In recent years, efforts to apprehend threat groups and shrink their operating landscape have gone international. As authorities across multiple countries continue to implement sanctions and openly communicate current trends to the public, threat groups increasingly resort to rebranding or creating similar variants under different names to sidestep crackdowns and obfuscate their identities.
In a February 2023 blog post, Ahnlab described a new ransomware campaign affecting South Korean organizations which deployed a malware they dubbed “TZW” ransomware. Our research links TZW ransomware to a known malware family called GlobeImposter (sometimes referred to as LOLNEK or LOLKEK). Close inspection of host origins and prominent file similarities used in both TZW and GlobeImposter campaigns suggest that actors behind GlobeImposter are updating their payloads and obfuscating their infrastructure in a manner consistent with a rebrand effort.

Overview of GlobeImposter & New Variant TZW
GlobeImposter has a long and winding history. First observed in-the-wild in 2016, the name “GlobeImposter” is based on the ransomware’s mimicry of Globe ransomware payloads. Multiple new versions and variations of GlobeImposter have appeared in the years since. Frequently, these have been referred to by their extension (e.g., .DREAM, .Nutella, .NARCO, .LEGO). However, these are all part of the same umbrella malware family. In that same year, Emisoft released a decryption tool for early versions of GlobeImposter. Shortly after, the malware authors responded with an updated version for which no decryption tools are available.
Since 2017, campaigns delivering GlobeImposter have continued to proliferate even though the ransomware has only evolved slightly. The ransomware has also been used in conjunction with some well-documented high-end cybercriminal groups. For example, in 2017 TA505 (also known as G0092, GOLD TAHOE) began using GlobeImposter in replacement of Jaff, GandCrab, and Snatch to extend the reach and effectiveness of their campaigns.
