Introduction
In late 2023 and early 2024, the ransomware ecosystem experienced repeated disruption of its most prolific Ransomware-as-a-Service (RaaS) groups at the hands of international Law Enforcement (LE). Alphv’s dark web data leak site was seized, then unseized, then re-seized in a December 2023 law enforcement operation that seemingly failed to deter the group – until AlphV ultimately claimed to disband via an apparent exit scam, immediately following a high-profile attack against Change Healthcare in March 2024. LockBit experienced a far more dramatic and well-marketed disruption, “Operation Cronos,” in February 2024, leading to the compromise of its infrastructure, internal operational details, and data. While LockBit has ostensibly continued operations, its highly publicized disruption raises the question of whether the group will be able to continue operating and attracting affiliates at the level they once enjoyed.
RaaS operations depend not just on the core ransomware group, which maintains infrastructure and the namesake ransomware; but also on affiliates, who perform the grunt work of hands-on-keyboard intrusions, and which may support multiple ransomware groups. With a few exceptions resulting from Operation Cronos, the affiliates that support RaaS groups remain “in the wild” and available to reorganize or support other RaaS groups, which leads to the inevitable questions: Where will these affiliates go next, and how will they decide? In the course of our Deep and Dark Web (DDW) research in the wake of Operation Cronos, we have identified multiple smaller RaaS groups attempting to welcome displaced affiliates with open arms, likely seeing a recruitment opportunity emerging out of recent disruptions.
Operation Cronos, Disruption, and Deception
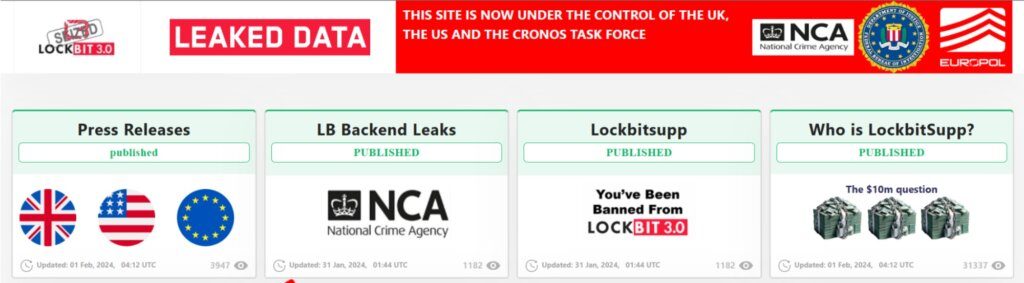
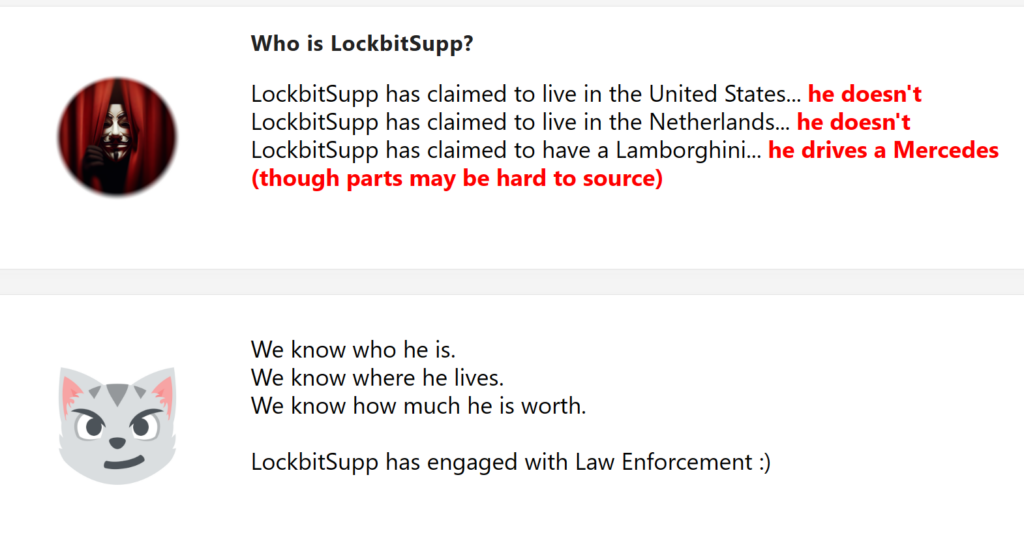
