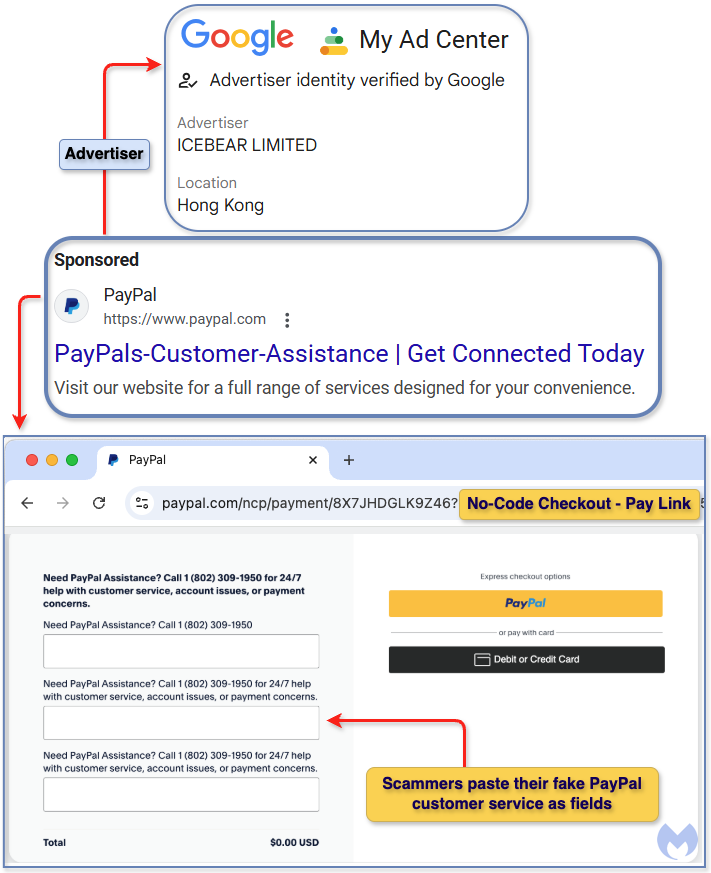
This article highlights a new scam targeting PayPal customers through misleading Google ads that mimic official PayPal links. Scammers exploit Google’s advertisement policies to direct potential victims to fraudulent pay pages, leading to personal information theft. Affected: PayPal customers, Google search users.
Keypoints :
- Scammers are creating fraudulent ads impersonating PayPal, using compromised advertiser accounts.
- Google’s ad policies allow this impersonation as long as the display and landing URLs share the same domain.
- Victims are diverted to a “no-code checkout” PayPal page tailored to trick users, featuring fake support numbers.
- The scam is particularly effective on mobile devices due to their limited screen size and lack of security software.
- Multiple malicious ads were observed redirecting victims to various deceptive pages.
- Users should be cautious and prioritize organic search results over paid ads to avoid scams.
- Malwarebytes is recommended for mobile users to block ads and malicious links.
- The campaign has been reported to both Google and PayPal.
MITRE Techniques :
- T1497: Virtualization/Sandbox Evasion – Scammers create ads that appear legitimate, exploiting familiar platforms to lure users.
- T1071: Application Layer Protocol – The use of pay links and impersonation of PayPal facilitates communication and data exchange under the guise of legitimate services.
- T1550.001: Use Alternate Authentication Material – Scammers promote a fraudulent support number appearing to be PayPal assistance.
Indicator of Compromise :
- [Archived URL] https://urlscan.io/result/3ea0654e-b446-4947-b926-b549624aa8b0
- [Malicious Link] hxxps://www.paypal.com/ncp/payment/8X7JHDGLK9Z46
- [Malicious Link] hxxps://www.paypal.com/ncp/payment/7QUEXNXR84X3L
- [Malicious Link] hxxps://www.paypal.com/ncp/payment/BHR4AMJAPWNZW
- [Scammers’ Phone Number] 1-802-309-1950
Full Story: https://www.malwarebytes.com/blog/scams/2025/02/paypals-no-code-checkout-abused-by-scammers
Views: 34