GlobeImposter’s Delivery Methods Explained
GlobeImposter is most often delivered via phishing email as an attachment or a link to a malicious attachment. The payloads are typically distributed via 7zip or traditional zip file archives. The archives often include a JavaScript (.js) file that downloads and executes the GlobeImposter payload.
More recent campaigns from within the past three years still tend to follow this formula.
GlobeImposter has also been distributed as a later-stage infection within some well-known botnets. For example, in 2017 GlobeImposter was distributed via the Necurs botnet. This occurred as part of multiple spam campaigns that also included 7zip archives and followed the execution flow previously described.
Linking TZW Attacks to GlobeImposter
AhnLab’s research revealed a ransomware campaign they referred to as “TZW” with victims in South Korea. The name is derived from the first 3 characters of the TOR-based victim portal. A closer look suggests that “TZW” samples represent a new variant of the GlobeImposter family.
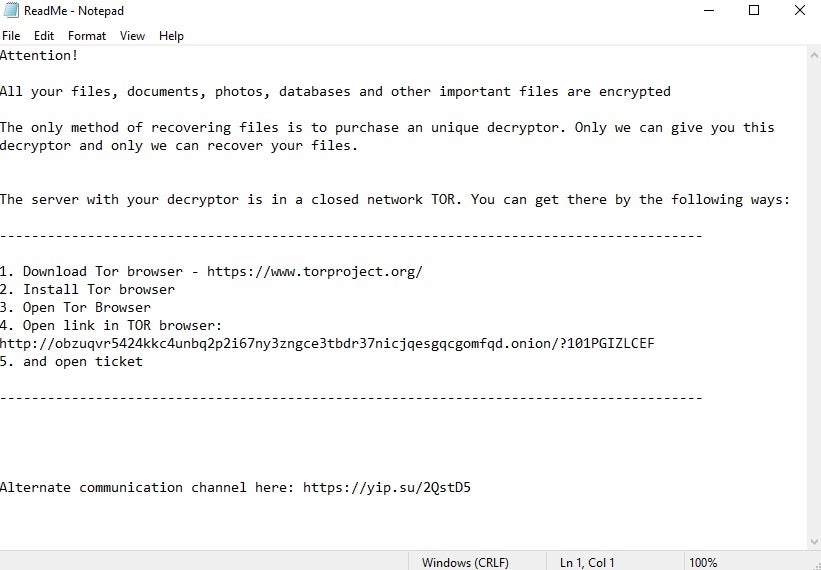
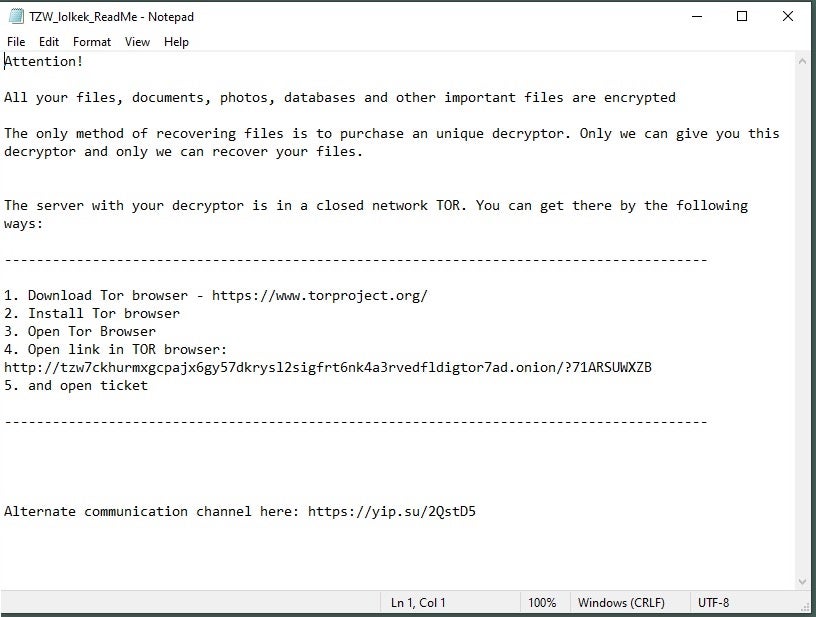
The pre-TZW GlobeImposter ransom notes follow the same template as the current TZW samples. Ransom note similarities are far from reliable, but it’s worth noting their likenesses.
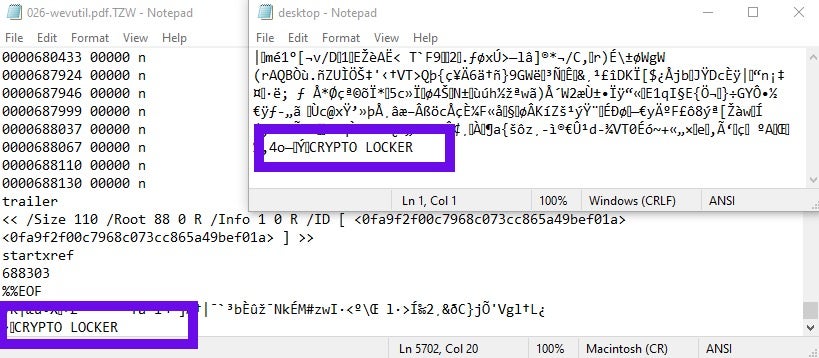
Once a machine is infected, more concrete markers indicate a deeper level of similarity. One such marker is the “CRYPTO LOCKER” string appended to the tail of the encrypted files. This is a known marker present across GlobeImposter variants.
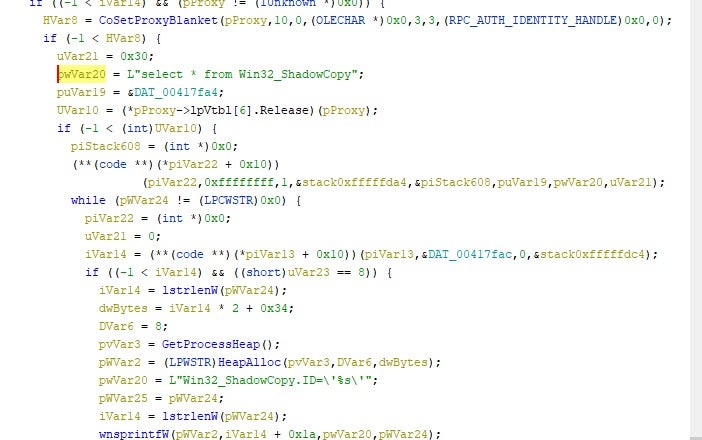
GlobeImposter has the ability to delete volume shadow copies, thereby inhibiting the recovery of data. There are clear similarities around the methodology of the VSS removal.
