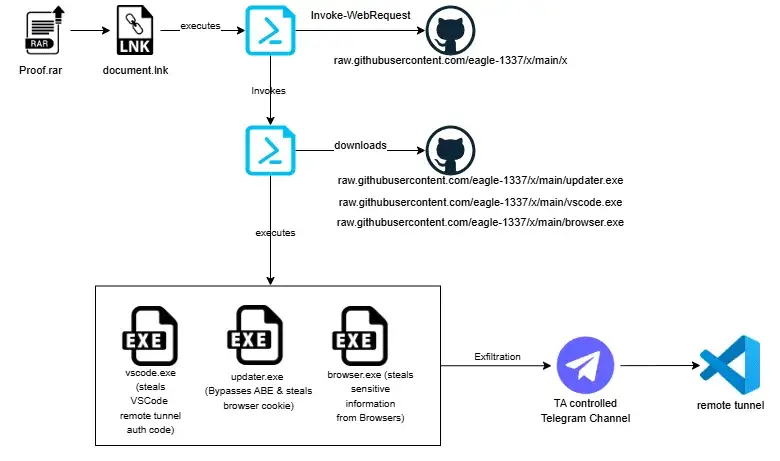
Summary: The Phantom Goblin malware campaign blends sophisticated social engineering with stealthy execution techniques to compromise systems and steal sensitive browser data. By deploying a malicious LNK file via phishing, it executes a multi-stage attack that establishes unauthorized access through Visual Studio Code tunnels. This emerging threat highlights the evolving tactics of cybercriminals and the challenges they pose to cybersecurity defenses.
Affected: General computer users and organizations with vulnerable systems
Keypoints :
- Phantom Goblin uses a RAR file with a disguised LNK file to trick users into executing malware.
- The malware executes PowerShell commands to extract sensitive data from browsers and modifies registry keys for persistence.
- Attackers utilize VSCode tunnels for remote access, making detection more difficult by blending in with normal operations.
Source: https://securityonline.info/phantom-goblin-malware-stealthy-attacks-via-vscode-tunnels/
Views: 22