
QakBot, also known as QBot, QuackBot, or Pinkslipbot, is a banking trojan malware that has existed for over a decade. In recent years, QakBot has become one of the leading banking trojans around the globe. Its main purpose is to steal banking credentials (e.g., logins, passwords, etc.)
Generally, QBot infects its victims by initial infection vectors of spam emails. This kind of email contains Microsoft Office documents (Excel) or sometimes with password-protected archives format attachments.
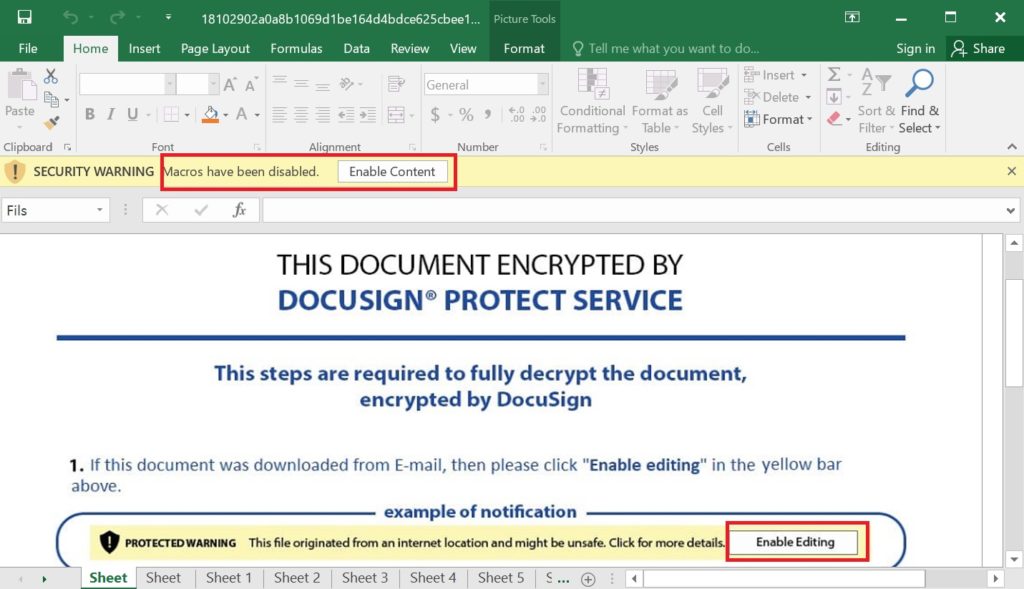
Usually, the document contains macros, and the victims are tricked to enable the content to perform the action. (e.g., an invoice or shipping attachments).
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
The initial vectors may vary depending on their targets and we all know that the threat actors perform basic reconnaissance methodologies to decide their infection vector.
QBot Infection Chain:
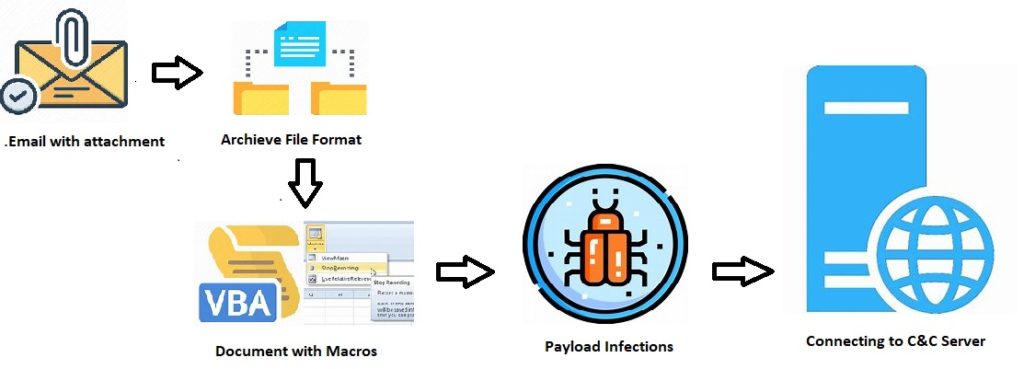
Distribution Techniques :
In this article, we will discuss two different recent distribution technologies.
