Summary: This content discusses the RansomHub ransomware-as-a-service, which is believed to have evolved from the now-defunct Knight ransomware project. RansomHub operates as a data theft and extortion group that sells stolen files to the highest bidder.
Threat Actor: RansomHub | RansomHub
Victim: United Health subsidiary Change Healthcare | Change Healthcare
Key Point :
- RansomHub is a relatively new ransomware-as-a-service that has evolved from the now-defunct Knight ransomware project.
- RansomHub operates as a data theft and extortion group, selling stolen files to the highest bidder.
- RansomHub gained attention when it leaked stolen data from Change Healthcare following a BlackCat/ALPHV attack, suggesting collaboration between the two.
- RansomHub also threatened to leak stolen data from Christie’s, an international auction house.
- Knight ransomware, the predecessor of RansomHub, launched in late July 2023 and targeted Windows, macOS, and Linux/ESXi machines to steal data and demand ransom.
- Knight ransomware offered affiliates an info-stealer component to enhance the impact of attacks.

Security researchers analyzing the relatively new RansomHub ransomware-as-a-service believe that it has evolved from the currently defunct Knight ransomware project.
RansomHub has a short history and operated mainly as a data theft and extortion group that sells stolen files to the highest bidder.
The gang grabbed attention in mid-April when it leaked stolen data from United Health subsidiary Change Healthcare following a BlackCat/ALPHV attack, suggesting some form of collaboration between the two.
More recently, on May 28, the international auction house Christie’s admitted it had suffered a security incident after RansomHub threatened to leak stolen data.
Knight ransomware launched in late July 2023 as a re-brand of the Cyclops operation and started breaching Windows, macOS, Linux/ESXi machines to steal data and demand a ransom.
One of the peculiarities of Knight was that it also offered affiliates an info-stealer component that could make the attacks more impactful.
In February 2024, the source code for version 3.0 of Knight ransomware put up for sale on hacker forums, the victims extortion portal went offline, and the RaaS operation went silent.
source: KELA
RansomHub’s Knight origin
Malware analysts at Symantec, part of Broadcom, found multiple similarities between the two ransomware families that point to a common origin:
- Both ransomware families are written in Go and use Gobfuscate for obfuscation.
- There are extensive code overlaps in the two malware payloads.
- Both use a unique obfuscation technique where important strings are encoded with unique keys.
- The ransom notes used by the two ransomware families are similar, with minor updates added on RansomHub.
- Both ransomware families restart endpoints in safe mode before encryption.
- The command-line help menus on the two families are identical, with the only difference being a ‘sleep’ command on RansomHub.
- The sequence and method of command execution operations are the same, though RansomHub now executes them via cmd.exe.
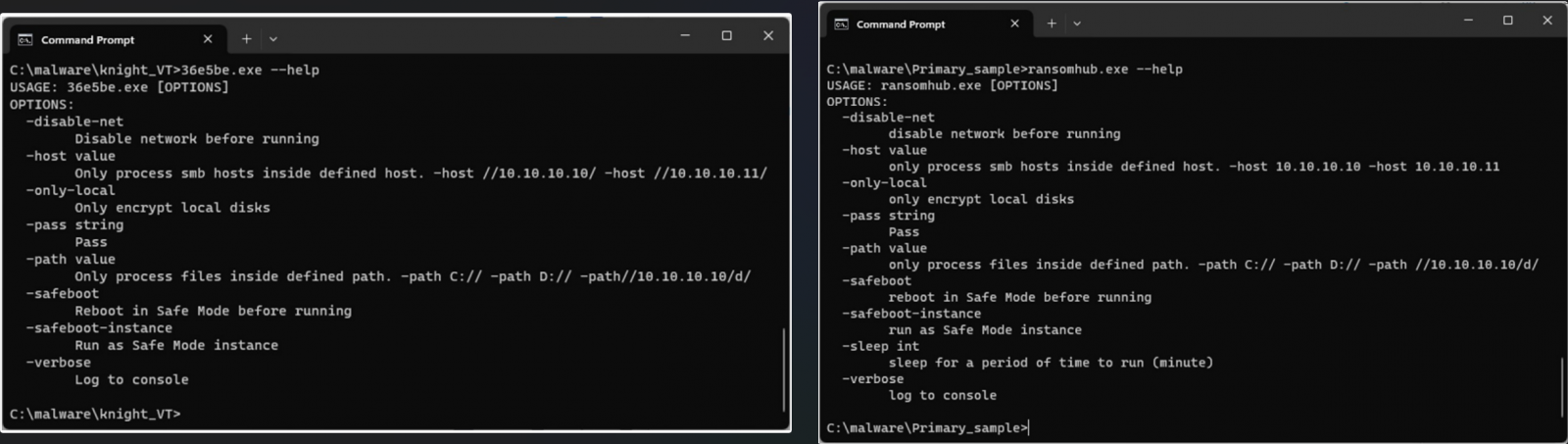
Source: Symantec
The above suggests that RansomHub was likely derived from Knight, and confirms that the extortion group indeed uses a data encryptor.
Also, the time RansomHub first appeared in the cybercrime space, in February 2024, matches the Knight source code sale.
According to the researchers, it is unlikely that RansomHub is run by Knight ransomware creators. They believe that another actor purchased the Knight source code and started using it in attacks.
Since it emerged, RansomHub has grown to become one of the most prolific RaaS operations, which Symantec attributes to the gang attracting former affiliates of the ALPHV operation, such as Notchy and Scattered Spider.
“An interesting youtube video that may be related to the article above”