On February 7, 2024, the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) released a joint Cybersecurity Advisory (CSA) assessing that People’s Republic of China (PRC) state-sponsored cyber actors were seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with the United States.
Volt Typhoon is a state-sponsored, politically motivated, Chinese adversary that has been active since at least 2021. Its primary focus is espionage and information gathering, specifically targeting critical infrastructure organizations in Guam and in the United States.
One of Volt Typhoon’s most notable characteristics is the use of Living-off-the-Land (LotL) techniques, where they leverage built-in network administration tools to achieve their objectives. This approach allows them to blend in with normal Windows systems and network activities while evading detection by endpoint detection and response (EDR) products.
AttackIQ has released a new attack graph that emulates the different behaviors exhibited by the Chinese-based adversary known as Volt Typhoon during its recent activities against multiple critical infrastructure organizations, with the aim of helping customers validate their security controls and their ability to defend against this sophisticated and recent threat.
Validating your security program performance against these behaviors is vital in reducing risk. By using this new assessment template in the AttackIQ Security Optimization Platform, security teams will be able to:
- Assess their security posture against a sophisticated threat seeking to pre-position themselves on networks for disruptive or destructive cyberattacks.
- Continuously validate detection and prevention pipelines against widely identified behaviors associated with Volt Typhoon.
[CISA AA24-038A] PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure
This attack graph emulates the different behaviors exhibited by the Chinese adversary known as Volt Typhoon during its recent activities against multiple critical infrastructure organizations in North America, Europe, and Oceania.
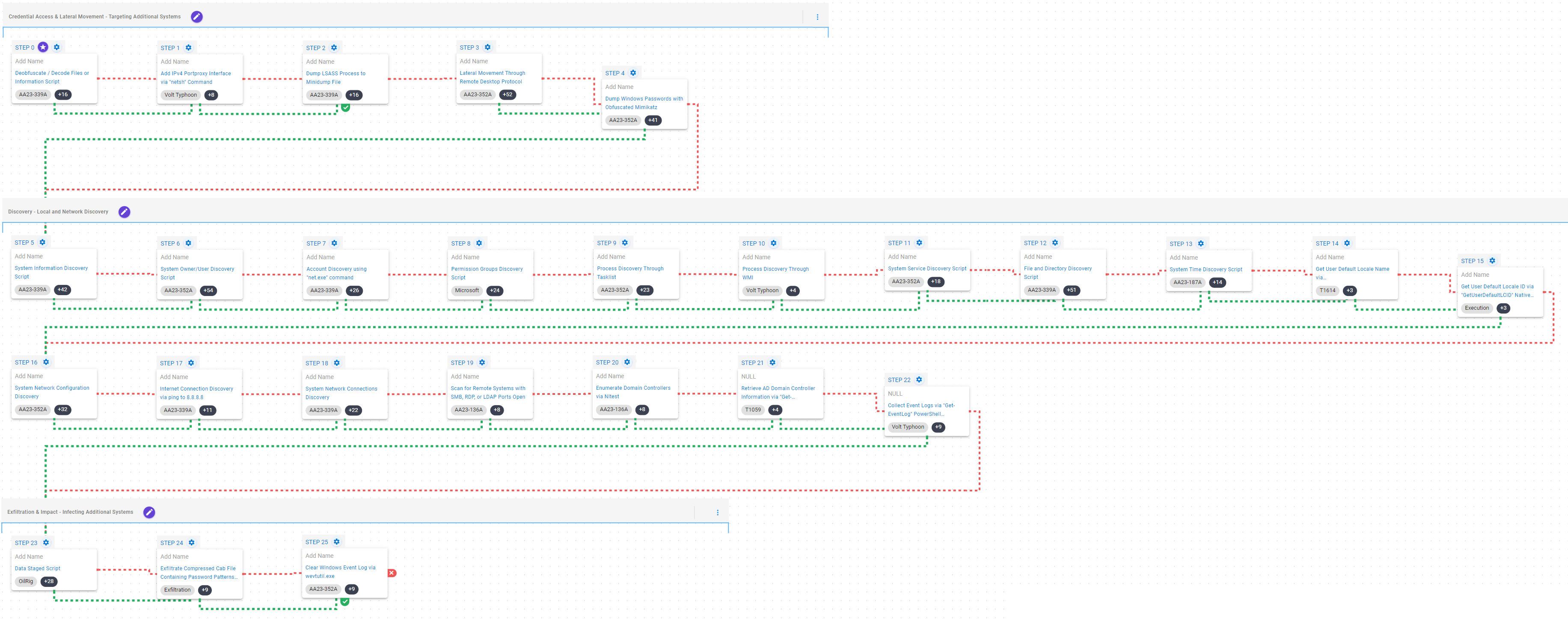
In the first stage, the adversary will attempt to deofuscate the used script through the CertUtil utility. After that, it will proceed to modify the system’s firewall using Netsh to create a new rule to proxy port connections from the targeted system.
