Short Summary
Unit 42 researchers reported a surge in phishing campaigns in 2024 that utilize HTTP response header refresh techniques. These campaigns, primarily targeting the financial sector and government domains, employ malicious URLs that automatically redirect users without interaction. The attackers leverage personalized approaches to enhance deception, making it challenging to identify malicious links. Palo Alto Networks offers protection through Advanced URL Filtering to combat these threats.
Key Points
- Large-scale phishing campaigns observed in 2024, averaging 2,000 malicious URLs daily.
- Attacks use HTTP response header refresh to redirect users automatically.
- Phishing emails often spoof legitimate webmail login pages and include recipients’ email addresses.
- Targeted sectors include financial services, government, and educational institutions.
- Attackers use legitimate or compromised domains to conceal malicious URLs.
- Palo Alto Networks’ Advanced URL Filtering helps identify and mitigate these phishing threats.
MITRE ATT&CK TTPs – created by AI
- Phishing (T1566)
- Attackers send emails with malicious URLs that redirect users to phishing pages.
- Credential Dumping (T1003)
- Phishing pages mimic legitimate login forms to capture user credentials.
- Exploitation of Vulnerability (T1203)
- Using HTTP response header refresh to exploit browser behavior for phishing.
Executive Summary
Unit 42 researchers observed many large-scale phishing campaigns in 2024 that used a refresh entry in the HTTP response header. From May-July we detected around 2,000 malicious URLs daily that were associated with campaigns of this type.
Unlike other phishing webpage distribution behavior through HTML content, these attacks use the response header sent by a server, which occurs before the processing of the HTML content. Malicious links direct the browser to automatically refresh or reload a webpage immediately, without requiring user interaction.
Attackers predominantly distribute the malicious URLs in the phishing campaigns via emails. These emails consistently include recipients’ email addresses and display spoofed webmail login pages based on the recipients’ email domain pre-filled with the users’ information. They largely target people in the global financial sector, well-known internet portals and government domains.
Since the original and landing URLs are often found under legitimate or compromised domains, it is difficult to spot malicious indicators within a URL string. Furthermore, attackers use personalized approaches that increase the likelihood that they will deceive their victim.
Palo Alto Networks customers are better protected from the threats discussed above through Advanced URL Filtering (AURL). Besides identifying phishing URLs in the described scenario, AURL extracts patterns from these suspicious URLs and could discover additional phishing websites.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
How the Header Refresh Technique Works
Phishing attackers commonly employ a variety of readily available tools and mechanisms to obscure their malicious intent and deceive their victims. We recently observed attackers using header refresh techniques to embed their phishing links and craft convincing email subjects to deceive customers.
These malicious links, which have the targeted user’s email address embedded in the refresh field of the HTTP response header, direct the browser to automatically refresh or reload a webpage immediately. They do so without requiring user interaction.
By carefully mimicking legitimate domains and redirecting victims to official sites, attackers can effectively mask their true objectives and increase the likelihood of successful credential theft. These tactics highlight the sophisticated strategies attackers use to avoid detection and exploit unsuspecting targets.
To see how the header refresh technique works, we will describe an example. In one phishing attempt we observed, the refresh field of the response header is:

Below, Figure 1 shows the refresh entry in the HTTP response headers in response to the original URL, as seen using DevTools in Google Chrome.
