA-256)
- [Hash] 4608a63c039975fb8f3ffd221ec6877078542def44767f50447db1d514eb0779 (SHA-256)
Full Story: https://www.lac.co.jp/lacwatch/report/20250213_004283.html