As part of February’s Operation Cronos–a combined UK National Crime Agency (NCA) operation–the newfound owners of LockBit’s infrastructure replaced elements of LockBit’s data leak site with Law Enforcement agency banners and logos, a tongue-in-cheek mimicry of LockBit’s iconic site design. Over the next several days, Cronos’ component agencies dangled a series of disclosures, each alluded to with countdown timers and enticing titles such as “LB Backend Leaks” and “Who is LockbitSupp?” The latter post attracted a great deal of speculation that the ambitious Administrator persona behind LockBit, known by the pseudonym “LockBitSupp,” had been identified by law enforcement. Sadly, this dream would ultimately end unrealized, as the new site owners posted a series of cryptic assertions pertaining to LockBitSupp’s identity but falling short of a full-fledged identification (or indictment). Importantly, amongst these assertions were the words “LockbitSupp has engaged with Law Enforcement 
(Black)Cat, Domesticated
Following the disruption of their data leak site in December 2023, Alphv appeared to pursue damage control, increasing the affiliate split of ransoms to 90% and declaring the removal of all target restrictions except for bans on attacking organizations in the Commonwealth of Independent States (CIS, consisting of the Russophone nations of Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Romania, Russia, Tajikistan, and Uzbekistan). Alphv reconstituted replacement infrastructure and appeared to resume operations until they announced Change Healthcare as a high-profile victim. On March 1st, a user on the illicit dark web forum RAMP, under the moniker “notchy,” alleged that they had been the affiliate responsible for the attack on Change Healthcare, that they had received no share of a $22 Million ransom payment, that their access to the Alphv affiliate panel had been revoked, and that they retained copies of Change Healthcare’s data.
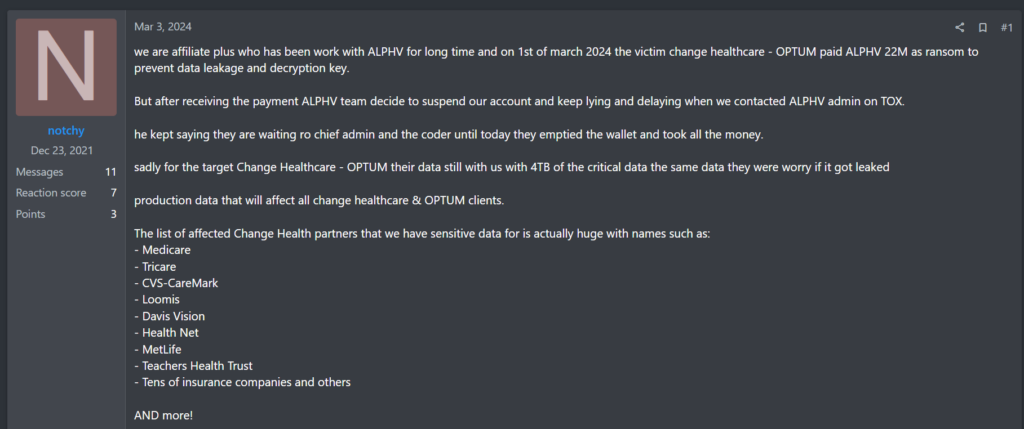
The same user would go on to provide evidence: a link to a blockchain tracking website reflecting the alleged ransom payment amount and its subsequent transfer; and a chat log with the Alphv administrator that allegedly substantiated notchy’s claims. A short two days later, Alphv’s data leak site was updated to display a familiar banner, explaining that the site had once more been seized by Law Enforcement.
