
New Insikt Group research examines RedHotel, a Chinese state-sponsored threat activity group that stands out due to its persistence, operational intensity, and global reach. RedHotel’s operations span 17 countries in Asia, Europe, and North America from 2021 to 2023. Its targets encompass academia, aerospace, government, media, telecommunications, and research sectors. Particularly focused on Southeast Asia’s governments and private companies in specified sectors, RedHotel’s infrastructure for malware command-and-control, reconnaissance, and exploitation points to administration in Chengdu, China. Its methods align with other contractor groups linked to China’s Ministry of State Security (MSS), indicating a nexus of cyber talent and operations in Chengdu.
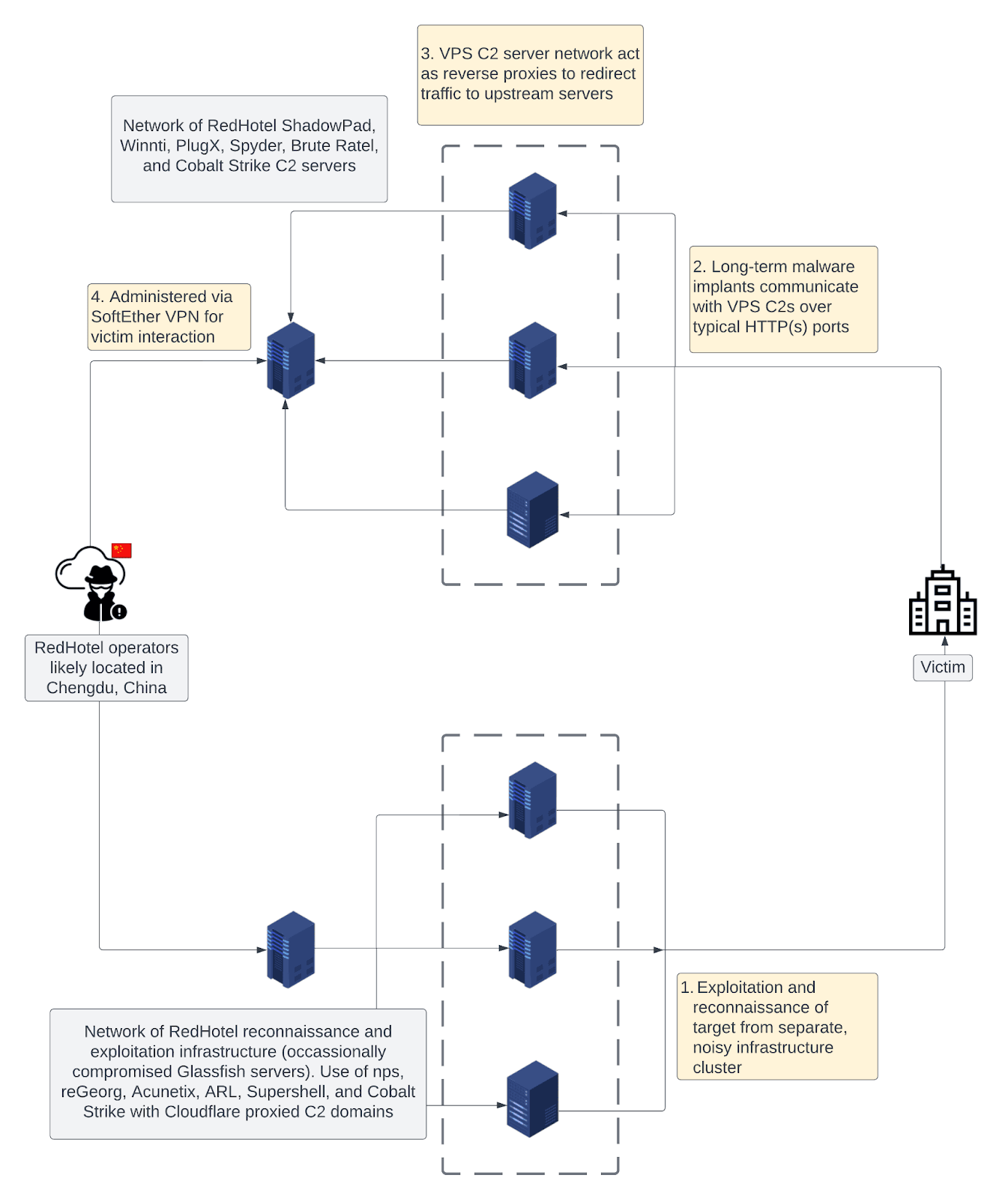
Schematic of RedHotel’s multi-tiered C2 infrastructure network
RedHotel has a dual mission of intelligence gathering and economic espionage. It targets both government entities for traditional intelligence and organizations involved in COVID-19 research and technology R&D. Notably, it compromised a US state legislature in 2022, highlighting its expanded reach. RedHotel employs a multi-tiered infrastructure with a distinct focus on reconnaissance and long-term network access via command-and-control servers.