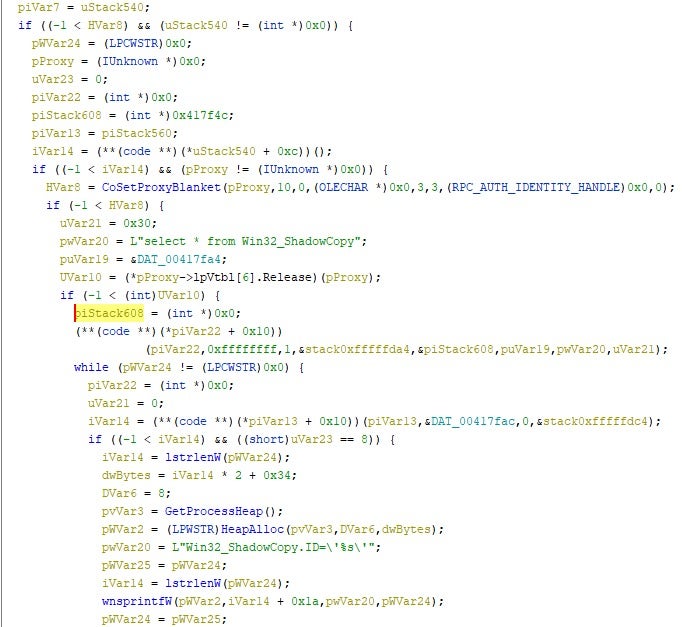
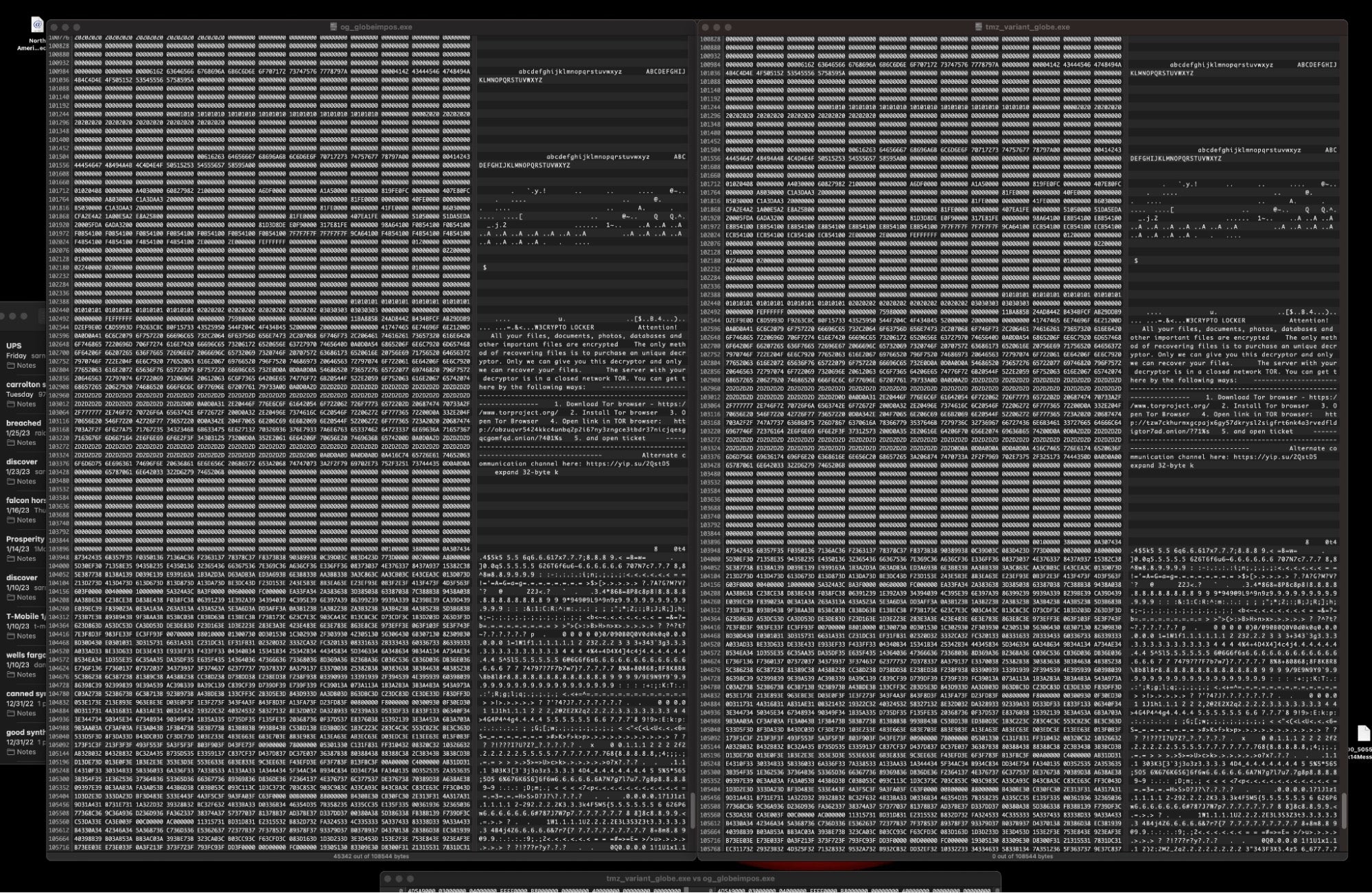
Code and functionality, by and large, are identical across GlobeImposter payloads pointing to obzuqvr5424kkc4unbq2p2i67ny3zngce3tbdr37nicjqesgqcgomfqd[.] onion and those pointing to the newer tzw7ckhurmxgcpajx6gy57dkrysl2sigfrt6nk4a3rvedfldigtor7ad[.]onion.
A thorough comparison of the two respective samples shows there are only minor differences.