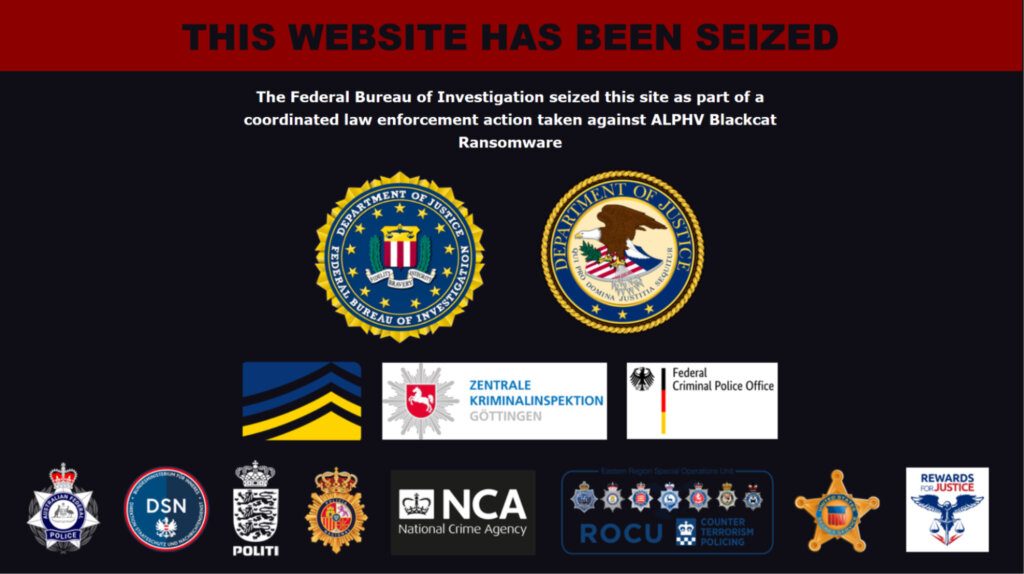
On the surface, the situation appeared to reflect additional law enforcement disruption impacting Alphv, but security researchers soon alleged that Alphv was instead “staging” a second takedown, based on a review of the page source indicating that “the seizure notice had been copied.” On March 5th, an apparent spokesperson for Alphv, using the moniker “Ransom,” replied to notchy’s accusations on RAMP:
“Yes, we knew about the problem, and we were trying to solve it. We told the affiliate to wait. We could send you our private chat logs where we are shocked by everything that’s happening and are trying to solve the issue with the transactions by using a higher fee, but there’s no sense in doing that because we decided to fully close the project. We can officially state that we got screwed by the feds.”
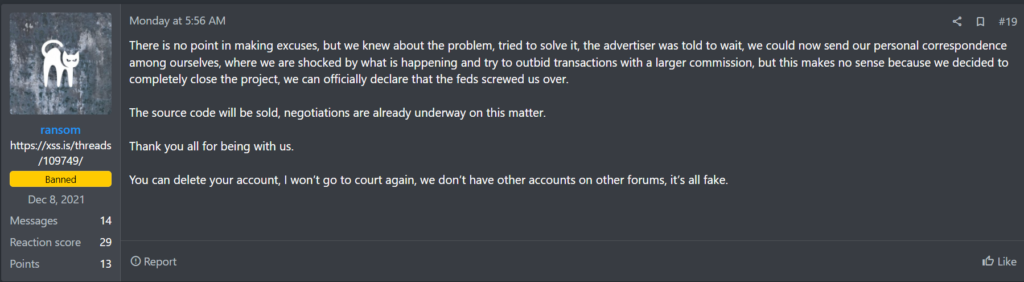
The emerging consensus amongst the security community has become that this series of events reflects a thinly veiled “exit scam,” with Alphv’s administrators absconding with one last large ransom while providing a plausible explanation and blaming Law Enforcement for the impacts.
(Dis)Honor Amongst Thieves
We assess that LockBit is likely to continue operations with some affiliates in the near term, but we expect the total number of affiliates to decrease. These disruptive events have resulted in distrust towards the most Established RaaS groups in the ransomware ecosystem today, including LockBit, and will almost certainly lead to the displacement of some portion of the associated affiliate corps; Reasons for departure may ultimately vary from distrust to disillusionment, to newfound unemployment. While some affiliates undoubtedly belong to more than one RaaS group, this is not universally true, and displaced affiliates may seek a new home out of preference or out of necessity going forward. Other RaaS groups have taken note.
Amidst RaaS groups, there are varying levels of operational tempo and maturity, with over 40 distinct groups claiming monthly victims ranging from none to double digits. While some groups start and stay “low level,” others aspire to grow and expand their operations. Given a potential influx of experienced affiliates, we have observed attempts by at least three smaller RaaS groups – Medusa, Cloak, and RansomHub – to attract or recruit new members through advertisements on Deep and Dark Web illicit forums. Each of these groups falls within different levels of GRIT’s Ransomware Taxonomy, indicating that RaaS groups of varying maturity levels are seeking to take advantage of circumstances.
