Summary: A critical vulnerability (CVE-2024-36814) in AdGuard Home allows authenticated attackers to read arbitrary files on the system, potentially exposing sensitive information. Discovered by security researcher Jack Moran, this flaw poses significant security risks due to improper file permission settings.
Threat Actor: Authenticated attackers | authenticated attackers
Victim: AdGuard Home users | AdGuard Home
Key Point :
- The vulnerability allows attackers to access sensitive configuration files, including usernames and password hashes, due to weak file permissions.
- Exploitation can occur through the custom filter list feature, enabling attackers to read critical system files like /etc/shadow.
- AdGuard Home developers have released a patch, and users are advised to update their installations immediately to mitigate risks.
- System administrators should verify file permissions and restrict access to configuration files until the patch is applied.
A critical vulnerability, identified as CVE-2024-36814, has been uncovered in AdGuard Home, an open-source network-wide ad-blocking solution. The vulnerability, discovered by security researcher Jack Moran, allows authenticated attackers to read arbitrary files on the system running AdGuard Home, potentially leading to severe security risks. This flaw has been rated with a CVSS score of 7.1, marking it as a high-severity issue.
Moran’s investigation revealed that AdGuard Home, when installed with root privileges, exposes a critical flaw in how it handles file permissions. A key insight Moran shared in his analysis is that during installation, AdGuard Home writes its configuration to the /opt/AdGuardHome directory. This directory contains the file AdGuardHome.yaml, which stores configuration data, including sensitive information like usernames and bcrypt password hashes.
The researcher noted that the file permissions of this directory are set to -rw-r–r–, meaning that any user on the system could read its contents. Moran’s analysis states, “Interestingly enough, this file is written with -rw-r–r– permissions, indicating anyone can read its contents.” This weak permission setting allows an authenticated attacker to access this sensitive configuration data, which is often all that’s needed to exploit a system further.
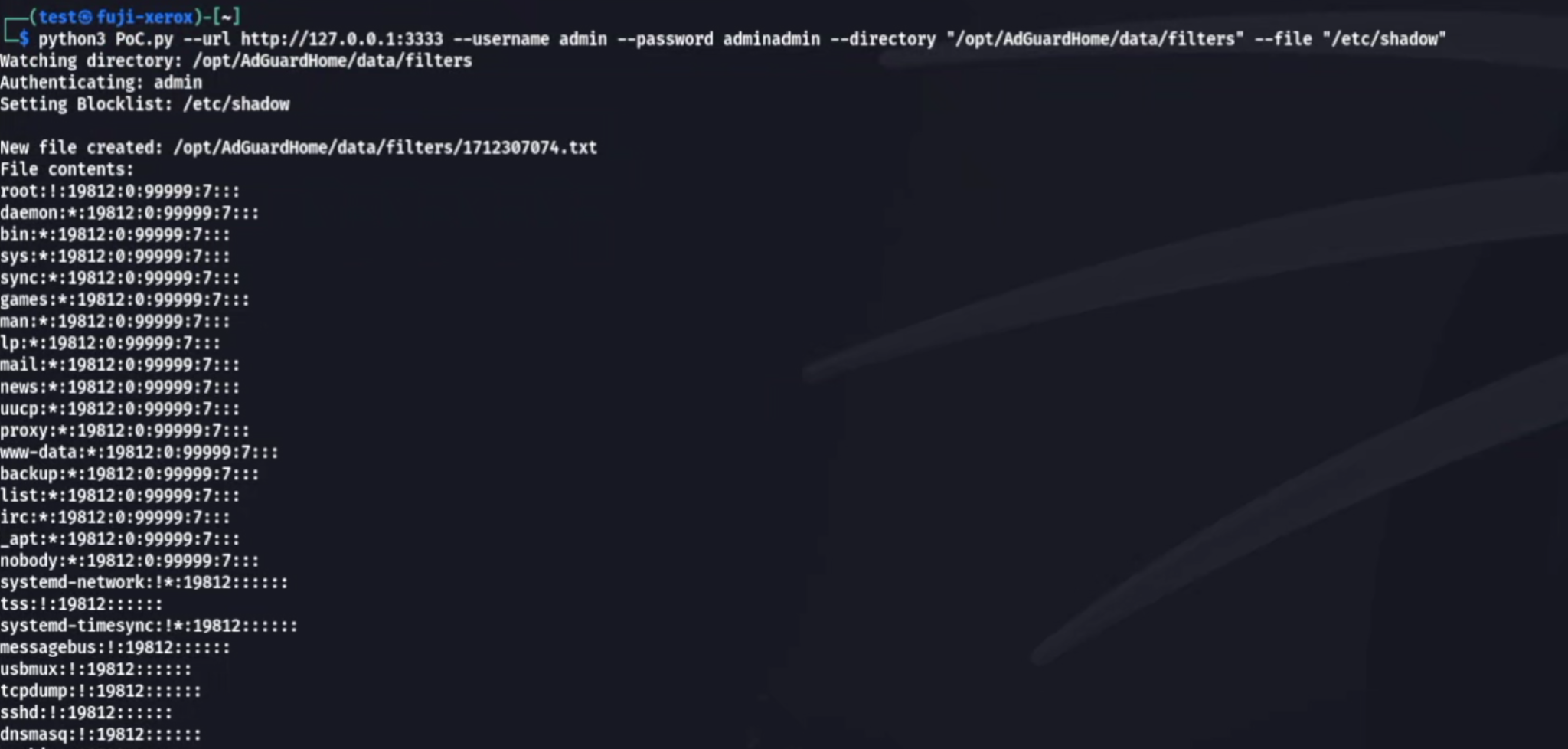
The arbitrary file read vulnerability is exploitable via the custom filter list feature in AdGuard Home. Users can add custom filter lists by specifying a URL or an absolute file path. This functionality can be abused to point to system files like /etc/shadow, which stores password hashes. The vulnerability allows an attacker to craft a POST request to AdGuard Home’s web interface, adding critical system files like /etc/shadow to the custom filter list.
Moran’s analysis explains this attack vector in detail: “Adding one is as simple as navigating to /#filters, clicking add block/allow list > add a custom list > and putting in the required URL or absolute file path… say /etc/shadow.”
Once the system file is added to the list, its contents are accessible through the web interface, exposing potentially sensitive information like password hashes, which an attacker could crack offline.
This vulnerability is particularly dangerous in shared environments where multiple users have access to the system running AdGuard Home. Given the wide permissions of the affected configuration file, even non-root users could access sensitive information. Once an attacker has access to system files, they could extract password hashes, crack them, and escalate their privileges on the affected system.
While the complexity of the attack requires prior authentication, the consequences of exploiting CVE-2024-36814 can be far-reaching. As Moran mentions, “assuming the user in question already has access to the AdGuard Home dashboard or the hash was successfully cracked (admin1234), resulting in access to the AdGuard Home dashboard.”
Research also published a simple Python script to demonstrate how to exploit this flaw.
The developers of AdGuard Home have acknowledged the issue and released a patch in version v0.107.53 to address the vulnerability. Users of AdGuard Home are strongly advised to update their installations immediately to prevent potential exploitation.
In the meantime, system administrators are urged to verify file permissions within /opt/AdGuardHome and restrict access to the configuration files until they can apply the patch. Additionally, limiting the exposure of the AdGuard Home dashboard and enforcing strong passwords can reduce the risk of an attack.