Technique 1: Distributed via XLSB
XLSB is an Excel Binary Workbook file. They store information in binary format instead of XML like with most other Excel files (like XLSX). They can be read from and written to much faster, making them extremely useful for very large spreadsheets. Also, the file sizes are smaller in XLSB, when compared with XLSX.
Sample:
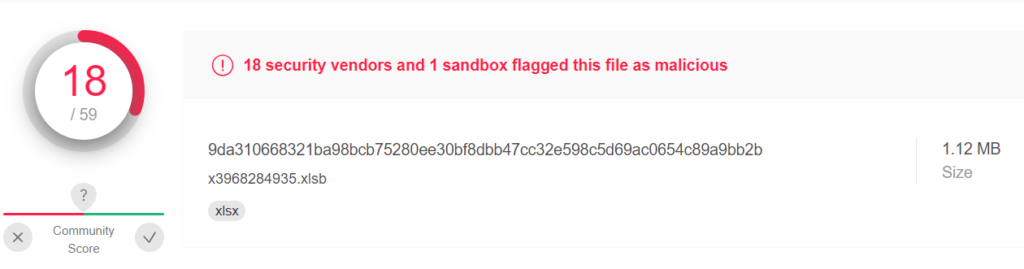
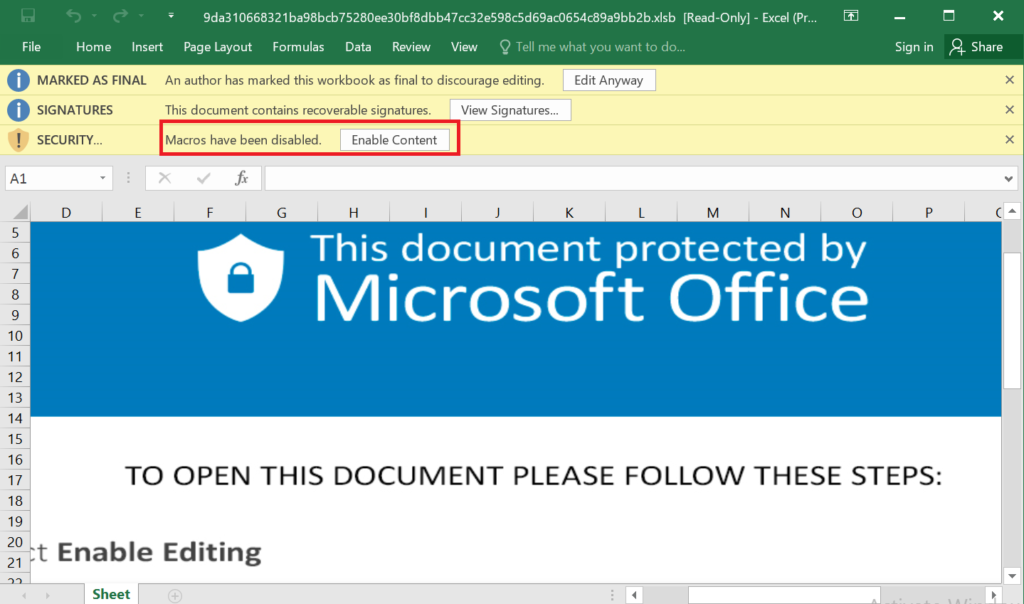
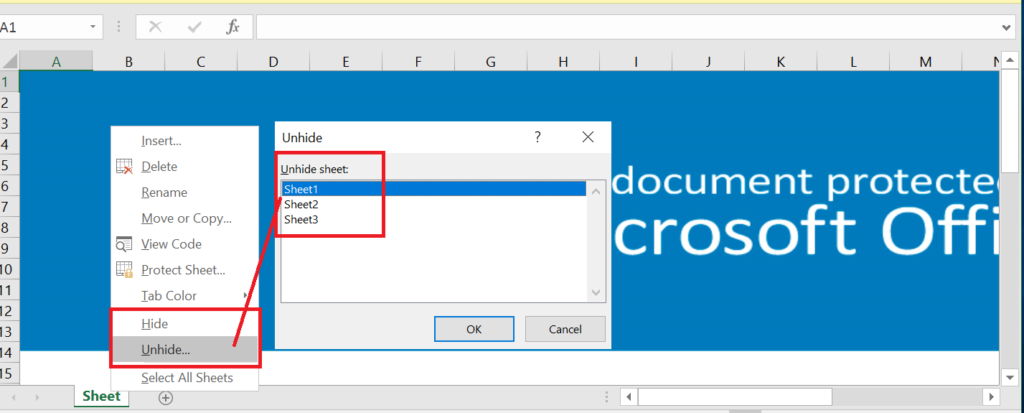
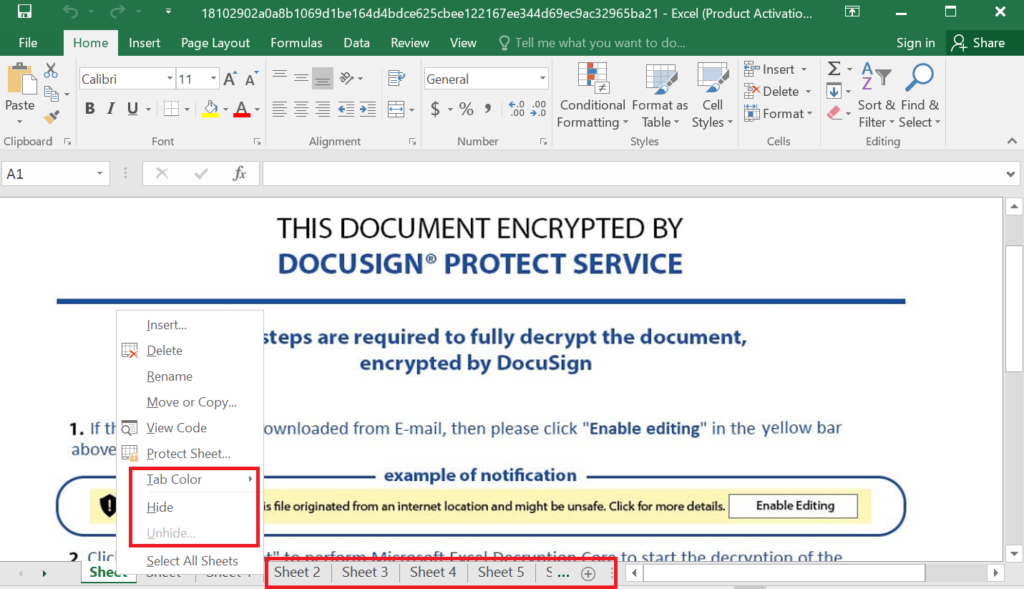
Here, the Sheets are in hidden mode, and we need to unhide them to see the contents embedded in the Sheets. Usually, it will contain URLs, Malicious/blacklisted IPs, payload file paths, etc.
