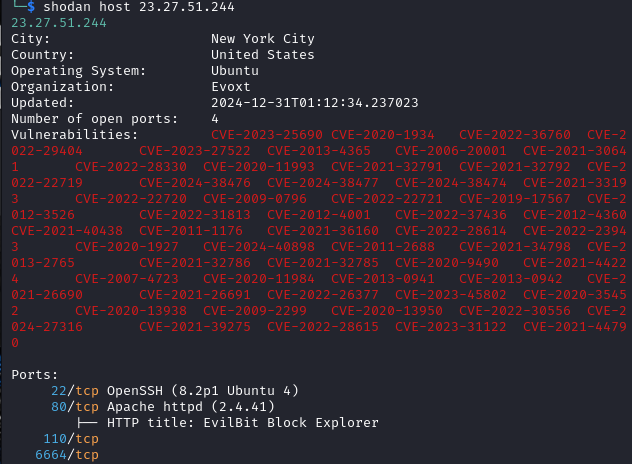
The article discusses a security analysis of a malicious URL that exploits vulnerable PHP servers to download and execute cryptocurrency mining software. The investigation reveals the use of specific executables and their associated hashes, as well as the identification of a wallet address linked to the mining activity. Affected: PHP servers
Keypoints :
- The SANS DShield project collects logs from participants.
- An interesting URL was identified that exploits vulnerable PHP servers.
- The URL is designed to download a secondary payload named dr0p.exe.
- Dynamic malware analysis revealed dr0p.exe retrieves another file, pkt1.exe.
- pkt1.exe spawns packetcrypt.exe and interacts with a cryptocurrency wallet.
- The observed activity highlights the need for PHP server audits and patches.
- The article emphasizes the distinction between PKT Classic and PKT cryptocurrency.
MITRE Techniques :
- Execution (T1203) – The malicious URL executes a PHP script that downloads and runs dr0p.exe.
- Command and Control (T1071) – The malware communicates with an external server to retrieve additional payloads.
- Credential Dumping (T1003) – The mining software may attempt to collect sensitive information from the compromised server.
- Data Encrypted for Impact (T1486) – The mining process could affect server performance and availability.
Indicator of Compromise :
- [IP address] 23.27.51.244
- [file hash] d078d8690446e831acc794ee2df5dfabcc5299493e7198993149e3c0c33ccb36
- [file hash] e3d0c31608917c0d7184c220d2510848f6267952c38f86926b15fb53d07bd562
- [file hash] 717fe92a00ab25cae8a46265293e3d1f25b2326ecd31406e7a2821853c64d397
- [others ioc] pkt1qxysc58g4cwwautg6dr4p7q7sd6tn2ldgukth5a
- Check the article for all found IoCs.
Full Research: https://isc.sans.edu/diary/PacketCrypt+Classic+Cryptocurrency+Miner+on+PHP+Servers/31564/