All Eyes on Medusa
We first observed the RaaS group Cloak posting on the illicit forum UFO Labs, while Medusa and RansomHub opted for the Russian-language RAMP forum for their advertisements. Each advertisement contains some fairly boilerplate details of the group, including a short description, ransom split rates, and communications details for contact over TOX. Encryption strength is touted, ease of panel use is claimed, and opportunity abounds for those interested “pentesters” out there. Aside from these similarities, we noticed some disparities in the approach of each distinct group.
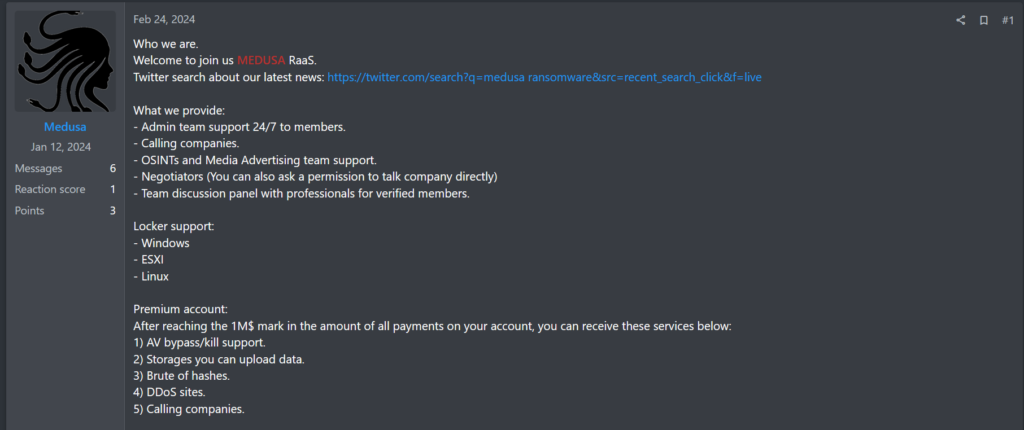
As objective outside reviewers, we considered Medusa’s post particularly appealing, as the group claims a sliding payout scale, starting at a 70/30 affiliate/core split, increasing up to 90/10, dependent on the size of the ransom payment obtained; only affiliates in receipt of a $1 Million+ ransom is eligible for a 90/10 split, likely incentivizing or creating the appearance of high ransom demands. To achieve these handsome ransom payments, Medusa offers 24/7 support of their “admin team,” “media advertising team,” and their own “negotiators,” should the prospective affiliate wish to take advantage. On 12 March, the group posted in a response on RAMP forums that they accept non-Russian speakers and “welcome teams worldwide”.
(Ransom)Hub and Spoke Model
RansomHub, by comparison, appears to have taken a less materialistic approach and opted to rely on contemporary events as a persuasive tool. A user on RAMP forums under the moniker “koley” opens the RansomHub advertisement by alluding to the recent Law Enforcement disruptions:
“We have noticed that some affiliates have been seized by the police or have escaped from fraudulent activity causing you to lose your funds.”
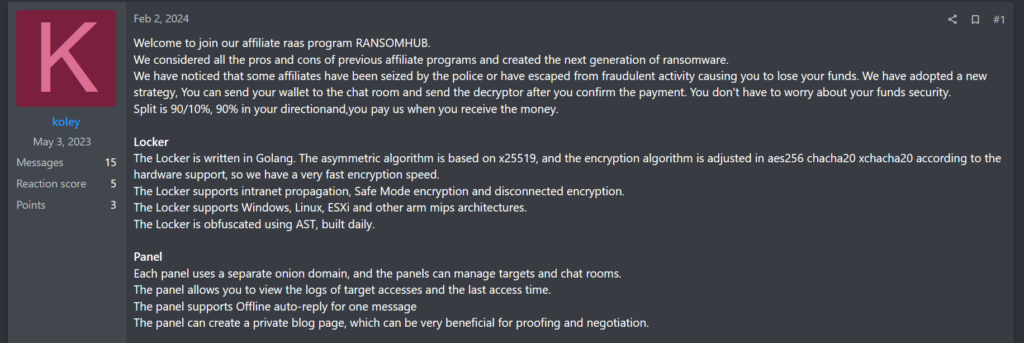
RansomHub continues implicitly addressing the crisis of confidence in RaaS groups by declaring that its affiliates are able to collect ransom payments directly before paying the core group a 10% fee. This approach is likely intended to assuage concerns of “exit scams” or other deceits that have been circulating as gossip and accusations around the proverbial cybercrime watercooler as of late. Finally, the group explicitly references participation in multiple RaaS groups as permitted, rounding out an open and welcome advertisement as the junior-most group we observed advertising.