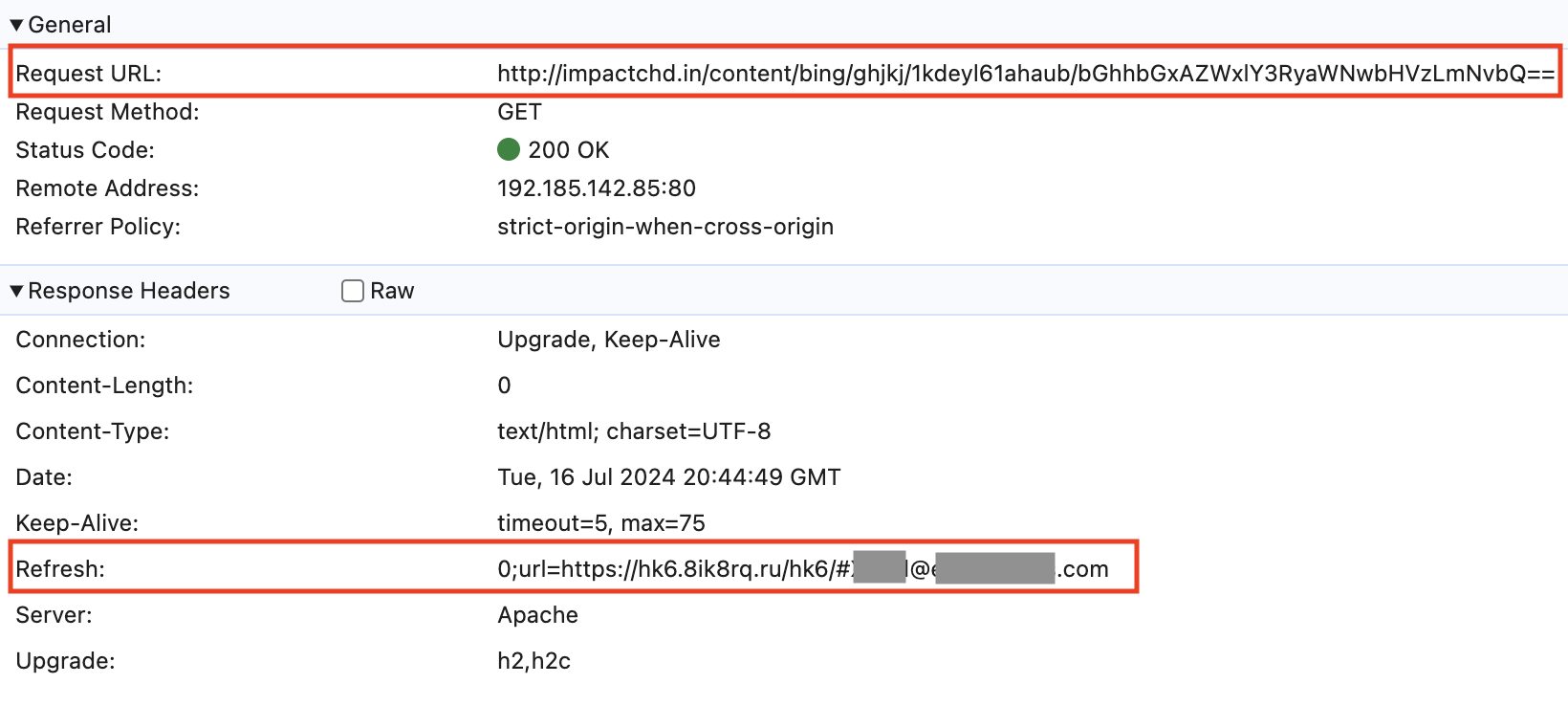
The original and landing URLs are often found under legitimate or compromised domains and hosts, a technique that’s often effective in concealing malicious URL strings. Additionally, attackers frequently use legitimate domains that offer URL shortening, tracking or campaign marketing services.
Many attackers also employ deep linking to dynamically generate content that appears tailored to the individual target. By using parameters in the URL, they pre-fill sections of a form, enhancing the credibility of the phishing attempt.
This personalized approach increases the likelihood that the attacker will deceive the victim. Attackers have exploited this mechanism because it enables them to load phishing content with minimum effort while concealing the malicious content.
Example of Header Refresh Phishing Attacks
To trick their targets and steal their credentials, malicious links in these attacks consistently include an organization’s email address and display an email login page pre-filled with victims’ information.
Figure 2 returns to the example above, showing a related phishing page found on July 14, 2024.