AhnLab’s research describes artifacts from a specific sample within a specific campaign. We have seen the newer TZW variations vary somewhat with regards to file metadata.
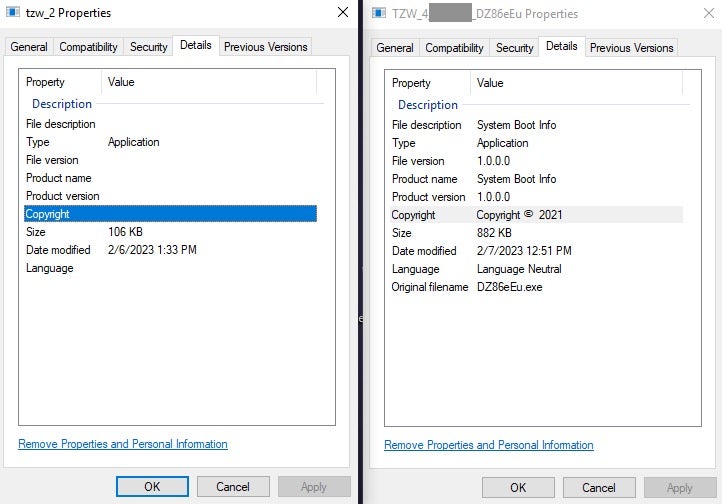
A majority of the TZW variant samples that we have analyzed resemble the version on the left hand side. The version on the right was seen in the samples noted by AhnLab.
Understanding TZW and GlobeImposter’s Shared Infrastructure
Previous GlobeImposter payloads directed victims to a TOR-based portal at obzuqvr5424kkc4unbq2p2i67ny3zngce3tbdr37nicjqesgqcgomfqd[.]onion.
