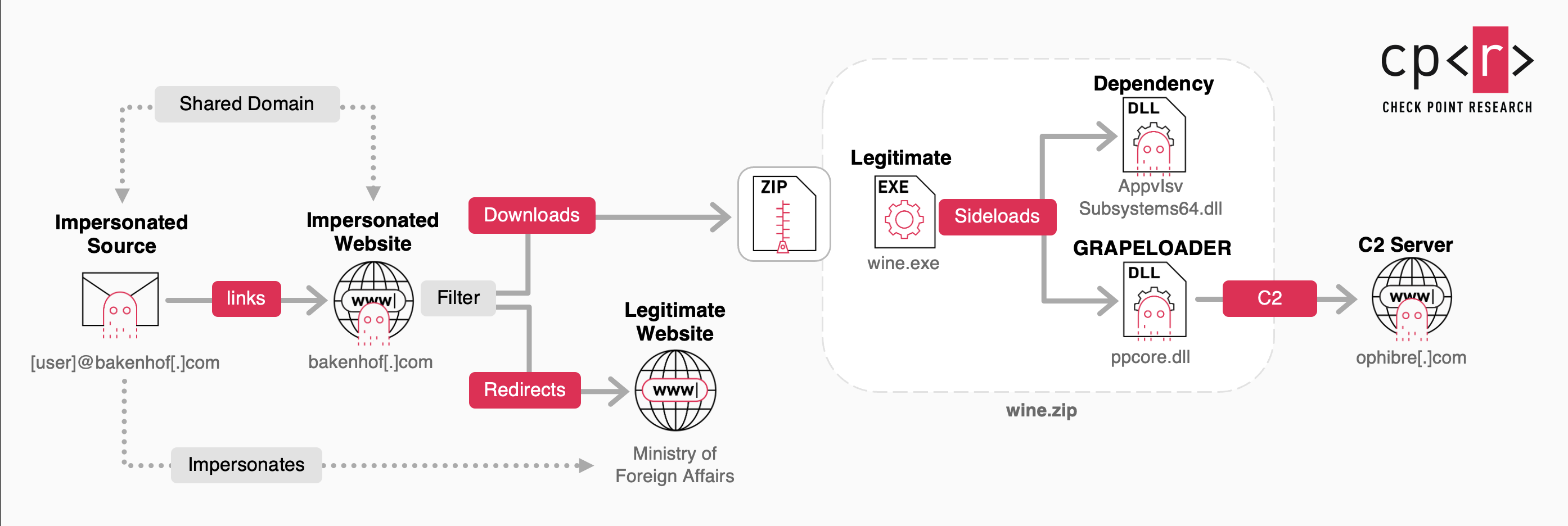
An advanced phishing campaign attributed to APT29, a Russia-linked threat group, is targeting diplomatic entities in Europe by impersonating a foreign affairs ministry to distribute invitations for wine tasting events. This campaign features the use of a new loader, GRAPELOADER, alongside an evolved variant of the existing backdoor WINELOADER, both of which enable stealth techniques and payload delivery. Affected: European diplomatic entities, government sectors
Keypoints :
- APT29, also known as Midnight Blizzard or Cozy Bear, is behind a targeted phishing campaign across Europe.
- The campaign involves impersonating a major European Ministry of Foreign Affairs to send fake wine event invitations.
- GRAPELOADER, a new loader, is used to download malware, while an improved version of WINELOADER is employed later in the attack.
- Malicious emails are sent from two domains, bakenhof[.]com and silry[.]com, featuring deceptive subject lines related to wine events.
- GRAPELOADER establishes persistence by modifying the Windows registry to execute automatically after system reboots.
- The campaign includes extensive anti-analysis techniques to evade detection by security solutions.
MITRE Techniques :
- T1071 – Application Layer Protocol: GRAPELOADER communicates with its C2 server via HTTPS POST requests.
- T1060 – Registry Run Keys / Startup Folder: GRAPELOADER modifies registry keys for persistence by adding entries to the Run key.
- T1059 – Command and Scripting Interpreter: GrapeLoader executes commands via a PowerPoint executable with side-loaded malicious DLLs.
- T1140 – Deobfuscate/Decode Files or Information: The malware employs sophisticated anti-analysis techniques, string obfuscation, and memory management to thwart detection.
Indicator of Compromise :
- [File] wine.zip
- [Hash MD5] 653db3b63bb0e8c2db675cd047b737cefebb1c955bd99e7a93899e2144d34358
- [File] wine.exe
- [Hash MD5] 420d20cddfaada4e96824a9184ac695800764961bad7654a6a6c3fe9b1b74b9a
- [Domain] bakenhof[.]com
Full Story: https://research.checkpoint.com/2025/apt29-phishing-campaign/
Views: 48