Threat Actor: Unknown | Unknown
Victim: Organizations using Pulse Connect Secure VPN | Pulse Connect Secure VPN
Price: Not specified
Exfiltrated Data Type: Not specified
Additional Information:
- The threat actor claims to have a Pulse Connect Secure VPN Remote Code Execution (RCE) 0-day exploit available for purchase.
- The exploit has been tested on 2,685 IP addresses, with 2,102 of them found to be vulnerable.
- Payments for the exploit are accepted in Monero (XMR) and Bitcoin (BTC).
- This vulnerability poses a potential risk to organizations relying on Pulse Connect Secure VPN for secure remote access.
- Organizations are advised to review their security posture and apply any available patches or mitigations promptly.
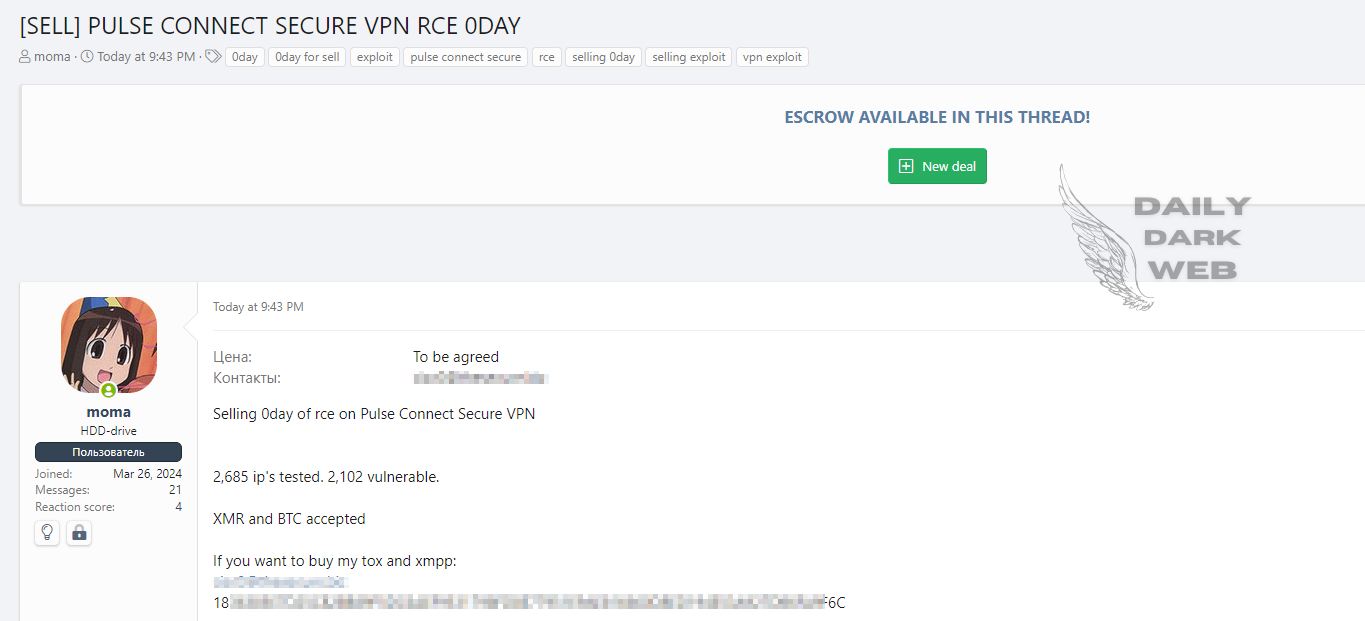
A threat actor claims to have a Pulse Connect Secure VPN Remote Code Execution (RCE) 0-day exploit available for purchase. According to the announcement, the exploit has been tested on 2,685 IP addresses, with 2,102 of them found to be vulnerable. This significant vulnerability poses a potential risk to numerous organizations relying on Pulse Connect Secure VPN for secure remote access.
The threat actor is reportedly accepting payments in Monero (XMR) and Bitcoin (BTC) for the exploit. This development highlights the ongoing risks associated with zero-day vulnerabilities and the importance of maintaining up-to-date security measures to protect against such threats. Organizations using Pulse Connect Secure VPN are advised to review their security posture and apply any available patches or mitigations promptly.
Original Source: https://dailydarkweb.net/pulse-connect-secure-vpn-rce-0-day-allegedly-for-sale/