Beginning in late 2022, we start to see victims also being directed to tzw7ckhurmxgcpajx6gy57dkrysl2sigfrt6nk4a3rvedfldigtor7ad[.]onion. The interfaces and required steps are identical:
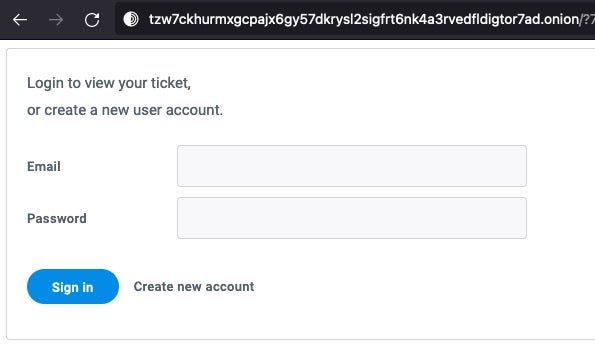
At the time of writing, both victim portals remain active. In addition, we can confirm the relationship between these via the publicly-viewable Apache Server Status Page.
This Apache status screen is visible as a result of a misconfiguration on the Apache server, allowing us to see all the active vhosts (virtual hosts) present there.
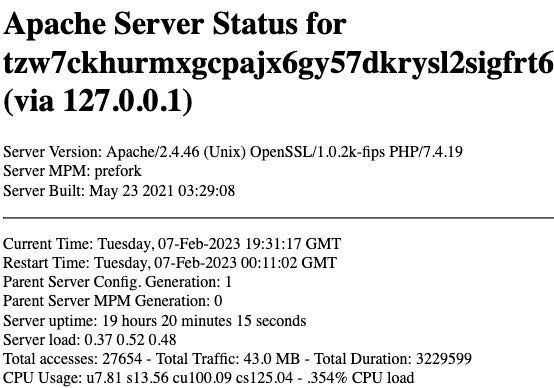
Through this view we see that the following vhosts are active on the device.
obzuqvr5424kkc4unbq2p2i67ny3zngce3tbdr37nicjqesgqcgomfqd[.]onion tzw7ckhurmxgcpajx6gy57dkrysl2sigfrt6nk4a3rvedfldigtor7ad[.]onion linux[.]3bcd0a[.]com
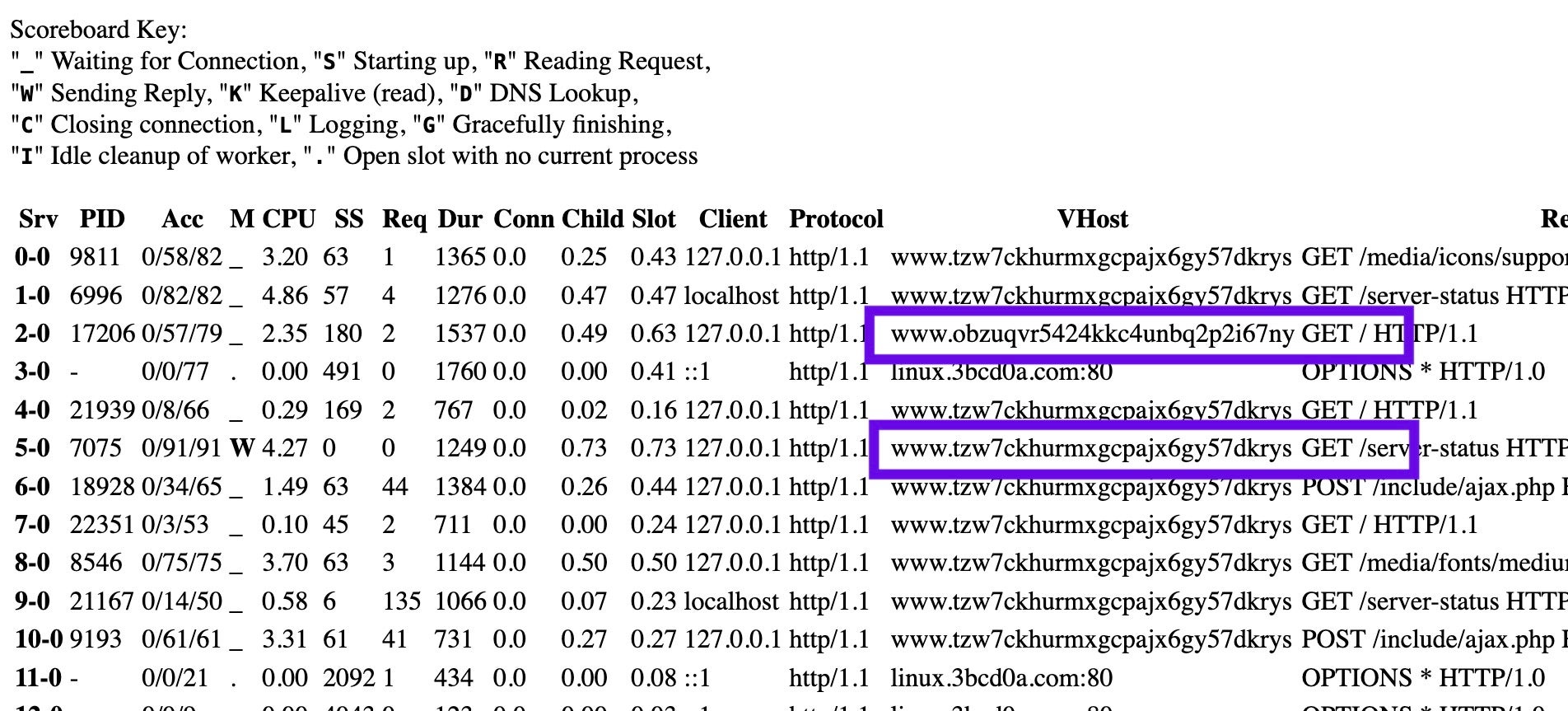
This evidence of shared infrastructure suggests that the newly rebranded TZW ransomware samples are likely being operated by the same group that was pushing recent waves of GlobeImposter malware.
How to Protect Against GlobeImposter and TZW Ransomware
SentinelOne Singularity™ protects against malicious behaviors and malware associated with GlobeImposter and TZW.
With the site policy set to Protect, GlobeImposter ransomware is detected and prevented automatically. In Detect-only mode, analysts can observe the malware’s behaviour and file encryption attempts, rolling back the device to a clean state on completion of the test.
Conclusion