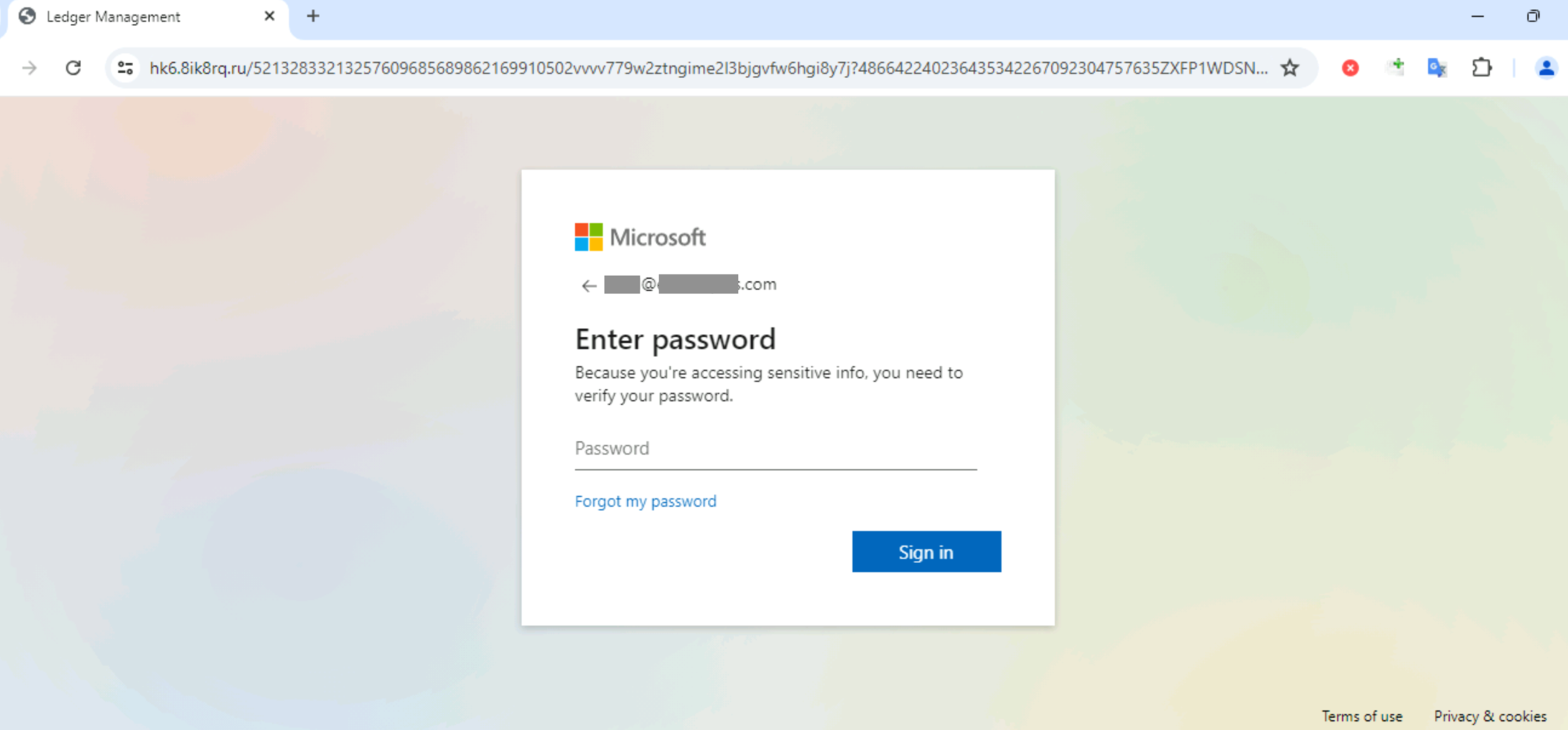
Table 1 below shows the original URL and the final URL from the phishing page in Figure 2. When clicking the original URL from the phishing email, the server hosting that original URL used a refresh entry in the HTTP response headers, as described in the previous section. This is used to redirect traffic to the final URL under the domain hk6.8ik8rq[.]ru.
This URL is the final address for the phishing page. In many cases, we find a landing URL between the original address and the final one in this chain.
| Date | Original URL | Final URL (Header Link) |
| July 14, 2024 | hxxp[:]//impactchd[.]in/content/bing/ghjkj/1kdeyl61ahaub/[Base64 string for recipient’s email address] | hxxps[:]//hk6.8ik8rq[.]ru/hk6/#[recipient’s email address] |
Table 1. Example of a phishing URL chain.
Phishing Campaign Example
From June 20-21, 2024, we observed large-scale phishing campaigns through emails predominantly targeting large corporations in Korea. We also saw campaigns targeting government agencies and schools in the U.S. One particular campaign was notable for its use of emails originating from the same source IP address at 195.19.93[.]5 and the same spoofed sender addresses of 2127394249@businessimageprint[.]com or 2127394249@docusign[.]com. Attackers varied the recipients across multiple domains ending with [.]gov, [.]edu and [.]com.