Also Read: Most Common Malware Obfuscation Techniques
Once the user enabled the content, then the payload files will execute.
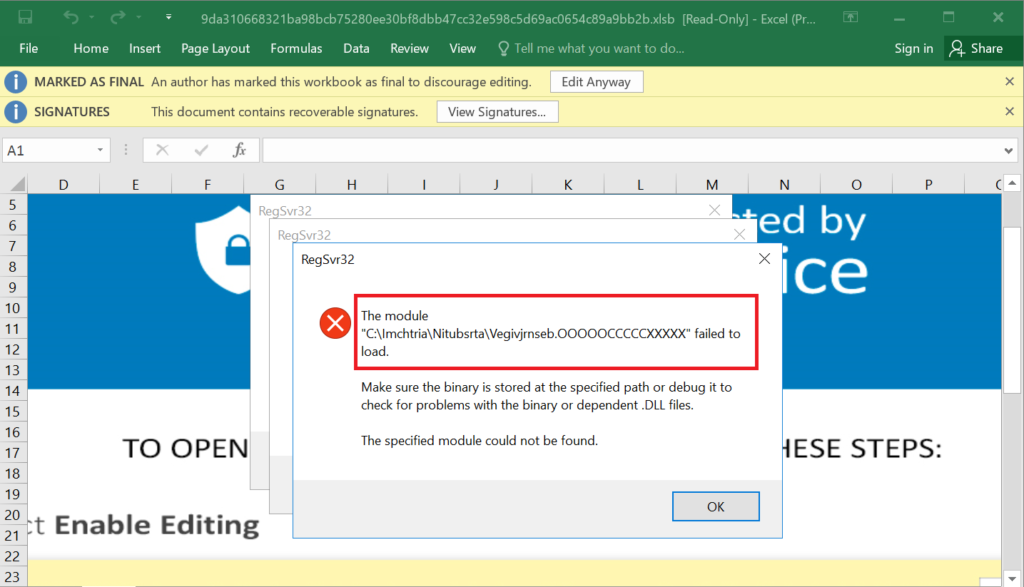
Indicators of Compromises
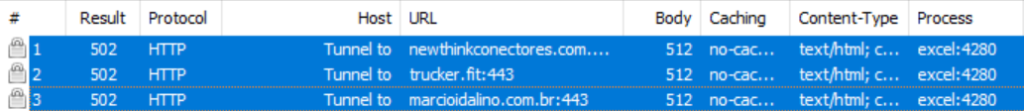
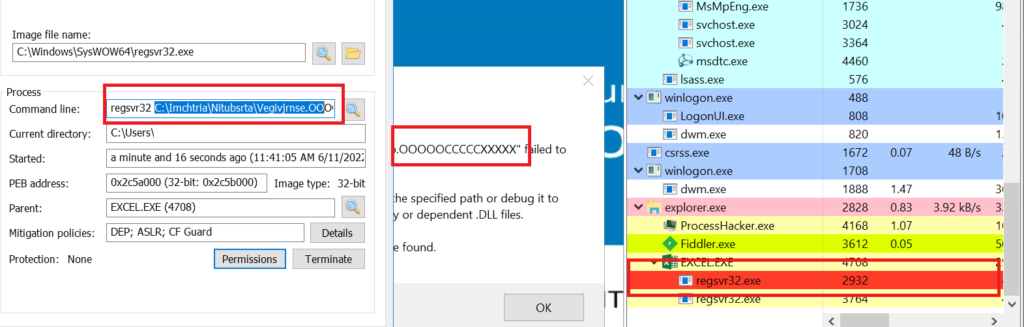
Here, the very interesting factor is that the malware author used the payload file extension as .ooooccccxxxx. Previously, they have used as .ocx or .dll
Also Read: Black Basta Ransomware operators leverage QBot for lateral movements
Technique 2: Distributed via XLTM
