Executive summary
- Following the 2023 holiday season, Akamai researchers uncovered a significant amount of highly likely malicious activity and domains purporting to be associated with the United States Postal Service (USPS).
- Akamai researchers compared five months of DNS traffic to the legitimate domain, usps[.]com, with DNS traffic to illegitimate combosquatted domain names.
- Through this analysis, we discovered the number of DNS queries to the collected malicious domains is generally about equal to the number of queries to usps[.]com, and even exceeds it during peak times.
Introduction
As one of the major package delivery institutions in the United States, the USPS is, and has been for some time, a common target for phishing and smishing campaigns. For U.S. residents, it’s almost guaranteed that you’ll receive at least one scam attempt around the holidays: USPS even has a separate web page dedicated to warning consumers about these kinds of fraud and scams. A quick web search brings up tons of examples.
One of our team members recently received one of these attempts on their phone (Figure 1). Considering the ubiquity of these scams, that attempt prompted us to start an analysis of what we see going on at the DNS level related to the USPS website. We were able to do this by accessing anonymized global DNS query logs originating from Akamai CacheServe DNS servers.
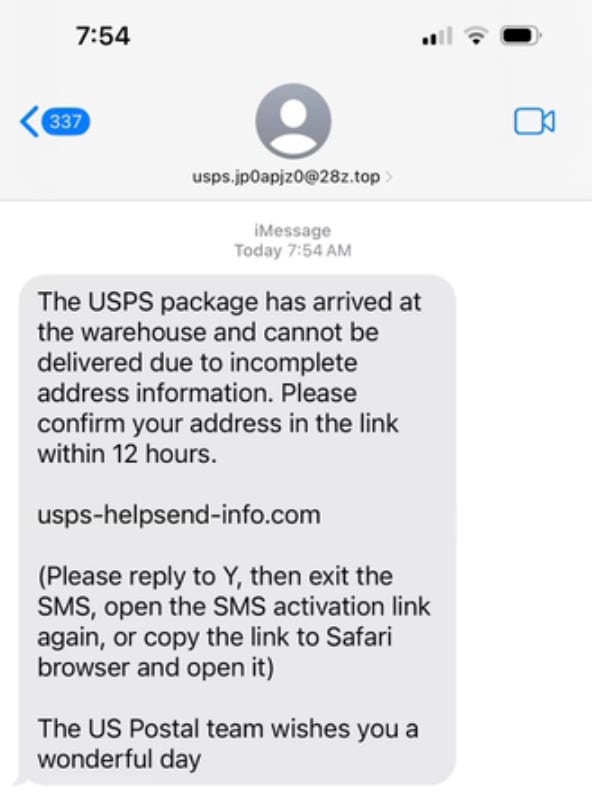
Fig. 1: USPS smishing attempt sent to team member
What we found surprised even us: The amount of traffic to the illegitimate domains was almost equal to the amount of traffic to legitimate domains on a normal day — and greatly exceeded legitimate traffic during the holidays.
In this blog post, we will explain our research process and present some of our findings from this analysis.
Creating a malicious USPS domains dataset
We began our journey by having a friendly chat with our internal SecOps team. They fetched for us a list of domains that were using the same (confirmed malicious) JavaScript file hashes as the one we saw in our team member’s smishing text message. The SecOps team also sent us a list of domain names for which the HTML was showing the same pattern as the one in the example text message.
Thanks to them we now have a list of domain names that are malicious, at the very least.
We filter this list down and keep only the domain names that contain the string ‘USPS’. This way, we are sure to keep only the domains that are targeting USPS consumers. We called that malicious data, part 1.
Then, we collected malicious data, part 2 by diving into our DNS query logs. To ensure that we are only including domains purporting to be associated with the USPS, we created very strict parameters through which to filter the data. We took five months of historic DNS query data and filtered it for:
- domain name label must start with “USPS”
- or domain name label must end with “USPS”
- or domain name label must contain “USPS-”
- or domain name label must contain “-USPS”
- and the domain must not resolve to an IP belonging to the official USPS IP ranges
This process grabbed all domain names having USPS clearly visible in the domain name while at the same time not resolving to the USPS’s official IP ranges. Anything matching these filters is at the very least suspicious because they’re mimicking a legitimate entity without resolving to it.
We did several checks to make sure we didn’t select any legitimate websites here. For example,. in the beginning, we used a filter “domain name label contains USPS” but this filter seemed too loose so we narrowed it even further.
In the end, we concatenated both malicious datasets into a single dataframe. Here are some examples of domain names, as well as a visual example of what a user would see if they landed on the page (Figure 2):
- usps-deliveryservice[.]icu
- uspshelp[.]vip
- usps-stampservice[.]com
- usps-lookup[.]com
- gh-usps[.]shop
The filters that we applied are quite strict: We aren’t including fully qualified domain names like us.ps393[.]com or usps.parceltracker-us[.]com because those involve the subdomain. For accuracy, we collected only the most obvious samples that use the combosquatting technique.
