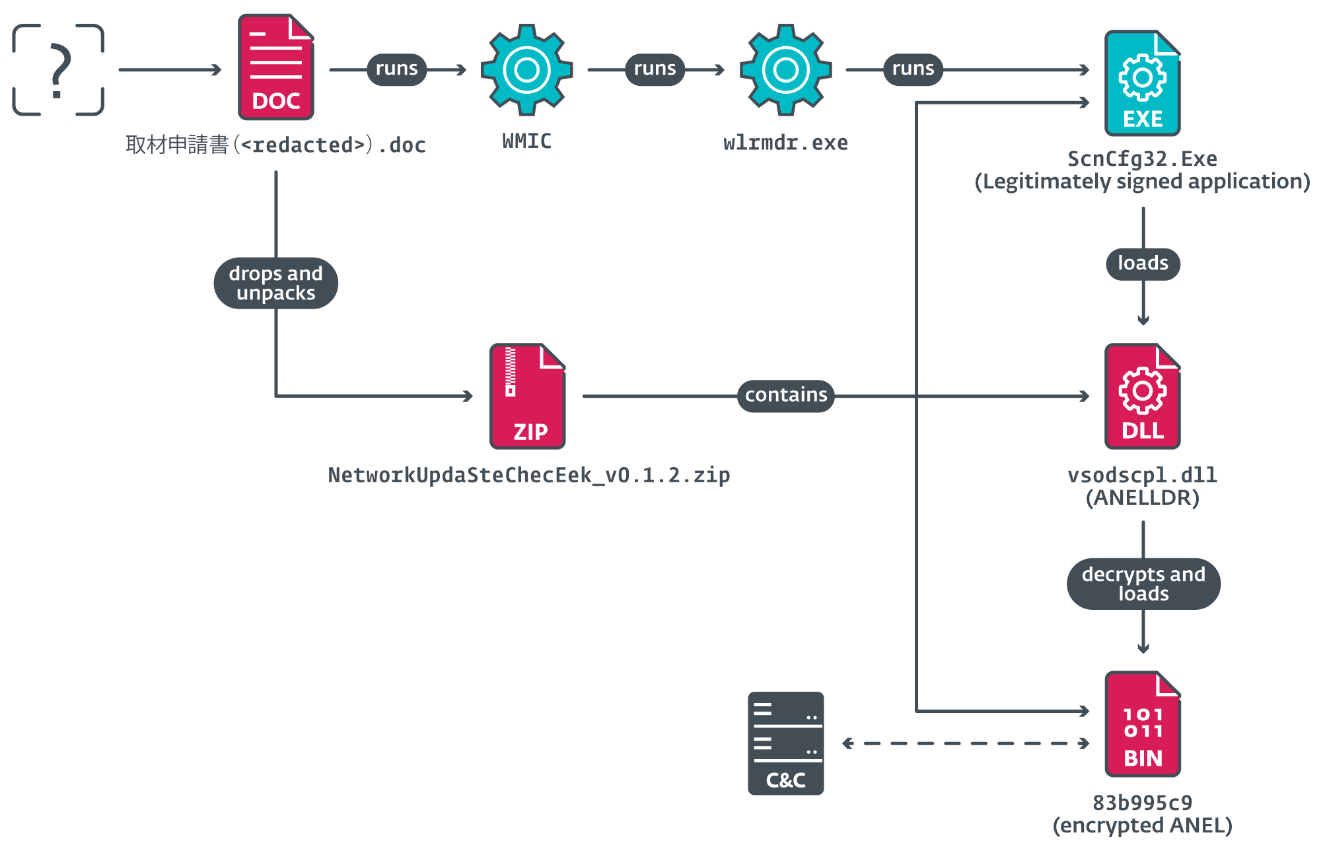
In August 2024, ESET researchers uncovered cyberespionage activities by the MirrorFace APT group targeting a Central European diplomatic institute related to Expo 2025 in Osaka, Japan. This marks the first instance of MirrorFace infiltrating a European entity, showcasing new tactics and tools, including the backdoor ANEL and a customized variant of AsyncRAT. The findings, arising from forensic analysis and collaboration with the affected institute, reveal insights into post-compromise operations. Affected: Central European diplomatic institute, Expo 2025, Europe, Japan
Keypoints :
- MirrorFace has refreshed its TTPs and tooling.
- First time MirrorFace has targeted a European entity.
- Utilization of ANEL backdoor, previously linked exclusively to APT10.
- Deployment of a heavily customized AsyncRAT with a complex execution chain inside Windows Sandbox.
- Cooperative forensic investigation with the Central European diplomatic institute led to new insights into MirrorFace’s activities.
- MirrorFace focused on espionage and exfiltration of information.
- Uncovered detailed mail chains as part of the spearphishing attack strategy utilized by MirrorFace.
MITRE Techniques :
- T1587.001 – Develop Capabilities: Malware – MirrorFace has developed custom tools such as HiddenFace.
- T1585.002 – Establish Accounts: Email Accounts – MirrorFace created a Gmail account for spearphishing.
- T1585.003 – Establish Accounts: Cloud Accounts – MirrorFace created a OneDrive account to host malicious files.
- T1588.001 – Obtain Capabilities: Malware – Used and customized AsyncRAT for its operations.
- T1566.002 – Phishing: Spearphishing Link – Sent a spearphishing email with a malicious OneDrive link.
- T1053.005 – Scheduled Task/Job: Scheduled Task – Used scheduled tasks to execute HiddenFace and AsyncRAT.
- T1204.001 – User Execution: Malicious Link – Relied on the target to download a malicious file from the shared OneDrive.
- T1047 – Windows Management Instrumentation – Used WMI to run ANEL as an execution proxy.
- T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys – ANEL uses a startup directory for persistence.
- T1070.001 – Indicator Removal: Clear Windows Event Logs – Cleared Windows event logs to delete evidence.
Indicator of Compromise :
- [Filename] The EXPO Exhibition in Japan in 2025.docx.lnk
- [Filename] HiddenFace
- [Filename] normal_.dotm
- [Filename] tmp.docx
- [Domain] vu4fleh3yd4ehpfpciinnwbnh4b77rdeypubhqr2dgfibjtvxpdxozid[.]onion