The most common email subject was Complete with DocuSign: ACH/EFT FORM ***. URLs embedded within these emails commonly contained a subpath of sf_rand_string_lowercase6. Figure 3 shows the campaign trending and Figure 4 shows the percentages of targeted industries.
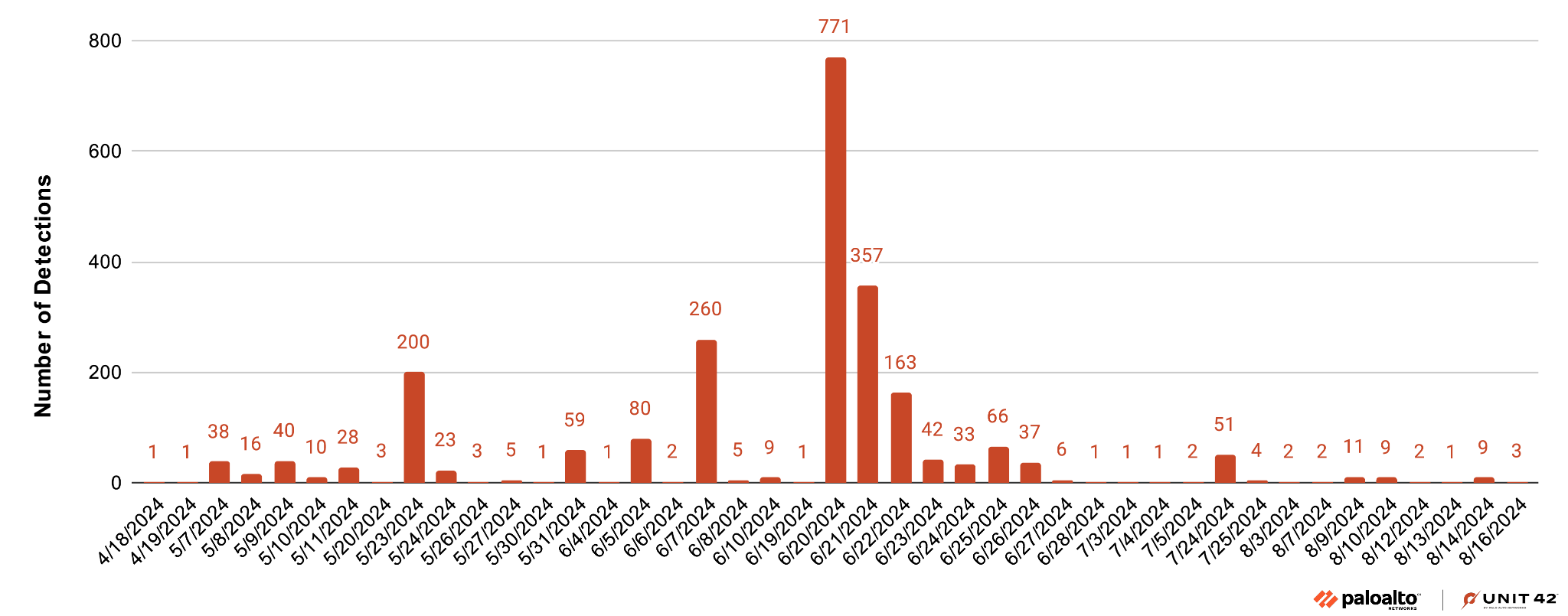
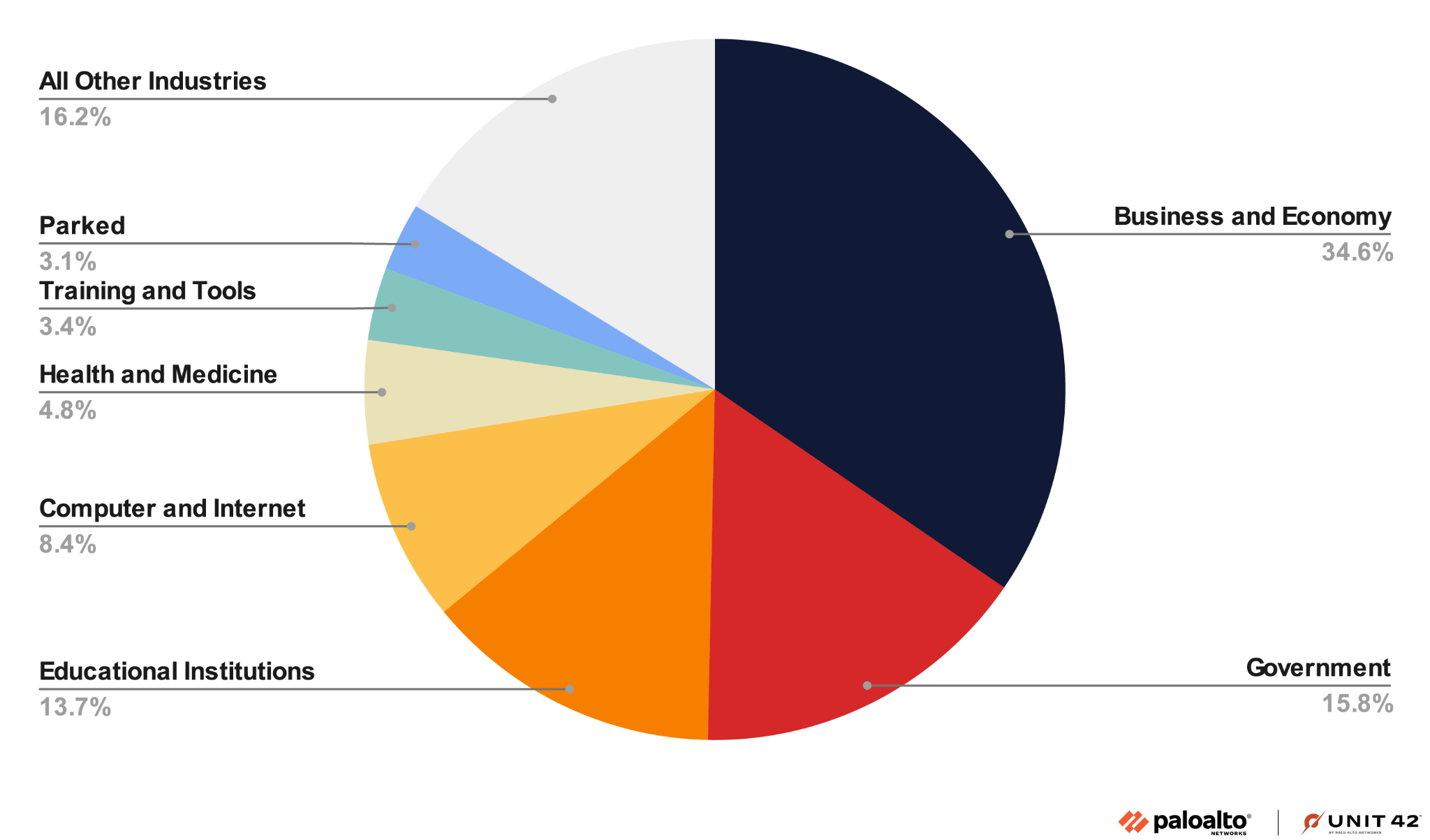
Over 34% of the attacks targeted people in the business-and-economy sector. Nearly 30% of the targets were from governments and educational institutions.
Attackers delivered the malicious links through header refresh URLs containing targeted recipients email addresses. Consistent with the email recipient’s domain, the final page would be automatically loaded with malicious link content when the victim clicks the link in the email body.
Upon landing on the phishing webpage, victims were presented with a login page requesting their credentials. An example of one of the campaigns is detailed on LinkedIn in our Unit 42 Timely Threat Intelligence post.
