
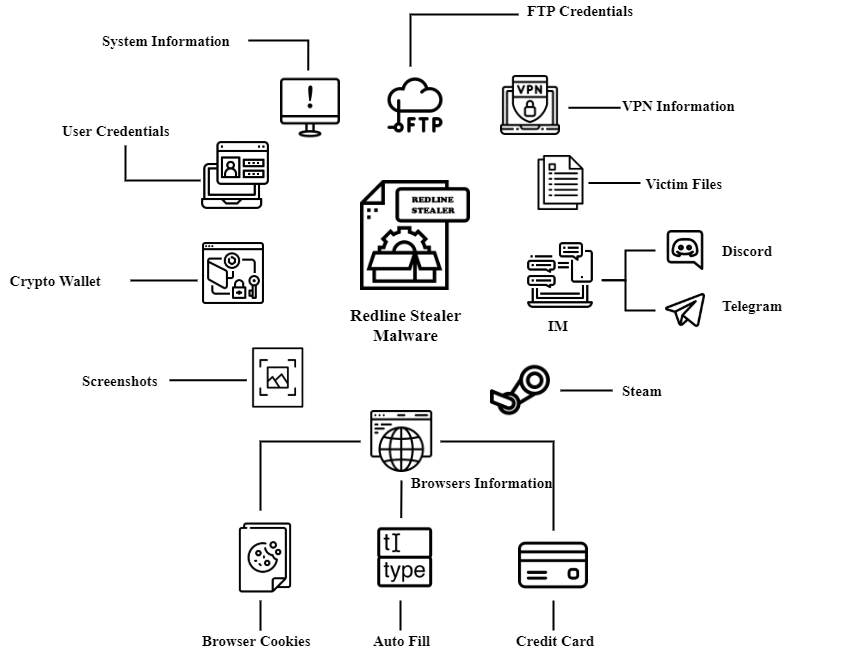
Redline Stealer is a type of malware that steals sensitive information from infected computers. The malware is known for its ability to bypass antivirus software and remain undetected on a victim’s computer for an extended period. In this essay, we will discuss the Redline Stealer malware, its history, its capabilities, and its impact. Additionally, we will provide a flowchart that outlines the basic steps of the malware.
Redline Stealer was first discovered in 2018 by researchers from Cisco Talos. Since then, it has evolved into a sophisticated piece of malware that poses a significant threat to individuals and organizations worldwide. The malware is typically distributed through phishing emails, malicious websites, or via software vulnerabilities. Once the malware infects a computer, it immediately begins to collect sensitive information, such as login credentials, credit card information, and other personal data.
The capabilities of the Redline Stealer malware are extensive. Once installed on a computer, it can perform a variety of functions, including keylogging, clipboard monitoring, and browser history tracking. The malware can also take screenshots and capture webcam footage, providing attackers with a wealth of information about a victim’s online activities. Furthermore, the malware can upload stolen data to a remote server, allowing attackers to access the stolen information from anywhere in the world.
To better understand the basic steps of the Redline Stealer malware, see below that outlines its key functions and capabilities.
Malware Spread:
- Firstly malware binary drops into the temp directory in any random name “C:UsersadminAppDataLocalTempfile.exe” and later it leverages same executable to generate separate folder with next level of malicious executables.
C:UsersadminAppDataLocalTempIXP001.TMPgwiasdL.exe
C:UsersadminAppDataLocalTempIXP002.TMPgasda0yL.exe
C:UsersadminAppDataLocalTempIXP003.TMPgasasdyL.exe
- Malicious files created under the temp folder are executed in background and at initial level it checks for browser cookies “C:UsersadminAppDataLocalGoogleChromeUser DataDefaultCookies” and search for installed softwares in registry keys “HKEY_LOCAL_MACHINESOFTWAREWOW6432NODEMICROSOFTWINDOWSCURRENTVERSIONUNINSTALL{60EC980A-BDA2-4CB6-A427-B07A5498B4CA}”
- Malicious executable will collect the credential from web browser “C:UsersadminAppDataRoamingFileZillarecentservers.xml” and also looking for VPN credentials “C:UsersadminAppDataLocalNordVPN” with this information malware connects with to the CNC server “193[.]233.20.13” with the destination port number “55871”
- One of the executable from temp directory connected to the server without proper hostname “HTTP://193[.]233[.]20.2/BN89HKU/INDEX.PHP” and it sends request to a Malicious DLL “HTTP://193[.]233[.]20.2/BN89HKU/PLUGINS/CLIP64.DLL” and it is downloaded in the folder “C:UsersadminAppDataRoamingc1ec479e5342a2clip64.dll”
- Next stage it modifies the registry values. below registry key is modified.