Since at least 2019, RedHotel has exemplified a relentless scope and scale of wider PRC state-sponsored cyber-espionage activity by maintaining a high operational tempo and targeting public and private sector organizations globally. The group often utilizes a mix of offensive security tools, shared capabilities, and bespoke tooling.
Recorded Future’s Insikt Group observes various Chinese state-sponsored cyber threats, with RedHotel standing out for its broad scope and intensity of activity. RedHotel’s campaigns include innovations such as exploiting a stolen code signing certificate and commandeering Vietnamese government infrastructure. Despite public exposure, RedHotel’s bold approach suggests it will persist in its activities.
To read the entire analysis with endnotes, click here to download the report as a PDF.
Appendix A — Indicators of Compromise
|
Domains: dga[.]asia kb.dga[.]asia video.dga[.]asia sc.dga[.]asia dgti.dga[.]asia nhqdc[.]com msdn.microsoft.nhqdc[.]com icoreemail[.]com demo.icoreemail[.]com officesuport[.]com kiwi.officesuport[.]com cdn.officesuport[.]com test.officesuport[.]com mail.officesuport[.]com ntpc.officesuport[.]com main.officesuport[.]com excel.officesuport[.]com remote.officesuport[.]com ismtrsn[.]club lrm.ismtrsn[.]club tgoomh.ismtrsn[.]club news.ismtrsn[.]club icarln.ismtrsn[.]club liveonlin[.]com npgsql.liveonlin[.]com public.liveonlin[.]com tech.liveonlin[.]com main.liveonlin[.]com cctv.liveonlin[.]com alexa-api[.]com www.alexa-api[.]com ngndc[.]com air.ngndc[.]com spa.ngndc[.]com mkn.ngndc[.]com ekaldhfl[.]club ts.ekaldhfl[.]club ist.ekaldhfl[.]club downloads.ekaldhfl[.]club pps.ekaldhfl[.]club plt.ekaldhfl[.]club tlt.ekaldhfl[.]club thy.ekaldhfl[.]club us.ekaldhfl[.]club asia-cdn[.]asia report.asia-cdn[.]asia freehighways[.]com map.freehighways[.]com iredemail[.]com index.iredemail[.]com demo.iredemail[.]com open.iredemail[.]com api.iredemail[.]com full.iredemail[.]com bbs.iredemail[.]com 0nenote[.]com keep.0nenote[.]com asia-cdn[.]asia api.asia-cdn[.]asia speedtest.asia-cdn[.]asia cyberoams[.]com checkip.cyberoams[.]com ekaldhfl[.]club pps.ekaldhfl[.]club usa.ekaldhfl[.]club mtlklabs[.]co conhostsadas[.]website itcom666[.]live qbxlwr4nkq[.]itcom666[.]live 8kmobvy5o[.]itcom666[.]live itcom888[.]live bwlgrafana[.]itcom888[.]live itsm-uat-app[.]itcom888[.]live dkxvb0mf[.]itcom888[.]live nvw3tdetwx[.]itcom888[.]live 0j10u9wi[.]itcom888[.]live yt-sslvpn[.]itcom888[.]live vappvcsa[.]itcom888[.]live 94ceaugp[.]itcom888[.]live sibersystems[.]xyz fyalluw0[.]sibersystems[.]xyz sijqlfnbes.sibersystems[.]xyz jmz8xhxen3.sibersystems[.]xyz 2h3cvvhgtf.sibersystems[.]xyz 3tgdtyfpt9.sibersystems[.]xyz n71qtqemam.sibersystems[.]xyz 711zm77cwq.sibersystems[.]xyz R77wu4s847.sibersystems[.]xyz caamanitoba[.]us jw7uvtodx4.caamanitoba[.]us xdryqrbe.caamanitoba[.]us b1k10pk9.caamanitoba[.]us 6hi6m62bzp.caamanitoba[.]us livehost[.]live sci.livehost[.]live C2 IP Addresses (seen May to June 2023) TLS Certificate (SHA256 Fingerprints): Cobalt Strike Loaders Brute Ratel Loaders Winnti Spyder FunnySwitch |
Appendix B — Mitre ATT&CK Techniques
| Tactic: Technique | ATT&CK Code | Observable |
| Reconnaissance: Active Scanning: Vulnerability Scanning | T1595.002 | RedHotel has used vulnerability scanning tools such as Acunetix to scan externally facing appliances for vulnerabilities |