Large Phishing Campaigns Statistics
Phishing attacks target a large number of users in various organizations, encompassing numerous large-scale campaigns. Table 2 shows the top domains for the initial URLs used by large campaigns in the past three months, and Figure 5 shows the frequency of those top domains.
| URL Domain | URL Domain Category | Number of Detections | Most Frequent Date | Top Targeted Industry |
| onelink[.]me | Computer-and-internet-info | 5,537 | May 10, 2024 | Financial-services |
| go[.]link | Business-and-economy | 5,374 | May 6, 2024 | News |
| speedpython[.]com | Malware | 3,027 | May 14, 2024 | Government |
| club-os[.]com | Business-and-economy | 2,384 | April 12, 2024 | Business-and-economy (mostly in Japan) |
| guide-orientation[.]tn | Educational-institutions | 1,888 | July 2, 2024 | Business-and-economy |
Table 2. Examples of large campaigns from April 12-July 7, 2024.
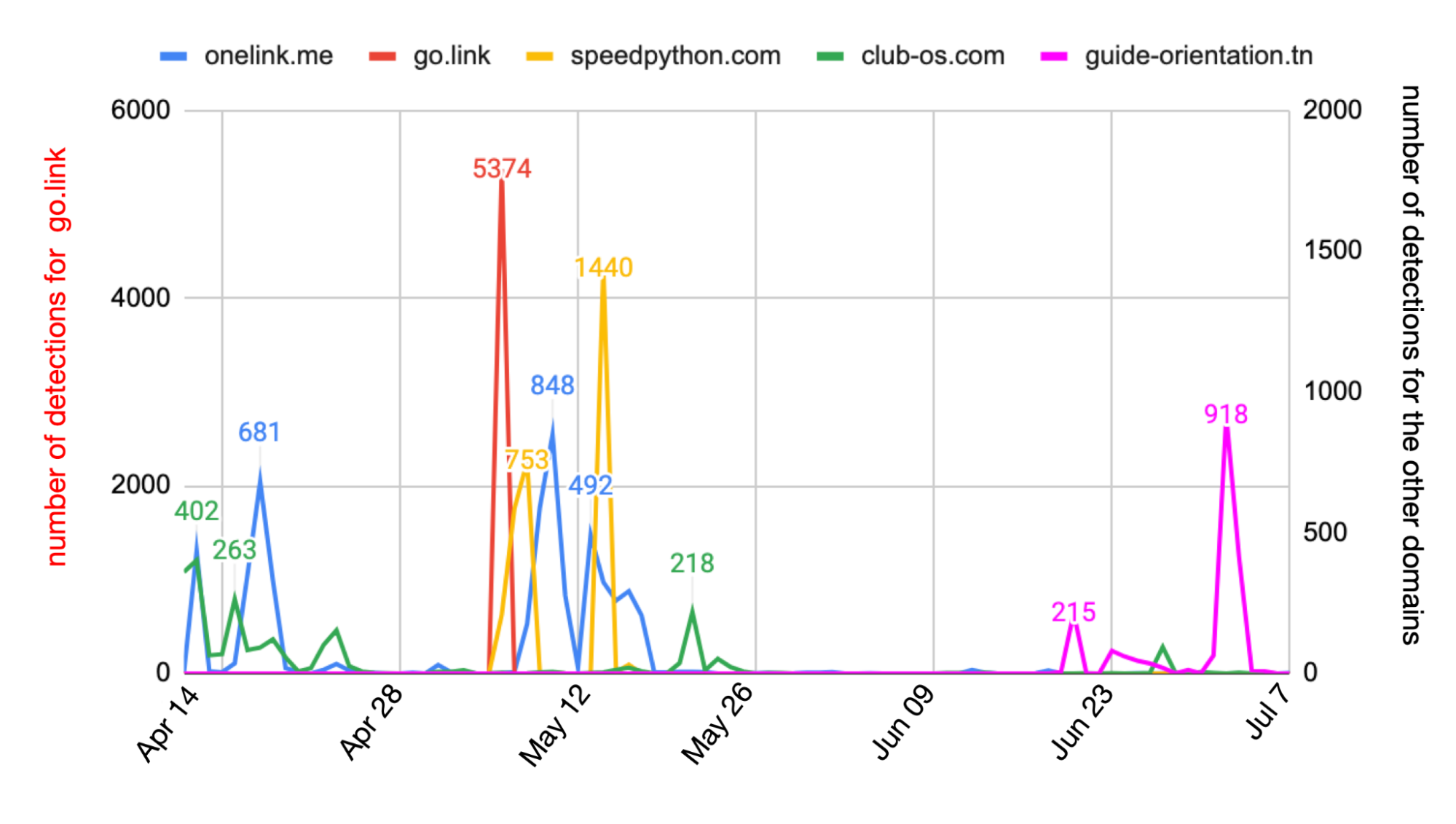
Different domains appeared during various time periods. Some campaigns, particularly those using malicious URLs under the domain onelink[.]me, have continued for a prolonged period. Figure 5 above shows the campaign had a peak on May 10, 2024, and lasted for about one month. The campaign targeted over 3,000 victims across more than 500 organizations.