Next, it will attempt to perform a dump of the Windows Local Security Authority Server Service (LSASS) process using the native comsvcs.dll library, with the aim of moving laterally to remotely accessible systems via Remote Desktop Protocol (RDP).
Lastly, the adversary will use the credential harvesting tool known as Mimikatz to extract credentials from the newly targeted systems.
Deobfuscate/Decode Files or Information (T1140): Use the legitimate certutil binary to decode a base64 encoded payload.
Impair Defenses: Disable or Modify System Firewall (T1562.004): This scenario creates a new rule in the Windows System Firewall using the netsh utility to proxy port connections in the targeted system.
OS Credential Dumping: LSASS Memory (T1003.001): Uses rundll32.exe with comsvcs.dll to call the MiniDump export that will dump the LSASS process memory to disk. This process contains a variety of credential materials and can be passed to additional dumping tools to extract credentials.
Remote Services: Remote Desktop Protocol (T1021.001): Remote Desktop is the built-in remote access utility used by Windows. This scenario attempts to remotely connect to another accessible asset with stolen credentials.
OS Credential Dumping (T1003): This scenario uses an obfuscated version of Mimikatz to dump passwords and hashes available in the targeted system.
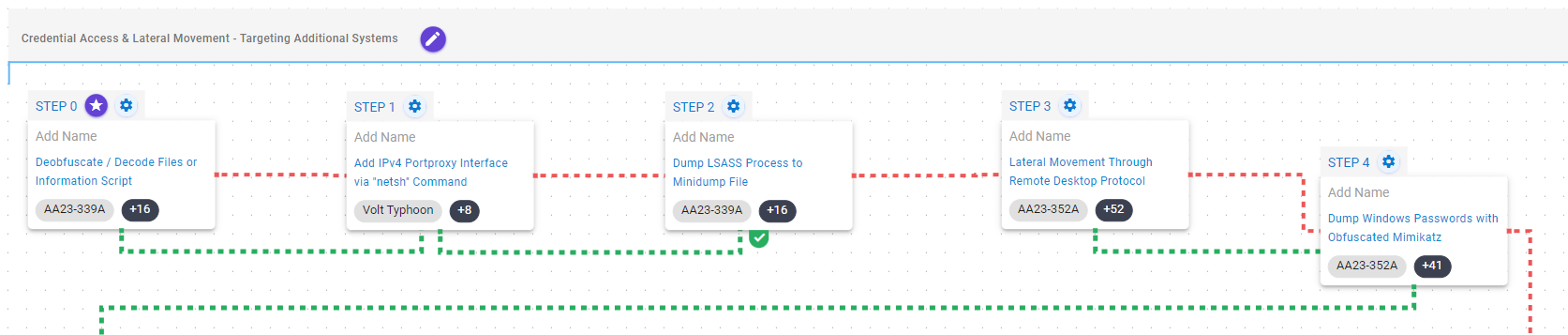
This stage is mainly focused on the discovery of information about the compromised environment.
At the local level, Volt Typhoon will retrieve information related to the system, local accounts and groups, running processes and services, files and directories, and the system’s location.
At the network level, it will seek to discover the network configuration, connectivity to the Internet, established network connections, accessible remote systems, and the presence of a domain controller.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all of the Windows system information.
System Owner / User Discovery (T1033): This scenario executes the native whoami and query user utilities to gain details about the currently available accounts and permission groups.
Account Discovery: Local Account (T1087.001): This scenario executes the native net user command to get a list of all available local accounts.
Permission Groups Discovery (T1069): This scenario will enumerate permission groups using the net localgroup and net group /domain commands.
Process Discovery (T1057): Window’s built-in tasklist command is executed as a command process and the results are saved to a file in a temporary location.
System Service Discovery (T1007): This scenario executes the native net start utility to query a list of all running services.
File and Directory Discovery (T1083): A batch script is executed that lists all files and directories in %ProgramFiles% and the %systemdrive%Users directory.
System Time Discovery (T1124): The scenario identifies the time and time zone of the compromised system through the net time command.
System Location Discovery (T1614): These scenarios execute the GetUserDefaultLocaleName and GetUserDefaultLCID API calls to retrieve the location of the targeted system.
System Network Configuration Discovery (T1016): Native Window’s commands like route, ipconfig, and net use are executed to collect details about the infected host and network shares.
Internet Connection Discovery (T1016.001): The actors used ping to Google’s 8.8.8.8 DNS server to verify if they could connect to the internet.
System Network Connections Discovery (T1049): The native Windows command line tool netstat is used to collect active connections and any listening services running on the host.
Remote System Discovery (T1018): This scenario executes the Nmap tool to scan the local network searching for any remotely accessible systems with open ports for the Samba File Sharing (SMB), Remote Desktop (RDP), or Active Directory (LDAP) services.