Our harsh parameters meant that we were exceedingly conservative with our analysis. Even so, we saw an extraordinary amount of malicious traffic, which makes the true impact of these impersonations astonishing. We could have definitely collected appreciably more malicious domains that impersonate the USPS, but it was critical that we avoided including false positives in this dataset.
All the statistics that follow are derived from the data sample available for this analysis. It may be a very large sample, but it’s still a sample, and its size makes all the numbers lower. This goes for both the malicious dataset and the legitimate usps[.]com dataset itself.
Analysis of the malicious domains
Top domain names
Table 1 shows the number of DNS queries that we saw for the most popular malicious domains over five months.
| Domain name | Query count* |
|---|---|
| usps-post[.]world | 169,379 |
| uspspost[.]me | 150,052 |
| usps-postoffices[.]top | 27,056 |
| stamps-usps[.]online | 24,352 |
| usps-shop[.]shop | 23,432 |
| uspspostoffice[.]top | 22,734 |
| uspspostoffices[.]top | 19,266 |
| usps-post[.]today | 18,775 |
| uspshelp[.]store | 6,048 |
| usps-pst[.]xyz | 5,800 |
Table 1: Malicious domains that saw most DNS traffic
As a result of the data filter that we applied, all these domain names display some form of combosquatting, a common technique used in phishing campaigns. In combosquatting, a familiar brand name (in this case, the USPS) is used to trigger a feeling of familiarity and legitimacy in the target victim.
Looking at the overall numbers, we see two domains got more than 100,000 hits each: usps-post[.]world and uspspost[.]me. Combined, these two are responsible for 29% of all malicious traffic inside our dataset. Keeping in mind that we’re only looking at a data sample, the traffic that some of these domains are seeing is truly mind-blowing. It’s not surprising that USPS phishing campaigns have been, and continue to be, so popular for scammers. Unfortunately, there are tons of people visiting these websites, which means they’re lucrative for the attackers running them.
Figure 3 is a bar plot showing the activity of both of the top two domains. In the chart, each bar represents a single day.
Fig. 3: Bar plot of malicious activity for the top two malicious domains
The most popular domain that we saw is usps-post[.]world, a domain which might be mistakenly interpreted as an official international branch of the USPS. Considering how lucrative well-designed malicious domains can be, we have to admit it is a well-chosen domain name. When you tack on the “failed delivery” messaging (Figure 4), and/or the holiday-focused branding (Figure 5) during the largest delivery time of the year in the United States, the success of these malicious pages makes sense.
Fig. 4: Screenshot of the usps-postoffices[.]top failed delivery message
Fig. 5: Screenshot of the holiday branding on usps-stampservice[.]com
Looking back at the blue bars in Figure 3, we see that usps-stampservice[.]com started seeing traffic on November 23, which is one day before Black Friday. It was active until the first of December and then stopped seeing traffic. We assume this is because the cybercriminals stopped sending text messages to potential victims at that time. The website was probably shut down then as we are not currently able to access it.
Now, let’s look at the other domain: uspspost[.]me (the orange bars in Figure 3). This domain seems to have targeted the Christmas period and, interestingly, December 6. If this was triggered by St. Nicholas Day, the campaign was targeting a very specific niche — St. Nicholas Day is only celebrated in a few places in the United States. This campaign might also have been targeting the trailing Cyber Monday customers.
Top TLDs
Next, let’s look at the most common top-level domains (TLDs) associated with the malicious core domains. We saw 233 different TLDs associated with malicious activity. Table 2 shows the most popular ones.
| TLD | Unique domains | Query count |
|---|---|---|
| [.]com | 4,459 | 271,278 |
| [.]top | 3,063 | 274,257 |
| [.]shop | 566 | 58,194 |
| [.]xyz | 397 | 30,870 |
| [.]org | 352 | 16,391 |
| [.]info | 257 | 7,597 |
| [.]net | 159 | 5,920 |
| [.]life | 153 | 5,616 |
| [.]vip | 105 | 8,724 |
| [.]cc | 103 | 6,430 |
Table 2: The most popular TLDs associated with the malicious core domains
The [.]com TLD is the most popular for registering new domains. We see almost 4,500 unique .com domains in our data. This is not surprising as a [.]com can give the potential victims a sense of familiarity and legitimacy globally.
The [.]top TLD seems to be the threat actor’s favorite alternative TLD. It comes in second with more than 3,000 different domain names. This generic TLD is operated by a technology company in China and is well known for being used maliciously in phishing campaigns.