Meanwhile, campaigns associated with the go[.]link domain experienced a sudden surge at the beginning of May, with over 5,000 malicious URLs detected. Domain club-os[.]com peaked on April 12, 2024, but persisted from late April to the present. In late June, we noticed a new campaign under guide-orientation[.]tn, which occurred most on July 2, 2024.
Affected Users
Phishing attacks aim to steal email login credentials from people at various organizations. Figure 6 shows the distribution of industries from our total detections in this wave of attacks.
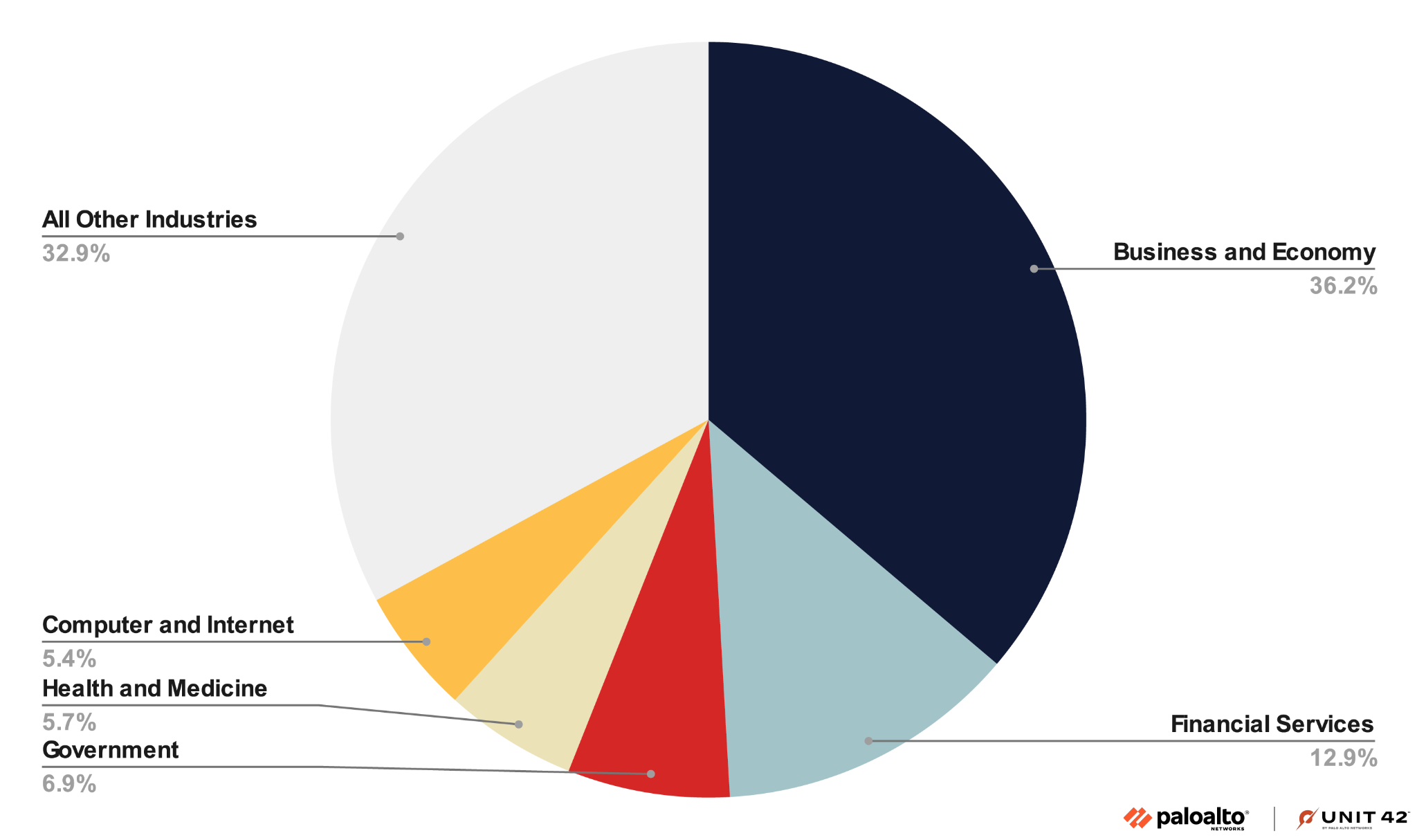
Over 36% of the attacks largely targeted people in the global business-and-economy sector. The second-largest sector is financial services, including global banks and financial service companies. We also observed that phishing emails were sent to users of well known internet portals and government domains.
