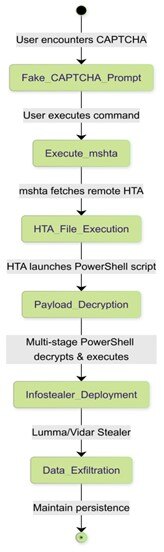
The article discusses a recent investigation by Trustwave SpiderLabs that uncovered a campaign leveraging fake CAPTCHA verifications to execute malicious PowerShell scripts, leading to the deployment of infostealers like Lumma and Vidar. The multi-stage attack involves deceptive prompts to execute commands, downloading HTA files, decrypting payloads, and executing infostealers. Affected: Trustwave SpiderLabs, PowerShell users, cybersecurity sector
Keypoints :
- Trustwave SpiderLabs discovered a resurgence of fake CAPTCHA verifications in February 2025.
- The attack uses a multi-stage PowerShell execution process to deploy infostealers.
- Malicious prompts trick users into executing PowerShell commands disguised as CAPTCHA verifications.
- The attack involves executing HTA files and decrypting further commands to advance the infection.
- Lumma and Vidar are two infostealers employed to steal sensitive information and maintain persistence.
MITRE Techniques :
- T1053.005 – Scheduled Task/Job: Scheduled Task is exploited to schedule malicious tasks.
- T1059.001 – Command and Scripting Interpreter: PowerShell is used for executing malicious commands.
- T1059.003 – Command and Scripting Interpreter: Windows Command Shell is utilized for command execution.
- T1204.002 – User Execution: Malicious File is used to rely on user action for execution.
- T1548.002 – Abuse Elevation Control Mechanism: Bypass User Account Control to gain elevated privileges.
- T1036.003 – Masquerading: Rename System Utilities to disguise malicious files.
- T1218.010 – System Binary Proxy Execution: Regsvr32 is used for executing remote payloads.
- T1562.002 – Impair Defenses: Disable Windows Event Logging to evade detection.
- T1564.003 – Hide Artifacts: Use hidden windows to conceal processes.
- T1552.001 – Unsecured Credentials: Credentials in files are targeted for exfiltration.
- T1555.003 – Credentials from Password Stores: Credentials from web browsers are accessed.
- T1012 – Query Registry is used for system discovery.
- T1033 – System Owner/User Discovery is performed to gather information about the system’s users.
- T1082 – System Information Discovery is conducted to extract system information.
- T1518 – Software Discovery is used to find installed software on systems.
- T1614 – System Location Discovery helps determine the geographical location of the system.
- T1071 – Application Layer Protocol is utilized for command and control communication.
- T1571 – Non-Standard Port is exploited for establishing command and control channels.
- T1102 – Web Service is used for communication between the attacker and compromised systems.
Indicator of Compromise :
- Domain hxxps://60d427489[.]kliplubuziy[.]shop
- MD5: 322579b54e4c6fecabeee9cdb75233d8d67ee7ae28a09bf7f6d33118a9d07527 (Lumma Stealer)
- MD5: 17190c7e5163b5c115e3d470f568ee5f (Vidar Stealer)
- MD5: 218261DAA1AEBD5484B29BF7F959B57A (HijackLoader)
- IP Address: 188[.]114[.]97[.]3185[.]195[.]97[.]57191[.]101[.]230[.]18172[.]67[.]149[.]66