Interestingly, the [.]world TLD does not appear in the table. That’s because for [.]world we counted a total of 170,126 queries (very high, nearly up there with [.]com and [.]top), but 99.5% of those were made to just usps-post[.]world (remember that usps-post[.]world was the domain name that received the most queries). We found just a few domain names under this TLD.
Top IP addresses
Next, we will look into the most common resolved IP address for the malicious dataset.
| IP address | Entity | Unique domains | Query count | Top domains (query count) |
|---|---|---|---|---|
| 155.94.151.28 | QuadraNet | 3 | 169,373 | usps-post[.]world (169,364)usps-post[.]vip (7)uspsos[.]com (2) |
| 99.83.178.7 | Amazon | 4,333 | 107,776 | appusps[.]com (208)alter-usps[.]shop (206)usps[.]solutions (192) |
| 75.2.110.227 | Amazon | 4,333 | 107,776 | appusps[.]com (208)alter-usps[.]shop (206)usps[.]solutions (192) |
| 155.94.156.254 | QuadraNet | 2 | 68,386 | uspspost[.]me (68,373)uspsposts[.]com (13) |
| 155.94.135.202 | QuadraNet | 2 | 63,593 | uspspost[.]me (63,589)uspsaps[.]top (4) |
| 99.83.179.4 | Amazon | 2,019 | 53,889 | usps-find[.]com (157)usps-mlpackage[.]com (154) |
| 75.2.78.236 | Amazon | 2,019 | 53,889 | usps-find[.]com (157)usps-mlpackage[.]com (154) |
| 107.150.7.53 | QuadraNet | 2 | 49,646 | usps-postoffices[.]top (26,938)uspspostoffice[.]top (22,798) |
| 172.86.125.227 | FranTech Solutions | 2 | 23,422 | usps-shop[.]shop (23,418)usps-shopusa[.]shop (4) |
| 104.223.16.2 | QuadraNet | 3 | 21,186 | uspspostoffice[.]top (19,180)usps-post[.]vip (2,002)uspsaps[.]top (4) |
Table 3: IP address of malicious core domains
The IPs belonging to QuadraNet have just a few domain names pointing to them, but still they are seeing high amounts of traffic.
The IPs pointing to Amazon have a large number of domain names attached, but each domain is responsible for just a small amount of queries.
The likely explanation is that we are looking at two different phishing attacks here. In one of them, the fraudsters made the decision to spread traffic across many different domain names. The other campaign spans just a few domains, and each one sees a lot of traffic.
usps.com vs. malicious domains
Now, we have a dataset that we are confident is accurate, so it’s time to compare it with the legitimate USPS traffic. Figure 6 shows the total number of queries in our dataset, for both usps.com and the malicious domains. As you can see, the numbers are almost the same. Despite the rigid filter parameters, the malicious domains receive approximately equal number of queries as usps.com itself. This is shocking.
Fig. 6: Comparison of traffic to usps.com vs. to malicious domains that are impersonating the USPS
We can also look at what happens over time. Figure 7 displays the same numbers aggregated by week.
Fig. 7: Comparison of traffic to usps.com vs. malicious domains that are impersonating the USPS from October 2023 through February 2024
Not only is the traffic relatively equivalent on a typical day, during some weeks, the malicious domains are getting more queries than usps.com itself. These peaks revolve around the Thanksgiving (Black Friday) and Christmas holidays, the highest delivery time of the year in the United States.
It seems the threat actors are well aware of these gift-giving holidays and are timing their USPS phishing campaigns accordingly. It does, of course, make sense for them to do that, as more people will be expecting parcels around those dates. The holidays are also an especially busy time for people, which means they may be more likely to make careless mistakes they might otherwise not make, such as clicking on these scam messages.
Conclusion
We have found that the USPS is under attack from text scams, especially during holiday seasons of Christmas and Thanksgiving because of the nature of gift buying in these holidays.
The total query counts of malicious domains vs. usps[.]com are almost the same, even when only counting domains including the explicit USPS acronym. Although the USPS won with 51% of the total queries for this 5-month period in this analysis, the way we filtered the data suggests that the malicious traffic significantly outweighs the legitimate traffic in the real world. We used the USPS as an example, but this combosquatting technique is used globally in phishing campaigns, and with good reason: It’s wildly successful.
We saw two different approaches from the malicious actors: They either spread traffic across many different domain names, or used only a few domains that each saw a lot of traffic. This could be for obfuscation purposes: Carriers and other hosting providers are aware of the ubiquity of these scams and are trying vigilantly to identify and remove these pages. Considering the level of attention given to eliminate these scams, their results and our observations are even more concerning.
We will continue to monitor and report on threats such as these both for our customers and the security community at large.
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português