Short Summary
The CERT-AGID has issued an alert regarding a large-scale malspam campaign aimed at distributing the Quasar RAT malware. This campaign, which utilizes official logos from the Ministry of the Interior to deceive victims, was first identified on August 16, 2024. The malware targets users of specific Italian banks.
Keypoints
- Massive malspam campaign identified by CERT-AGID on August 16, 2024.
- Quasar RAT malware is being distributed through deceptive emails.
- Attackers are using official logos from the Ministry of the Interior.
- The malware version used is “1.0.00.r6” with unchanged C2 servers.
- Strings in the malware are encoded with XOR algorithm.
- Targeted attacks focus on users of specific Italian banks.
- Indicators of Compromise (IoCs) have been shared with accredited organizations.
MITRE ATT&CK TTPs – created by AI
- Credential Dumping (T1003)
- Procedures: The malware may attempt to gather credentials from the infected system.
- Remote Access Tools (T1219)
- Procedures: Utilizes Quasar RAT for remote access and control of infected systems.
- Phishing (T1566)
- Procedures: Employs deceptive emails to lure victims into executing the malware.
Full Article Translation
19/08/2024
The CERT-AGID has recently issued an alert on the official Telegram channel regarding a massive malspam campaign, first identified by this CERT on Friday, August 16, aimed at spreading the Quasar RAT malware. We reiterate the rarity of this event in the Italian context.
The attacks continue with new campaigns that exploit institutional logos from the Ministry of the Interior to impersonate official communications and deceive victims.
The version of the RAT used this week, “1.0.00.r6”, is the same as the previous week. The C2 servers remain unchanged, while the URLs of the repositories from which the executables are downloaded have changed.
All strings are encoded with the XOR algorithm, and the key is obviously included in the code. It was therefore possible to decode the strings to make them readable. Below is the Python function used for decoding.
import binascii
def decrypt_xor(encrypted_text_with_iv):
array = encrypted_text_with_iv.split(':')
if len(array) != 2:
raise ValueError("Invalid encrypted text format.")
hex1 = array[0]
hex2 = array[1]
array2 = binascii.unhexlify(hex1)
array3 = binascii.unhexlify(hex2)
fixed_key = "Ro54jbrahHe0vZbfHzp9hUuRf7hJsuuyKLy3eNZ4edLAZqEXagk0x5wgV2w6MTKS96ry6yYfMjfEo5e94xN9lhN4kQLNty1tBpIt"
bytes_key = fixed_key.encode('utf-8')
array4 = bytearray(len(array3))
for i in range(len(array3)):
array4[i] = array3[i] ^ bytes_key[i % len(bytes_key)] ^ array2[i]
return array4.decode('utf-8')
After decoding the strings, the objective becomes evident: to target users of specific Italian banks.
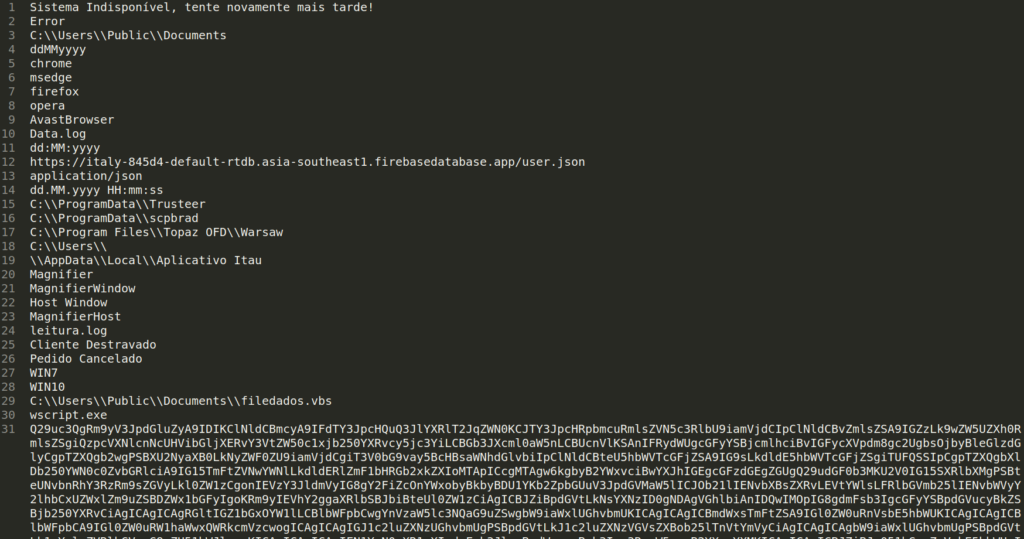
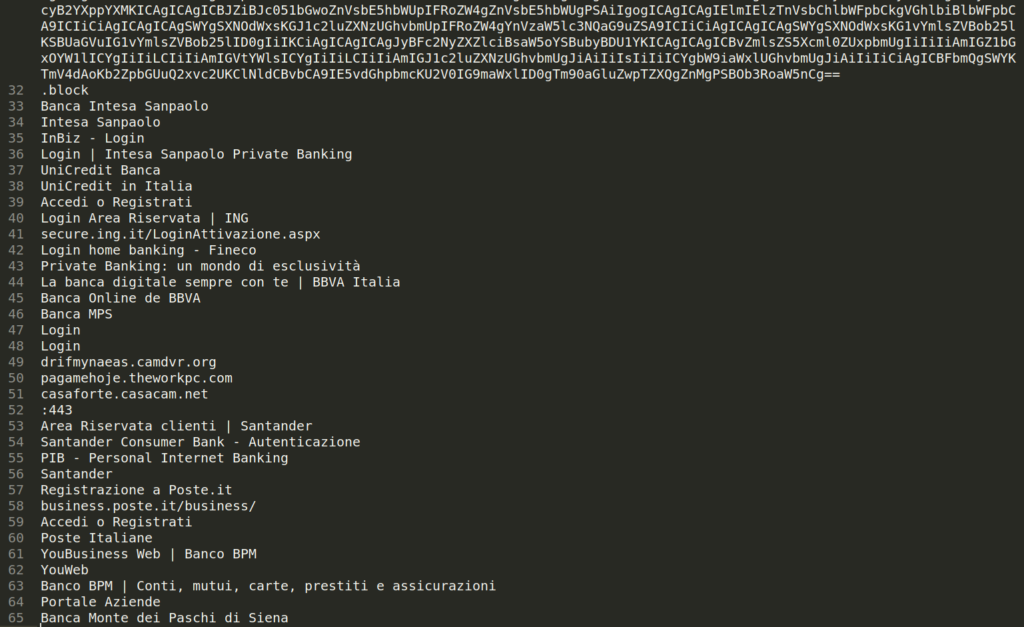
As highlighted by other analysts on X, this is BlotchyQuasar, a banking trojan developed from the code of Quasar RAT.
Indicators of Compromise
In order to make public the details of the analyzed sample, the following indicators have been derived and shared with accredited organizations through the IoC Flow of CERT-AGID.
Link: Download IoC
Source: Original Post