HKEY_CURRENT_USERSOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORERUSER SHELL FOLDERS
Once registry key is modified , it takes task scheduler to run the specific malicious file under temp folder for every 5 minutes “C:WindowsSystem32schtasks.exe" /Create /SC MINUTE /MO 1 /TN mnolyk.exe /TR "C:UsersadminAppDataLocalTemp4b9a106e76mnolyk.exe" /F
- Again it connects to external server 193.233.20[.]2 on the destination port 80 and Windows inbuilt utility “icacls.exe” is used to modify the file permission "C:WindowsSystem32cmd.exe" /k echo Y|CACLS "mnolyk.exe" /P "admin:N"&&CACLS "mnolyk.exe" /P "admin:R" /E&&echo Y|CACLS "..4b9a106e76" /P "admin:N"&&CACLS "..4b9a106e76" /P "admin:R" /E&&Exit
Above command shows file permission is changed for mnolyk.exe file and scheduled task is started and running.
- At the final stage , one of the executable in temp folder has executed the app launcher which is under the path C:WindowsMicrosoft.NETFrameworkv4.0.30319AppLaunch.exe and steals browser data and credentials and connects back to the CNC server “176[.]113.115.17” and destination port “4132”
The impact of the Redline Stealer malware is significant. It can result in the theft of sensitive information, including bank account details and login credentials, which can lead to financial loss and identity theft. Additionally, the malware can compromise a victim’s privacy, allowing attackers to monitor their online activities and potentially use that information for malicious purposes. The impact of Redline Stealer can be devastating, particularly for businesses and organizations that may hold large amounts of sensitive data.
Indicators of Compromise
IPs:
193[.]233.20.13
176[.]113.115.17
File hashes:
3854f7f1fcb2dd48a235e69be3a7618bec6faf676c8af4fc3ad1d253dc653591
Detection & Response
Splunk:
source=”WinEventLog:*” AND (((ParentImage=”Explorer.EXE”) AND (CommandLine=”*UsersAdminAppDataLocalTemp*.exe*” OR CommandLine=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) AND (Image=”*.EXE”) AND (CommandLine=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) AND (CommandLine=”*UsersadminAppDataLocalTemp**.exe*”) AND (Image=”schtasks.exe”) AND (CommandLine=”*/Create /SC MINUTE*” OR CommandLine=”*/MO 1 /TN*” OR CommandLine=”*/F*”) AND (Image=”cmd.exe”) AND (CommandLine=”*/k echo Y|CACLS*” OR CommandLine=”*/P ”admin:R*” OR CommandLine=”*/P ”admin:N”&&CACLS*” OR CommandLine=”*/E&&Exit*”) AND (Image=”rundll32.exe”) AND (CommandLine=”*UsersadminAppDataRoaming*” OR CommandLine=”**.DLL*” OR CommandLine=”*Main*” OR CommandLine=”*Roaming**.dll*”)) OR ((Image=”*.exe”) AND (CommandLine=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) AND (Image=”AppLaunch.exe” OR Image=”*.exe”) AND (CommandLine=”*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*”)))
Qradar:
SELECT UTF8(payload) FROM events WHERE LOGSOURCETYPENAME(devicetype)=’Microsoft Windows Security Event Log’ AND (((“ParentImage” = ‘Explorer.EXE’) AND (“Process CommandLine” ILIKE ‘%UsersAdminAppDataLocalTemp*.exe%’ OR “Process CommandLine” ILIKE ‘%UsersadminAppDataLocalTempIXP***.TMP*.exe%’) AND (“Image” ILIKE ‘%.EXE’) AND “Process CommandLine” ILIKE ‘%UsersadminAppDataLocalTempIXP***.TMP*.exe%’ AND “Process CommandLine” ILIKE ‘%UsersadminAppDataLocalTemp**.exe%’ AND (“Image” = ‘schtasks.exe’) AND (“Process CommandLine” ILIKE ‘%/Create /SC MINUTE%’ OR “Process CommandLine” ILIKE ‘%/MO 1 /TN%’ OR “Process CommandLine” ILIKE ‘%/F%’) AND (“Image” = ‘cmd.exe’) AND (“Process CommandLine” ILIKE ‘%/k echo Y|CACLS%’ OR “Process CommandLine” ILIKE ‘%/P “admin:R%’ OR “Process CommandLine” ILIKE ‘%/P “admin:N”&&CACLS%’ OR “Process CommandLine” ILIKE ‘%/E&&Exit%’) AND (“Image” = ‘rundll32.exe’) AND (“Process CommandLine” ILIKE ‘%UsersadminAppDataRoaming%’ OR “Process CommandLine” ILIKE ‘%*.DLL%’ OR “Process CommandLine” ILIKE ‘%Main%’ OR “Process CommandLine” ILIKE ‘%Roaming**.dll%’)) OR ((“Image” ILIKE ‘%.exe’) AND “Process CommandLine” ILIKE ‘%UsersadminAppDataLocalTempIXP***.TMP*.exe%’ AND (“Image” = ‘AppLaunch.exe’ OR “Image” ILIKE ‘%.exe’) AND “Process CommandLine” ILIKE ‘%Microsoft.NETFrameworkv4.0.30319AppLaunch.exe%’))
Elastic Query:
(((process.parent.executable.text:”Explorer.EXE” AND process.command_line.text:(*UsersAdminAppDataLocalTemp*.exe* OR *UsersadminAppDataLocalTempIXP***.TMP*.exe*) AND process.executable.text:*.EXE AND process.command_line.text:*UsersadminAppDataLocalTempIXP***.TMP*.exe* AND process.command_line.text:*UsersadminAppDataLocalTemp**.exe* AND process.executable.text:”schtasks.exe” AND process.command_line.text:(*/Create /SC MINUTE* OR */MO 1 /TN* OR */F*) AND process.executable.text:”cmd.exe” AND process.command_line.text:(*/k echo Y|CACLS* OR */P ”admin:R* OR */P ”admin:N”&&CACLS* OR */E&&Exit*) AND process.executable.text:”rundll32.exe” AND process.command_line.text:(*UsersadminAppDataRoaming* OR **.DLL* OR *Main* OR *Roaming**.dll*))) OR ((process.executable.text:*.exe AND process.command_line.text:*UsersadminAppDataLocalTempIXP***.TMP*.exe* AND process.executable.text:(“AppLaunch.exe” OR *.exe) AND process.command_line.text:*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*)))
Carbon Black:
(((parent_name:”Explorer.EXE” AND process_cmdline:(*UsersAdminAppDataLocalTemp*.exe* OR *UsersadminAppDataLocalTempIXP***.TMP*.exe*) AND process_name:*.EXE AND process_cmdline:*UsersadminAppDataLocalTempIXP***.TMP*.exe* AND process_cmdline:*UsersadminAppDataLocalTemp**.exe* AND process_name:”schtasks.exe” AND process_cmdline:(*/Create /SC MINUTE* OR */MO 1 /TN* OR */F*) AND process_name:”cmd.exe” AND process_cmdline:(*/k echo Y|CACLS* OR */P ”admin:R* OR */P ”admin:N”&&CACLS* OR */E&&Exit*) AND process_name:”rundll32.exe” AND process_cmdline:(*UsersadminAppDataRoaming* OR **.DLL* OR *Main* OR *Roaming**.dll*))) OR ((process_name:*.exe AND process_cmdline:*UsersadminAppDataLocalTempIXP***.TMP*.exe* AND process_name:(“AppLaunch.exe” OR *.exe) AND process_cmdline:*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*)))
GrayLog:
(((ParentImage:”Explorer.EXE” AND CommandLine:(*UsersAdminAppDataLocalTemp*.exe* *UsersadminAppDataLocalTempIXP***.TMP*.exe*) AND Image.keyword:*.EXE AND CommandLine:*UsersadminAppDataLocalTempIXP***.TMP*.exe* AND CommandLine:*UsersadminAppDataLocalTemp**.exe* AND Image:”schtasks.exe” AND CommandLine:(*/Create /SC MINUTE* */MO 1 /TN* */F*) AND Image:”cmd.exe” AND CommandLine:(*/k echo Y|CACLS* */P ”admin:R* */P ”admin:N”&&CACLS* */E&&Exit*) AND Image:”rundll32.exe” AND CommandLine:(*UsersadminAppDataRoaming* **.DLL* *Main* *Roaming**.dll*))) OR ((Image.keyword:*.exe AND CommandLine:*UsersadminAppDataLocalTempIXP***.TMP*.exe* AND Image.keyword:(“AppLaunch.exe” *.exe) AND CommandLine:*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*)))
FireEye:
(metaclass:`windows` ((pprocess:`Explorer.EXE` args:[‘*UsersAdminAppDataLocalTemp*.exe*’, ‘*UsersadminAppDataLocalTempIXP***.TMP*.exe*’] process:`*.EXE` args:[‘*UsersadminAppDataLocalTempIXP***.TMP*.exe*’] args:[‘*UsersadminAppDataLocalTemp**.exe*’] process:`schtasks.exe` args:[‘*/Create /SC MINUTE*’, ‘*/MO 1 /TN*’, ‘*/F*’] process:`cmd.exe` args:[‘*/k echo Y|CACLS*’, ‘*/P “admin:R*’, ‘*/P “admin:N”&&CACLS*’, ‘*/E&&Exit*’] process:`rundll32.exe` args:[‘*UsersadminAppDataRoaming*’, ‘**.DLL*’, ‘*Main*’, ‘*Roaming**.dll*’]) OR (process:`*.exe` args:[‘*UsersadminAppDataLocalTempIXP***.TMP*.exe*’] process:[`AppLaunch.exe`,`*.exe`] args:[‘*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*’])))
Microsoft Defender:
DeviceProcessEvents | where ((InitiatingProcessFolderPath =~ @’Explorer.EXE’ and (ProcessCommandLine contains @’UsersAdminAppDataLocalTemp*.exe’ or ProcessCommandLine contains @’UsersadminAppDataLocalTempIXP***.TMP*.exe’) and FolderPath =~ @’*.EXE’ and ProcessCommandLine contains @’UsersadminAppDataLocalTempIXP***.TMP*.exe’ and ProcessCommandLine contains @’UsersadminAppDataLocalTemp**.exe’ and FolderPath =~ @’schtasks.exe’ and (ProcessCommandLine contains @’/Create /SC MINUTE’ or ProcessCommandLine contains @’/MO 1 /TN’ or ProcessCommandLine contains @’/F’) and FolderPath =~ @’cmd.exe’ and (ProcessCommandLine contains @’/k echo Y|CACLS’ or ProcessCommandLine contains @’/P “admin:R’ or ProcessCommandLine contains @’/P “admin:N”&&CACLS’ or ProcessCommandLine contains @’/E&&Exit’) and FolderPath =~ @’rundll32.exe’ and (ProcessCommandLine contains @’UsersadminAppDataRoaming’ or ProcessCommandLine contains @’*.DLL’ or ProcessCommandLine contains @’Main’ or ProcessCommandLine contains @’Roaming**.dll’)) or (FolderPath =~ @’*.exe’ and ProcessCommandLine contains @’UsersadminAppDataLocalTempIXP***.TMP*.exe’ and FolderPath in~ (@’AppLaunch.exe’, @’*.exe’) and ProcessCommandLine contains @’Microsoft.NETFrameworkv4.0.30319AppLaunch.exe’))
Microsoft Sentinel:
SecurityEvent | where EventID == 4688 | where ((ParentProcessName =~ @’Explorer.EXE’ and (CommandLine contains @’UsersAdminAppDataLocalTemp*.exe’ or CommandLine contains @’UsersadminAppDataLocalTempIXP***.TMP*.exe’) and NewProcessName =~ @’*.EXE’ and CommandLine contains @’UsersadminAppDataLocalTempIXP***.TMP*.exe’ and CommandLine contains @’UsersadminAppDataLocalTemp**.exe’ and NewProcessName =~ @’schtasks.exe’ and (CommandLine contains @’/Create /SC MINUTE’ or CommandLine contains @’/MO 1 /TN’ or CommandLine contains @’/F’) and NewProcessName =~ @’cmd.exe’ and (CommandLine contains @’/k echo Y|CACLS’ or CommandLine contains @’/P “admin:R’ or CommandLine contains @’/P “admin:N”&&CACLS’ or CommandLine contains @’/E&&Exit’) and NewProcessName =~ @’rundll32.exe’ and (CommandLine contains @’UsersadminAppDataRoaming’ or CommandLine contains @’*.DLL’ or CommandLine contains @’Main’ or CommandLine contains @’Roaming**.dll’)) or (NewProcessName =~ @’*.exe’ and CommandLine contains @’UsersadminAppDataLocalTempIXP***.TMP*.exe’ and NewProcessName in~ (@’AppLaunch.exe’, @’*.exe’) and CommandLine contains @’Microsoft.NETFrameworkv4.0.30319AppLaunch.exe’))
Securonix:
index = activity AND (rg_functionality = “Microsoft Windows” AND (((((@sourceprocessname = “Explorer.EXE”) AND (@resourcecustomfield3 = “*UsersAdminAppDataLocalTemp*.exe*” OR @resourcecustomfield3 = “*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) AND ((@customstring54 ENDS WITH “.EXE”) OR (@destinationprocessname ENDS WITH “.EXE”)) AND (@resourcecustomfield3 = “*UsersadminAppDataLocalTempIXP***.TMP*.exe*”)) AND (((@customstring54 ENDS WITH “.EXE”) OR (@destinationprocessname ENDS WITH “.EXE”)) AND (@resourcecustomfield3 = “*UsersadminAppDataLocalTemp**.exe*”)) AND ((@customstring54 = “schtasks.exe”) OR (@destinationprocessname = “schtasks.exe”)) AND (@resourcecustomfield3 CONTAINS “/Create /SC MINUTE” OR @resourcecustomfield3 CONTAINS “/MO 1 /TN” OR @resourcecustomfield3 CONTAINS “/F”)) AND (((@customstring54 = “cmd.exe”) OR (@destinationprocessname = “cmd.exe”)) AND (@resourcecustomfield3 CONTAINS “/k echo Y|CACLS” OR @resourcecustomfield3 CONTAINS “/P “admin:R” OR @resourcecustomfield3 CONTAINS “/P “admin:N”&&CACLS” OR @resourcecustomfield3 CONTAINS “/E&&Exit”)) AND ((@customstring54 = “rundll32.exe”) OR (@destinationprocessname = “rundll32.exe”)) AND (@resourcecustomfield3 CONTAINS “UsersadminAppDataRoaming” OR @resourcecustomfield3 = “**.DLL*” OR @resourcecustomfield3 CONTAINS “Main” OR @resourcecustomfield3 = “*Roaming**.dll*”)) OR (((@customstring54 ENDS WITH “.exe”) OR (@destinationprocessname ENDS WITH “.exe”)) AND (@resourcecustomfield3 = “*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) AND ((@customstring54 = “AppLaunch.exe” OR @customstring54 ENDS WITH “.exe”) OR (@destinationprocessname = “AppLaunch.exe” OR @destinationprocessname ENDS WITH “.exe”)) AND (@resourcecustomfield3 CONTAINS “Microsoft.NETFrameworkv4.0.30319AppLaunch.exe”))))
RSA Netwitness:
(((ParentImage = ‘Explorer.EXE’) && (CommandLine contains ‘UsersAdminAppDataLocalTemp*.exe’, ‘UsersadminAppDataLocalTempIXP***.TMP*.exe’) && (Image contains ‘.EXE’) && (CommandLine contains ‘UsersadminAppDataLocalTempIXP***.TMP*.exe’) && (CommandLine contains ‘UsersadminAppDataLocalTemp**.exe’) && (Image = ‘schtasks.exe’) && (CommandLine contains ‘/Create /SC MINUTE’, ‘/MO 1 /TN’, ‘/F’) && (Image = ‘cmd.exe’) && (CommandLine contains ‘/k echo Y|CACLS’, ‘/P “admin:R’, ‘/P “admin:N”&&CACLS’, ‘/E&&Exit’) && (Image = ‘rundll32.exe’) && (CommandLine contains ‘UsersadminAppDataRoaming’, ‘*.DLL’, ‘Main’, ‘Roaming**.dll’)) || ((Image contains ‘.exe’) && (CommandLine contains ‘UsersadminAppDataLocalTempIXP***.TMP*.exe’) && (Image = ‘AppLaunch.exe’ || Image contains ‘.exe’) && (CommandLine contains ‘Microsoft.NETFrameworkv4.0.30319AppLaunch.exe’)))
Crowdstike:
(((((ParentBaseFileName=”Explorer.EXE”) AND ((CommandLine=”*UsersAdminAppDataLocalTemp*.exe*” OR CommandLine=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) OR (CommandHistory=”*UsersAdminAppDataLocalTemp*.exe*” OR CommandHistory=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”)) AND (ImageFileName=”*.EXE”) AND ((CommandLine=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) OR (CommandHistory=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”))) AND ((ImageFileName=”*.EXE”) AND ((CommandLine=”*UsersadminAppDataLocalTemp**.exe*”) OR (CommandHistory=”*UsersadminAppDataLocalTemp**.exe*”))) AND (ImageFileName=”schtasks.exe”) AND ((CommandLine=”*/Create /SC MINUTE*” OR CommandLine=”*/MO 1 /TN*” OR CommandLine=”*/F*”) OR (CommandHistory=”*/Create /SC MINUTE*” OR CommandHistory=”*/MO 1 /TN*” OR CommandHistory=”*/F*”))) AND ((ImageFileName=”cmd.exe”) AND ((CommandLine=”*/k echo Y|CACLS*” OR CommandLine=”*/P ”admin:R*” OR CommandLine=”*/P ”admin:N”&&CACLS*” OR CommandLine=”*/E&&Exit*”) OR (CommandHistory=”*/k echo Y|CACLS*” OR CommandHistory=”*/P ”admin:R*” OR CommandHistory=”*/P ”admin:N”&&CACLS*” OR CommandHistory=”*/E&&Exit*”))) AND (ImageFileName=”rundll32.exe”) AND ((CommandLine=”*UsersadminAppDataRoaming*” OR CommandLine=”**.DLL*” OR CommandLine=”*Main*” OR CommandLine=”*Roaming**.dll*”) OR (CommandHistory=”*UsersadminAppDataRoaming*” OR CommandHistory=”**.DLL*” OR CommandHistory=”*Main*” OR CommandHistory=”*Roaming**.dll*”))) OR ((ImageFileName=”*.exe”) AND ((CommandLine=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”) OR (CommandHistory=”*UsersadminAppDataLocalTempIXP***.TMP*.exe*”)) AND (ImageFileName=”AppLaunch.exe” OR ImageFileName=”*.exe”) AND ((CommandLine=”*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*”) OR (CommandHistory=”*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*”))))
SumoLogic:
((_sourceCategory=*windows* AND (((((ParentImage = Explorer.EXE) AND (CommandLine=*UsersAdminAppDataLocalTemp*.exe* OR CommandLine=*UsersadminAppDataLocalTempIXP***.TMP*.exe*) AND (Image = *.EXE) AND (CommandLine=*UsersadminAppDataLocalTempIXP***.TMP*.exe*) AND (CommandLine=*UsersadminAppDataLocalTemp**.exe*) AND (Image = schtasks.exe) AND (CommandLine=*/Create /SC MINUTE* OR CommandLine=*/MO 1 /TN* OR CommandLine=*/F*) AND (Image = cmd.exe) AND (CommandLine=*/k echo Y|CACLS* OR CommandLine=*/P “admin:R* OR CommandLine=*/P “admin:N”&&CACLS* OR CommandLine=*/E&&Exit*) AND (Image = rundll32.exe) AND (CommandLine=*UsersadminAppDataRoaming* OR CommandLine=**.DLL* OR CommandLine=*Main* OR CommandLine=*Roaming**.dll*))) OR (((Image = *.exe) AND (CommandLine=*UsersadminAppDataLocalTempIXP***.TMP*.exe*) AND (Image = AppLaunch.exe OR Image = *.exe) AND (CommandLine=*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe*)))))))