Remote System Discovery (T1018): This scenario executes the nltest command to gather a list of domain controllers associated with a domain.
Remote System Discovery (T1018): This scenario will execute the Get-ADDomainController PowerShell cmdlet to discover the available domain controller.
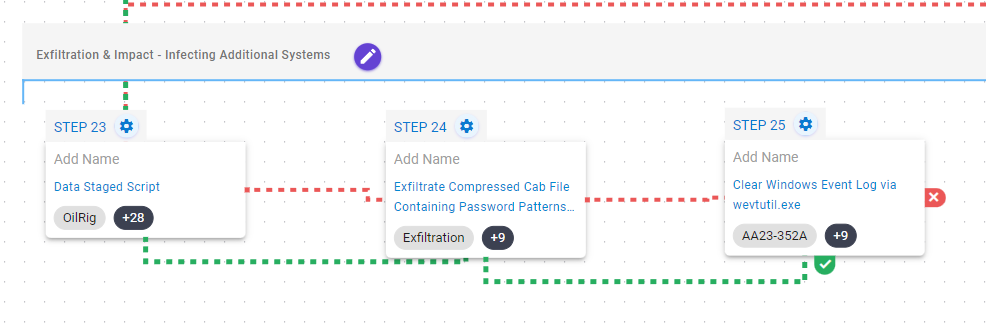
In the last stage, Volt Typhoon will perform the staging, compression, and exfiltration of the information collected in the previous stage. After that, it will attempt to delete Windows event logs using the wevtutil.exe utility to remove evidence of their intrusion activity.
Data Staged: Local Data Staging (T1074.001): Files are collected and stored in a temporary directory so they can be exfiltrated later.
Exfiltration Over C2 Channel (T1041): Files are sent to an AttackIQ controlled server using HTTP POST requests.
Indicator Removal: Clear Windows Event Logs (T1070.001): The scenario will use the wevtutil.exe binary to clear event logs from the system.
Opportunities to Expand Emulation Capabilities
In addition to the released assessment template, AttackIQ recommends the following scenarios to extend the emulation of the capabilities exhibited by Volt Typhoon.
These scenarios can be selected from within the scenario library and should be run in their respective environments and with their respective privileges.
User-based Scenarios:
- Discover PuTTY Stored Sessions via Registry: The
HKEY_CURRENT_USERSOFTWARESimonTathamPuTTYSessionsregistry key is queried to enumerate valid stored sessions. - Lateral Movement Through PAExec: This scenario aims to move laterally to additional remote systems that belong to the compromised network via the Server Message Block (SMB) protocol. This scenario utilizes PAExec, an open-source version of PSExec.
Active Directory/Domain Controller Environment:
- Dump Active Directory Database using Volume Shadow Copy via vssadmin.exe: This scenario attempts to create a copy of the Active Directory domain database with the objective of acquiring credential information.
- Enumerate DNS Zones Managed by Windows DNS Server using dnscmd: This scenario enumerates the DNS zones configured and managed by a Windows DNS server by using the native
dnscmdutility with the/enumzonesflag.
Detection and Mitigation Opportunities
Given the number of different techniques being utilized by this threat, it can be difficult to know which to prioritize for prevention and detection opportunities. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Review CISA’s Patching and Detection Recommendations:
CISA has provided a significant number of recommendations for the best ways to defend yourself from these and similar attacks. AttackIQ strongly recommends reviewing the detection and mitigation recommendations to adapt them to your environment first to determine if you have any existing impact before reviewing the assessment results.
2. Review AttackIQ’s Blog About Monitoring and Testing for Living off the Land Binaries:
AttackIQ published a blog about the abuse of Living-off-the-Land binaries. The report highlights additional tools and commands used by threat actors beyond the scope of what Volt Typhoon has utilized. Each native tool has a breakdown of how it can be abused along with Sigma rules to help organizations detect these behaviors.
3. OS Credential Dumping: LSASS Memory (T1003.001):
Adversaries may attempt to extract user and credential information from the Local Security Authority Subsystem Service (LSASS) process.
3a. Detection
Search for executions of comsvcs.exe that attempt to access the LSASS process.
Process Name == (comsvcs)
Command Line CONTAINS (‘lsass’)
3b. Mitigation
MITRE ATT&CK recommends the following mitigation recommendations:
- M1028 – Operating System Configuration
- M1027 – Password Policies
- M1026 – Privileged Account Management
- M1017 – User Training
- M1040 – Behavior Prevention on Endpoint
- M1043 – Credential Access Protection
- M1025 – Privileged Process Integrity
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against the recent activities carried out by the Chinese adversary Volt Typhoon. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this assessment template and other aspects of the AttackIQ Security Optimization Platform, including through our fully managed service, AttackIQ Ready!, and our co-managed security service, AttackIQ Enterprise.
The post Response to CISA Advisory (AA24-038A): PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure appeared first on AttackIQ.
Source: Original Post