XLTM is a macro-enabled spreadsheet template file. With this file, we can store one or more macros, it may contain settings, layout information, and spreadsheet data. We can save spreadsheets as .XLTM files when we looking to create multiple spreadsheets (i.e;.XLSM) with the same information and layout.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Sample:
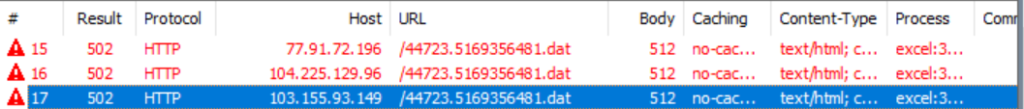
Once the user enabled the content, then the payload files will execute.
Indicators of Compromises
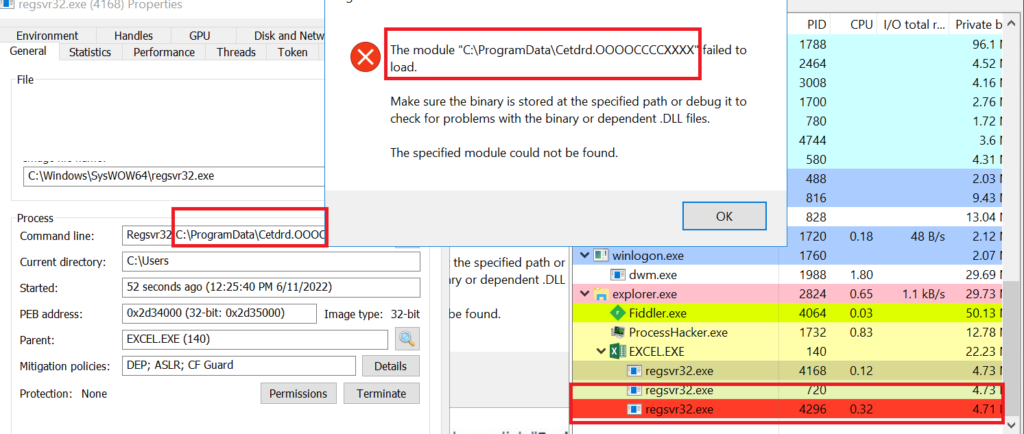
Once infected, the following actions are performed:
- Collecting information about the compromised host.