| Resource Development: Acquire Infrastructure: Domains | T1583.001 | RedHotel has purchased domains, primarily via Namecheap. |
| Resource Development: Acquire Infrastructure: Virtual Private Server | T1583.003 | RedHotel has provisioned actor-controlled VPS, with a preference for the providers Choopa (Vultr), G-Core, and Kaopu Cloud HK Limited. |
| Resource Development: Compromise Infrastructure: Server | T1584.004 | RedHotel has also used compromised GlassFish servers as Cobalt Strike C2s and to scan target networks. |
| Initial Access: Exploit Public-Facing Application | T1190 | RedHotel has exploited public-facing applications for initial access, including Zimbra Collaboration Suite (CVE-2022-24682, CVE-2022-27924, CVE-2022-27925 chained with CVE-2022-37042, and CVE-2022-30333), Microsoft Exchange (ProxyShell), and the Log4Shell vulnerability in Apache Log4J. |
| Initial Access: Spearphishing: Spearphishing Attachment | T1566.001 | RedHotel has used archive spearphishing attachments containing shortcut (LNK) files which fetch remotely hosted scripts (HTA, VBScript). These scripts are then used to trigger DLL search order hijacking infection chains and display decoy documents to users. |
| Persistence: Server Software Component: Web Shell | T1505.003 | RedHotel has used web shells within victim environments and to interact with compromised GlassFish servers |
| Persistence:: Scheduled Task/Job: Scheduled Task | T1053.005 | RedHotel has used scheduled tasks for persistence for the group’s Spyder backdoor:
|
| Persistence: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 | The ScatterBee ShadowPad loader persists via the Run registry key and also stores the encrypted ShadowPad payload in the registry. |
| Defense Evasion: Obfuscated Files or Information | T1027 | RedHotel has used the tool ScatterBee to obfuscate ShadowPad payloads. The group has also repeatedly stored encrypted or encoded payloads within files named bin.config.
|
| Defense Evasion: Deobfuscate/Decode Files or Information | T1140 | |
| Defense Evasion: Subvert Trust Controls: Code Signing | T1553.002 | RedHotel has signed malicious binaries using stolen code signing certificates (such as the referenced WANIN International certificate). |
| Defense Evasion: Hijack Execution Flow: DLL Search Order Hijacking | T1574.001 | RedHotel has abused multiple legitimate executables for DLL search order hijacking, including vfhost.exe, mcods.exe, and BDReinit.exe.
|
| Defense Evasion: Masquerading: Match Legitimate Name or Location | T1036.005 | RedHotel has used legitimate file names in tandem with DLL search order hijacking to load malicious DLLs. |
| Command and Control: Proxy: External Proxy | T1090.002 | RedHotel has used VPS C2s to proxy traffic upstream to actor-controlled servers. |
| Command and Control: Application Layer Protocol: Web Protocols | T1071.001 | RedHotel Brute Ratel and Cobalt Strike samples referenced within this report communicate over HTTPS. |
| Exfiltration: Exfiltration Over C2 Channel | T1041 | RedHotel has exfiltrated data over malware C2 channels. |
Source: Original Post
“An interesting youtube video that may be related to the article above”