Since many companies use Microsoft/Outlook for their email service, the phishing pages frequently imitate the webmail login page, such as the Outlook webmail login portal shown below in Figure 7.

As shown in Table 3, the original URL of the above example was under domain cices[.]org but landed on a different domain dominicanmidia[.]com. When the victim clicked this URL, it reloaded a webpage under sirius-maritime[.]com and showed a fake Outlook webmail login page prefilled with the user’s email address (associated with a technology company). The attack was designed to trick the user into entering their password on the fake page, exposing their credentials to the attacker.
The page allowed the victim to enter their password three times at most, capturing these attempts, then redirecting to the official site office[.]com. We also saw similar attacks targeting other recipients associated with different companies.
| Date | Original URL | Landing URL | Final URL (Header Link) |
| May 21, 2024 | hxxps[:]//www[.]cices[.]org/?wptouch_switch=desktop&redirect=HtTPs[:]//dominicanmidia[.]com//zres/rezs/obld//[base64 string for recipient’s email address] | hxxps[:]//dominicanmidia[.]com//zres/rezs/obld//[base64 string for recipient’s email address] | hxxps[:]//sirius-maritime[.]com/0utl0ok/?email=[recipient’s email address] |
| May 5, 2024 | hxxps[:]//www[.]cices[.]org/?wptouch_switch=desktop&redirect=HtTPs[:]//dominicanmidia[.]com//zres/rezs/dnne//[base64 string for recipient’s email address] | hxxps[:]//dominicanmidia[.]com//zres/rezs/dnne//[base64 string for recipient’s email address] | hxxps[:]//sirius-maritime[.]com/0utl0ok/?email=[recipient’s email address] |
| May 21, 2024 | hxxps[:]//www[.]cices[.]org/?wptouch_switch=desktop&redirect=HtTPs[:]//dominicanmidia[.]com//zres/rezs/crej//[base64 string for recipient’s email address] | hxxps[:]//dominicanmidia[.]com//zres/rezs/crej//zres/rezs/crej//[base64 string for recipient’s email address] | hxxps[:]//sirius-maritime[.]com/0utl0ok/?email=[recipient’s email address] |
Table 3. Similar phishing attacks on different recipients.
Conclusion
In the additional resources section below, we’ve listed some examples of phishing webpage distribution behavior through HTML content, specifically through the injection of a malicious URL to the meta field of the HTML file. However, as of August 2024, no literature specifically addresses attacks using a refresh entry in the response header sent by a server that occurs before the server processes the HTML content of the response body.
This article documents the frequent use of HTTP refresh fields in HTTP response headers in phishing attacks.
In our research, we found no legitimate websites exhibiting this behavior. Although the refresh header can be useful in specific situations like dynamically updating websites, we more commonly see other methods such as JavaScript-based techniques or server-side push technologies like WebSockets.
Ultimately, organizations should be more aware of the potential for malicious use of HTTP refresh headers.
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected from the threats discussed above through Advanced URL Filtering. To identify phishing URLs in the described scenario, we analyzed the response headers of websites.
URLs containing an email address injected into the refresh field were typically flagged as suspicious. We extracted patterns from these suspicious URLs and discovered additional phishing websites.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
We have compiled a CSV file containing 58 examples of sanitized URL chains from May 1-July 2, 2024. It is available as a file in this GitHub repository.
Additional Resources
Source: Original Post