- Creating scheduled tasks (privilege escalation and persistence).
- Credentials harvesting.
- Credential dumping (.exe access).
- Password stealing (from browser history and cookies).
- Targeting web banking links (web injects).
- Password brute-forcing.
- Registry manipulation (persistence).
- Replicating its copies.
- Process injection to conceal the malicious action.
Also Read: Latest Cyber Security News – Hacker News !
MITRE ATT&CK Tactics & Techniques used by QBot:
| ID | Tactic | Technique |
| TA0001 | Initial Access | T1566.001 – Spearphishing Attachment T1566.002 – Spearphishing Link |
| TA0002 | Execution | T1027 – Obfuscated Files or Information T1059.005 – Visual Basic T1204.002 – Malicious File |
| TA0003 | Persistence | T1053.005 – Scheduled Task T1547.001 – Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | T1053.005 – Scheduled Task |
| TA0005 | Defense Evasion | T1027.002 – Software Packing T1055 – Process Injection T1055.012 – Process Hollowing T1497.001 – System Checks |
| TA0006 | Credential Access | T1003 – OS Credential Dumping T1110.001 – Password Guessing T1555.003 – Credentials from Web Browsers |
| TA0007 | Discovery | T1016 – System Network Configuration Discovery |
| TA0011 | C&C Server | T1071.001 – Web Protocols T1090 – Proxy T1090.002 – External Proxy |
Detection & Response:
Qradar:
SELECT UTF8(payload), "Process CommandLine", "ParentCommandLine" from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("ParentImage" ilike '%excel.exe') and "Image" ilike '%regsvr32.exe' and ("Process CommandLine" ilike '%.OOOCCCXXX%' or "Process CommandLine" ilike '%.OOOOOCCCCCXXXXX%' or "Process CommandLine" ilike '%.dddlllxxx%')Splunk Alert:[Regsvr32 Anomaly] alert.severity = 3 description = Detects various anomalies in relation to regsvr32.exe (Rule ID: yasuasuaudasud9393) cron_schedule = 0 * * * * disabled = 1 is_scheduled = 1 is_visible = 1 dispatch.earliest_time = -60m@m dispatch.latest_time = now search = index=* ((ParentImage="*excel.exe") AND Image="*regsvr32.exe" AND (CommandLine="*.OOOCCCXXX*" OR CommandLine="*.OOOOOCCCCCXXXXX*" OR CommandLine="*.dddlllxxx*")) AND source=WinEventLog:* | table CommandLine,ParentCommandLine alert.suppress = 0 alert.track = 1Elastic Query:(process.parent.executable:*excel.exe AND process.executable:*regsvr32.exe AND process.command_line:(*.OOOCCCXXX* OR *.OOOOOCCCCCXXXXX* OR *.dddlllxxx*))Crowstike:((ParentBaseFileName="*excel.exe") AND ImageFileName="*regsvr32.exe" AND ((CommandLine="*.OOOCCCXXX*" OR CommandLine="*.OOOOOCCCCCXXXXX*" OR CommandLine="*.dddlllxxx*") OR (CommandHistory="*.OOOCCCXXX*" OR CommandHistory="*.OOOOOCCCCCXXXXX*" OR CommandHistory="*.dddlllxxx*"))) | table CommandLine,CommandHistoryCarbonBlack:(parent_name:*excel.exe AND process_name:*regsvr32.exe AND process_cmdline:(*.OOOCCCXXX* OR *.OOOOOCCCCCXXXXX* OR *.dddlllxxx*))Fireeye:(metaclass:`windows` pprocess:`*excel.exe` process:`*regsvr32.exe` args:[`.OOOCCCXXX`,`.OOOOOCCCCCXXXXX`,`.dddlllxxx`])Google Chronicle:principal.process.file.full_path = /.