Google Chronicle:
rule { meta: version = “0.01” created = “2023-02-17” category = “process_creation” product = “windows” events: (($selection1.principal.process.file.full_path = “Explorer.EXE” and (re.regex($selection1.target.process.command_line, `.*UsersAdminAppDataLocalTemp*.exe.*`) or re.regex($selection1.target.process.command_line, `.*UsersadminAppDataLocalTempIXP***.TMP*.exe.*`)) and re.regex($selection1.target.process.file.full_path, `.*.EXE`) and (re.regex($selection1.target.process.command_line, `.*UsersadminAppDataLocalTempIXP***.TMP*.exe.*`)) and (re.regex($selection1.target.process.command_line, `.*UsersadminAppDataLocalTemp**.exe.*`)) and $selection1.target.process.file.full_path = “schtasks.exe” and (re.regex($selection1.target.process.command_line, `.*/Create /SC MINUTE.*`) or re.regex($selection1.target.process.command_line, `.*/MO 1 /TN.*`) or re.regex($selection1.target.process.command_line, `.*/F.*`)) and $selection1.target.process.file.full_path = “cmd.exe” and (re.regex($selection1.target.process.command_line, `.*/k echo Y|CACLS.*`) or re.regex($selection1.target.process.command_line, `.*/P ”admin:R.*`) or re.regex($selection1.target.process.command_line, `.*/P ”admin:N”&&CACLS.*`) or re.regex($selection1.target.process.command_line, `.*/E&&Exit.*`)) and $selection1.target.process.file.full_path = “rundll32.exe” and (re.regex($selection1.target.process.command_line, `.*UsersadminAppDataRoaming.*`) or re.regex($selection1.target.process.command_line, `.**.DLL.*`) or re.regex($selection1.target.process.command_line, `.*Main.*`) or re.regex($selection1.target.process.command_line, `.*Roaming**.dll.*`))) or (re.regex($selection1.target.process.file.full_path, `.*.exe`) and (re.regex($selection1.target.process.command_line, `.*UsersadminAppDataLocalTempIXP***.TMP*.exe.*`)) and ($selection1.target.process.file.full_path = “AppLaunch.exe” or re.regex($selection1.target.process.file.full_path, `.*.exe`)) and (re.regex($selection1.target.process.command_line, `.*Microsoft.NETFrameworkv4.0.30319AppLaunch.exe.*`)))) condition: $selection1 }
Conclusion
Redline Stealer is a dangerous form of malware that can cause significant harm to individuals and organizations. It is distributed through a variety of means and can remain undetected on a victim’s computer for an extended period. The malware’s capabilities are extensive, and its impact can be devastating. It is essential that individuals and organizations take steps to protect themselves against this threat, including using up-to-date antivirus software and implementing strong security measures. By being aware of the dangers of Redline Stealer, we can take steps to prevent its spread and minimize its impact.
Source: https://www.socinvestigation.com/redline-stealer-returns-with-new-ttps-detection-response/