Cloak and Dagger
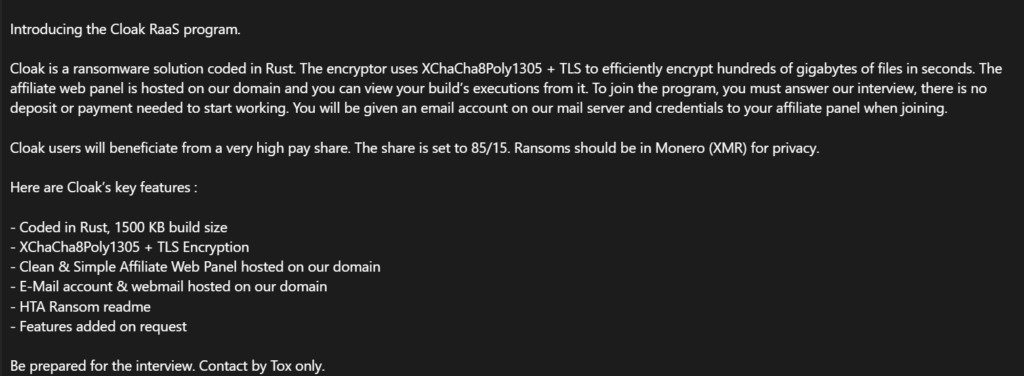
In comparison to Medusa and RansomHub, the RaaS group Cloak’s advertisement appears the least remarkable, with few unique features that would entice a potential affiliate with options. The advertisement clarifies that “Ransoms should be in Monero (XMR) for privacy,” a frequent request by ransomware affiliates due to the traceability of Bitcoin transactions, but one that is less frequently indulged by victims. Cloak advertises a respectable 85/15 affiliate/core split of ransoms and requires no deposit or payment to join their ranks; an interview, instead, is proposed to vet new entrants. Cloak highlights the strength of its ransomware and the availability of features for addition on request, but otherwise fails to advertise the full services and generous ransom splits of its sister RaaS groups we observed.
Desperately Seeking Cybercriminals
Outside of these advertisements from known and active RaaS groups, we have also observed recent attempts to capitalize on prospective and current RaaS affiliates elsewhere across the Deep and Dark Web, including the following:
A March 12 post on the illicit forum “CyberNulled” advertising a $100/month or $800/year subscription membership to “RAAS FLOCKER’s elite affiliate program,” a vaguely named service offering that promises “access to the latest [ransomware] tools and techniques,” “[securing] your spot in the ransomware market with unparalleled access,” and “a lucrative share of the profits for each successful campaign you execute.”

A February 12 post advertising “BEAST Ransomware” for Windows, Linux, and ESXi, from a new forum member on the illicit Breach Forums. When confronted about their lack of credibility or members vouching for their offering, the initial posting user iterated that their program offers “The most favorable conditions on the market and dynamic raites for each advert. First contact with a description of your experience, availability of targets for attacks.” While this strain of ransomware has been advertised on illicit forums intermittently since at least mid-2022, users on forums have responded with dismissal or scrutiny in recent months.
Conclusion
As we have assessed in GRIT’s ransomware taxonomy and our recurring Ransomware Reports, ransomware groups, including RaaS groups, most frequently Rebrand or Splinter as a means of continuing operations in the wake of law enforcement scrutiny. Affiliates, by comparison, face a marketplace of competing RaaS groups with a limited talent pool of affiliates from which to draw; recent increases in advertisements for affiliates may indicate continued limitations in available human resources, growing distrust in particular RaaS groups or the RaaS operating model, or impacted groups that do not intend to continue operations. If affiliates were to migrate to other RaaS groups, we would expect to see a decrease in posted victims from the losing RaaS groups and an increase in posted victims from gaining RaaS groups; We would also expect to see higher-profile victims attributable to historically less mature RaaS groups.
We intend to continue monitoring for additional signs of distrust and discontent among RaaS groups and affiliates as indications that the RaaS model may be becoming increasingly scrutinized, particularly as RaaS TTPs make the entrance of scammers and unskilled actors easier. From a Law Enforcement and policy lens, murmurs within the RaaS ecosystem and its component members likely represent an opportunity to encourage discord, amplify skeptical messaging, and solicit collaborators with unique access or connections.