*excel.exe/ and target.process.file.full_path = /.*regsvr32.exe/ and (target.process.command_line = /.*.OOOCCCXXX.*/ or target.process.command_line = /.*.OOOOOCCCCCXXXXX.*/ or target.process.command_line = /.*.dddlllxxx.*/)GrayLog:(ParentImage.keyword:*excel.exe AND Image.keyword:*regsvr32.exe AND CommandLine.keyword:(*.OOOCCCXXX* *.OOOOOCCCCCXXXXX* *.dddlllxxx*))Logpoint:(ParentImage IN "*excel.exe" Image="*regsvr32.exe" CommandLine IN ["*.OOOCCCXXX*", "*.OOOOOCCCCCXXXXX*", "*.dddlllxxx*"])Microsoft Defender:DeviceProcessEvents | where ((InitiatingProcessFolderPath endswith @"excel.exe") and FolderPath endswith @"regsvr32.exe" and (ProcessCommandLine contains ".OOOCCCXXX" or ProcessCommandLine contains ".OOOOOCCCCCXXXXX" or ProcessCommandLine contains ".dddlllxxx"))RSA Netwitness:((ParentImage contains 'excel.exe') && (Image contains 'regsvr32.exe') && (CommandLine contains '.OOOCCCXXX', '.OOOOOCCCCCXXXXX', '.dddlllxxx'))Arcsight: (sourceProcessName CONTAINS "*excel.exe" AND ((destinationProcessName CONTAINS "*regsvr32.exe" OR sourceProcessName CONTAINS "*regsvr32.exe" OR deviceProcessName CONTAINS "*regsvr32.exe")) AND ((deviceCustomString1 CONTAINS "*.OOOCCCXXX*" OR deviceCustomString1 CONTAINS "*.OOOOOCCCCCXXXXX*" OR deviceCustomString1 CONTAINS "*.dddlllxxx*" OR destinationServiceName CONTAINS "*.OOOCCCXXX*" OR destinationServiceName CONTAINS "*.OOOOOCCCCCXXXXX*" OR destinationServiceName CONTAINS "*.dddlllxxx*"))) Microsoft Sentinel:SecurityEvent | where EventID == 4688 | where ((ParentProcessName endswith @'excel.exe') and NewProcessName endswith @'regsvr32.exe' and (CommandLine contains '.OOOCCCXXX' or CommandLine contains '.OOOOOCCCCCXXXXX' or CommandLine contains '.dddlllxxx'))Windows Powershell:Get-WinEvent | where {(($_.message -match "ParentImage.*.*excel.exe") -and $_.message -match "Image.*.*regsvr32.exe" -and ($_.message -match "CommandLine.*.*.OOOCCCXXX.*" -or $_.message -match "CommandLine.*.*.OOOOOCCCCCXXXXX.*" -or $_.message -match "CommandLine.*.*.dddlllxxx.*")) } | select TimeCreated,Id,RecordId,ProcessId,MachineName,MessageAws Opensearch:(process.parent.executable:*excel.exe AND process.executable:*regsvr32.exe AND process.command_line:(*.OOOCCCXXX* OR *.OOOOOCCCCCXXXXX* OR *.dddlllxxx*))Humio:winlog.event_data.ParentImage="*excel.exe" winlog.event_data.Image="*regsvr32.exe" winlog.event_data.CommandLine="*.OOOCCCXXX*" or winlog.event_data.CommandLine="*.OOOOOCCCCCXXXXX*" or winlog.event_data.CommandLine="*.dddlllxxx*"SumoLogic:(_sourceCategory=*windows* AND (ParentImage = "*excel.exe") AND Image="*regsvr32.exe" AND (CommandLine = "*.OOOCCCXXX*" OR CommandLine = "*.OOOOOCCCCCXXXXX*" OR CommandLine = "*.dddlllxxx*"))
Source: https://www.socinvestigation.com/qbot-returns-returns-with-new-ttps-detection-response/