Threat Actor: OnePlus | OnePlus
Victim: Users of OnePlus devices | OnePlus
Price: Not specified
Exfiltrated Data Type: User data, including IMEI and manufacturer details
Additional Information :
- Security researcher Elliot Alderson discovered a file called “badword.txt” in the OnePlus clipboard application.
- The file contains a large number of Chinese phrases, suggesting that user data is being sent to Chinese servers without consent.
- The file is duplicated in a zip file called “pattern” which contains several other files.
- All these files are used in an obfuscated package that appears to be an Android library from teddymobile, a Chinese company.
- TeddyMobile has worked with various manufacturers, including Oppo.
- The TeddyMobile package may have the ability to collect various data from a phone.
- OnePlus denied the claim that the keywords in the file were used to filter out data that was not uploaded.
Security researcher Elliot Alderson found a file called badword.txt in OnePlus clipboard application, which contains a large number of Chinese phrases such as “Chairman, Vice President, Deputy Director, Associate Professor, Deputy Heads, General, Private Message, shipping, Address, email, …”. This badword.txt is duplicated in a zip file called pattern. This archive contains 7 files: – badword.txt – brackets.txt – end.txt – follow.txt – key.txt – start.txt . All these files are used in an obfuscated package which seems to be an Android library from teddymobile. TeddyMobile is a Chinese company, they worked with a lot of manufacturers including Oppo.
The @OnePlus #clipboard app contains a strange file called badword.txt
In these words, we can find: Chairman, Vice President, Deputy Director, Associate Professor, Deputy Heads, General, Private Message, shipping, Address, email, …https://t.co/ePQvD1citn pic.twitter.com/3dCh0joVkH
— Baptiste Robert (@fs0c131y) January 25, 2018
Researchers suspect that one plus one sends the user’s various data to the servers of Chinese companies without the user’s consent.
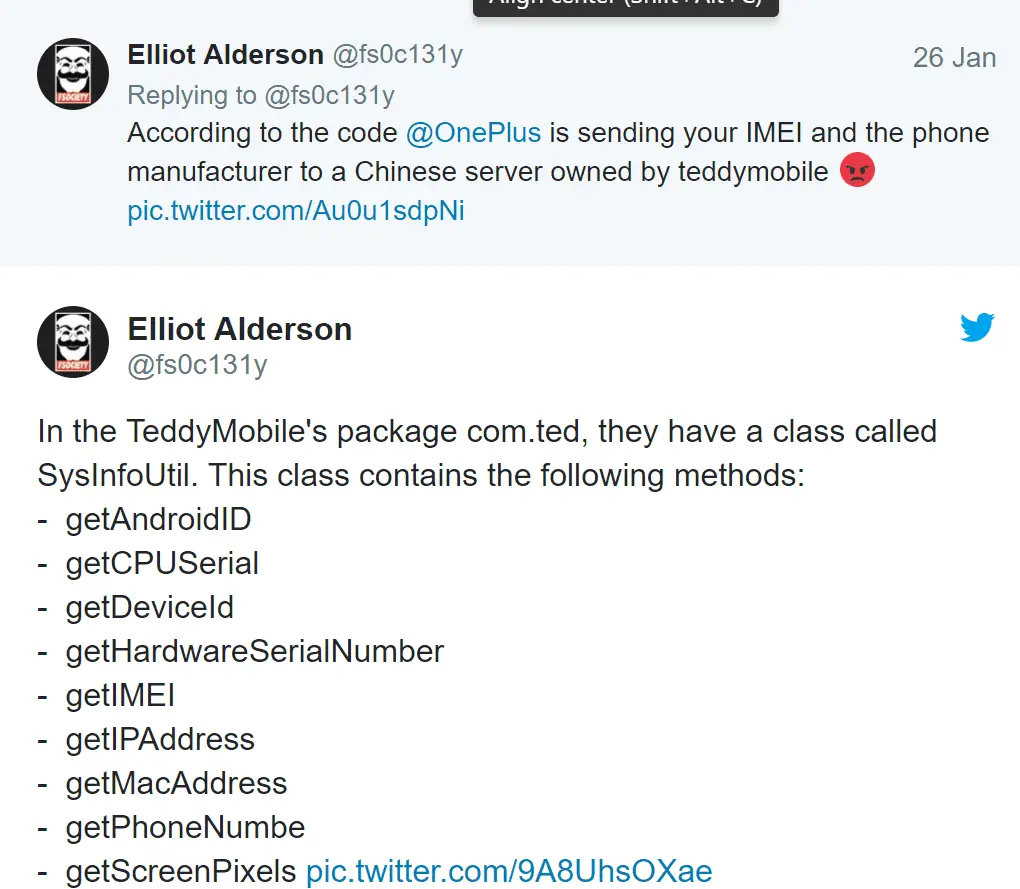
TeddyMobile package might be able to grab all sorts of data from a phone.
In the TeddyMobile’s package com.ted, they have a class called SysInfoUtil. This class contains the following methods:
– getAndroidID
– getCPUSerial
– getDeviceId
– getHardwareSerialNumber
– getIMEI
– getIPAddress
– getMacAddress
– getPhoneNumbe
– getScreenPixels pic.twitter.com/9A8UhsOXae— Baptiste Robert (@fs0c131y) January 25, 2018
One plus soon responded in an official forum, denying the claim that the keywords were used to filter out data that was not uploaded.
Original Source: https://securityonline.info/oneplus-sends-imei-and-the-phone-manufacturer-to-a-chinese-server/
Views: 1


 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português