Summary: A significant security vulnerability known as ‘PKfail’ has been identified, affecting approximately nine percent of firmware images that utilize non-production cryptographic keys, making Secure Boot devices susceptible to UEFI bootkit malware attacks. Discovered by Binarly, this issue involves test Secure Boot master keys that were improperly used by various computer manufacturers, leaving numerous devices at risk.
Threat Actor: Various threat actors | PKfail
Victim: Multiple manufacturers and users | affected manufacturers
Key Point :
- Approximately 791 out of 10,095 firmware submissions were found vulnerable due to the use of non-production keys.
- The flaw affects a wide range of devices, including medical devices, gaming consoles, and even voting machines.
- Major manufacturers like Dell, HP, and Intel have begun releasing patches to address the vulnerability.
- Users of unsupported devices are advised to limit physical access and isolate them from critical network segments.

Roughly nine percent of tested firmware images use non-production cryptographic keys that are publicly known or leaked in data breaches, leaving many Secure Boot devices vulnerable to UEFI bootkit malware attacks.
Known as ‘PKfail,’ and now tracked as CVE-2024-8105, the supply chain attack is caused by test Secure Boot master key (Platform Key “PK”), which computer vendors were supposed to replace with their own securely generated keys.
Even though these keys were marked as “DO NOT TRUST,” they were still used by numerous computer manufacturers, including Acer, Dell, Fujitsu, Gigabyte, HP, Intel, Lenovo, Phoenix, and Supermicro.
The issue was discovered by Binarly in late July 2024, which warned about the use of untrusted test keys, many already leaked on GitHub and other locations, on over eight hundred consumer and enterprise device models.
PKfail could allow threat actors to bypass Secure Boot protections and plant undetectable UEFI malware on vulnerable systems, leaving users no way to defend or even discover the compromise.
PKfail impact and response
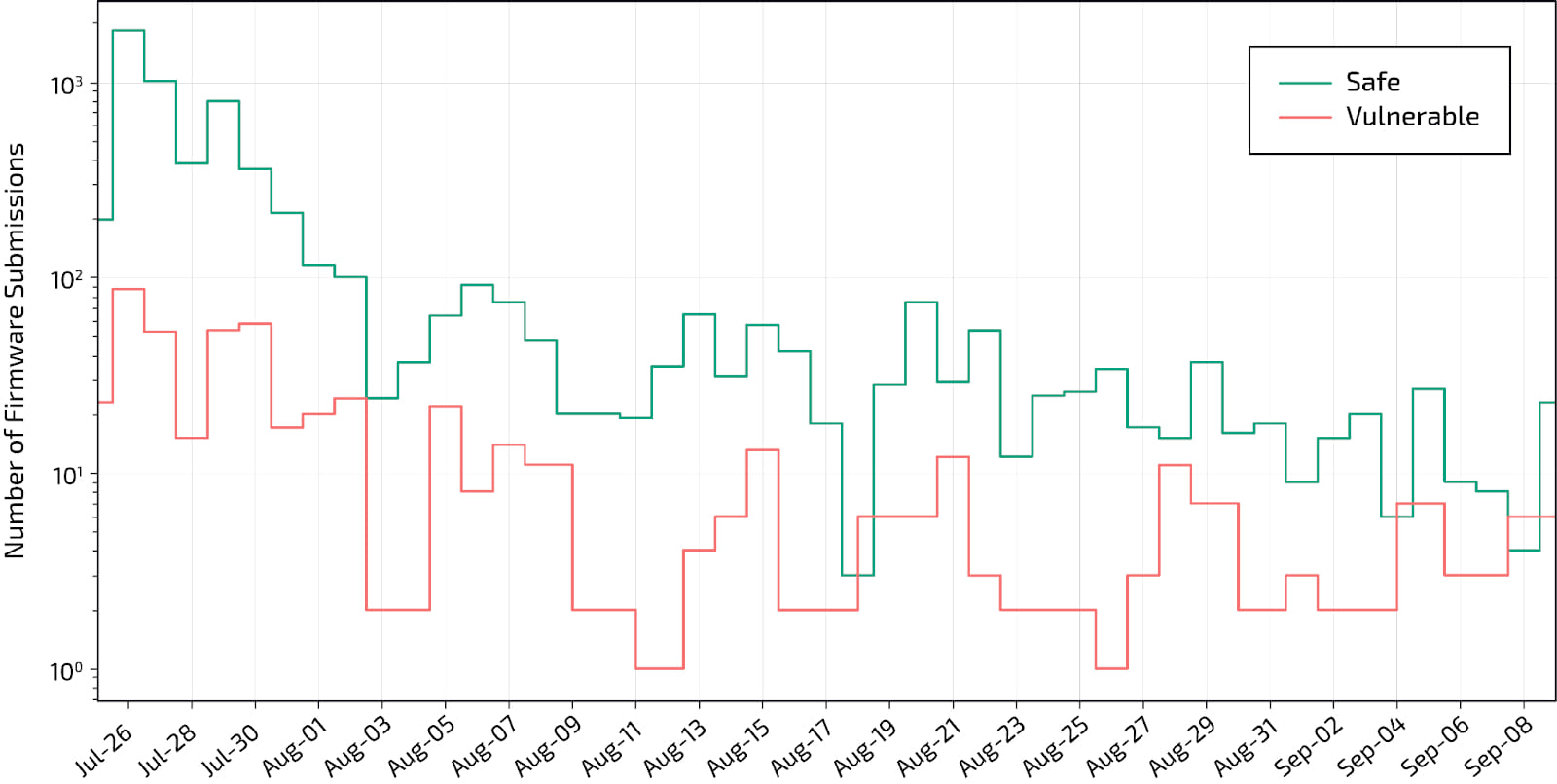
As part of their research, Binarly released a “PKfail scanner,” which vendors can use to upload their firmware images to see if they’re using a test key.
Since its release, the scanner has found 791 vulnerable firmware submissions out of 10,095, according to the latest metrics.
“Based on our data, we found PKfail and non-production keys on medical devices, desktops, laptops, gaming consoles, enterprise servers, ATMs, POS terminals, and some weird places like voting machines.” reads the new report by Binarly.
The majority of the vulnerable submissions are keys from AMI (American Megatrends Inc.), followed by Insyde (61), Phoenix (4), and one submission from Supermicro.
Source: Binarly
For the Insyde keys, which were generated in 2011, Binarly says that the firmware image submissions reveal they’re still used in modern devices. Previously, it was assumed that they were only to be found in legacy systems.
The community has also confirmed that PKfail impacts specialized devices from Hardkernel, Beelink, and Minisforum, so the flaw’s impact is broader than first estimated.
Binarly comments that vendor response to PKfail has generally been proactive and swift, though not everyone quickly published advisories about the security risk. Bulletins on PKfail are currently available by Dell, Fujitsu, Supermicro, Gigabyte, Intel, and Phoenix.
Several vendors have already released patches or firmware updates to remove vulnerable Platform Keys or replace them with production-ready cryptographic materials, and users can get those by updating their BIOS.
If your device is no longer supported and is unlikely to receive security updates for PKfail, it is recommended that physical access to it be limited and that it be isolated from more critical parts of the network.