Summary: A recent analysis revealed a critical local privilege escalation vulnerability (CVE-2024-9473) in Palo Alto Networks’ GlobalProtect MSI installer, allowing low-privileged attackers to gain SYSTEM-level access. This security flaw affects multiple versions of GlobalProtect, necessitating immediate upgrades to the patched version 6.2.5 to mitigate risks.
Threat Actor: Local attackers | local attackers
Victim: Palo Alto Networks | Palo Alto Networks
Key Point :
- Vulnerability CVE-2024-9473 allows local low-privileged users to escalate privileges to SYSTEM level.
- The issue arises during the repair process of the GlobalProtect MSI installer, which executes a subprocess with SYSTEM privileges.
- Multiple versions of GlobalProtect are affected, with users urged to upgrade to version 6.2.5 to mitigate risks.
In a recent vulnerability analysis by Michael Baer from SEC Consult Vulnerability Lab, a significant local privilege escalation vulnerability (CVE-2024-9473) was uncovered in Palo Alto Networks’ GlobalProtect MSI installer. This flaw, if exploited, allows local, low-privileged attackers to gain SYSTEM-level access to affected machines, presenting a critical security risk for software users.
The CVE-2024-9473 vulnerability lies in the MSI installer for GlobalProtect. According to Baer’s findings, the issue arises when GlobalProtect is installed using the MSI file. A low-privileged user can trigger a repair of the installation by launching the installer without requiring User Account Control (UAC) prompts. During this repair process, a subprocess called PanVCrediChecker.exe is executed with SYSTEM privileges, which interacts with the file libeay32.dll located in the program files directory.
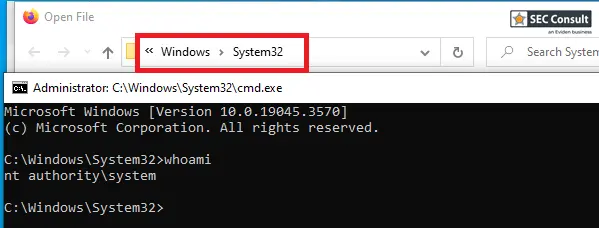
Baer explains that this process opens a significant loophole: “The configuration of the GlobalProtect MSI installer file was found to produce a visible conhost.exe window running as the SYSTEM user when using the repair function of msiexec.exe.” This allows the attacker to manipulate the system by opening a SYSTEM-level command prompt, granting full control over the machine.
The exploitation process is surprisingly straightforward. An attacker can locate the MSI installer file on the machine (even if it has been removed from its original location) and trigger the repair process. By leveraging the tool SetOpLock.exe from Google Project Zero, the attacker can place a lock on libeay32.dll, which is accessed multiple times during the repair.
By carefully releasing and holding the lock at specific points, the attacker can ensure the conhost.exe window stays open, allowing them to escalate privileges. “The conhost window that gets opened when PanVCrediChecker.exe is executed doesn’t close and can then be interacted with,” Baer explains. The final step involves opening a SYSTEM-level command prompt via a browser and executing cmd.exe.
The analysis reveals that multiple versions of GlobalProtect are vulnerable. The tested versions included 5.1.5 and 5.2.10, as well as 6.1.2, but Palo Alto Networks has confirmed that all versions prior to 6.2.5 are affected. However, version 5.2.x has reached its end of life and will not receive a patch. Users running any of the affected versions are strongly encouraged to upgrade immediately to the patched version 6.2.5 to mitigate the risk.