Based on our analysis, the TZW ransomware recently documented by AhnLab is yet another example of the threat actors behind GlobeImposter pivoting their TTPs alongside a rebrand, including a new but related Onion address. We also show that the old “LOLNEK” Onion address and the Onion address within the TZW variant are hosted on the same server as two vhosts.
Regardless of the name or brand, GlobeImposter continues to pose a threat to enterprises. Ensuring good user hygiene, along with strong, properly-configured, and robust security controls will go a long way to prevent these attacks from affecting your environment.
SentinelOne Singularity™ protects against malicious behaviors and malware associated with GlobeImposter and TZW.
Indicators of Compromise
SHA1
4585da0ff7a763be1a46d78134624f7cd13e6940
14be1c43fbfb325858cda78a126528f82cf77ad2
dc98b516c9c589c2b40bc754732ad5f16deb7c82
d034880d1233d579854e17b6ffad67a18fb33923
858f3f7f656397fcf43ac5ea13d6d4cbe7a5ca11
9a080cd497b8aa0006dc953bd9891155210c609c
8c64e820a4c5075c47c4fbaea4022dc05b3fd10b
3326708ba36393b1b4812aa8c88a03d72689ac24
cf5ab37612f24ed422a85e3745b681945c96190e
cf21028b54c4d60d4e775bf05efa85656de43b68
Onions
tzw7ckhurmxgcpajx6gy57dkrysl2sigfrt6nk4a3rvedfldigtor7ad[.]onion
obzuqvr5424kkc4unbq2p2i67ny3zngce3tbdr37nicjqesgqcgomfqd[.]onion
MITRE ATT&CK
T1005 – Data from Local System
T1202 – Indirect Command Execution
T1486 – Data Encrypted for Impact
T1070.004 – Indicator Removal: File Deletion
T1112 – Modify Registry
T1012 – Query Registry
T1083 – File and Directory Discovery
T1027.002 – Obfuscated Files or Information: Software Packing
T1082 – System Information Discovery
T1490 – Inhibit System Recovery
T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder